Netinfo Security ›› 2025, Vol. 25 ›› Issue (6): 988-1002.doi: 10.3969/j.issn.1671-1122.2025.06.013
Previous Articles Next Articles
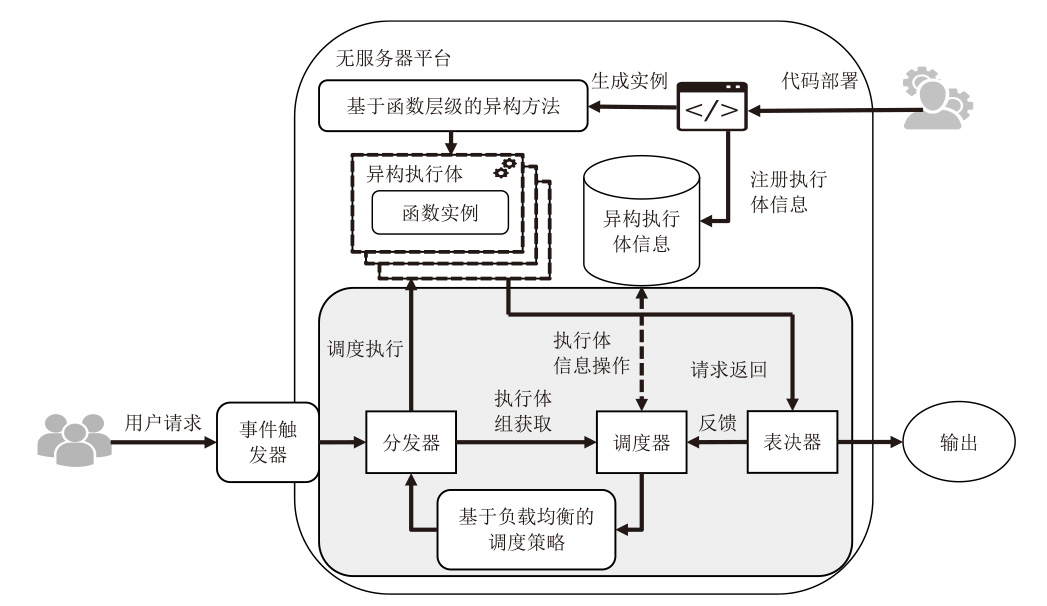
Mimetic Function: Mimetic Defense Research for Serverless
FU Zefan, PAN Gaoning( ), REN Yizhi, HU Mingde
), REN Yizhi, HU Mingde
- School of Cyberspace, Hangzhou Dianzi University, Hangzhou 310018, China
-
Received:2025-02-28Online:2025-06-10Published:2025-07-11 -
Contact:PAN Gaoning E-mail:pgn@hdu.edu.cn
CLC Number:
Cite this article
FU Zefan, PAN Gaoning, REN Yizhi, HU Mingde. Mimetic Function: Mimetic Defense Research for Serverless[J]. Netinfo Security, 2025, 25(6): 988-1002.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.06.013
| 攻击面 | 攻击类型 | 技术特征与风险 |
|---|---|---|
| 事件注入攻击 | 参数篡改注入、恶意负载注入(如SQL/NoSQL 注入)、反序列化攻击 | 通过函数输入参数或事件源(如 API Gateway)注入恶意代码,利用函数处理逻辑缺陷执行非授权操作 |
| 第三方依赖漏洞 | 供应链攻击(污染依赖包)、过时库漏洞利用、运行时动态依赖加载劫持 | 开源依赖库(如 NPM/PyPI)中的已知漏洞被利用,或恶意包通过 CI/CD 流程混入无服务器环境 |
| 函数调用链攻击 | 中间人攻击(Man-in-the-MiddleAttack,MITM)、调用链劫持、服务间认证绕过 | 篡改函数间通信(如 AWS Step Functions),利用弱身份验证机制伪造调用源,触发非预期函数执行 |
| 权限配置错误 | 过度权限分配(IAM 策略漏洞)、临时凭证泄露、横向权限提升 | 函数角色被授予超出需求的权限(如S3 完全访问),导致攻击者通过函数上下文获取高权限凭证 |
| 资源耗尽型 DDoS | 函数执行超时攻击、冷启动攻击、高频触发器滥用 | 通过高频事件触发(如 API Gateway)消耗函数实例配额,或利用冷启动延迟制造服务不可用 |
| 敏感数据泄露 | 环境变量泄露、日志信息泄露、存储服务(如 S3)配置错误 | 未加密的环境变量或调试日志暴露密钥信息,或存储桶权限配置不当导致数据公开访问 |
| 层级/攻击面 | 具体风险项 | 问题描述 |
|---|---|---|
| 函数应用 | 代码漏洞 | 注入漏洞或输入校验缺失导致远程代码执行(RCE)或数据篡改 IAM |
| 配置项错误 | 权限过大、敏感密钥硬编码或未启用 加密通信协议 | |
| 不安全第三方 依赖引入 | 包含漏洞的库文件或恶意软件包触发 远程攻击 | |
| 日志泄露 | 未脱敏日志暴露用户凭证或内部系统 路径信息 | |
| 存储服务 配置错误 | 云存储桶公开访问或未加密导致数据泄露风险 | |
| 运行时环境 | 容器运行时操作 系统漏洞 | 基础镜像未修复 CVE 漏洞导致容器 逃逸攻击 |
| 中间件漏洞 | 老旧版本中间件引发未授权访问或 远程代码执行 | |
| 供应链攻击 | 恶意镜像层或受污染依赖仓库植入 后门程序 | |
| 硬件架构 | 虚拟化机制 | Hypervisor 漏洞导致虚拟机逃逸或资源劫持攻击 |
| CPU 漏洞 | 侧信道攻击(如 Spectre)窃取加密密钥等敏感数据 |
| 配置项 | 配置值 | |
|---|---|---|
| 拟态函数配置 | 运行环境 | Debian 10(自定义运行时) |
| Python 版本 | 3.10 | |
| 执行超时时间/s | 60 | |
| 单实例并发度 | 单个函数实例最多同时处理 20 个请求 | |
| 异构执行体配置 | Python 版本 | 3.9、3.10 |
| CPU 架构 | x86_64、arm64 | |
| 容器运行时操作系统 | Amazon Linux 2、Debian 9、Debian 10 | |
| 第三方依赖库 | PIL-8.4.0、PIL-9.3.0、PIL-10.1.0、PIL-10.4.0、PIL-11.1.0 | |
| 异构执行体池内执行体 数量/个 | 6 | |
| 异构执行体组内执行体 数量/个 | 3 | |
| 单实例并发度 | 单个函数实例最多同时处理 10 个请求 |
| [1] | RAJAN R A P. Serverless Architecture-A Revolution in Cloud Computing[C]// IEEE. 2018 Tenth International Conference on Advanced Computing (ICoAC). New York: IEEE, 2018: 88-93. |
| [2] | Amazon Web Services. Aws Lambda[EB/OL]. [2024-12-24]. https://aws.amazon. |
