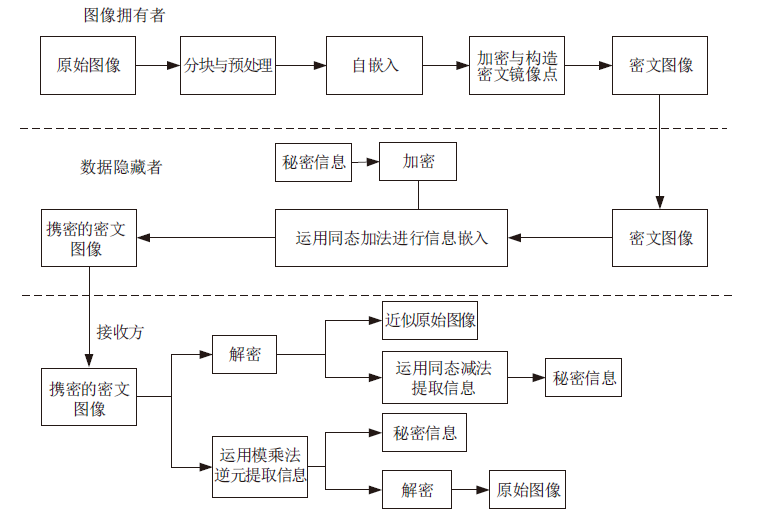
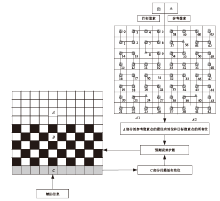
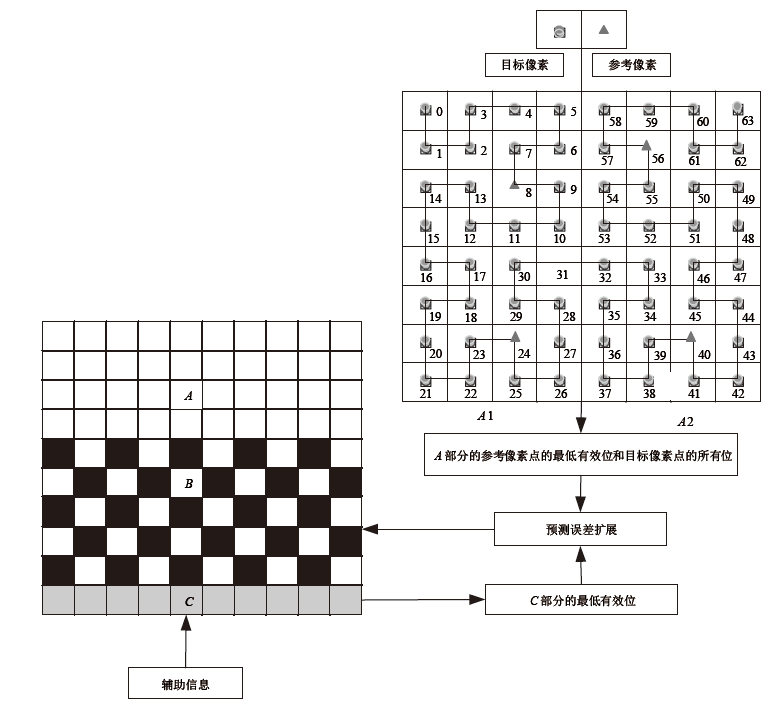
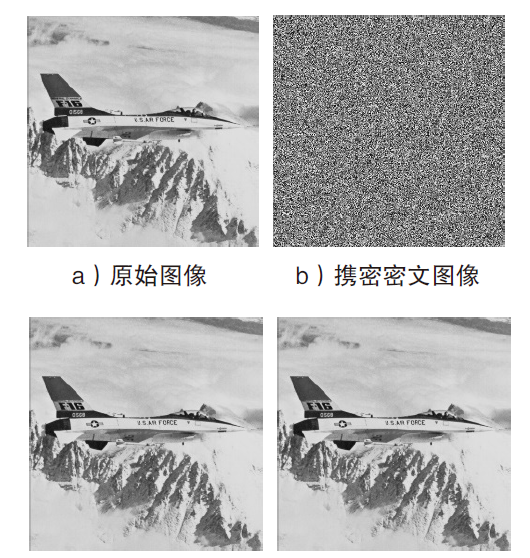
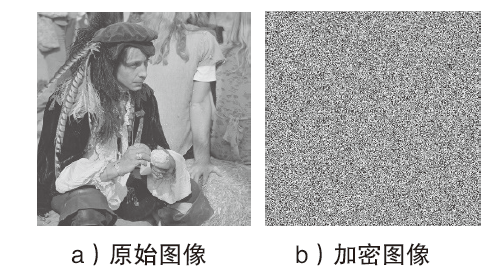
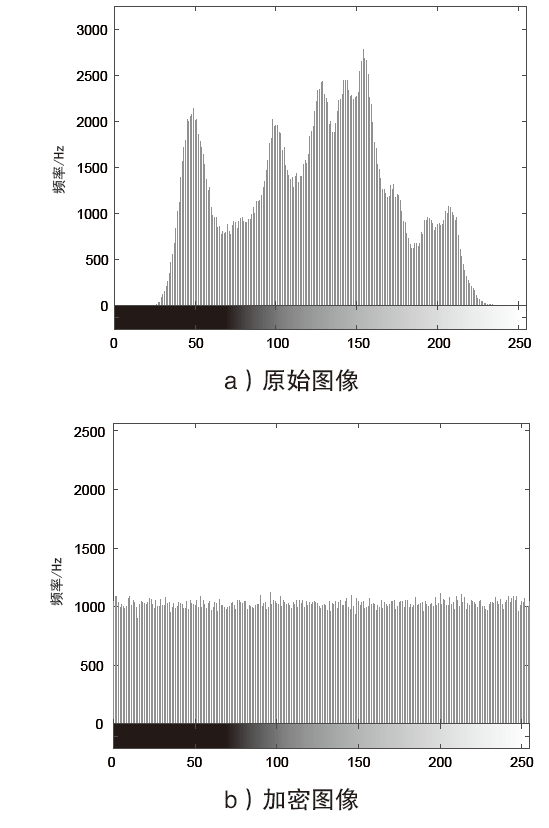
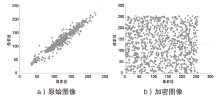
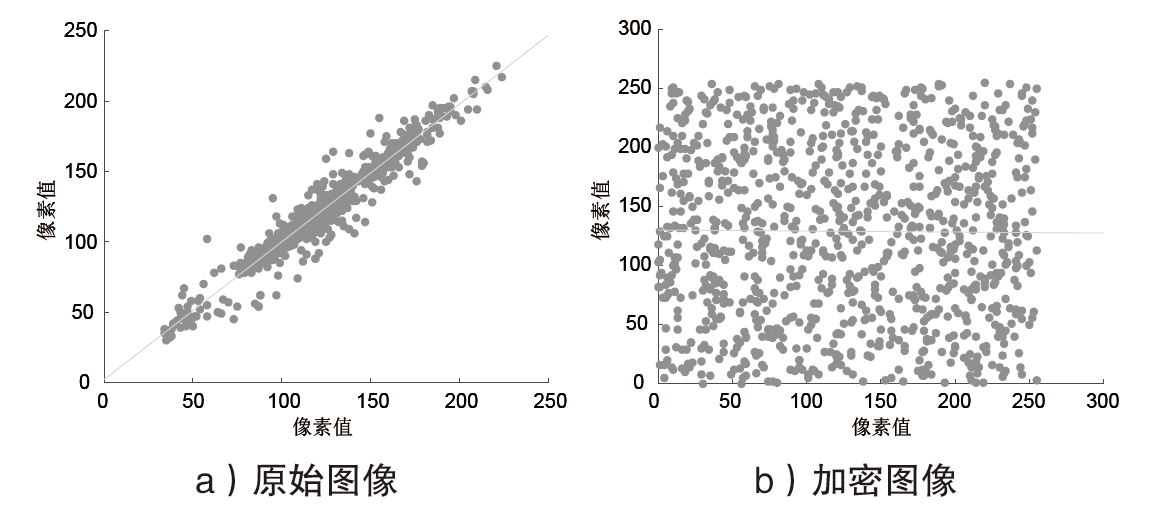
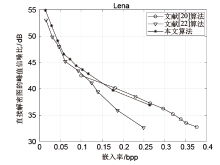
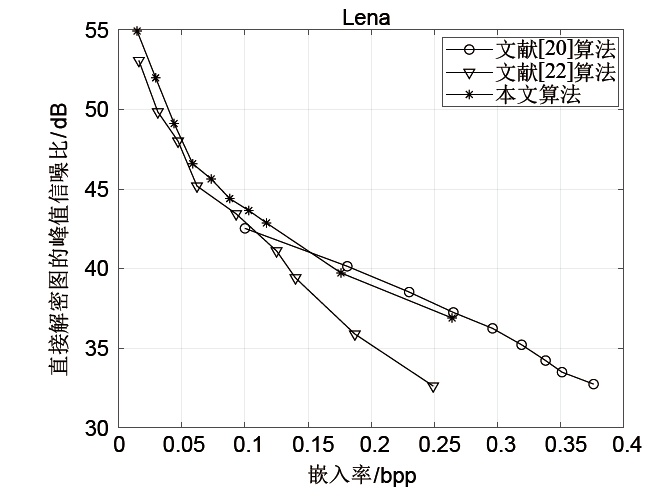
Netinfo Security ›› 2021, Vol. 21 ›› Issue (4): 73-80.doi: 10.3969/j.issn.1671-1122.2021.04.008
Previous Articles Next Articles
Research on Technology of Reversible Data Hiding in Encrypted Domain Based on Homomorphic Encryption
LIN Wenbing1,2, ZHANG Minqing1,2( ), ZHOU Neng1,2, KONG Yongjun1,2
), ZHOU Neng1,2, KONG Yongjun1,2
- 1. College of Cryptography Engineering, Engineering University of Chinese People Armed Police Force(PAP), Xi’an 710086, China
2. Key Laboratory of Network and Information Security under PAP, Xi’an 710086, China
-
Received:2020-11-06Online:2021-04-10Published:2021-05-14 -
Contact:ZHANG Minqing E-mail:api_zmq@126.com
CLC Number:
Cite this article
LIN Wenbing, ZHANG Minqing, ZHOU Neng, KONG Yongjun. Research on Technology of Reversible Data Hiding in Encrypted Domain Based on Homomorphic Encryption[J]. Netinfo Security, 2021, 21(4): 73-80.
