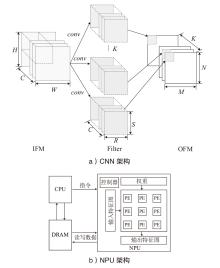
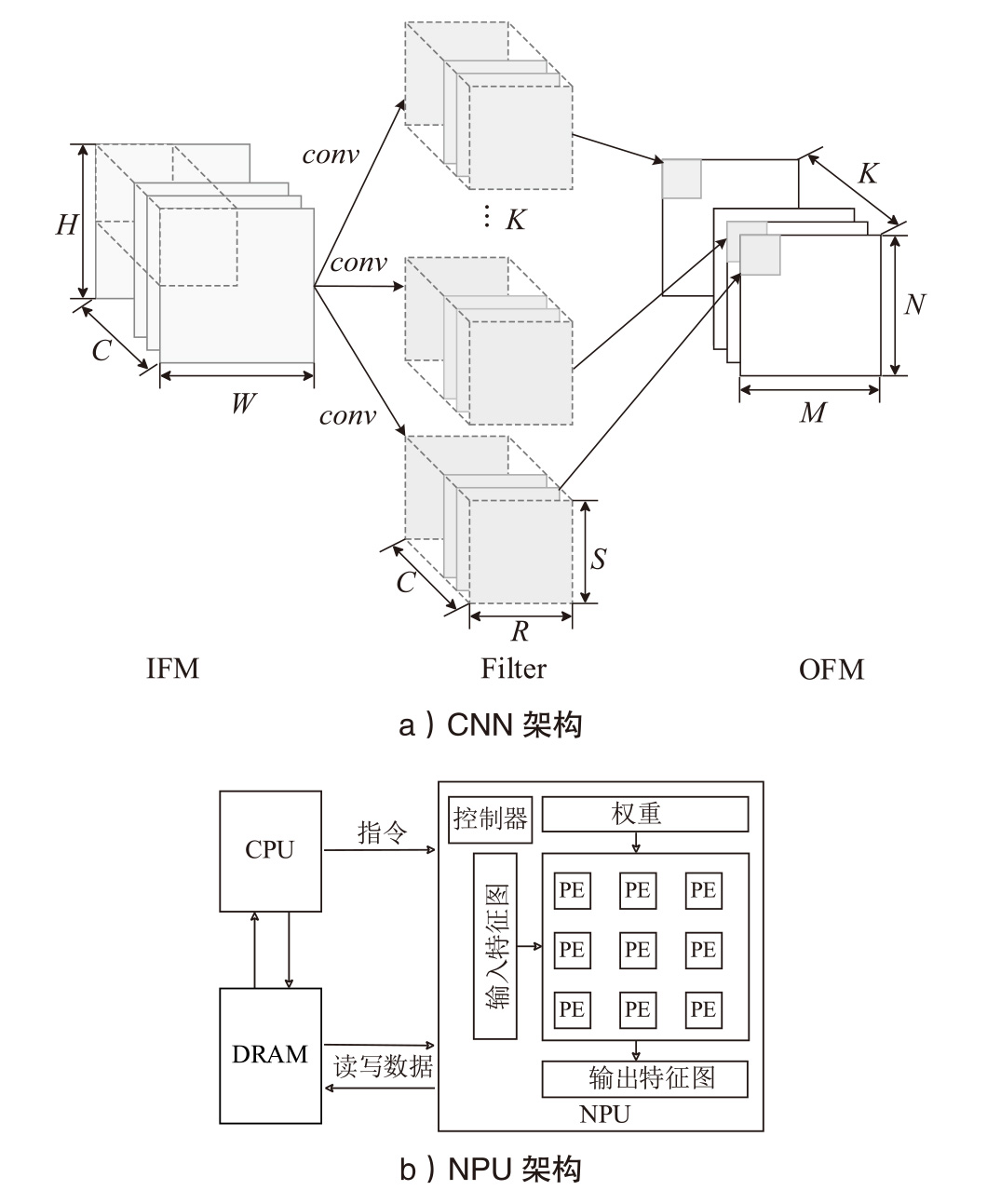
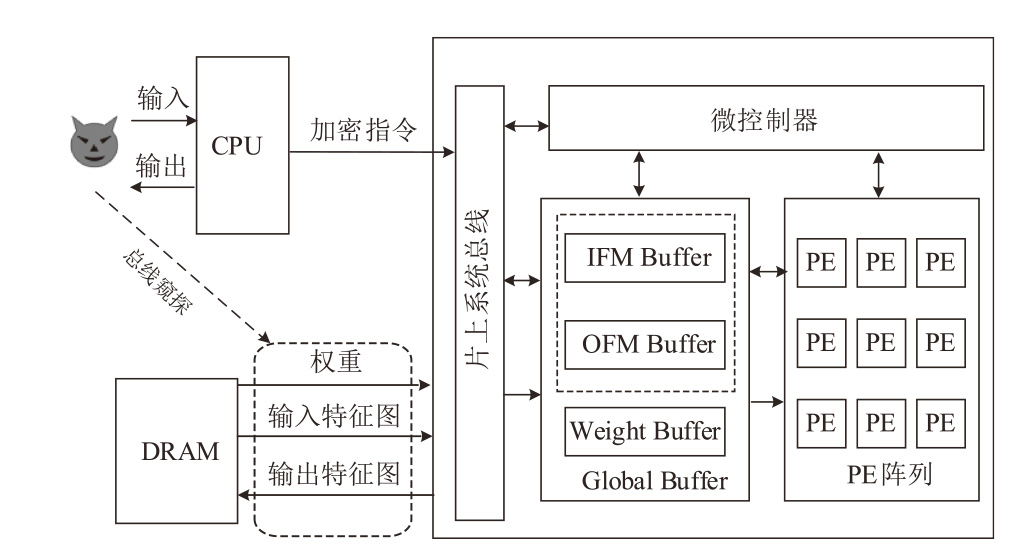
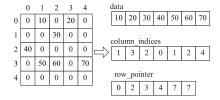
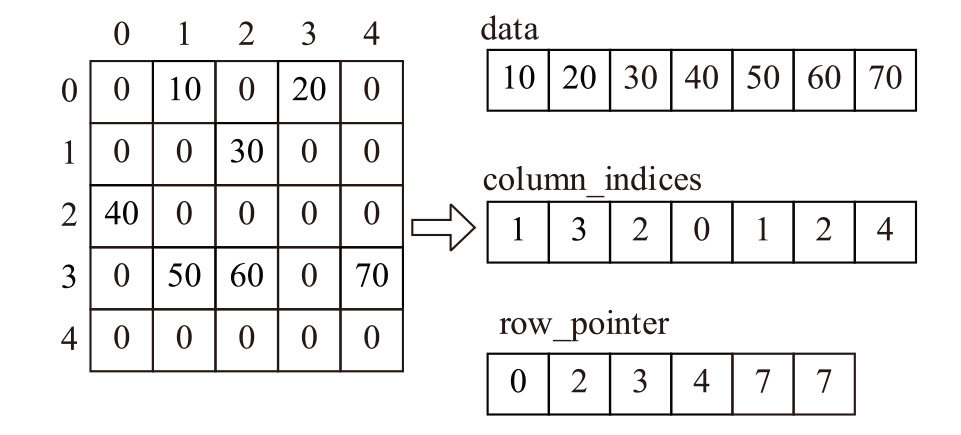
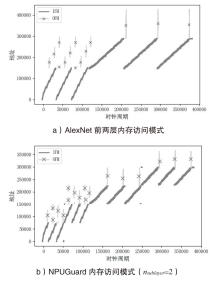
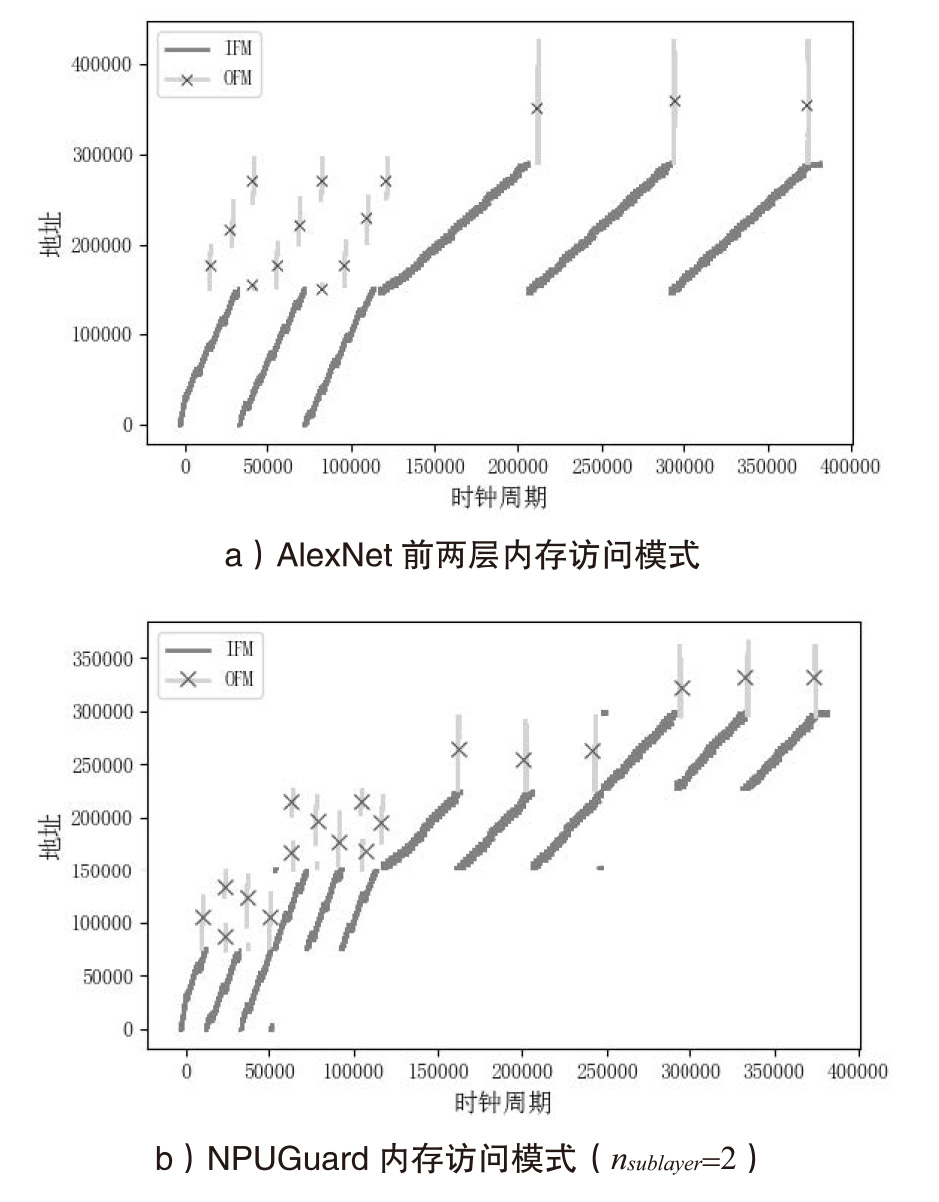
Netinfo Security ›› 2025, Vol. 25 ›› Issue (6): 977-987.doi: 10.3969/j.issn.1671-1122.2025.06.012
Previous Articles Next Articles
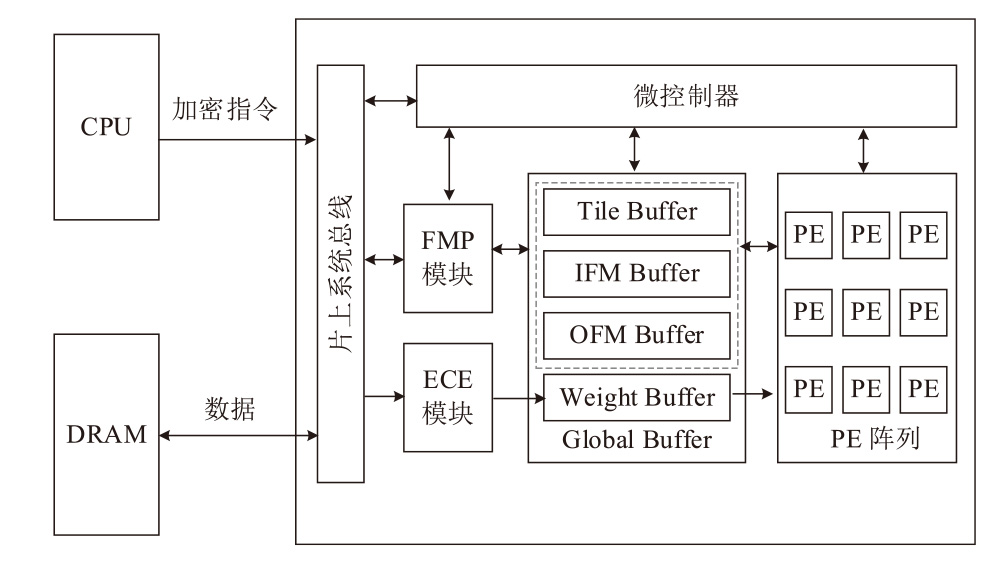
A Security Protection Scheme against Memory Side-Channel Attacks on NPU
HU Wenao, YAN Fei( ), ZHANG Liqiang
), ZHANG Liqiang
- School of Cyber Science and Engineering, Wuhan University, Wuhan 430040, China
-
Received:2025-01-24Online:2025-06-10Published:2025-07-11
CLC Number:
Cite this article
