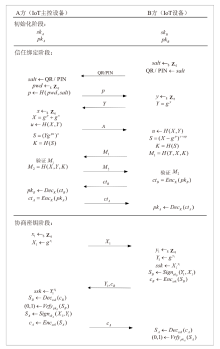
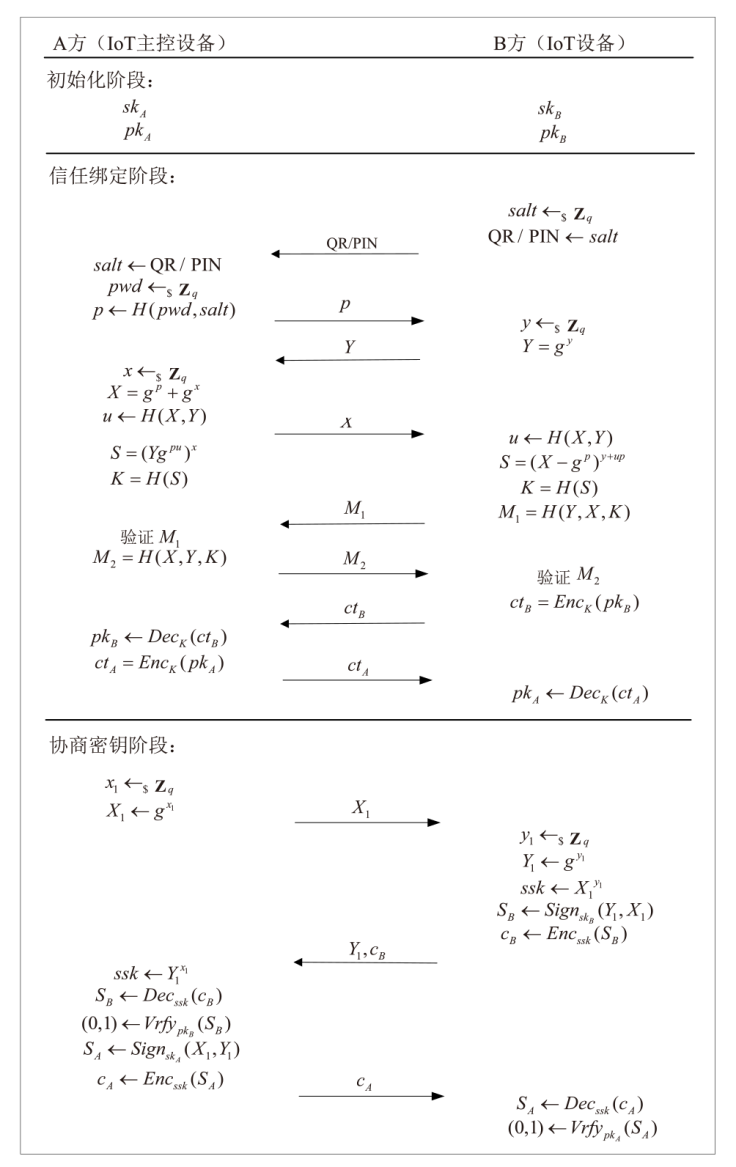
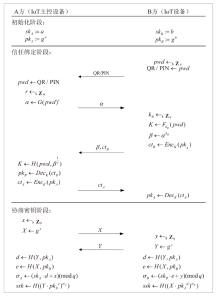
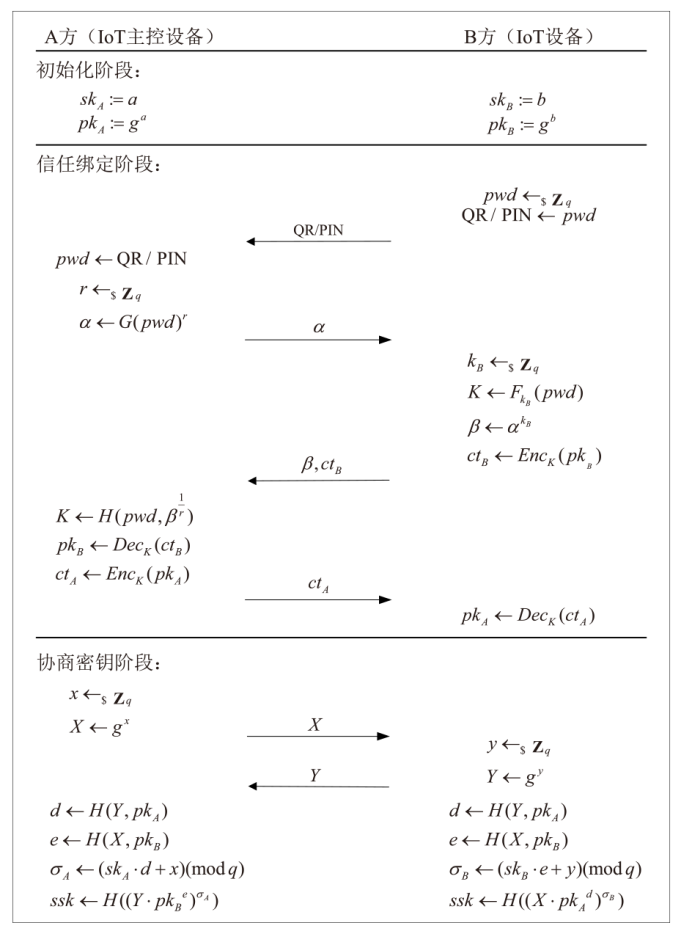
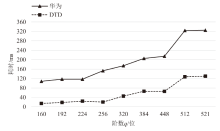
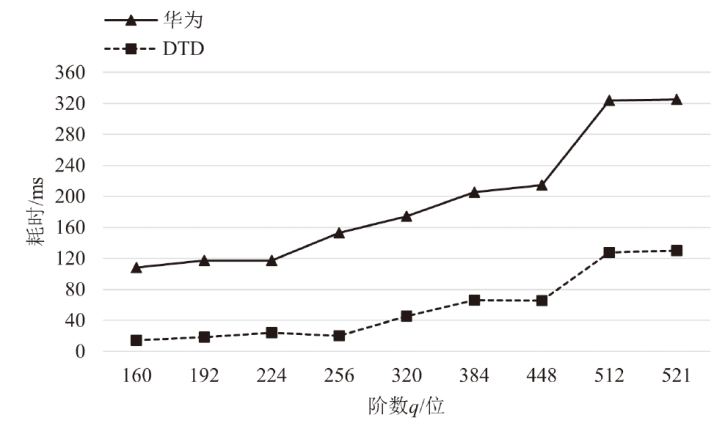
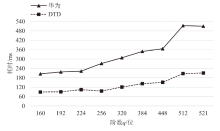
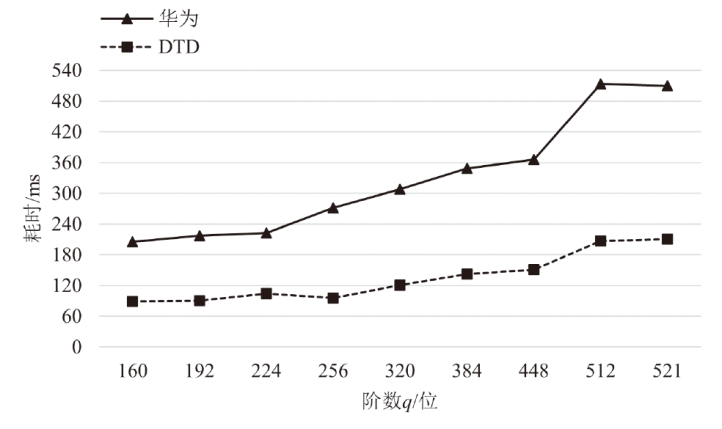
Netinfo Security ›› 2025, Vol. 25 ›› Issue (7): 1032-1043.doi: 10.3969/j.issn.1671-1122.2025.07.003
Previous Articles Next Articles
Research on Simple and Low Interaction Authentication Protocols for IoT Devices
WANG Mei1,2( ), YANG Xiaoran2, LI Zengpeng1,2
), YANG Xiaoran2, LI Zengpeng1,2
- 1. Quan Cheng Laboratory, Jinan 250103, China
2. School of Cyber Science and Technology, Shandong University, Qingdao 266237, China
-
Received:2024-12-13Online:2025-07-10Published:2025-08-07 -
Contact:WANG Mei E-mail:wangmeiz@sdu.edu.cn
CLC Number:
Cite this article
WANG Mei, YANG Xiaoran, LI Zengpeng. Research on Simple and Low Interaction Authentication Protocols for IoT Devices[J]. Netinfo Security, 2025, 25(7): 1032-1043.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.07.003
| 符号 | 含义 |
|---|---|
| 大素数 | |
| 群的阶 | |
| 群的生成元 | |
| 有限群 | |
| 实例生成器 | |
| 安全参数 | |
| 多项式时间内敌手 | |
| 阶为 | |
| 模 | |
| 从一个集合中均匀随机采样 | |
| 口令 | |
| 哈希函数 | |
| 在 | |
| 密钥为 | |
| PPT | 多项式时间 |
| [1] | GARBA A, KHOURY D, BALIAN P, et al. LightCert4IoTs: Blockchain-Based Lightweight Certificates Authentication for IoT Applications[J]. IEEE Access, 2023, 11: 28370-28383. |
| [2] | AMANLOU S, HASAN M K, ABU B K A. Lightweight and Secure Authentication Scheme for IoT Network Based on Publish-Subscribe Fog Computing Model[EB/OL]. (2021-09-13) [2024-10-15]. https://doi.org/10.1016/j.comnet.2021.108465. |
| [3] | SIDDIQUI Z, GAO Jiechao, KHAN M K. An Improved Lightweight PUF-PKI Digital Certificate Authentication Scheme for the Internet of Things[J]. IEEE Internet of Things Journal, 2022, 9(20): 19744-19756. |
| [4] | TSAI J L, LO N W. Secure Anonymous Key Distribution Scheme for Smart Grid[J]. IEEE Transactions on Smart Grid, 2016, 7(2): 906-914. |
| [5] | BELLOVIN S M, MERRITT M. Encrypted Key Exchange: Password-Based Protocols Secure against Dictionary Attacks[C]// IEEE. Proceedings 1992 IEEE Computer Society Symposium on Research in Security and Privacy. New York: IEEE, 1992: 72-84. |
