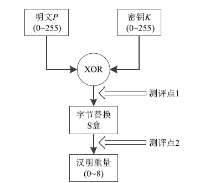
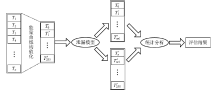
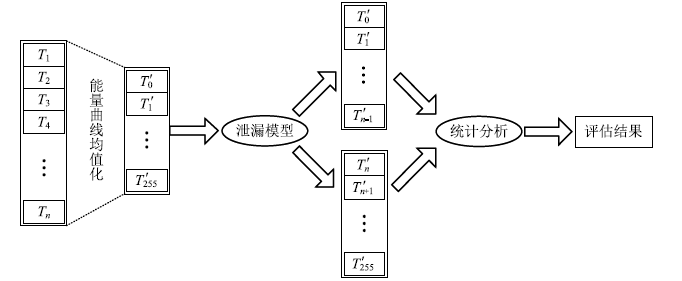
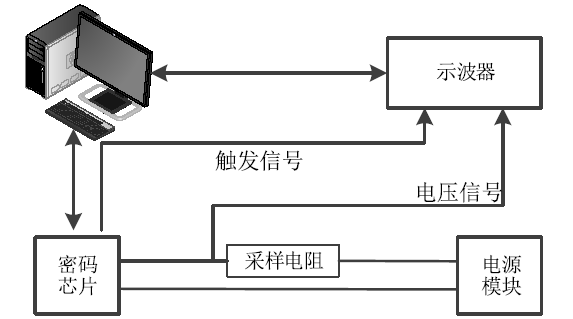
Netinfo Security ›› 2020, Vol. 20 ›› Issue (10): 57-66.doi: 10.3969/j.issn.1671-1122.2020.10.008
Previous Articles Next Articles
Research on the Assessment Method of Side Channel Information Leakage Based on t-test
WANG Kai1( ), GUO Pengfei1, ZHOU Cong2, YAN Yingjian1
), GUO Pengfei1, ZHOU Cong2, YAN Yingjian1
- 1. PLA Strategic Support Force Information Engineering University, Zhengzhou 450001, China
2. The Logistics Departments of the PLA Rocket Force, Beijing 100085, China
-
Received:2020-06-15Online:2020-10-10Published:2020-11-25 -
Contact:WANG Kai E-mail:yixiwk@163.com
CLC Number:
Cite this article
WANG Kai, GUO Pengfei, ZHOU Cong, YAN Yingjian. Research on the Assessment Method of Side Channel Information Leakage Based on t-test[J]. Netinfo Security, 2020, 20(10): 57-66.
share this article
| 类型Ⅰ | 类型Ⅱ | 类型Ⅲ | 类型Ⅳ | |
|---|---|---|---|---|
| 字节0 | 27.67 | 13.13 | 20.05 | 18.46 |
| 字节1 | 27.57 | 8.02 | 18.77 | 19.61 |
| 字节2 | 24.58 | 8.88 | 18.99 | 20.14 |
| 字节3 | 27.11 | 8.30 | 19.71 | 20.61 |
| 字节4 | 25.89 | 6.38 | 18.86 | 17.56 |
| 字节5 | 27.79 | 8.13 | 17.43 | 20.21 |
| 字节6 | 24.49 | 7.05 | 17.68 | 20.81 |
| 字节7 | 26.45 | 7.22 | 20.36 | 20.12 |
| 字节8 | 25.61 | 6.70 | 19.00 | 18.12 |
| 字节9 | 28.06 | 7.81 | 17.84 | 19.89 |
| 字节10 | 23.87 | 6.91 | 18.03 | 20.91 |
| 字节11 | 28.15 | 7.90 | 18.47 | 19.88 |
| 字节12 | 15.28 | 6.05 | 18.59 | 17.74 |
| 字节13 | 14.67 | 7.78 | 19.08 | 20.18 |
| 字节14 | 17.87 | 6.64 | 17.81 | 20.54 |
| 字节15 | 21.72 | 18.34 | 18.35 | 19.64 |
| 类型Ⅰ | 类型Ⅱ | 类型Ⅲ | 类型Ⅳ | |
|---|---|---|---|---|
| 字节0 | 3.64 | 4.00 | 3.81 | 3.09 |
| 字节1 | 3.33 | 3.25 | 3.34 | 3.84 |
| 字节2 | 3.87 | 3.83 | 3.85 | 3.85 |
| 字节3 | 3.49 | 3.53 | 3.30 | 3.61 |
| 字节4 | 4.04 | 3.46 | 3.85 | 3.63 |
| 字节5 | 3.85 | 3.79 | 3.82 | 3.66 |
| 字节6 | 3.86 | 3.97 | 3.13 | 3.47 |
| 字节7 | 3.82 | 3.18 | 3.27 | 3.43 |
| 字节8 | 3.28 | 3.18 | 2.91 | 3.38 |
| 字节9 | 3.35 | 2.84 | 3.67 | 3.22 |
| 字节10 | 3.58 | 3.95 | 3.86 | 3.83 |
| 字节11 | 4.15 | 3.27 | 3.23 | 3.22 |
| 字节12 | 3.21 | 3.50 | 3.34 | 3.23 |
| 字节13 | 3.38 | 3.85 | 4.44 | 3.95 |
| 字节14 | 3.47 | 3.82 | 3.83 | 3.30 |
| 字节15 | 3.21 | 3.53 | 3.58 | 3.79 |
| [1] | KOCHER P, JAFFE J, JUN B. Differential Power Analysis [C]//CRYPTO’99. Advances in Cryptology—CRYPTO’99, August 15-19, 1999, Santa Barbara, California, USA. Berlin: Springer, 1999: 786-789. |