HU Wenao, YAN Fei, ZHANG Liqiang. A Security Protection Scheme against Memory Side-Channel Attacks on NPU[J]. Netinfo Security, 2025, 25(6): 977-987.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.06.012
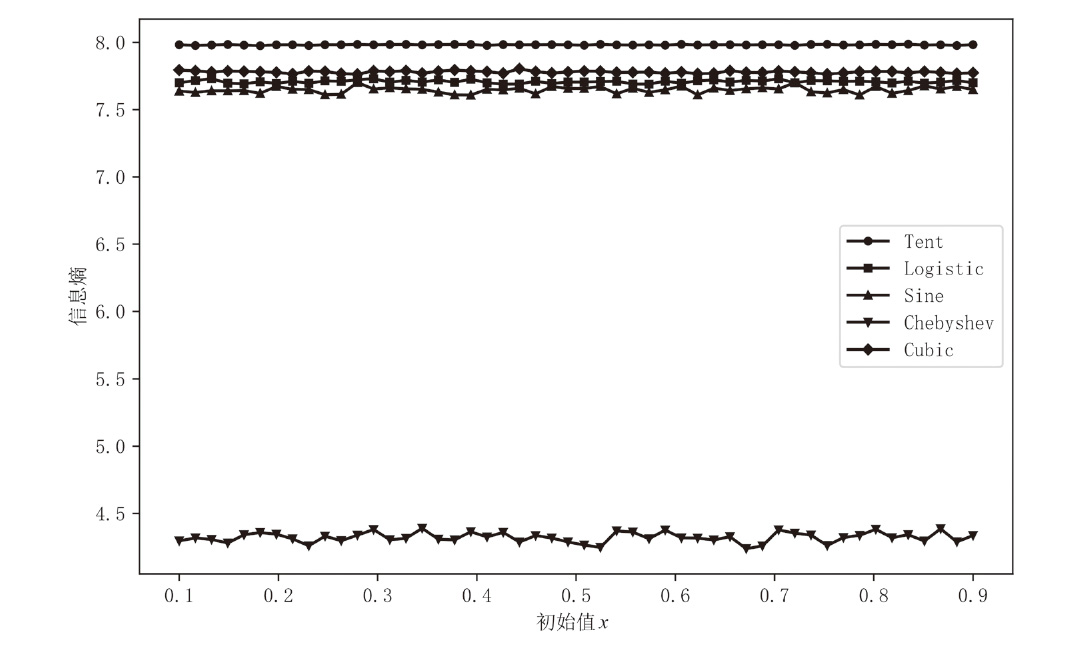
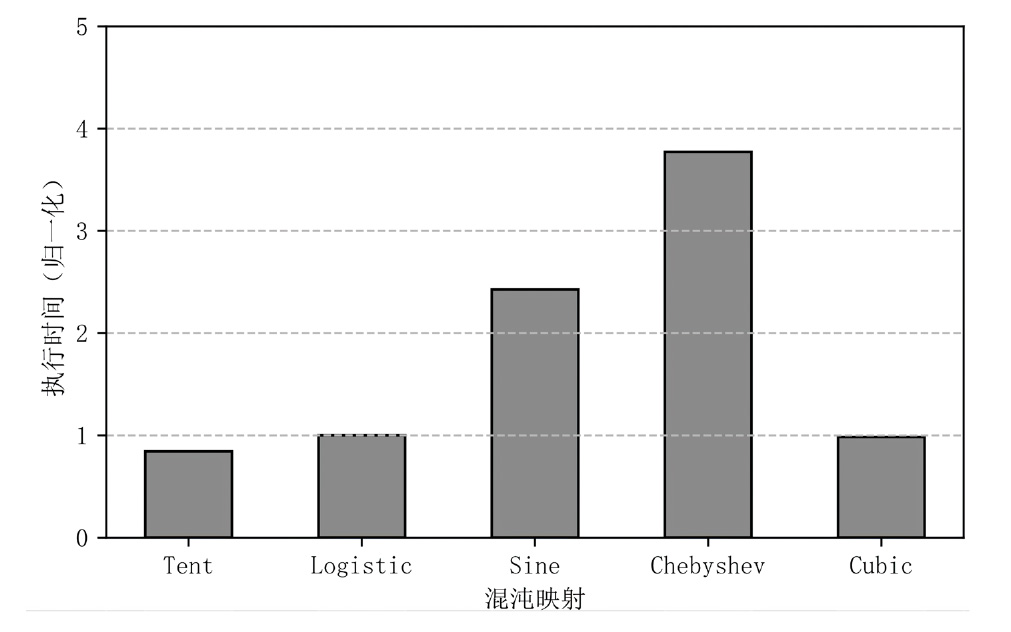
| 混沌映射 | 映射函数 | 参数 |
|---|---|---|
| Tent | a = 0.49 | |
| Logisitc | a = 3.98 | |
| Sine | a = 4 | |
| Chebyshev | a = 4 | |
| Cubic | a = 2.595 |
| [1] | ZOTING S. Artificial Intelligence(AI) in Hardware Market Size, Share, and Trends 2025 to 2034[EB/OL]. [2025-01-10]. https://www.precedenceresearch.com/artificial-intelligence-in-hardware-market. |
| [2] | WANG Xingbin, HOU Rui, ZHU Yifan, et al. NPUFort: A Secure Architecture of DNN Accelerator against Model Inversion Attack[C]// ACM. 16th ACM International Conference on Computing Frontiers. New York: ACM, 2019: 190-196. |
