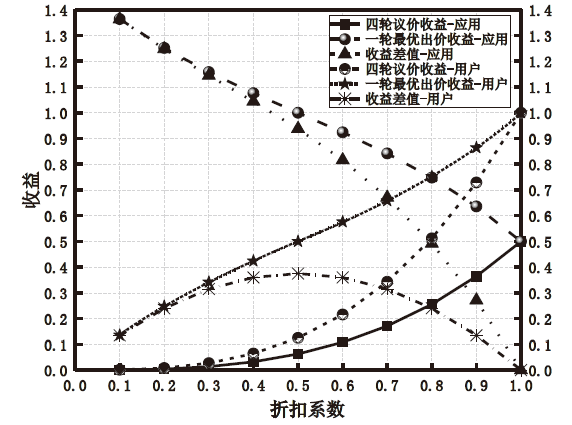
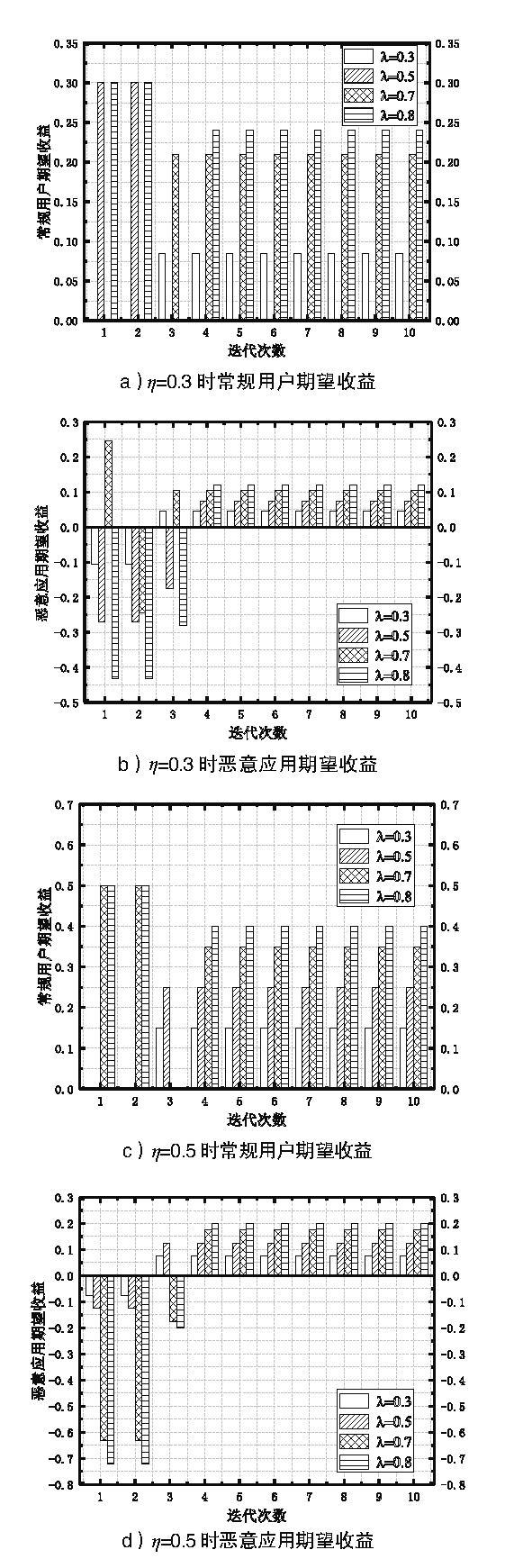
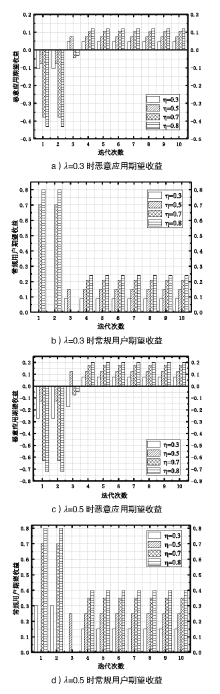
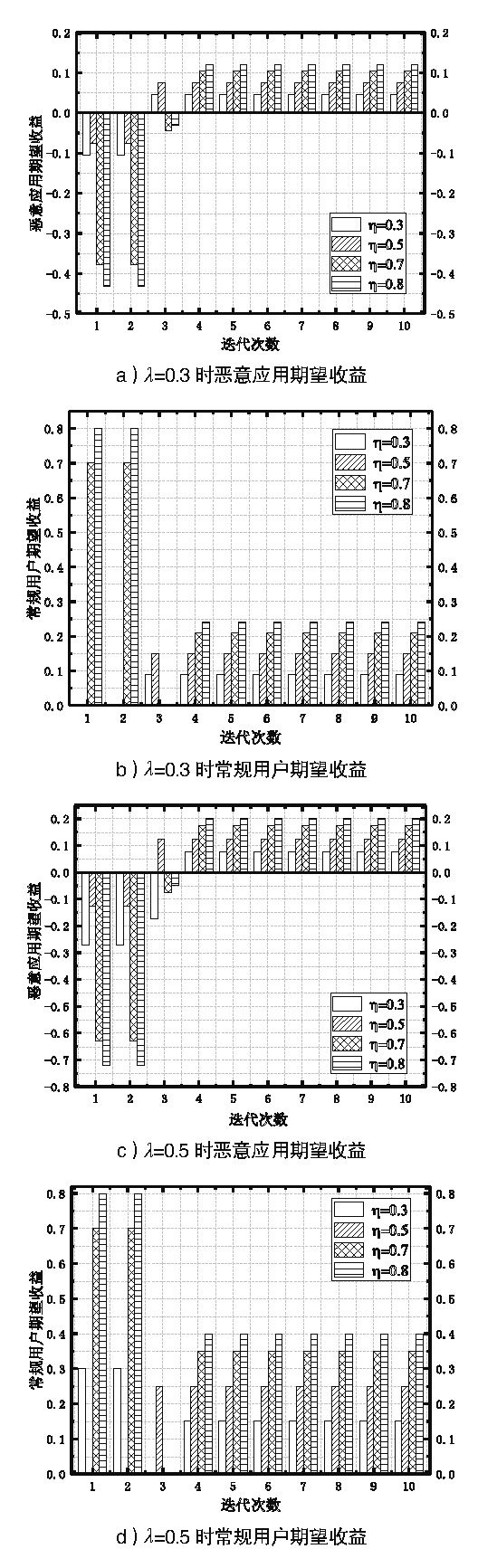
Netinfo Security ›› 2021, Vol. 21 ›› Issue (4): 81-88.doi: 10.3969/j.issn.1671-1122.2021.04.009
Previous Articles Next Articles
A Novel Fraud Prevention Strategy Based on Bargaining Bayesian Game Model
REN Hang1, CHENG Xiangguo1( ), ZHANG Rui2, XIA Hui2
), ZHANG Rui2, XIA Hui2
- 1. College of Computer Science and Technology, Qingdao University, Qingdao 266071, China
2. College of Information Science and Engineering, Ocean University of China, Qingdao 266100, China
-
Received:2021-01-16Online:2021-04-10Published:2021-05-14 -
Contact:CHENG Xiangguo E-mail:15964252399@163.com
CLC Number:
Cite this article
REN Hang, CHENG Xiangguo, ZHANG Rui, XIA Hui. A Novel Fraud Prevention Strategy Based on Bargaining Bayesian Game Model[J]. Netinfo Security, 2021, 21(4): 81-88.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.04.009
| [1] |
CALLSNAN C, JERMAN B, BLAZIC A J. User Awareness and Tolerance of Privacy Abuse on Mobile Internet: An Exploratory Study[J]. Telematics and Informatics, 2016,33(1):109-128.
doi: 10.1016/j.tele.2015.04.009 URL |
| [2] | KIRNER-LUDWIG M C. Creation, Dissemination and Uptake of Fake-quotes in Lay Political Discourse on Facebook and Twitter[EB/OL]. http://apps.webofknowledge.com/full_record.do?product=UA&search_mode=GeneralSearch&qid=2&SID=8DrGRLng7MjX1mVH2x4&page=1&doc=1, 2021-01-05. |