| [6] | HAO Feng, RYAN P Y A. Password Authenticated Key Exchange by Juggling[C]// Springer. Security Protocols XVI. Heidelberg: Springer, 2011: 159-171. |
| [7] | LEE H, WON D. Prevention of Exponential Equivalence in Simple Password Exponential Key Exchange (SPEKE)[J]. Symmetry, 2015, 7(3): 1587-1594. |
| [8] | POINTCHEVAL D, WANG Guilin. VTBPEKE: Verifier-Based Two-Basis Password Exponential Key Exchange[C]// ACM. Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security. New York: ACM, 2017: 301-312. |
| [9] | SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]// Springer. Advances in Cryptology. Heidelberg: Springer, 2007: 47-53. |
| [10] | LI Xiong, XIONG Yongping, MA Jian, et al. An Efficient and Security Dynamic Identity Based Authentication Protocol for Multi-Server Architecture Using Smart Cards[J]. Journal of Network and Computer Applications, 2012, 35(2): 763-769. |
| [11] | WU T D. The Secure Remote Password Protocol[EB/OL]. [2024-10-15]. https://www.ndss-symposium.org/wp-content/uploads/2017/09/The-Secure-Remote-Password-Protocol.pdf. |
| [12] | JARECKI S, KRAWCZYK H, XU Jiayu. OPAQUE: An Asymmetric PAKE Protocol Secure against Pre-Computation Attacks[C]// Springer. 37th Annual International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2018: 456-486. |
| [13] | DIFFIE W, VAN O P C, WIENER M J. Authentication and Authenticated Key Exchanges[J]. Designs, Codes and Cryptography, 1992, 2(2): 107-125. |
| [14] | BLAKE W S, MENEZES A. Unknown Key-Share Attacks on the Station-to-Station (STS) Protocol[C]// Springer. International Workshop on Public Key Cryptography. Heidelberg: Springer, 1999: 154-170. |
| [15] | LAW L, MENEZES A, QU Minghua, et al. An Efficient Protocol for Authenticated Key Agreement[J]. Designs, Codes and Cryptography, 2003, 28(2): 119-134. |
| [16] | KRAWCZYK H. HMQV: A High-Performance Secure Diffie-Hellman Protocol: (Extended Abstract)[C]// Springer. Advances in Cryptology- CRYPTO 2005. Heidelberg: Springer, 2005: 546-566. |
| [17] | KUMARI S, KARUPPIAH M, DAS A K, et al. A Secure Authentication Scheme Based on Elliptic Curve Cryptography for IoT and Cloud Servers[J]. The Journal of Supercomputing, 2018, 74(12): 6428-6453. |