| [3] | ZUO Pengfei, HUA Yu, LIANG Ling, et al. Sealing Neural Network Models in Encrypted Deep Learning Accelerators[C]// IEEE. 2021 58th ACM/IEEE Design Automation Conference(DAC). New York: IEEE, 2021: 1255-1260. |
| [4] | WEERASENA H, MISHRA P. Revealing CNN Architectures via Side-channel Analysis in Dataflow-Based Inference Accelerators[J]. ACM Transactions on Embedded Computing Systems, 2024, 23(6): 1-25. |
| [5] | HUA Weizhe, ZHANG Zhiru, SUH G E. Reverse Engineering Convolutional Neural Networks through Side-Channel Information Leaks[C]// ACM. 55th Annual Design Automation Conference. New York: ACM, 2018: 1-6. |
| [6] | YANG Dingqing, NAIR P J, LIS M. HuffDuff: Stealing Pruned DNNs from Sparse Accelerators[C]// ACM. The 28th ACM International Conference on Architectural Support for Programming Languages and Operating Systems. New York: ACM, 2023: 385-399. |
| [7] | HU Xing, LIANG Ling, LI Shuangchen, et al. DeepSniffer: A DNN Model Extraction Framework Based on Learning Architectural Hints[C]// ACM. The Twenty-Fifth International Conference on Architectural Support for Programming Languages and Operating Systems. New York: ACM, 2020: 385-399. |
| [8] | HUANG Yongbing, CHEN Licheng, CUI Zehan, et al. HMTT: A Hybrid Hardware/Software Tracing System for Bridging the DRAM Access Trace’s Semantic Gap[J]. ACM Transactions on Architecture and Code Optimization(TACO), 2014, 11(1): 1-25. |
| [9] | FLETCHER C W, REN Ling, KWON A, et al. A Low-Latency, Low-Area Hardware Oblivious RAM Controller[C]// IEEE. 2015 IEEE 23rd Annual International Symposium on Field-Programmable Custom Computing Machines. New York: IEEE, 2015: 215-222. |
| [10] | LIU Yuntao, DACHMAN-SOLED D, SRIVASTAVA A. Mitigating Reverse Engineering Attacks on Deep Neural Networks[C]// IEEE. 2019 IEEE Computer Society Annual Symposium on VLSI (ISVLSI). New York: IEEE, 2019: 657-662. |
| [11] | LI Jingtao, HE Zhezhi, RAKIN A S, et al. Neurobfuscator: A Full-stack Obfuscation Tool to Mitigate Neural Architecture Stealing[C]// IEEE. 2021 IEEE International Symposium on Hardware Oriented Security and Trust(HOST). New York: IEEE, 2021: 248-258. |
| [12] | CHE Yuezhi, WANG Rujia. DNNCloak: Secure DNN Models against Memory Side-Channel Based Reverse Engineering Attacks[C]// IEEE. 2022 IEEE 40th International Conference on Computer Design(ICCD). New York: IEEE, 2022: 89-96. |
| [13] |
CHEN Yuxin, YANG Tianyu, EMER J, et al. Eyeriss v2: A Flexible Accelerator for Emerging Deep Neural Networks on Mobile Devices[J]. IEEE Journal on Emerging and Selected Topics in Circuits and Systems, 2019, 9(2): 292-308.
