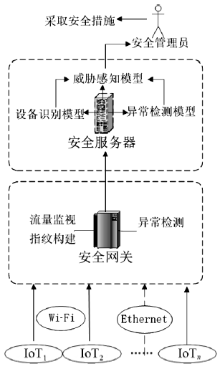
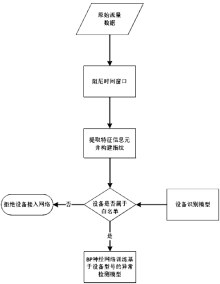
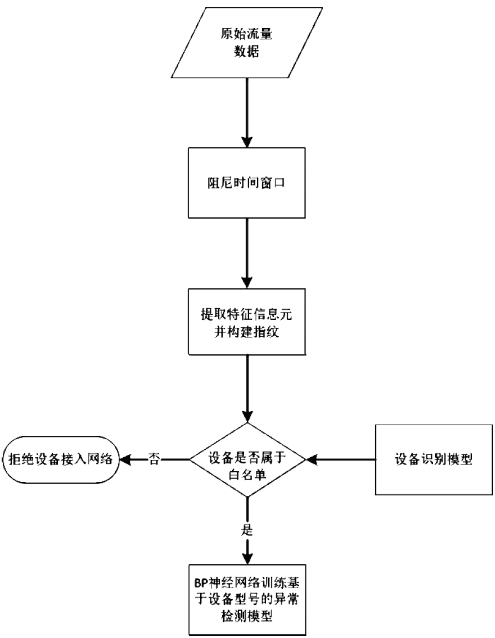
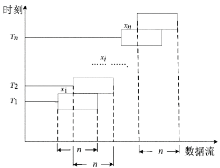
| [1] |
HOWELL J. Number of Connected IoT Devices will Surge to 125 Billion by 2030[EB/OL]. , 2018-11-7/2019-7-15.
|
| [2] |
CALERO. 3 Ways the Internet of Things will Impact Enterprise Security[EB/OL]. , 2018-6-17/2019-7-15.
|
| [3] |
STANKOVIC J A.Research Directions for the Internet of Things[J]. IEEE Internet of Things Journal, 2014, 3(1): 3-9.
|
| [4] |
KOLIAS C, KAMBOURAKIS G, STAVROU A, et al.DDoS in the IoT: Mirai and Other Botnets[J]. Computer, 2017, 50(7): 80-84.
|
| [5] |
HOQUE N, BHATTACHARYYA D K, KALITA J K, et al.Botnet in DDoS Attacks: Trends and Challenges[J]. IEEE Communications Surveys & Tutorials, 2015, 17(4): 2242-2270.
|
| [6] |
AHMED M, MAHMOOD A N, HU J,et al.A Survey of Network Anomaly Detection Techniques[J]. Journal of Network and Computer Applications, 2016, 60(5): 19-31.
|
| [7] |
NGUYEN T D, MARCHAL S, MIETTINEN M, et al.Diot: A Crowdsourced Self-learning Approach for Detecting Compromised IoT Devices[J]. arXiv preprint, 2018, 18(4): 13-19.
|
| [8] |
APTHORPE N, REISMAN D, FEAMSTER N.A Smart Home is no Castle: Privacy Vulnerabilities of Encrypted IoT Traffic[J]. arXiv preprint, 2017, 17(5): 6-11.
|
| [9] |
DOSHI R, APTHORPE N, FEAMSTER N.Machine Learning DDoS Detection for Consumer Internet of Things Devices[C]//IEEE. 2018 IEEE Security and Privacy Workshops(SPW), Auguest 11-15, 2018, Los Angeles, USA. New York: IEEE, 2018: 29-35.
|
| [10] |
HAFEEZ I, ANTIKAINEN M, DING A Y, et al.IoT-KEEPER: Securing IoT Communications in Edge Networks[J]. arXiv preprint, 2018, 18(10): 84-95.
|
| [11] |
MCMAHAN H B, MOORE E, RAMAGE D, et al.Communication-efficient Learning of Deep Networks from Decentralized Data[J]. preprint, 2016, 16(2): 16-29.
|
| [12] |
MIRSKY Y, DOITSHMAN T, ELOVICI Y, et al.Kitsune: An Ensemble of Autoencoders for Online Network Intrusion Detection[J]. arXiv preprint, 2018, 18(2): 90-99.
|
| [13] |
MO Yun.Research on Location Fingerprint Indoor Location Method Based on Spatial Partitioning and Dimensionality Reduction Technology[D]. Harbin: Harbin Institute of Technology, 2016.
|
|
莫云. 基于空间分区与降维技术的位置指纹室内定位方法研究[D].哈尔滨:哈尔滨工业大学,2016.
|
| [14] |
WANG Tao, ZHANG Lisha, GAO Yan.Diagnosis of the Abnormal State of Long-span Arch Bridge Based on BP Neural Network Improved Novel Detection Technology[J]. Journal of Beijing Institute of Technology, 2016, 36(2): 157-162.
|
|
王涛,张丽莎,高岩.基于BP神经网络的改进型新奇检测技术诊断大跨度拱桥异常状态[J].北京理工大学学报,2016,36(2):157-162.
|
| [15] |
BREIMAN L.Random Forests[J]. Machine Learning, 2001, 45(1): 5-32.
|
| [16] |
GAO S, ZHANG H, ZHENG X, et al.Improving SVM Classifiers with Link Structure for Web Spam Detection[J]. Journal of Computational Information Systems, 2014, 10(6): 2435-2443.
|
| [17] |
MEIDAN Y, BOHADANA M, MATHOV Y, et al.N-BaIoT—Network-based Detection of IoT Botnet Attacks Using Deep Autoencoders[J]. IEEE Pervasive Computing, 2018, 17(3): 12-22.
|
| [18] |
SHI W, CAO J, ZHANG Q, et al.Edge Computing: Vision and Challenges[J]. IEEE Internet of Things Journal, 2016, 3(5): 637-646.
|
| [19] |
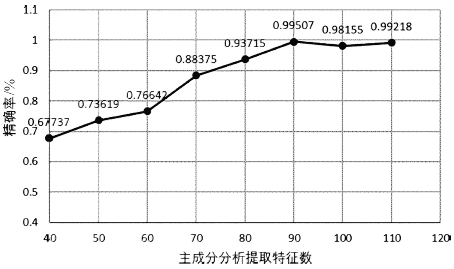
JOLLIFFE I T, CADIMA J.Principal Component Analysis: A Review and Recent Developments[J]. Philosophical Transactions of the Royal Society A: Mathematical, Physical and Engineering Sciences, 2016, 374(5): 29-37.
|
| [20] |
APTHORPE N, REISMAN D, SUNDARESAN S, et al.Spying on the Smart Home: Privacy Attacks and Defenses on Encrypted IoT Traffic[J]. arXiv preprint, 2017, 17(8): 44-50.
|
 ), Yuanbo GUO, Ya ZHONG, Shuaihui ZHEN
), Yuanbo GUO, Ya ZHONG, Shuaihui ZHEN