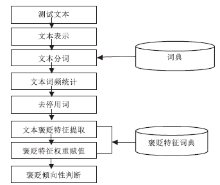
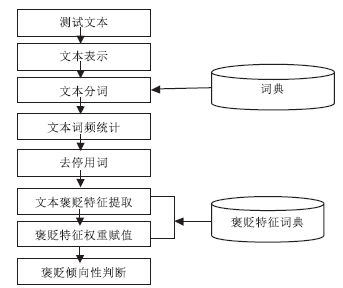
Netinfo Security ›› 2014, Vol. 14 ›› Issue (11): 30-35.doi: 10.3969/j.issn.1671-1122.2014.11.005
• Orginal Article • Previous Articles Next Articles
Research on Chinese Text Appraisive Classification in the Present Era of Big Data
ZENG Fan-feng, ZHU Wan-shan( ), WANG Jing-zhong
), WANG Jing-zhong
- College of Information Engineering of North China University of Technology, Beijing 100144, China
-
Received:2014-09-28Online:2014-11-01Published:2020-05-18
CLC Number:
Cite this article
ZENG Fan-feng, ZHU Wan-shan, WANG Jing-zhong. Research on Chinese Text Appraisive Classification in the Present Era of Big Data[J]. Netinfo Security, 2014, 14(11): 30-35.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2014.11.005
| [1] | 陶县俊.情感Ontology构建及其网络舆情文本倾向分析[D].新乡:河南师范大学,2009. |
| [2] | Tumey Peter.Thumbs Up or Thumbs Down? Semantic Orientation Applied to Unsupervised Classification of Reviews[C]//Proceedings of the 40th Annual Meeting of the Association for Computational Linguistics, 2002:417-424. |
| [3] | Kamps J,Marx M, Mokken R J, ea al. Using WordNet to measure semantic orientation of adjectives[C]//Proceedings of LREC-04,4th International Conference on Language Resources and Evaluation,Lisbon, 2004: 1115-1118. |
| [4] | Pang B, Lee L.Seeing Stars: Exploiting Class Relationships for Sentiment Categorization with Respect to Rating Scales[C]//Proceedings of the Association for Computational Linguistics(ACL), 2005:115-124. |
| [5] | Yu H, Hatzivassiloglou V.Towards Answering Opinion Questions: Separating Facts from Opinions and Identifying the Polarity of Opinion Sentences[C]//M. Collins and M. Steedman (eds): Proceed of EMNLP-03. 8th Conference on Empirical Methods in Natural Language Processing . Sapporo. Japan, 2003: 129-136. |
| [6] | Sista S P, Srinicasan S H.Polarized lexicon for review classification[C]//Proceedings of ICAI-04,the International Conference on Artificial Intelligence. Las Vegas, USA, CSREA Press, 2004:867-872. |
| [7] | Fei Zhongchao, Liu Jian, Wu Gengfeng.Sentiment Classification Using Phrase Pattens[C]//The Fourth Intemational Confereneeon Computerand Information Technology,2004:1147-1157. |
| [8] | 朱嫣岚,闵锦,周雅倩,等.基于HowNet 的词汇语义倾向计算[J].中文信息学报,2006,20(1):14-20. |
| [9] | Turney P.Thumbs Up or Thumbs Down? Semantic Orientation Applied to Unsupervised Classification of Reviews[C]//Proc. of the Meeting of the Association for Computational Linguistics (ACL'02), 2002:417-424. |
| [10] | Qiang Ye, Wen Shi, Yijun Li.Sentiment Classification for Movie Reviews in Chinese by Improved Semantic Oriented Approach[C]//Proceedings of the 39th Hawaii International Conference on System Sciences, 2006. |
| [11] | Hu M, Liu B, Mining and Summary Customer Reviews[C]//KDD'04, 2004. |
| [12] | Bin Shi, Kuiyu Chang.Mining Chinese Reviews[C]//Sixth IEEE International Conference on Data Mining-Workshops(ICDMW'06),2006. |
| [13] | 路斌,万小军,杨建武,等.基于同义词词林的词汇褒贬计算[C]//Proceedings of the 7th International Conference on Chinese Computing, wuhan,2007:17-23. |
| [14] | 徐琳宏,林鸿飞,杨志豪.基于语义理解的文本倾向性识别机制[J]. 中文信息学报,2007,21(1):96-100. |
| [15] | Wei Wei,Liu Hongyan,He Jun,ea al.Extracting Feature and Opinion Words Effectively from Chinese Product Reviews[C]//Proceedings of the fifth International Conference on Fuzzy Systems and Konwledge Discovery FSKD,2008. |