| [3] | TIWARI N, SARDAR A S. Advancements in Reversible Data Hiding Techniques: A Review[J]. International Journal of Computer Science and Network Security, 2017,17(3):195-205. |
| [4] | LONG Min, ZHAO Yu, ZHANG Xiang, et al. A Separable Reversible Data Hiding Scheme for Encrypted Images Based on TrominoScrambling and Adaptive Pixel Value Ordering[EB/OL]. http://apps.webofknowledge.com/full_record.do?product=UA&search_mode=GeneralSearch&qid=18&SID=8DrGRLng7MjX1mVH2x4&page=1&doc=1, 2021-01-03. |
| [5] | KAUR G, SINGH S, RANI R, et al. A Comprehensive Study of Reversible Data Hiding (RDH) Schemes Based on Pixel Value Ordering (PVO)[EB/OL]. http://apps.webofknowledge.com/full_record.do?product=UA&search_mode=GeneralSearch&qid=22&SID=8DrGRLng7MjX1mVH2x4&page=1&doc=1, 2021-01-03. |
| [6] | YUAN Ziqian, GUAN Zijie, FENG Hao. An Improved Information Hiding Algorithm Based on Image[C]// IEEE. 2017 IEEE 15th International Conference on Software Engineering Research, Management and Applications, June 7-9, 2017, London, UK. NJ: IEEE, 2017: 169-172. |
| [7] | OU Bo, SHI Xianglian. Reversible Data Hiding for Three-dimensional Image Based on Depth No-synjournal-error Model[J]. Netinfo Security, 2018,18(5):24-31. |
| 欧博, 石向莲. 基于深度无合成误差模型的三维图像可逆信息隐藏方法研究[J]. 信息网络安全, 2018,18(5):24-31. | |
| [8] |
MOHANARATHINAM A, KAMALRAJ S, VENKATESAN G, et al. Digital Watermarking Techniques for Image Security: A Review[J]. Journal of Ambient Intelligence and Humanized Computing, 2020,11(8):3221-3229.
