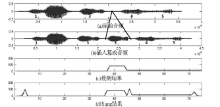
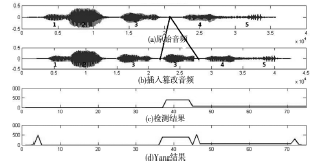
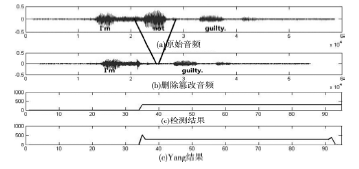
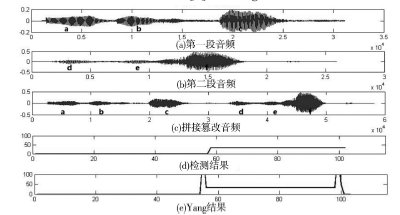
Netinfo Security ›› 2014, Vol. 14 ›› Issue (10): 7-10.doi: 10.3969/j.issn.1671-1122.2014.10.002
Previous Articles Next Articles
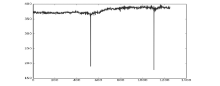
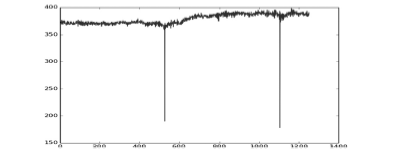
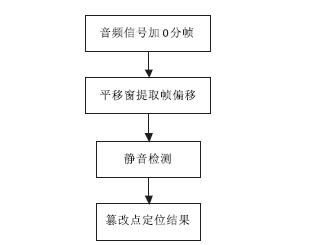
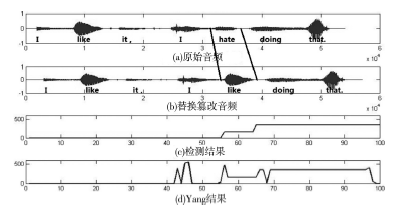
An Improved Method of MP3 Passive Forgery Detection
YANG Jing, FAN Meng-di, GAO Xiong-zhi, REN Yan-zhen
- Computer Department of Wuhan University, Wuhan Hubei 430072, China
-
Received:2014-08-03Online:2014-10-01Published:2015-08-17
CLC Number:
Cite this article
YANG Jing, FAN Meng-di, GAO Xiong-zhi, REN Yan-zhen. An Improved Method of MP3 Passive Forgery Detection[J]. Netinfo Security, 2014, 14(10): 7-10.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2014.10.002
| [1] | Yang R, Shi Y Q, Huang J.Detecting double compression of audio signal[C]//IS&T/SPIE Electronic Imaging. International Society for Optics and Photonics, 2010. |
| [2] | Bianchi T, De Rosa A, Fontani M, et al.Detection and classification of double compressed MP3 audio tracks[C]//Proceedings of the first ACM workshop on Information hiding and multimedia security .ACM, 2013: 159-164. |
| [3] | Liu, Qingzhong,Sung, Andrew H,Qiao, Mengyu.Detection of Double MP3 Compression , Cognitive Computation, 2010,2(4):291-296. |
| [4] | 高阳. 数字音频材料的真实性检测[D]. 上海: 上海交通大学, 2008. |
| [5] | J.R Chen, S.J Xiang.Exposing Digital Audio Forgeries in Time Domain by Using Singularity Analysis with Wavelets[C]//Proc of the first ACM workshop on Information hiding and multimedia security. New York, USA,2013: 149-158. |
| [6] | Xunyu Pan, Xing Zhang, Siwei Lyu.Detecting splicing in digital audios using local noise level estimation[C]//ICASSP 2012: 1841-1844. |
| [7] | Yang R, Qu Z, Huang J.Exposing MP3 audio forgeries using frame offsets[J]. ACM Transactions on Multimedia Computing, Communications, and Applications (TOMCCAP), 2012, 8(2S): 35. |
| [8] | Yang R, Shi Y Q, Huang J.Detecting double compression of audio signal[C]//IS&T/SPIE Electronic Imaging. International Society for Optics and Photonics, 2010. |
| [9] | Softonic软件天堂.Cool Edit Pro 2.1[EB/OL].. |
| [10] | 西西软件园.hi-q recorder [EB/OL].. |
| [11] | 卓乐网.sound recorder [EB/OL].. |
| [1] | HUANG Wangwang, ZHOU Hua, WANG Daiqiang, ZHAO Qi. Design of Reconfigurable Key Security Authentication Protocol for IoT Based on National Cryptography SM9 [J]. Netinfo Security, 2024, 24(7): 1006-1014. |