| [2] | BRIER E, CLAVIER C, OLIVIER F. Correlation Power Analysis with A Leakage Model [C]// Springer. 6th International Workshop on Cryptographic Hardware and Embedded Systems, August 11-13, 2004, MA, USA. Berlin: Springer, 2004: 16-29. |
| [3] | CHARI S, RAO J R, ROHATGI P. Template attacks [C]// Springer. 4th International Workshop on Cryptographic Hardware and Embedded Systems, August 13-15, 2002, Redwood Shores, CA, USA. Berlin: Springer, 2003: 13-28. |
| [4] | BIRYUKOV A, BOGDANOV A, KHOVRATOVICH D, et al. Collision Attacks on AES-Based MAC: Alpha-MAC [C]//Springer. 9th International Workshop on Cryptographic Hardware and Embedded Systems, September 10-13, 2007, Vienna, Austria. Berlin: Springer, 2007: 166-180. |
| [5] | GIERLICHS B, BATINA L, TUYLS P, et al. Mutual Information Analysis [C]//Springer. 10th International Workshop on Cryptographic Hardware and Embedded Systems, August 10-13, 2008, Washington, DC, USA. Berlin: Springer, 2008: 426-442. |
| [6] | BIHAM E, SHAMIR A. Power Analysis of the Key Scheduling of the AES Candidates[EB/OL]. https://www.researchgate.net/publication/239666203_Power_Analysis_of_the_Key_Scheduling_of_the_AES_Canditates, 2020-4-30. |
| [7] | FIPS PUB 140-2. Security Requirements for Cryptographic Modules[EB/OL]. http://csrc.nist.gov/publications/fips/fips140-2/fips 1402.pdf, 2020-4-30. |
| [8] | ASAHIKO Y. A Generalization of ISO/IEC 24761 to Enhance Remote Authentication with Trusted Product at Claimant[M]. Morocco: ICT Systems Security and Privacy Protection, 2016. |
| [9] | GM/T 0028-2014. Security Requirements for Cryptographic Modules[EB/OL]. http://www.gmbz.org.cn/main/viewfile/2018011 0021846184575.html, 2020-4-30. |
| GM/T 0028-2014. 密码模块安全技术要求[EB/OL]. http://www.gmbz. org.cn/main/viewfile/20180110021846184575.html,2020-4-30. | |
| [10] | GOODWILL G, JUN B, JAFFE J, et al. A Testing Methodology for Side Channel Resistance Validations[EB/OL]. https://www.rambus.com/wp-content/uploads/2015/08/a-testing-methodology-for-side-channel-resistance-validation.pdf, 2020-4-30. |
| [11] | BECKER G, COOPER J, DEMULDER E, et al. Test Vector Leakage Assessment(TVLA) Methodology in Practice[EB/OL]. http://pdfs.semanticscholar.org/a10f/31018c9ce38a5231b6481a8f9d4881bca64c.pdf, 2020-4-30. |
| [12] | SCHNEIDER T, MORADI A. Leakage Assessment Methodology [C]//Springer. 17th International Workshop on Cryptographic Hardware and Embedded Systems, September 13-16, 2015, Saint-Malo, France. Berlin: Springer, 2015: 495-513. |