doi: 10.1109/JETCAS.2019.2910232 |
| [14] | LIU Fangxin, YANG Ning, LI Haoming, et al. SPARK: Scalable and Precision-Aware Acceleration of Neural Networks via Efficient Encoding[C]// IEEE. 2024 IEEE International Symposium on High-Performance Computer Architecture(HPCA). New York: IEEE, 2024: 1029-1042. |
| [15] | YAN Mengjia, FLETCHER C W, TORRELLAS J. Cache Telepathy: Leveraging Shared Resource Attacks to Learn DNN Architectures[C]// USENIX. 29th USENIX Security Symposium(USENIX Security 20). Berkeley: USENIX, 2020: 2003-2020. |
| [16] | GAO Yansong, QIU Huming, ZHANG Zhi, et al. DeepTheft: Stealing DNN Model Architectures through Power Side Channel[C]// IEEE. 2024 IEEE Symposium on Security and Privacy(SP). New York: IEEE, 2024: 3311-3326. |
| [17] | WEI Junyi, ZHANG Yicheng, ZHOU Zhe, et al. Leaky DNN: Stealing Deep-Learning Model Secret with GPU Context-Switching Side-Channel[C]// IEEE. 2020 50th Annual IEEE/IFIP International Conference on Dependable Systems and Networks(DSN). New York: IEEE, 2020: 125-137. |
| [18] | MAIA H T, XIAO Chang, LI Dingzeyu, et al. Can One Hear the Shape of a Neural Network: Snooping the GPU via Magnetic Side Channel[C]// USENIX. 31th USENIX Security Symposium(USENIX Security 22). Berkeley: USENIX, 2022: 4383-4400. |
| [19] | RAKIN A S, CHOWDHURYY M H I, YAO Fan, et al. DeepSteal: Advanced Model Extractions Leveraging Efficient Weight Stealing in Memories[C]// IEEE. 2022 IEEE Symposium on Security and Privacy(SP). New York: IEEE, 2022: 1157-1174. |
| [20] | SUN Yu, XIONG Gaojian, LIU Xiao, et al. A Survey on Trusted Execution Environment Based Secure Inference[J]. Netinfo Security, 2024, 24(12): 1799-1818. |
| 孙钰, 熊高剑, 刘潇, 等. 基于可信执行环境的安全推理研究进展[J]. 信息网络安全, 2024, 24(12):1799-1818. | |
| [21] | LEE S, KIM J, NA S, et al. TNPU: Supporting Trusted Execution with Tree-less Integrity Protection for Neural Processing Unit[C]// IEEE. 2022 IEEE International Symposium on High-Performance Computer Architecture(HPCA). New York: IEEE, 2022: 229-243. |
| [22] | SHRIVASTAVA N, SARANGI S R. Securator: A Fast and Secure Neural Processing Unit[C]// IEEE. 2023 IEEE International Symposium on High-Performance Computer Architecture(HPCA). New York: IEEE, 2023: 1127-1139. |
| [23] | FENG Erhu, FENG Dahu, DU Dong, et al. sNPU: Trusted Execution Environments on Integrated NPUs[C]// IEEE. 2024 ACM/IEEE 51st Annual International Symposium on Computer Architecture(ISCA). New York: IEEE, 2024: 708-723. |
| [24] | ZHAO Geng, MA Yingjie, DONG Youheng. New Progress in Research and Application of Chaotic Cryptography Theory[J]. Netinfo Security, 2024, 24(2): 203-216. |
| 赵耿, 马英杰, 董有恒. 混沌密码理论研究与应用新进展[J]. 信息网络安全, 2024, 24(2):203-216. | |
| [25] | SAMAJDAR A, JOSEPH J M, ZHU Yuhao, et al. A Systematic Methodology for Characterizing Scalability of DNN Accelerators Using Scale-sim[C]// IEEE. 2020 IEEE International Symposium on Performance Analysis of Systems and Software(ISPASS). New York: IEEE, 2020: 58-68. |