share this article
| PSNR/dB | ||||||||
|---|---|---|---|---|---|---|---|---|
| 图像 | n | 嵌入容量/bpp | ||||||
| 0.015 | 0.029 | 0.044 | 0.059 | 0.073 | 0.088 | 0.103 | ||
| Lena | 1 | 48.40 | 45.07 | 42.22 | 40.10 | 38.44 | 37.19 | 36.21 |
| 2 | 54.27 | 51.39 | 48.54 | 46.15 | 45.31 | 43.87 | 42.64 | |
| 3 | 54.92 | 51.98 | 49.12 | 47.59 | 45.64 | 44.40 | 43.65 | |
| 4 | 52.11 | 49.31 | 47.45 | 45.21 | 44.27 | 42.47 | 41.16 | |
| Hill | 1 | 51.60 | 45.65 | 41.36 | 38.50 | 36.44 | 34.98 | 34.24 |
| 2 | 52.42 | 51.34 | 48.03 | 45.52 | 43.18 | 41.27 | 39.77 | |
| 3 | 53.18 | 52.04 | 50.65 | 47.44 | 46.54 | 45.31 | 43.56 | |
| 4 | 52.74 | 51.50 | 49.09 | 46.80 | 45.51 | 44.85 | 42.82 | |
| Plane | 1 | 42.66 | 41.04 | 39.33 | 37.51 | 36.08 | 35.33 | 34.78 |
| 2 | 46.65 | 42.65 | 41.88 | 41.01 | 40.21 | 39.31 | 38.16 | |
| 3 | 47.55 | 45.28 | 42.50 | 41.85 | 41.66 | 40.88 | 40.21 | |
| 4 | 47.37 | 44.63 | 41.59 | 40.88 | 39.22 | 39.03 | 38.64 | |
| Man | 1 | 43.79 | 40.92 | 39.53 | 38.28 | 37.29 | 36.47 | 35.84 |
| 2 | 45.73 | 43.80 | 41.88 | 40.08 | 39.50 | 38.68 | 37.54 | |
| 3 | 46.57 | 44.22 | 42.68 | 40.83 | 40.05 | 39.25 | 38.33 | |
| 4 | 46.28 | 43.03 | 41.72 | 39.90 | 38.95 | 38.01 | 37.83 | |