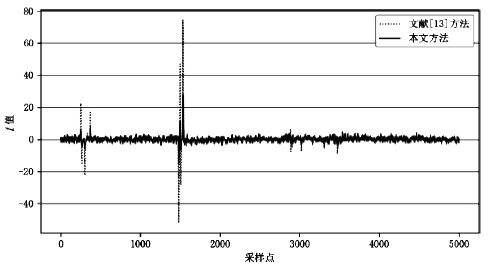
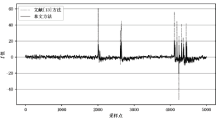
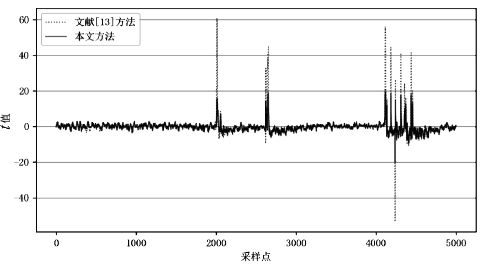
| [13] | CHEN Jiahe, LI Hexin, WANG Yanan, et al. Evaluating Side-Channel Information Leakage in 3DES using the t-test[J]. Journal of Tsinghua University (Science and Technology), 2016,65(5):499-503. |
| 陈佳哲, 李贺鑫, 王亚楠, 等. 运用t检验评估3DES算法的侧信道信息泄漏[J]. 清华大学学报(自然科学版), 2016,56(5):499-503. | |
| [14] | MATHER L, OSWALD E, BANDENBURG J, et al. Does My Device Leak Information? An Priori Statistical Power Analysis of Leakage Detection Tests [C]//Springer. 19th International Conference on the Theory and Application of Cryptology and Information Security, December 1-5, 2013, Bengaluru, India. Berlin: Springer, 2013: 486-505. |
| [15] | JOURNANLT A, STANDAERT F X. Very High Order Masking: Efficient Implementation and Security Evaluation [C]//Springer. 19th International Conference on Cryptographic Hardware and Embedded Systems, September 25-28, 2017, Taipei, China. Berlin: Springer, 2017: 623-643. |
| [16] | WEGENER F, MORADI A. A First-Order SCA Resistant AES without Fresh Randomness [C]//COSADE. 9th International Workshop on Constructive Side-Channel Analysis and Secure Design, April 23-24, 2018, Singapore. Berlin: Springer, 2018: 245-262. |
| [17] | BHATTACHARYA S, BHASIN S, MUKHOPADHYAY D. Online Detection and Reactive Countermeasure for Leakage from BPU Using TVLA [C]//IEEE. 2018 31st International Conference on VLSI Design and 2018 17th International Conference on Embedded Systems (VLSID), January 6-10, 2018, Pune, India. New York: IEEE, 2018: 155-160. |
| [18] | DIEHL W, ABDULGADIR A, FARAHMAND F, et al. Comparison of Cost of Protection Against Differential Power Analysis of Selected Authenticated Ciphers [C]//IEEE. IEEE International Symposium on Hardware Oriented Security and Trust(HOST), April 30-May 4, 2018, Washington DC, USA. New York: IEEE, 2018: 147-152. |
| [19] | LU Fuxiang, LI Weijian, HUANG Xian. Research on Optimization of Side Channel Leakage Assessment Based on Paired t Test[J]. Journal of Chinese Computer Systems. 2019,40(12):2585-2590. |
| 鹿福祥, 李伟键, 黄娴. 基于配对t检验的侧信道泄漏评估优化研究[J]. 小型微型计算机系统, 2019,40(12):2585-2590. | |
| [20] | ZHANG Zhijun, WANG Lei, SHEN Yang. Cryptographic Security Assessment of Radio and Television Intelligent Terminal Chip Based on T-test[J]. Radio & TV Broadcast Engineering. 2020,47(1):94-98. |
| 张智军, 王磊, 沈阳. 基于T检验的广电智能终端芯片密码安全评估[J]. 广播与电视技术, 2020,47(1):94-98. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||