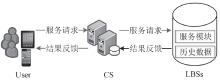
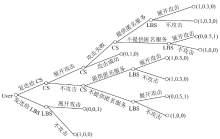
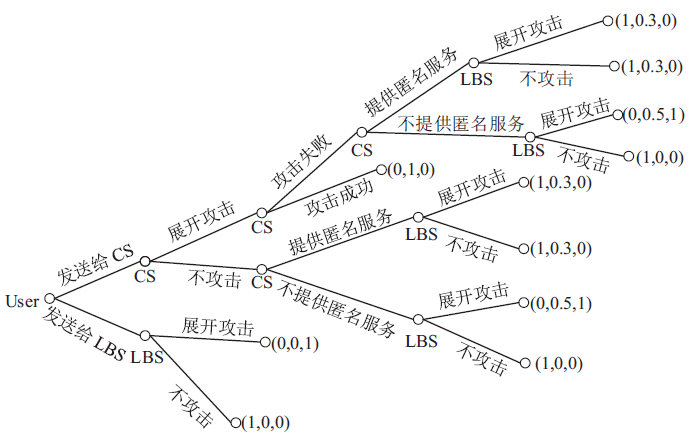
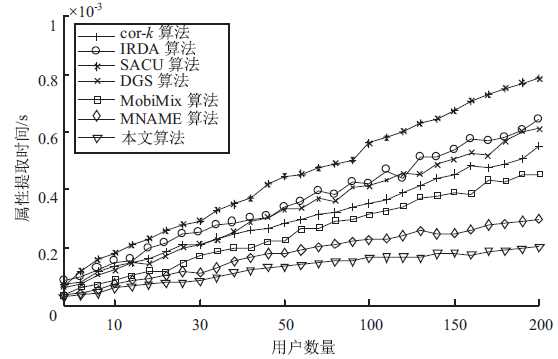
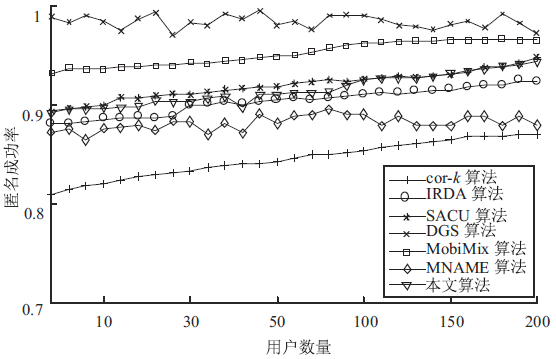
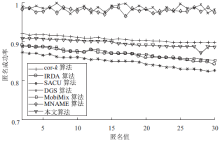
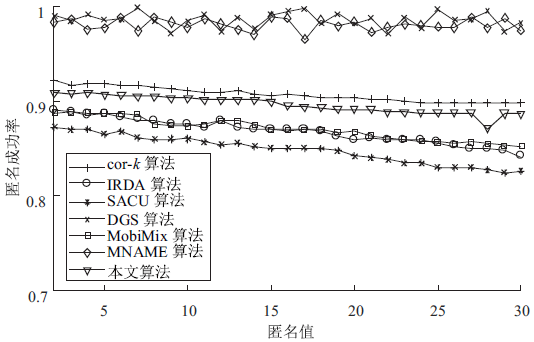
| [1] |
GRUTESER M, GRUNWALD D.Anonymous usage of location-based services through spatial and temporal cloaking[C]//ACM. 1st International Conference on Mobile Systems, Applications and Services, May 5-8, 2003, San Francisco, California. New York: ACM, 2003: 31-42.
|
| [2] |
LIU Fuyu L, HUA K A, CAI Ying.Query l-diversity in Location-based Services[C]//IEEE. 10th International Conference on Mobile Data Management: Systems, Services and Middleware, May 18-20, 2009, Taipei, China. New Jersey: IEEE, 2009: 436-442.
|
| [3] |
XIAO Zhen, XU Jianliang, MENG Xiaofeng. p-Sensitivity: A Semantic Privacy-protection Model for Location-based Services[C]//IEEE. 9th International Conference on Mobile Data Management Workshops, April 27-30, 2008, Beijing, China. New Jersey: IEEE, 2008: 47-54.