| 嵌入容量/ bits | PSNR/ dB | |||
|---|---|---|---|---|
| m = 4 | m = 8 | m = 16 | m = 32 | |
| 3 840 | 38.780 | 54.179 | 54.922 | 54.053 |
| 7 680 | 35.901 | 51.160 | 51.984 | 50.774 |
| 11 520 | 33.623 | 46.931 | 49.118 | 46.691 |
| 15 360 | 32.483 | 45.934 | 46.587 | 45.670 |
| 19 200 | 31.648 | 45.141 | 45.636 | 44.997 |
| 23 040 | 30.715 | 43.991 | 44.401 | 43.148 |
| 26 880 | 30.093 | 43.285 | 43.651 | 42.539 |
| 30 720 | 29.569 | 42.569 | 42.872 | 41.869 |
| 46 080 | 27.709 | 39.654 | 39.731 | 38.732 |
| 69 120 | 25.956 | 36.329 | 36.899 | 35.903 |
| 嵌入容量/ bits | PSNR/ dB | |||
|---|---|---|---|---|
| Lena | Hill | Man | Plane | |
| 3840 | 54.922 | 53.179 | 46.566 | 47.549 |
| 7680 | 51.984 | 52.038 | 44.221 | 45.280 |
| 11520 | 49.118 | 50.647 | 42.683 | 42.502 |
| 15360 | 46.587 | 47.444 | 40.833 | 41.851 |
| 19200 | 45.636 | 46.538 | 40.051 | 41.655 |
| 23040 | 44.401 | 45.310 | 39.246 | 40.883 |
| 26880 | 43.651 | 43.555 | 38.326 | 40.214 |
| 30720 | 42.872 | 42.558 | 37.616 | 39.924 |
| 46080 | 39.731 | 38.759 | 35.176 | 37.536 |
| 69120 | 36.899 | 35.107 | 33.114 | 35.288 |
| [1] | WANG Lina, ZHANG Huanguo, YE Dengpan, et al. Information Hiding Technology and Application[M]. Wuhan: Wuhan University Press, 2012. |
