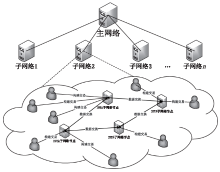
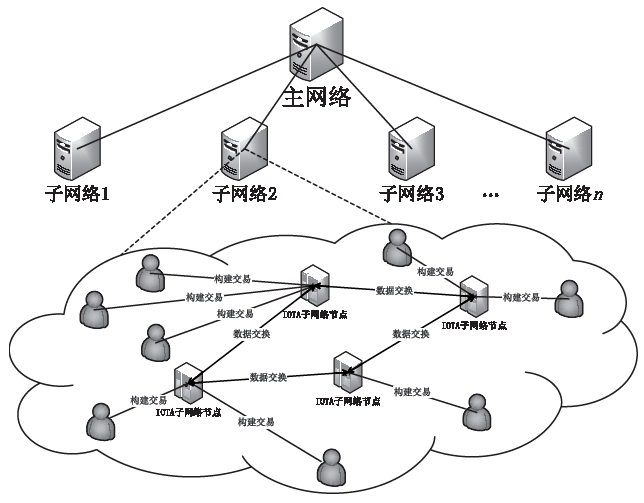
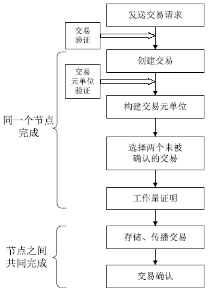
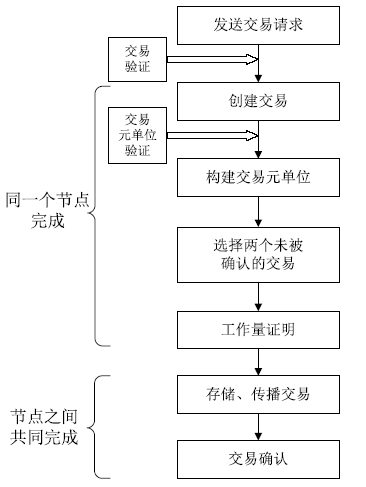
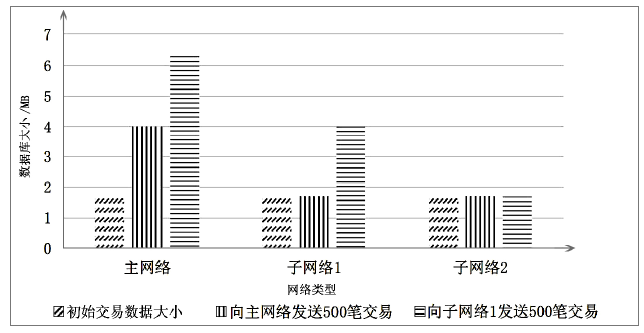
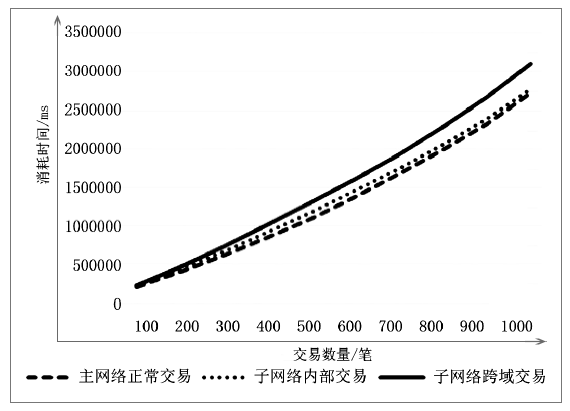
Netinfo Security ›› 2020, Vol. 20 ›› Issue (10): 41-48.doi: 10.3969/j.issn.1671-1122.2020.10.006
Previous Articles Next Articles
An Optimizing Scheme on Multi-domain Collaborative IOTA Blockchain Technology for the Internet of Things
LIU Kaifang( ), FU Shaojing, SU Jinshu, ZHANG Fucheng
), FU Shaojing, SU Jinshu, ZHANG Fucheng
- College of Computer Science, National University of Defence Technology, Changsha 410073, China
-
Received:2020-04-09Online:2020-10-10Published:2020-11-25 -
Contact:LIU Kaifang E-mail:15190228618@163.com
CLC Number:
Cite this article
LIU Kaifang, FU Shaojing, SU Jinshu, ZHANG Fucheng. An Optimizing Scheme on Multi-domain Collaborative IOTA Blockchain Technology for the Internet of Things[J]. Netinfo Security, 2020, 20(10): 41-48.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.10.006
| [1] | DORRI A, KANHERE S S, JURDAK R, et al. Blockchain for IoT Security and Privacy: The Case Study of a Smart Home [C]//IEEE. 2017 IEEE International Conference on Pervasive Computing and Communications Workshops(PerCom Workshops), March 13-17, 2017, Kona, HI, USA. NJ: IEEE, 2017: 618-623. |
| [2] | SHAFAGH H, BURKHALTER L, HITHNAWI A, et al. Towards Blockchain-based Auditable Storage and Sharing of IoT Data [C]//ACM. 2017 ACM SIGSAC Conference on Computer and Communications Security, October 30-November 3, 2017, Dallas, TX, USA. New York: ACM, 2017: 45-50. |
| [3] | WU Zhenquan, LIANG Yuhui, KANG Jiawen, et al. Secure Data Storage and Sharing System Based on Consortium Blockchain in Smart Grid[J]. Journal of Computer Applications, 2017,37(10):2742-2747. |
| 吴振铨, 梁宇辉, 康嘉文, 等. 基于联盟区块链的智能电网数据安全存储与共享系统[J]. 计算机应用, 2017,37(10):2742-2747. | |
| [4] | ZHANG Yajiao, WANG Zong. Application of Blockchain Technology in the Safe Storage of Medical Data[EB/OL]. http://www.paper.edu.cn/releasepaper/content/201612-553, 2016-12-27. |
| 张亚娇, 王枞. 区块链技术在医疗数据安全存储中的应用[EB/OL]. http://www.paper.edu.cn/releasepaper/content/201612-553,2016-12-27. | |
| [5] | POON J, DRYJA T. The Bitcoin Lightning Network: Scalable Off-chain Instant Payments[EB/OL]. https://lightning.network/lightning-network-paper.pdf, 2016-1-14. |
| [6] | CZEPLUCH J S. Raiden Network 1.1.1 Documentation[EB/OL]. https://raiden-network.readthedocs.io/en/stable/, 2020-1-20. |