| [26] | LEE J, PARK S, MO S, et al. Layer-adaptive Sparsity for the Magnitude-Based Pruning[C]// ICLR. The Ninth International Conference on Learning Representations. Vienna: ICLR, 2021: 1-19. |
| [1] | ZHAO Bo, PENG Junru, WANG Yixuan. Network Security Situation Assessment Method Based on Threat Propagation [J]. Netinfo Security, 2025, 25(6): 843-858. |
| [2] | SUN Jianwen, ZHANG Bin, SI Nianwen, FAN Ying. Lightweight Malicious Traffic Detection Method Based on Knowledge Distillation [J]. Netinfo Security, 2025, 25(6): 859-871. |
| [3] | XUN Yijie, CUI Jiarong, MAO Bomin, QIN Junman. Intrusion Detection System for the Controller Area Network Bus of Intelligent Vehicles Based on Federated Learning [J]. Netinfo Security, 2025, 25(6): 872-888. |
| [4] | DENG Dongshang, WANG Weiye, ZHANG Weidong, WU Xuangou. Layered Personalized Federated Learning Guided by Model Feature Orientation [J]. Netinfo Security, 2025, 25(6): 889-897. |
| [5] | LIU Feng, HUANG Hao. A Decentralized Regulatory Architecture Based on Smart Contracts and Prophecy Machines with Active Sensor Networks [J]. Netinfo Security, 2025, 25(6): 898-909. |
| [6] | SHI Kaibo, DING Jia, WANG Jun, CAI Xiao. Supervised Restart-Based Cybersecurity Defense Strategy for Power Systems [J]. Netinfo Security, 2025, 25(6): 910-919. |
| [7] | ZHU Shuaishuai, LIU Keqian. A Masking-Based Selective Federated Distillation Scheme [J]. Netinfo Security, 2025, 25(6): 920-932. |
| [8] | FENG Jingyu, PAN Meng, WANG Jialin, ZHAO Xiang. Deep Semantic Parsing Based Active Defense against API Overstep Vulnerabilities [J]. Netinfo Security, 2025, 25(6): 933-942. |
| [9] | CHEN Da, CAI Xiao, SUN Yanbin, DONG Chongwu. Optimization of Data Conf lict and DDoS Attack Defense Mechanisms in Industrial Control Systems Based on Greedy Algorithm [J]. Netinfo Security, 2025, 25(6): 943-954. |
| [10] | ZHU Zhicheng, CAO Hui, WANG Yinsheng. Research on Active Defense Security System Based on Four-Honey Coordination for Energy Systems [J]. Netinfo Security, 2025, 25(6): 955-966. |
| [11] | GENG Zhiyuan, XU Zexuan, ZHANG Hengwei. A Decision-Making Method for Cloud-Native Moving Target Defense Based on Stochastic Games and DQN Algorithm [J]. Netinfo Security, 2025, 25(6): 967-976. |
| [12] | FU Zefan, PAN Gaoning, REN Yizhi, HU Mingde. Mimetic Function: Mimetic Defense Research for Serverless [J]. Netinfo Security, 2025, 25(6): 988-1002. |
| [13] | PAN Jing, LI Boxun, WAN Beilin, ZHONG Yantao. An Overview on Lattice-Based Zero-Knowledge Proofs [J]. Netinfo Security, 2025, 25(5): 679-688. |
| [14] | LI Jun’e, MA Ziyu, LU Qiuyu, YU Kailong. An Intelligent Detection Method for IEC 61850 Network Attacks Incorporating Temporal and Sequence Features [J]. Netinfo Security, 2025, 25(5): 689-699. |
| [15] | ZHAO Feng, FAN Song, ZHAO Yanqi, CHEN Qian. Privacy-Preserving Methods for Streaming Data in Wearable Medical Devices Based on Local Differential Privacy [J]. Netinfo Security, 2025, 25(5): 700-712. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||