| 王丽娜, 张焕国, 叶登攀, 等. 信息隐藏技术与应用[M]. 武汉: 武汉大学出版社, 2012. | |
| [2] |
SHI Yunqing, LI Xiaolong, ZHANG Xinpeng, et al. Reversible Data Hiding: Advances in The Past Two Decades[J]. IEEE Access, 2016,4(5):3210-3237.
doi: 10.1109/ACCESS.2016.2573308 URL |
| [3] |
LI Xiaolong, LI Bin, YANG Bin, et al. General Framework to Histogram Shifting Based Reversible Data Hiding[J]. IEEE Trans on Image Processing, 2013,22(6):2181-2191.
doi: 10.1109/TIP.2013.2246179 URL |
| [4] | FRIDRICH J, GOLJAN M, DU R. Lossless Data Embedding New Paradigm in Digital Watermarking[J]. EURASIP Journal on Advances in Signal Processing, 2002,2002(2):185-196. |
| [5] |
CELIK M U, SHARMA G, TEKALP A M, et al. Lossless Generalized LSB Data Embedding[J]. IEEE Trans on Image Processing, 2005,14(2):253-266.
doi: 10.1109/TIP.2004.840686 URL |
| [6] |
TIAN Jun. Reversible Data Embedding Using a Difference Expansion[J]. IEEE Trans on Circuits and Systems for Video Technology, 2003,13(8):890-896.
doi: 10.1109/TCSVT.2003.815962 URL |
| [7] |
SUBBURAM S, SELVAKUMAR S, GEETHA S. High Performance Reversible Data Hiding Scheme Through Multilevel Histogram Modification in Lifting Integer Wavelet Transform[J]. Multimedia Tools and Applications, 2018,77(6):7071-7095.