| [3] | MARIN E, PERINO D, DI P R. Serverless Computing: A Security Perspective[EB/OL]. (2022-10-01)[2024-12-24]. https://doi.org/10.1186/s13677-022-00347-w. |
| [4] | SOFTWARE C P. A Deep Dive into Serverless Attacks, Sls-1:Event Injection[EB/OL]. [2024-12-24]. https://www.protego.io/a-deep-dive-into-serverless-attacks-sls-1-event-injection/. |
| [5] | DALY J. Event Injection: Protecting Your Serverless Applications[EB/OL]. [2024-12-24]. https://www.jeremydaly.com/event-injection-protecting-your-serverless-applications/. |
| [6] | BEN-SHIMOL L, LAVI D, KLEVANSKY E, et al. Detection of compromised functions in a serverless cloud environment[EB/OL]. (2024-12-10)[2024-12-24]. https://doi.org/10.1016/j.cose.2024.104261. |
| [7] | PUSULURI V S R. Taxonomy of Security and Privacy Issues in Serverless Computing[D]. Saint Cloud: Saint Cloud State University, 2022. |
| [8] | ADAMSON C. Analyze Cloudtrail Logs to Identify User Activities[EB/OL]. [2024-12-24]. https://medium.com/@christopheradamson253/analyze-cloudtrail-logs-to-identify-user-activities-7a1bb641fdfb. |
| [9] | CHAWLA R. Information Flow Control for Serverless Systems[J]. International Journal of Advanced Computer Science and Applications, 2021, 12(9): 1-10. |
| [10] | IDENTITY O. Converged Iam -the Future of Identity Security?[EB/OL]. [2024-12-24]. https://www.oneidentity.com/what-is-converged-identity-and-access-management/. |
| [11] | SOLDANI J, BROGI A. Anomaly Detection and Failure Root Cause Analysis in (Micro) Service-Based Cloud Applications: A Survey[J]. ACM Computing Surveys, 2022, 55(3): 1-39. |
| [12] | MOHAMED A K Y S, AUER D, HOFER D, et al. A Systematic Literature Review for Authorization and Access Control: Definitions, Strategies and Models[J]. International Journal of Web Information Systems, 2022, 18(2/3): 156-180. |
| [13] | DE N K M, RUTKOWSKI A F, SAUNDERS C. The Whole of Cyber Defense: Syncing Practice and Theory[EB/OL]. [2024-12-24]. https://doi.org/10.1016/j.jsis.2024.101861. |
| [14] | DEY N S, REDDY S P K, LAVANYA G. Serverless Computing:Architectural Paradigms, Challenges, and Future Directions in Cloud Technology[C]// IEEE. 2023 7th International Conference on I-SMAC (IoT in Social, Mobile, Analytics and Cloud)( I-SMAC). New York: IEEE, 2023: 406-414. |
| [15] |
Wu Jiangxing. The Original Intent and Vision of Mimic Computing and Mimic Security Defense[J]. Telecommunications Science, 2014, 30(7): 2-7.