| [18] | BABU E S, DADI A K, SINGH K K, et al. A Distributed Identity-Based Authentication Scheme for Internet of Things Devices Using Permissioned Blockchain System[EB/OL]. (2022-02-04) [2024-10-15]. https://doi.org/10.1111/exsy.12941. |
| [19] | DANIEL R M, THOMAS A, RAJSINGH E B, et al. A Strengthened ECK Secure Identity Based Authenticated Key Agreement Protocol Based on the Standard CDH Assumption[EB/OL]. (2023-07-11) [2024-10-15]. https://doi.org/10.1016/j.ic.2023.105067. |
| [20] | CAO Jin, LI Hui, MA Maode, et al. A Simple and Robust Handover Authentication between HeNB and eNB in LTE Networks[J]. Computer Networks, 2012, 56(8): 2119-2131. |
| [21] | GB/T 32907-2016 Information Security Technology—SM4 Block Cipher Algorithm[S]. Beijing: Standards Press of China, 2016. |
| GB/T 32907-2016 信息安全技术 SM4 分组密码算法[S]. 北京: 中国标准出版社, 2016. | |
| [22] | GB/T 32918.2-2016 Information Security Technology—Public Key Cryptographic Algorithm SM2 Based on Elliptic Curves-Part 2: Digital Signature Algorithm[S]. Beijing: Standards Press of China, 2016. |
| GB/T 2918. 2-2016信息安全技术 SM2椭圆曲线公钥密码算法第2部分:数字签名算法[S]. 北京: 中国标准出版社, 2016. | |
| [23] | CASACUBERTA S, HESSE J, LEHMANN A. SoK: Oblivious Pseudorandom Functions[C]// IEEE. 2022 IEEE 7th European Symposium on Security and Privacy (EuroS&P). New York: IEEE, 2022: 625-646. |
| [24] | BELLARE M, POINTCHEVAL D, ROGAWAY P. Authenticated Key Exchange Secure against Dictionary Attacks[C]// Springer. Advances in Cryptology — EUROCRYPT 2000. Heidelberg: Springer, 2000: 139-155. |
| [25] | ABDALLA M, FOUQUE P A, POINTCHEVAL D. Password-Based Authenticated Key Exchange in the Three-Party Setting[C]// Springer. Public Key Cryptography-PKC 2005. Heidelberg: Springer, 2005: 65-84. |
| [1] | ZHANG Xuewang, CHEN Siyu, LUO Xinyue, LEI Zhitao, XIE Haofei. Efficient Searchable Attribute-Based Encryption Scheme for Cloud-Assisted Industrial IoT [J]. Netinfo Security, 2024, 24(9): 1352-1363. |
| [2] | HU Chengcong, HU Honggang. Lattice-Based Round-Optimal Password Authenticated Secret Sharing Protocol [J]. Netinfo Security, 2024, 24(6): 937-947. |