doi: 10.1007/s11042-017-4622-0 URL |
| [8] |
QIU Yingqiang, QIAN Zhenxing, YU Lun. Adaptive Reversible Data Hiding by Extending The Generalized Integer Transformation[J]. IEEE Signal Processing Letters, 2016,23(1):130-134.
doi: 10.1109/LSP.2015.2504464 URL |
| [9] |
PAN Zhibin, HU Sen, MA Xiaoxiao, et al. Reversible Data Hiding Based on Local Histogram Shifting with Multilayer Embedding[J]. Journal of Visual Communication and Image Representation, 2015,31(8):64-74.
doi: 10.1016/j.jvcir.2015.05.005 URL |
| [10] |
LI Xiaolong, ZHANG Weiming, GUI Xinlu, et al. Efficient Reversible Data Hiding Based on Multiple Histograms Modification[J]. IEEE Transactions on Information Forensics and Security, 2017,10(9):2016-2027.
doi: 10.1109/TIFS.2015.2444354 URL |
| [11] |
GE Haoli, CHEN Yan, QIAN Zhenxing, et al. A High Capacity Multi-level Approach for Reversible Data Hiding in Encrypted Images[J]. IEEE Transactions on Circuits and Systems for Video Technology, 2019,29(8):2285-2295.
doi: 10.1109/TCSVT.76 URL |
| [12] |
YIN Zhaoxia, XIANG Youzhi, ZHANG Xinpeng, et al. Reversible Data Hiding in Encrypted Images Based on Multi-MSB Prediction and Huffman Coding[J]. IEEE Transactions on Multimedia, 2020,22(4):874-884.
doi: 10.1109/TMM.6046 URL |
| [13] |
YI Shuang, ZHOU Yicong. Separable and Reversible Data Hiding in Encrypted Images Using Parametric Binary Tree Labeling[J]. IEEE Transactions on Multimedia, 2019,21(1):51-64.
doi: 10.1109/TMM.2018.2844679 URL |
| [14] |
MALIK A, WANG Hongxia, CHEN Yanli, et al. A Reversible Data Hiding in Encrypted Image Based on Prediction-error Estimation and Location Map[J]. Multimedia Tools and Applications, 2020,79(1):11591-11614.
doi: 10.1007/s11042-019-08460-w URL |
| [15] | PUTEAUX P, PUECH W. An Efficient MSB Prediction-based Method for High-capacity Reversible Data Hiding in Encrypted Images[J]. IEEE Transactions on Information Forensics and Security, 2018,18(6):1-12. |
| [16] |
ZHANG Xinpeng. Reversible Data Hiding in Encrypted Image[J]. IEEE Signal Processing Letters, 2011,18(4):255-258.
doi: 10.1109/LSP.2011.2114651 URL |
| [17] |
HONG Wen, CHEN Tingshou, WU Hanyan. An Improved Reversible Data Hiding in Encrypted Images Using Side Match[J]. IEEE Signal Processing Letters, 2012,19(4):199-202.
doi: 10.1109/LSP.2012.2187334 URL |
| [18] | ZHANG Xinpeng. Separable Reversible Data Hiding in Encrypted Image[J]. IEEE Trans on Information Forensics and Security, 2012,7(2):526-532. |
| [19] |
CHEN Yuchi, SHI Chihei, HORNG Gwoboa. Encrypted Signal-based Reversible Data Hiding with Public Key Cryptosystem[J]. Journal of Visual Communication and Image Representation, 2014,25(5):1164-1170.
doi: 10.1016/j.jvcir.2014.04.003 URL |
| [20] |
ZHANG Xinpeng, LONG Jing, WANG Zichi, et al. Lossless and Reversible Data Hiding in Encrypted Images with Public Key Cryptography[J]. IEEE Trans on Circuits and Systems for Video Technology, 2016,26(9):1622-1631.
doi: 10.1109/TCSVT.2015.2433194 URL |
| [21] |
FRIDRICH J, GOLJAN M, LISONEK P, et al. Writing on Wet Paper[J]. IEEE Trans on Signal Processing, 2005,53(10):3923-3935.