| [16] | Changli Zhang, Wanli Zuo, Tao Peng, et al.Sentiment Classification for Chinese Reviews Using Machine Learning Methods Based on String Kernel[C]//Third 2008 International Conference on Convergence and Hybrid Information Technology,2008. |
| [17] | Kim S M, Hovy E.Automatic Detection of Opinion Bearing words and Sentences[C]//The Second International Joint Conference on Natral Language Processing.Jeju Island, KR, 2005:61-66. |
| [18] | Salton G,Wong A,Yang C S.A Vector Space Model for Auto-matic Indexing[J].Communications of the ACM,1975,18(5):613-620. |
| [19] | 朱颖东,钟勇.一种新的基于多启发的特征选择方法[J].计算机应用,2009,29(3):849-851. |
| [20] | 李荣陆. 文本分类及相关技术研究[D].上海:复旦大学,2005. |
| [21] | 尚文倩. 文本分类及其相关技术研究[D].北京:北京交通大学,2007. |
| [22] | 吴鹏. 支持向量机文本分类算法的研究及其应用[D].大连:大连理工大学,2009. |
| [1] | HUANG Wangwang, ZHOU Hua, WANG Daiqiang, ZHAO Qi. Design of Reconfigurable Key Security Authentication Protocol for IoT Based on National Cryptography SM9 [J]. Netinfo Security, 2024, 24(7): 1006-1014. |
| [2] | ZHANG Xiaojun, ZHANG Nan, HAO Yunpu, WANG Zhouyang, XUE Jingting. Three-Factor Authentication and Key Agreement Protocol Based on Chaotic Map for Industrial Internet of Things Systems [J]. Netinfo Security, 2024, 24(7): 1015-1026. |
| [3] | ZHANG Jiwei, WANG Wenjun, NIU Shaozhang, GUO Xiangkuo. Blockchain Scaling Solutions: ZK-Rollup Review [J]. Netinfo Security, 2024, 24(7): 1027-1037. |
| [4] | ZHANG Liqiang, LU Mengjun, YAN Fei. A Cross-Contract Fuzzing Scheme Based on Function Dependencies [J]. Netinfo Security, 2024, 24(7): 1038-1049. |
| [5] | DONG Yunyun, ZHU Yuling, YAO Shaowen. High-Quality Full-Size Image Steganography Method Based on Improved U-Net and Hybrid Attention Mechanism [J]. Netinfo Security, 2024, 24(7): 1050-1061. |
| [6] | ZHOU Shucheng, LI Yang, LI Chuanrong, GUO Lulu, JIA Xinhong, YANG Xinghua. Context-Based Abnormal Root Cause Algorithm [J]. Netinfo Security, 2024, 24(7): 1062-1075. |
| [7] | REN Changyu, ZHANG Ling, JI Hangyuan, YANG Liqun. Research on TTP Extraction Method Based on Pre-Trained Language Model and Chinese-English Threat Intelligence [J]. Netinfo Security, 2024, 24(7): 1076-1087. |
| [8] | CAI Manchun, XI Rongkang, ZHU Yi, ZHAO Zhongbin. A Fingerprint Identification Method of Multi-Page and Multi-Tag Targeting Tor Website [J]. Netinfo Security, 2024, 24(7): 1088-1097. |
| [9] | XIANG Hui, XUE Yunhao, HAO Lingxin. Large Language Model-Generated Text Detection Based on Linguistic Feature Ensemble Learning [J]. Netinfo Security, 2024, 24(7): 1098-1109. |
| [10] | SHEN Xiuyu, JI Weifeng. Optimization of Cost of Edge-Cloud Collaborative Computing Offloading Considering Security [J]. Netinfo Security, 2024, 24(7): 1110-1121. |
| [11] | ZHAO Xinqiang, FAN Bo, ZHANG Dongju. Research on APT Attack Defense System Based on Threat Discovery [J]. Netinfo Security, 2024, 24(7): 1122-1128. |
| [12] | WEN Wen, LIU Qinju, KUANG Lin, REN Xuejing. Research and Scheme Design of Cyber Threat Intelligence Sharing under Privacy Protection System [J]. Netinfo Security, 2024, 24(7): 1129-1137. |
| [13] | LIU Yidan, MA Yongliu, DU Yibin, CHENG Qingfeng. A Certificateless Anonymous Authentication Key Agreement Protocol for VANET [J]. Netinfo Security, 2024, 24(7): 983-992. |
| [14] | LUO Ming, ZHAN Qibang, QIU Minrong. A Heterogeneous Cross-Domain Conditional Privacy Protection Ring Signcryption Scheme for V2I Communication [J]. Netinfo Security, 2024, 24(7): 993-1005. |
| [15] | LI Zengpeng, WANG Siyang, WANG Mei. Research of Privacy-Preserving Proximity Test [J]. Netinfo Security, 2024, 24(6): 817-830. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||