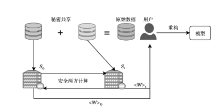
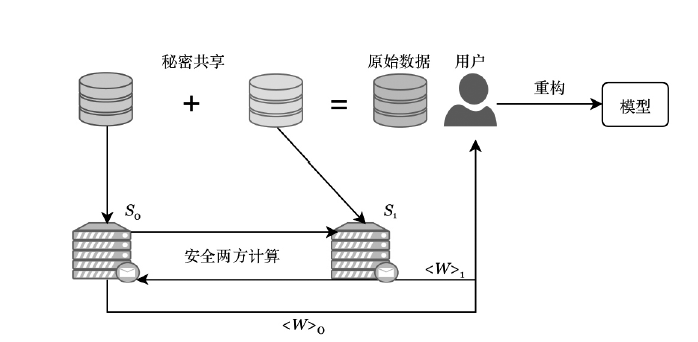
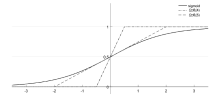
| [1] |
WEN Weiping, WU Bozhi, JIAO Yingnan, et al.Design and Implementation on Malicious Documents Detection Tool Based on Machine Learning[J].Netinfo Security,2018,18(8):1-7.
|
|
文伟平,吴勃志,焦英楠,等.基于机器学习的恶意文档识别工具设计与实现[J].信息网络安全,2018,18(8):1-7.
|
| [2] |
LINDELL Y, PINKAS B.Privacy Preserving Data Mining[J].Journal of Cryptology, 2002,15(3):177-206.
|
| [3] |
MARCHAL S, SAARI K, SINGH N, et al.Know Your Phish: Novel Techniques for Detecting Phishing Sites and Their Targets[C]// IEEE. IEEE 36th International Conference on Distributed Computing Systems, June 27-30, 2016, Nara, Japan. NJ: IEEE, 2016:323-333.
|
| [4] |
GENTRY C.Fully Homomorphic Encryption Using Ideal Lattices[J]. Stoc, 2009, 9(4):169-178.
|
| [5] |
LV Haifeng, DING Yong, DAI Hongyan, et al.Survey on LWE-based Fully Homomorphic Encryption Scheme[J].Netinfo Security, 2015,15(1):32-38.
|
|
吕海峰,丁勇,代洪艳,等.LWE上的全同态加密方案研究[J].信息网络安全,2015,15(1):32-38.
|
| [6] |
DOWLIN N, GILAD-BACHRACH R, LAINE K, et al. CryptoNets: Applying Neural Networks to Encrypted Data with High Throughput and Accuracy[EB/OL].,2018-7-23.
|
| [7] |
XIE Pengtao, BILENKO M, FINLEY T, et al. Crypto-Nets: Neural Networks over Encrypted Data[EB/OL]. .
|
| [8] |
MOHASSEL P, ZHANG Yupeng.SecureML: A System for Scalable Privacy-preserving Machine Learning[C]// IEEE. IEEE Symposium on Security and Privacy, May 22-26, 2017, San Jose, CA, USA. NJ: IEEE, 2017:19-38.
|
| [9] |
WAGH S, GUPTA D, CHANDRAN N. Cryptology ePrint Archive: Report 2018/442[EB/OL].
|
| [10] |
LIU Jian, JUUTI M, LU Yao, et al.Oblivious Neural Network Predictions via MiniONN Transformations[C]// ACM.2017 ACM SIGSAC Conference on Computer and Communications Security, October 30 - November 3, 2017, Dallas, Texas, USA. New York: ACM, 2017:619-631.
|
| [11] |
FENG Dengguo.Security Protocol: Theory and Practice[M]. Beijing: Tsinghua University Press,2011.
|
|
冯登国. 安全协议:理论与实践[M]. 北京:清华大学出版社, 2011.
|
| [12] |
ZHOU Zhihua.Machine Learning[M]. Beijing: Tsinghua University Press,2016.
|
|
周志华. 机器学习[M]. 北京:清华大学出版社, 2016.
|
| [13] |
BEAVER D. Efficient Multiparty Protocols Using Circuit Randomization[EB/OL]. .
|
| [14] |
DEMMLER D, SCHNEIDER T, ZOHNER M.ABY - A Framework for Efficient Mixed-protocol Secure Two-party Computation[J]. NDSS, 2015(2):8-11.
|
| [15] |
CANETTI R.Universally Composable Security: A New Paradigm for Cryptographic Protocols[C]// IEEE. 2001 IEEE International Conference on Cluster Computing, October 14-17, 2001, Las Vegas, Nevada, USA.NJ:IEEE, 2001:136.
|
| [16] |
WANG Xiao, MALOZEMOFF A J, KATZ J. Faster Secure Two-Party Computation in the Single-execution Setting[EB/OL]. .
|
| [17] |
CHEN Li, LIN Bogang.Secure Protocols for Resolving Distributed System of Linear Equations[J].Netinfo Security, 2013,13(9):2-5.
|
|
陈莉,林柏钢.基于分布式线性方程组求解的安全多方计算协议[J].信息网络安全,2013,13(9):2-5.
|