doi: 10.1109/TSP.2005.855393 URL |
| [22] |
XIANG Shijun, LUO Xinrong. Reversible Data Hiding in Homomorphic Encrypted Domain by Mirroring Ciphertext Group[J]. IEEE Trans on Circuits and Systems for Video Technology, 2018,28(11):3099-3110.
doi: 10.1109/TCSVT.2017.2742023 URL |
| [23] | PAILLIER P. Public-key Cryptosystems Based on Composite Degree Residuosity Classes[J]. Proceeding of the Advances Cryptology, 1999,92(4), 223-238. |
| [1] | ZHANG Minqing, ZHOU Neng, LIU Mengmeng, KE Yan. Research on Reversible Data Hiding Technology in Homomorphic Encrypted Domain [J]. Netinfo Security, 2020, 20(8): 25-36. |
| [2] | LI Ningbo, ZHOU Haonan, CHE Xiaoliang, YANG Xiaoyuan. Design of Directional Decryption Protocol Based on Multi-key Fully Homomorphic Encryption in Cloud Environment [J]. Netinfo Security, 2020, 20(6): 10-16. |
| [3] | ZHOU Haonan, LI Ningbo, CHE Xiaoliang, YANG Xiaoyuan. Multi-key Fully Homomorphic Encryption Scheme over Prime Power Cyclotomic Rings [J]. Netinfo Security, 2020, 20(5): 83-87. |
| [4] | FU Zhizhou, WANG Liming, TANG Ding, ZHANG Shuguang. HBase Secondary Ciphertext Indexing Method Based on Homomorphic Encryption [J]. Netinfo Security, 2020, 20(4): 55-64. |
| [5] | TANG Chunming, LIN Xuhui. Protocol of Privacy-preserving Set Intersection Computation [J]. Netinfo Security, 2020, 20(1): 9-15. |
| [6] | Hongqiong TANG, Ke NIU, Yingnan ZHANG, Xiaoyuan YANG. Reversible Data Hiding in Videos Based on Adaptive Two-dimensional Histogram Modification [J]. Netinfo Security, 2019, 19(9): 106-110. |
| [7] | Wenchao LIU, Feng PAN, Xiaoyuan YANG, Tanping ZHOU. Debug and Analysis of Fully Homomorphic Encryption Library Based on GPU [J]. Netinfo Security, 2019, 19(6): 76-83. |
| [8] | Zhongyuan QIN, Yin HAN, Xuejin ZHU. Research on Ciphertext Full-text Retrieval of Cloud Storage Based on Improved DGHV Algorithm [J]. Netinfo Security, 2019, 19(1): 8-8. |
| [9] | Bo OU, Xianglian SHI. Reversible Data Hiding for Three-dimensional Image Based on Depth No-synthesis-error Model [J]. Netinfo Security, 2018, 18(5): 24-31. |
| [10] | Lin YOU, Jiahao LIANG. Research on Secure Identity Authentication Based on Homomorphic Encryption and Biometric [J]. Netinfo Security, 2018, 18(4): 1-8. |
| [11] | Xinxia SONG, Jiamin MA, Zhigang CHEN, Kefei CHEN. Iris Ciphertext Authentication System Based on SEAL [J]. Netinfo Security, 2018, 18(12): 15-22. |
| [12] | Rongbing WANG, Yanan LI, Hongyan XU, Yong FENG. Full Homomorphic Encryption Scheme over Real Number Suitable for Cloud Service Environment [J]. Netinfo Security, 2018, 18(11): 49-56. |
| [13] | Yongjian WANG, Jian ZHANG, Shaoyu CHENG, Xiaohui TIE. An Improved Design of Homomorphic Encryption for Cloud Computing [J]. Netinfo Security, 2017, 17(3): 21-26. |
| [14] | Di XIAO, Ying WANG, Yanting CHANG, Jiaqi ZHOU. Reversible Data Hiding in Encrypted Image Based on Additive Homomorphism and Multi-level Difference Histogram Shifting [J]. Netinfo Security, 2016, 16(4): 9-16. |
| [15] | Zengpeng LI, Yan ZOU, Lei ZHANG, Chunguang MA. A Privacy Preservation Scheme for Data Exchange of Smart Grid Based on Homomorphic Encryption [J]. Netinfo Security, 2016, 16(3): 1-7. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||