doi: 10.1007/s12652-019-01500-1 URL |
| [9] | LIU Yang, TANG Shanyu, LIU Ran, et al. Secure and Robust Digital Image Watermarking Scheme Using Logistic and RSA Encryption[EB/OL]. http://apps.webofknowledge.com/full_record.do?product=UA&search_mode=GeneralSearch&qid=35&SID=8DrGRLng7MjX1mVH2x4&page=1&doc=1, 2018-05-01. |
| [10] | MAMIDI R, DADHICH G, DSOUZA E, et al. Novel Algorithm for Embedding Audio Watermark in Images[C]// IEEE. 3rd International Conference on Computing for Sustainable Global Development, March 16-18, 2016, New Delhi, India. New York: IEEE, 2016: 2654-2659. |
| [11] | NAGTODE S A, KORDE S A. Splicing Detection Technique for Images[C]// Springer. Vaigai College of Engineering. International Conference on Computer Networks, Big Data and IoT, December 19-20, 2018, Madurai, India. Switzerland: Springer International Publishing Ag, 2020: 654-660. |
| [12] | LI Ce, MA Qiang, XIAO Limei, et al. Image Splicing Detection Based on Markov Features in QDCTDomain[EB/OL]. http://apps.webofknowledge.com/full_record.do?product=UA&search_mode=GeneralSearch&qid=46&SID=8DrGRLng7MjX1mVH2x4&page=1&doc=2, 2017-03-08. |
| [13] | VAMSI K, CHADHA R, RAMKUMAR B, et al. Image Splicing Detection Using HMRF Superpixel Segmentation[C]// IEEE. 2017 7th International Conference on Communication Systems and Network Technologies, November 11-13, 2017, Nagpur, India. New York: IEEE, 2018: 177-182. |
| [14] | WANG Shunfei, YAN Junhua, WANG Zhigang. Improved Moving Object Detection Algorithm Based on Local United Feature[J]. Chinese Journal of Scientific Instrument, 2015,36(10):2241-2248. |
| 王顺飞, 闫钧华, 王志刚. 改进的基于局部联合特征的运动目标检测方法[J]. 仪器仪表学报, 2015,36(10):2241-2248. | |
| [15] | ZHANG Yang, LIU Tingwen, SHA Hongzhou, et al. Malicious Domain Detection Based on Multiple-dimensional Features[J]. Journal of Computer Applications, 2016,36(004):941-944. |
| 张洋, 柳厅文, 沙泓州, 等. 基于多元属性特征的恶意域名检测[J]. 计算机应用, 2016,36(004):941-944. | |
| [16] | YUILL J J, JAMES J. Defensive Computer-security Deception Operations: Processes, Principles and Techniques[D]. North Carolina: North Carolina State University, 2006. |
| [17] | HAN Xiao, KHEIR N, BALZAOTTI D. Deception Techniques in Computer Security: A Research Perspective[J]. ACM Computing Surveys, 2018,51(4):36. |
| [18] | ALMESHEKAH M H, SPAFFORD E H. Cyber Security Deception[M]. West-berlin: Springer International Publishing, 2016. |
| [19] | URIAS V E, STOUT W M S LUC-WATSON J. et al. Technologies to Enable Cyber Deception[C]// IEEE. 2017 International Carnahan Conference on Security Technology, October 23-26, 2017, Madrid, SPAIN. New York: IEEE, 2017: 1-6. |
| [20] | WANG Changchun, SHI Changhui, WANG Chong, et al. An Analyzing Method for Computer Network Security Based on Markov Game Model[C]// IEEE. 2016 IEEE Advanced Information Management, Communicates, Electronic and Automation Control Conference, October 3-5, 2016, Xi'an, China. New York: IEEE, 2017: 454-458. |
| [21] | ATTIAH A, CHATTERJEE M, ZOU C C. A Game Theoretic Approach to Model Cyber Attack and Defense Strategies[C]// IEEE. 2018 IEEE International Conference on Communications, May 20-24, 2018, Kansas City, MO, USA. New York: IEEE, 2018: 1-7. |