|
| [4] |
GHINITA G, KALNIS P, KHOSHGOZARAN A, et al.Private Queries in Location Based Services: Anonymizers are not Necessary[C]//ACM. 2008 ACM SIGMOD International Conference on Management of Data, June 10-12, 2008, Vancouver, Canada. New York: ACM, 2008: 121-132.
|
| [5] |
CHOW C Y, MOKBEL M F, LIU Xuan.A Peer-to-Peer Spatial Cloaking Algorithm for Anonymous Location-based Service[C]//ACM. 14th Annual ACM International Symposium on Advances in Geographic Information Systems, November 10-11, 2006, Arlington, Virginia, USA. New York: ACM, 2006: 171-178.
|
| [6] |
SCHLEGEL R, CHOW C Y, HUANG Qiong, et al.User-defined Privacy Grid System for Continuous Location-based Services[J]. IEEE Transactions on Mobile Computing, 2015, 14(10): 2158-2172.
|
| [7] |
NIU Ben, ZHU Xioayan, LI Qinghua, et al.A Novel Attack to Spatial Cloaking Schemes in Location-based Services[J]. Future Generation Computer Systems, 2015, 49(C): 125-132.
|
| [8] |
MA Chunguang, ZHANG Lei, YANG Songtao, et al.Achieve Personalized Anonymity through Query Blocks Exchanging[J]. China Communications, 2016, 13(11): 106-118.
|
| [9] |
SUN Yanming, CHEN Min, HU Long, et al. ASA: Against Statistical Attacks for Privacy-aware users in Location Based Service[EB/OL]. , 2017-10-12.
|
| [10] |
马春光,张磊,杨松涛. 位置轨迹隐私保护综述[J]. 信息网络安全,2015(10):24-31.
|
| [11] |
PALANISAMY B, LIU Ling, LEE K, et al.Anonymizing Continuous Queries with Delay-tolerant Mix-zones over Road Networks[J]. Distributed and Parallel Databases, 2014, 32(1): 91-118.
|
| [12] |
HWANG R H, HSUEH Y L, CHUNG H W.A Novel Time-obfuscated Algorithm for Trajectory Privacy Protection[J]. IEEE Transactions on Services Computing, 2014, 7(2): 126-139.
|
| [13] |
ZEBERGA K, JIN R, CHO H J, et al. A Safe-region Approach to a Moving k-RNN Queries in a Directed Road Network[EB/OL]. , 2016-11-25.
|
| [14] |
肖剑川,许力,叶阿勇,等. 基于Voronoi图的路网轨迹隐私保护研究[J]. 信息网络安全,2016(6):15-21.
|
| [15] |
张磊,马春光,杨松涛,等. 基于轮廓泛化的位置隐私保护模型及方法[J]. 系统工程与电子技术,2016,38(12):2894-2900.
|
| [16] |
王勇,高诗梦,聂肖,等. 基于速度动态差异的位置服务匿名算法[J]. 信息网络安全,2015(4):28-35.
|
| [17] |
张磊,马春光,杨松涛,等. 关联概率不可区分的位置隐私保护方法[J]. 通信学报,2017,38(8):37-49.
|
| [18] |
张磊,马春光,杨松涛,等. 基于属性基加密的用户协作连续查询隐私保护策略[J]. 通信学报,2017,38(9):76-85.
|
| [19] |
ZHANG Lei, LI Jing, YANG Songtao, et al.Privacy Preserving in Cloud Environment for Obstructed Shortest Path Query[J]. Wireless Personal Communications, 2017, 96(2): 2305-2322.
|
| [20] |
周凯,彭长根,何建琼,等. 可证明安全的LBS中连续查询的轨迹隐私保护方案[J]. 信息网络安全,2017(1):43-47.
|
| [21] |
张磊,马春光,杨松涛. 基于位置关联相似性的匿名算法[J]. 中国科技论文,2016,11(2):197-201.
|
| [22] |
PALANISAMY B, LIU Ling.Attack-Resilient Mix-zones over Road Networks: Architecture and Algorithms[J]. IEEE Transactions on Mobile Computing, 2015, 14(3): 495-508.
|
 )
)