| [3] | LI Zhihua, CHEN Liang, LU Xulin, FANG Zhaohui, QIAN Junhao. Lightweight Detection Method for IoT Mirai Botnet [J]. Netinfo Security, 2024, 24(5): 667-681. |
| [4] | YIN Jie, CHEN Pu, YANG Guinian, XIE Wenwei, LIANG Guangjun. Detection of DDoS Attacks in the Internet of Things Based on Artificial Intelligence [J]. Netinfo Security, 2024, 24(11): 1615-1623. |
| [5] | YIN Chunyong, JIANG Yiyang. Differential Privacy Trajectory Protection Model Based on Personalized Spatiotemporal Clustering [J]. Netinfo Security, 2024, 24(1): 80-92. |
| [6] | GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System [J]. Netinfo Security, 2023, 23(3): 1-12. |
| [7] | WU Kehe, CHENG Rui, JIANG Xiaochen, ZHANG Jiyu. Security Protection Scheme of Power IoT Based on SDP [J]. Netinfo Security, 2022, 22(2): 32-38. |
| [8] | LI Qun, DONG Jiahan, GUAN Zhitao, WANG Chao. A Clustering and Classification-based Malicious Attack Detection Method for Internet of Things [J]. Netinfo Security, 2021, 21(8): 82-90. |
| [9] | LIU Xin, YANG Haorui, GUO Zhenbin, WANG Jiayin. An Authentication Protocol Achieving Online Registration and Privilege Separation for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(7): 1-9. |
| [10] | WANG Kaixuan, TENG Yajun, WANG Qiongxiao, WANG Wei. Research on the Application of SM Algorithms of Implicit Certificate [J]. Netinfo Security, 2021, 21(5): 74-81. |
| [11] | XU Huikai, LIU Yue, MA Zhenbang, DUAN Haixin. A Large-scale Measurement Study of MQTT Security [J]. Netinfo Security, 2020, 20(9): 37-41. |
| [12] | SHI Runhua, SHI Ze. Key Management Scheme for IoT Based on Blockchain Technology [J]. Netinfo Security, 2020, 20(8): 1-8. |
| [13] | CHEN Lu, SUN Yajie, ZHANG Liqiang, CHEN Yun. A Scheme of Measurement for Terminal Equipment Based on DICE in IoT [J]. Netinfo Security, 2020, 20(4): 21-30. |
| [14] | CHENG Yang, LEI Min, LUO Qun. Access Authentication Method for IoT Terminal Devices Based on Deep Learning [J]. Netinfo Security, 2020, 20(11): 67-74. |
| [15] | LIU Kaifang, FU Shaojing, SU Jinshu, ZHANG Fucheng. An Optimizing Scheme on Multi-domain Collaborative IOTA Blockchain Technology for the Internet of Things [J]. Netinfo Security, 2020, 20(10): 41-48. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||