doi: 10.3969/j.issn.1000-0801.2014.07.001 |
|
邬江兴. 拟态计算与拟态安全防御的原意和愿景[J]. 电信科学, 2014, 30(7):2-7.
doi: 10.3969/j.issn.1000-0801.2014.07.001 |
|
| [16] | WANG Junchao, PANG Jianmin, WEI Jin. Security-as-a-Service with Cyberspace Mimic Defense Technologies in Cloud[EB/OL]. [2024-12-24]. https://api.semanticscholar.org/CorpusID:239433258. |
| [17] | LI Lingshu. Research on Mimic Saas Cloud Security Architecture and Key Technologies[D]. Zhengzhou: Information Engineering University of the Strategic Support Force, 2021. |
| 李凌书. 拟态SaaS云安全体系架构及关键技术研究[D]. 郑州: 战略支援部队信息工程大学, 2021. | |
| [18] |
ZHANG Shuai, GUO Yunfei, HU Hongchao, et al. Atssc: An Attack Tolerant System in Serverless Computing[J]. China Communications, 2024, 21(6): 192-205.
doi: 10.23919/JCC.fa.2021-0635.202406 |
| [19] | KOCHER P, HORN J, FOGH A, et al. Spectre Attacks: Exploiting Speculative Execution[J]. Communications of the ACM, 2020, 63(7): 93-101. |
| [20] | DANIEL K, FRANK G G, ENDA B. DoWNet-Classification of Denial-of-Wallet attacks on serverless application traffic[EB/OL]. [2024-12-24]. https://doi.org/10.1093/cybsec/tyae004. |
| [21] | RADICHEL T. Serverless Attack Vectors[EB/OL]. [2024-12-24]. https://www.classcentral.comhttps://www.classcentral.com/course/youtube-serverless-attack-vectors-140128. |
| [22] | NI Kan, MONDAL S, KABIR H M D, et al. Toward security quantification of serverless computing[EB/OL]. [2024-12-24]. https://doi.org/10.1186/s13677-024-00703-y. |
| [23] | WANG Liang, LI Mengyuan, ZHANG Yinqian, et al. Peeking behind the Curtains of Serverless Platforms[C]// USENIX. 2018 USENIX annual technical conference (USENIX ATC 18). Berkeley: USENIX, 2018: 133-146. |
| [24] | Microsoft Corporation. Azure Functions[EB/OL]. [2024-12-24]. https://azure.microsoft.com/en-us/services/functions/. |
| [25] | Google LLC. Google Cloud Functions[EB/OL]. [2024-12-24]. https://cloud.google.com/functions. |
| [26] | LI Guangsong, WANG Wei, GAI Keke, et al. A Framework for Mimic Defense System in Cyberspace[J]. Signal Process System, 2021, 93: 169-185. |
| [27] | LI Qi, DUAN Pengsong, CAO Yangjie, et al. Summary of Research on Mimic Defense Architecture Design Methods[J]. Journal of Image and Graphics, 2024, 29(8): 2319-2332. |
| 李淇, 段鹏松, 曹仰杰, 等. 拟态防御架构设计方法研究进展[J]. 中国图象图形学报, 2024, 29(8):2319-2332. | |
| [28] | YU Fei. Research and Implementation of Key Technologies for Industrial Network Boundary Mimetic Defense[D]. Zhengzhou: Information Engineering University of Strategic Support Force, 2021. |
| 余飞. 工业网络边界拟态防护关键技术研究及其实现[D]. 郑州: 战略支援部队信息工程大学, 2021. | |
| [29] | WANG Xiaofan. Design and Implementation of a Mimetic Microcontroller System Based on Heterogeneous Redundant Architecture[D]. Nanjing: Southeast University, 2023. |
| 王肖凡. 基于异构冗余架构的拟态微控制器系统的设计与实现[D]. 南京: 东南大学, 2023. | |
| [30] | ALAFAA P. Data Privacy and Data Protection: The Right of User’s and the Responsibility of Companies in the Digital World[EB/OL]. [2024-12-24]. https://ssrn.com/abstract=4005750. |
| [31] | ZENG Liming. Research on Mimic Cloud Service Architecture and Key Technologies[D]. Zhengzhou: Information Engineering University of the Strategic Support Force, 2021. |
| 曾黎明. 拟态云服务架构及关键技术研究[D]. 郑州: 战略支援部队信息工程大学, 2021. | |
| [32] | ZHENG Yu, LI Zheng, XU Xiaolong, et al. Dynamic Defenses in Cyber Security: Techniques, Methods and Challenges[J]. Digital Communications and Networks, 2022, 8(4): 422-435. |