| [7] | GAO Zhengfeng, ZHENG Jilai, TANG Shuyang, et al. State-of-the-art Survey of Consensus Mechanisms on DAG-based Distributed Ledger[J]. Journal of Software, 2020,31(4):1124-1142. |
| 高政风, 郑继来, 汤舒扬, 等. 基于DAG的分布式账本共识机制研究[J]. 软件学报, 2020,31(4):1124-1142. | |
| [8] | CHAUHAN A, MALVIYA O P, VERMA M, et al. Blockchain and Scalability [C]//IEEE. 2018 IEEE International Conference on Software Quality, Reliability and Security Companion(QRS-C), July 16-20, 2018, Lisbon, Portugal. NJ: IEEE, 2018: 122-128. |
| [9] | DANG H, DINH T T A, LOGHIN D, et al. Towards Scaling Blockchain Systems via Sharding[EB/OL]. https://dl.acm.org/doi/abs/10.1145/3299869.3319889, 2020-1-20. |
| [10] | POPOV S. The Tangle[EB/OL]. http://iotatoken.com/IOTA_Whitepaper.pdf, 2016-7-6. |
| [11] | CHURYUNOV A. A Decentralized System for Storage and Transfer of Value[EB/OL]. , 2017-10-24. |
| [12] | BAIRD L, HARMON M, MADSEN P. Hedera: A Public Hashgraph Network & Governing Council[EB/OL]. https://www.hedera.com/hh-whitepaper-v1.5-190219.pdf, 2019-2-19. |
| [13] | KARGER D, LEHMAN E, LEIGHTON T, et al. Consistent Hashing and Random Trees: Distributed Caching Protocols for Relieving Hot Spots on the World Wide Web [C]//ACM. The twenty-ninth Annual ACM Symposium on Theory of Computing, May 4-6, 1997, El Paso, Texas, USA. New York: ACM, 1997: 654-663. |
| [14] | BUTERIN V. Ethereum Sharding[EB/OL]. https://github.com/ethereum/sharding/blob/develop/docs/doc.md, 2018-5-16. |
| [15] | ZHANG Guochao, WANG Ruijin. Blockchain Shard Storage Model Based on Threshold Secret Sharing[J]. Computer Application, 2019,39(9):2617-2622. |
| 张国潮, 王瑞锦. 基于门限秘密共享的区块链分片存储模型[J]. 计算机应用, 2019,39(9):2617-2622. | |
| [16] | CHEN Zhidong, YU Zhuo, DUAN Zhangbo. et al. Inter-blockchain Communication[EB/OL]. http://dpi-proceedings.com/index.php/dtcse/article/view/12539, 2020-1-20. |
| [17] | LUU L, NARAYANAN V, ZHENG Chaodong, et al. A Secure Sharding Protocol for Open Blockchains [C]//ACM. 2016 ACM SIGSAC Conference on Computer and Communications Security, October 24-28, 2016, Vienna, Austria. New York: ACM, 2016: 17-30. |
| [18] | ZHU Yihai, YAN Jun, TANG Yufei, et al. Joint Substation-Transmission Line Vulnerability Assessment Against the Smart Grid[J]. IEEE Transactions on Information Forensics & Security, 2017,10(5):1010-1024. |
| [19] | TONG Wei, DONG Xuewen, SHEN yulong, et al. A Hierarchical Sharding Protocol for Multi-domain IoT Blockchains [C]//IEEE. 2019 IEEE International Conference on Communications(ICC), May 20-24, 2019, Shanghai, China. NJ: IEEE, 2019: 1-6. |