| [2] | ZHANG Xiaojun, ZHANG Nan, HAO Yunpu, WANG Zhouyang, XUE Jingting. Three-Factor Authentication and Key Agreement Protocol Based on Chaotic Map for Industrial Internet of Things Systems [J]. Netinfo Security, 2024, 24(7): 1015-1026. |
| [3] | ZHANG Jiwei, WANG Wenjun, NIU Shaozhang, GUO Xiangkuo. Blockchain Scaling Solutions: ZK-Rollup Review [J]. Netinfo Security, 2024, 24(7): 1027-1037. |
| [4] | ZHANG Liqiang, LU Mengjun, YAN Fei. A Cross-Contract Fuzzing Scheme Based on Function Dependencies [J]. Netinfo Security, 2024, 24(7): 1038-1049. |
| [5] | DONG Yunyun, ZHU Yuling, YAO Shaowen. High-Quality Full-Size Image Steganography Method Based on Improved U-Net and Hybrid Attention Mechanism [J]. Netinfo Security, 2024, 24(7): 1050-1061. |
| [6] | ZHOU Shucheng, LI Yang, LI Chuanrong, GUO Lulu, JIA Xinhong, YANG Xinghua. Context-Based Abnormal Root Cause Algorithm [J]. Netinfo Security, 2024, 24(7): 1062-1075. |
| [7] | REN Changyu, ZHANG Ling, JI Hangyuan, YANG Liqun. Research on TTP Extraction Method Based on Pre-Trained Language Model and Chinese-English Threat Intelligence [J]. Netinfo Security, 2024, 24(7): 1076-1087. |
| [8] | CAI Manchun, XI Rongkang, ZHU Yi, ZHAO Zhongbin. A Fingerprint Identification Method of Multi-Page and Multi-Tag Targeting Tor Website [J]. Netinfo Security, 2024, 24(7): 1088-1097. |
| [9] | XIANG Hui, XUE Yunhao, HAO Lingxin. Large Language Model-Generated Text Detection Based on Linguistic Feature Ensemble Learning [J]. Netinfo Security, 2024, 24(7): 1098-1109. |
| [10] | SHEN Xiuyu, JI Weifeng. Optimization of Cost of Edge-Cloud Collaborative Computing Offloading Considering Security [J]. Netinfo Security, 2024, 24(7): 1110-1121. |
| [11] | ZHAO Xinqiang, FAN Bo, ZHANG Dongju. Research on APT Attack Defense System Based on Threat Discovery [J]. Netinfo Security, 2024, 24(7): 1122-1128. |
| [12] | WEN Wen, LIU Qinju, KUANG Lin, REN Xuejing. Research and Scheme Design of Cyber Threat Intelligence Sharing under Privacy Protection System [J]. Netinfo Security, 2024, 24(7): 1129-1137. |
| [13] | LIU Yidan, MA Yongliu, DU Yibin, CHENG Qingfeng. A Certificateless Anonymous Authentication Key Agreement Protocol for VANET [J]. Netinfo Security, 2024, 24(7): 983-992. |
| [14] | LUO Ming, ZHAN Qibang, QIU Minrong. A Heterogeneous Cross-Domain Conditional Privacy Protection Ring Signcryption Scheme for V2I Communication [J]. Netinfo Security, 2024, 24(7): 993-1005. |
| [15] | LI Zengpeng, WANG Siyang, WANG Mei. Research of Privacy-Preserving Proximity Test [J]. Netinfo Security, 2024, 24(6): 817-830. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||