| [22] | LIU Qilie, LIU Maosong, LI Yun, et al. Novel Game-based Incentive Strategy for opportunistic networks[J]. Application Research of Computers, 2015,32(7):2128-2132. |
| 刘期烈, 刘茂松, 李云, 等. 基于博弈论的机会网络激励机制的研究[J]. 计算机应用研究, 2015,32(7):2128-2132. |
| [1] | ZHOU Yousheng, WANG Ming, LIU Yuanni. Privacy Protection Scheme Supporting Interval Query for LBS Outsourced Data [J]. Netinfo Security, 2021, 21(3): 26-36. |
| [2] | LIU Feng, YANG Jie, QI Jiayin. Two-Party ECDSA for Blockchain Based on Hash Proof Systems [J]. Netinfo Security, 2021, 21(1): 19-26. |
| [3] | LI Ningbo, ZHOU Haonan, CHE Xiaoliang, YANG Xiaoyuan. Design of Directional Decryption Protocol Based on Multi-key Fully Homomorphic Encryption in Cloud Environment [J]. Netinfo Security, 2020, 20(6): 10-16. |
| [4] | XIAO Biao, YAN Hongqiang, LUO Haining, LI Jucheng. Research on Improvement of Bayesian Network Privacy Protection Algorithm Based on Differential Privacy [J]. Netinfo Security, 2020, 20(11): 75-86. |
| [5] | HE Jingsha, DU Jinhui, ZHU Nafei. Research on k-anonymity Algorithm for Personalized Quasi-identifier Attributes [J]. Netinfo Security, 2020, 20(10): 19-26. |
| [6] | HUANG Baohua, CHENG Qi, YUAN Hong, HUANG Pirong. K-means Clustering Algorithm Based on Differential Privacy with Distance and Sum of Square Error [J]. Netinfo Security, 2020, 20(10): 34-40. |
| [7] | Wenjiang HAO, Yun LIN. Research on Social Responsibility of Internet Enterprises and Its Enlightenment [J]. Netinfo Security, 2019, 19(9): 130-133. |
| [8] | Quan ZHOU, Shumei XU, Ningbin YANG. A Privacy Protection Scheme for Smart Grid Based on Attribute-based Group Signature [J]. Netinfo Security, 2019, 19(7): 25-30. |
| [9] | Yanming FU, Zhenduo LI. Research on k-means++ Clustering Algorithm Based on Laplace Mechanism for Differential Privacy Protection [J]. Netinfo Security, 2019, 19(2): 43-52. |
| [10] | Ronglei HU, Yanqiong HE, Ping ZENG, Xiaohong FAN. Design and Implementation of Medical Privacy Protection Scheme in Big Data Environment [J]. Netinfo Security, 2018, 18(9): 48-54. |
| [11] | Peili LI, Haixia XU, Tianjun MA, Yongheng MU. The Application of Blockchain Technology in Network Mutual Aid and User Privacy Protection [J]. Netinfo Security, 2018, 18(9): 60-65. |
| [12] | Rong MA, Xiuhua CHEN, Hui LIU, Jinbo XIONG. Research on User Privacy Measurement and Privacy Protection in Mobile Crowdsensing [J]. Netinfo Security, 2018, 18(8): 64-72. |
| [13] | Le WANG, Zherong YANG, Rongjing LIU, Xiang WANG. A CP-ABE Privacy Preserving Method for Wearable Devices [J]. Netinfo Security, 2018, 18(6): 77-84. |
| [14] | Lei ZHANG, Bin WANG, Lili YU. A Markov Prediction-based Algorithm for Continuous Query Privacy Protection [J]. Netinfo Security, 2018, 18(5): 12-12. |
| [15] | Lei ZHANG, Bin WANG, Lili YU. A Hash Function-based Attribute Generalization Privacy Protection Scheme [J]. Netinfo Security, 2018, 18(3): 14-25. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||