| [33] | ZHANG Shuai, SHANG Ke, GUO Yunfei, et al. Design of Meta-Capability Based Attack-Tolerant System for Cloud-Native Environment[J]. Journal of Information Engineering University, 2022, 23(6): 730-736. |
| 张帅, 商珂, 郭云飞, 等. 基于元能力的云原生攻击容忍系统设计[J]. 信息工程大学学报, 2022, 23(6):730-736. | |
| [34] | Alibaba Cloud. Understanding runtime list and termination strategies to choose the right programming language for function compute (fc)[EB/OL]. [2024-12-24]. https://help.aliyun.com/zh/functioncompute/fc-3-0/user-guide/runtime-overview-3?spm=a2c4g.1118662. |
| [1] | ZHAO Bo, PENG Junru, WANG Yixuan. Network Security Situation Assessment Method Based on Threat Propagation [J]. Netinfo Security, 2025, 25(6): 843-858. |
| [2] | SUN Jianwen, ZHANG Bin, SI Nianwen, FAN Ying. Lightweight Malicious Traffic Detection Method Based on Knowledge Distillation [J]. Netinfo Security, 2025, 25(6): 859-871. |
| [3] | XUN Yijie, CUI Jiarong, MAO Bomin, QIN Junman. Intrusion Detection System for the Controller Area Network Bus of Intelligent Vehicles Based on Federated Learning [J]. Netinfo Security, 2025, 25(6): 872-888. |
| [4] | DENG Dongshang, WANG Weiye, ZHANG Weidong, WU Xuangou. Layered Personalized Federated Learning Guided by Model Feature Orientation [J]. Netinfo Security, 2025, 25(6): 889-897. |
| [5] | LIU Feng, HUANG Hao. A Decentralized Regulatory Architecture Based on Smart Contracts and Prophecy Machines with Active Sensor Networks [J]. Netinfo Security, 2025, 25(6): 898-909. |
| [6] | SHI Kaibo, DING Jia, WANG Jun, CAI Xiao. Supervised Restart-Based Cybersecurity Defense Strategy for Power Systems [J]. Netinfo Security, 2025, 25(6): 910-919. |
| [7] | ZHU Shuaishuai, LIU Keqian. A Masking-Based Selective Federated Distillation Scheme [J]. Netinfo Security, 2025, 25(6): 920-932. |
| [8] | FENG Jingyu, PAN Meng, WANG Jialin, ZHAO Xiang. Deep Semantic Parsing Based Active Defense against API Overstep Vulnerabilities [J]. Netinfo Security, 2025, 25(6): 933-942. |
| [9] | CHEN Da, CAI Xiao, SUN Yanbin, DONG Chongwu. Optimization of Data Conf lict and DDoS Attack Defense Mechanisms in Industrial Control Systems Based on Greedy Algorithm [J]. Netinfo Security, 2025, 25(6): 943-954. |
| [10] | ZHU Zhicheng, CAO Hui, WANG Yinsheng. Research on Active Defense Security System Based on Four-Honey Coordination for Energy Systems [J]. Netinfo Security, 2025, 25(6): 955-966. |
| [11] | GENG Zhiyuan, XU Zexuan, ZHANG Hengwei. A Decision-Making Method for Cloud-Native Moving Target Defense Based on Stochastic Games and DQN Algorithm [J]. Netinfo Security, 2025, 25(6): 967-976. |
| [12] | HU Wenao, YAN Fei, ZHANG Liqiang. A Security Protection Scheme against Memory Side-Channel Attacks on NPU [J]. Netinfo Security, 2025, 25(6): 977-987. |
| [13] | PAN Jing, LI Boxun, WAN Beilin, ZHONG Yantao. An Overview on Lattice-Based Zero-Knowledge Proofs [J]. Netinfo Security, 2025, 25(5): 679-688. |
| [14] | LI Jun’e, MA Ziyu, LU Qiuyu, YU Kailong. An Intelligent Detection Method for IEC 61850 Network Attacks Incorporating Temporal and Sequence Features [J]. Netinfo Security, 2025, 25(5): 689-699. |
| [15] | ZHAO Feng, FAN Song, ZHAO Yanqi, CHEN Qian. Privacy-Preserving Methods for Streaming Data in Wearable Medical Devices Based on Local Differential Privacy [J]. Netinfo Security, 2025, 25(5): 700-712. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||