| [1] | HUO Wei. Research and Thinking on Promoting the Application of Cryptography Fusion [J]. Netinfo Security, 2020, 20(10): 1-5. |
| [2] | HE Jingsha, DU Jinhui, ZHU Nafei. Research on k-anonymity Algorithm for Personalized Quasi-identifier Attributes [J]. Netinfo Security, 2020, 20(10): 19-26. |
| [3] | LIU Yi, LI Jianhua, CHEN Yu, QI Zisen. A Shared Protection Algorithm for Data Center Network Nodes [J]. Netinfo Security, 2020, 20(10): 27-33. |
| [4] | HUANG Baohua, CHENG Qi, YUAN Hong, HUANG Pirong. K-means Clustering Algorithm Based on Differential Privacy with Distance and Sum of Square Error [J]. Netinfo Security, 2020, 20(10): 34-40. |
| [5] | PENG Ruyue, MA Zhaofeng, LUO Shoushan. Research and Implementation of Digital Content Service and Security Supervision Technology Based on Blockchain [J]. Netinfo Security, 2020, 20(10): 49-56. |
| [6] | WANG Kai, GUO Pengfei, ZHOU Cong, YAN Yingjian. Research on the Assessment Method of Side Channel Information Leakage Based on t-test [J]. Netinfo Security, 2020, 20(10): 57-66. |
| [7] | GUO Rui, CHEN Yushuang, ZHENG Dong. A Blockchain-based Efficient Certificateless Aggregate Signature Scheme for Wireless Medical Sensor Networks [J]. Netinfo Security, 2020, 20(10): 6-18. |
| [8] | GU Zhaojun, HAO Jintao, ZHOU Jingxian. Classification of Malicious Network Traffic Based on Improved Bilinear Convolutional Neural Network [J]. Netinfo Security, 2020, 20(10): 67-74. |
| [9] | WANG Yudi, LIU Xiaojie, WANG Yunpeng. Research on Anomaly Detection Method Based on Improved Negative Selection Algorithm [J]. Netinfo Security, 2020, 20(10): 75-82. |
| [10] | LIU Yuan, SUN Chen, ZHANG Yanling. A Zero Trust Network Research Based on Overlay Technology [J]. Netinfo Security, 2020, 20(10): 83-91. |
| [11] | LI Yu, HAN Yiliang, LI Zhe, ZHU Shuaishuai. A Post Quantum Authenticated Key Exchange Protocol Based on LWE [J]. Netinfo Security, 2020, 20(10): 92-99. |
| [12] | LU Jiali. Log Anomaly Detection Method Based on Improved Time Series Model [J]. Netinfo Security, 2020, 20(9): 1-5. |
| [13] | SHEN Jinwei, ZHAO Yi, LIANG Chunlin, ZHANG Ping. RFID Group Tag Ownership Transfer Protocol Based on Cyclic Grouping Function [J]. Netinfo Security, 2020, 20(9): 102-106. |
| [14] | ZHOU Zhining, WANG Binjun, ZHAI Yiming, TONG Xin. Spam Filtering Model Based on ALBERT Dynamic Word Vector [J]. Netinfo Security, 2020, 20(9): 107-111. |
| [15] | HAN Lei, CHEN Wuping, ZENG Zhiqiang, ZENG Yingming. Research on Hierarchical Network Structure and Application of Blockchain [J]. Netinfo Security, 2020, 20(9): 112-116. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||