Netinfo Security ›› 2025, Vol. 25 ›› Issue (5): 700-712.doi: 10.3969/j.issn.1671-1122.2025.05.003
Previous Articles Next Articles
Privacy-Preserving Methods for Streaming Data in Wearable Medical Devices Based on Local Differential Privacy
ZHAO Feng1, FAN Song1( ), ZHAO Yanqi1, CHEN Qian2
), ZHAO Yanqi1, CHEN Qian2
- 1. School of Cyberspace Security, Xi’an University of Posts & Telecommunications, Xi’an 710121, China
2. Institute of Mathematics and Interdisciplinary Sciences, Xidian University, Xi’an 710071, China
-
Received:2024-12-16Online:2025-05-10Published:2025-06-10
CLC Number:
Cite this article
ZHAO Feng, FAN Song, ZHAO Yanqi, CHEN Qian. Privacy-Preserving Methods for Streaming Data in Wearable Medical Devices Based on Local Differential Privacy[J]. Netinfo Security, 2025, 25(5): 700-712.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.05.003
| [1] | LIU Qiang, LI Tong, YU Yang, et al. Data Security and Privacy Preserving Techniques for Wearable Devices a Survey[J]. Journal of Computer Research and Development, 2018, 55(1): 14-29. |
| 刘强, 李桐, 于洋, 等. 面向可穿戴设备的数据安全隐私保护技术综述[J]. 计算机研究与发展, 2018, 55(1): 14-29. | |
| [2] |
ZHANG Wei, ZHOU Yini, ZHOU Yi. Validation of the Watch-Type HUAWEI WATCH D Oscillometric Wrist Blood Pressure Monitor in Adult Chinese[J]. Blood Pressure Monitoring, 2022, 27(5): 353-356.
doi: 10.1097/MBP.0000000000000608 pmid: 35687029 |
| [3] |
CAMPION E W, JARCHO J A. Watched by Apple[J]. New England Journal of Medicine, 2019, 381(20): 1964-1965.
doi: 10.1056/NEJMe1913980 |
| [4] | WANG Qian, ZHANG Yan, LU Xiao, et al. RescueDP: Real-Time Spatio-Temporal Crowd-Sourced Data Publishing with Differential Privacy[C]// IEEE. IEEE INFOCOM 2016-The 35th Annual IEEE International Conference on Computer Communications. New York: IEEE, 2016: 1-9. |
| [5] | ZHANG Hancheng. The Realistic Dilemma and Compliance Response of Health and Medical Data Sharing[J]. Medicine and Philosophy, 2024, 45(17): 52-57. |
| 张汉成. 健康医疗数据共享的现实困境与合规因应[J]. 医学与哲学, 2024, 45(17): 52-57. | |
| [6] | DWORK C, MCSHERRY F, NISSIM K, et al. Calibrating Noise to Sensitivity in Private Data Analysis[C]// Springer. Theory of Cryptography:Third Theory of Cryptography Conference. Heidelberg: Springer, 2006: 265-284. |
| [7] | KASIVISWANATHAN S P, LEE H K, NISSIM K, et al. What Can We Learn Privately?[J]. SIAM Journal on Computing, 2011, 40(3): 793-826. |
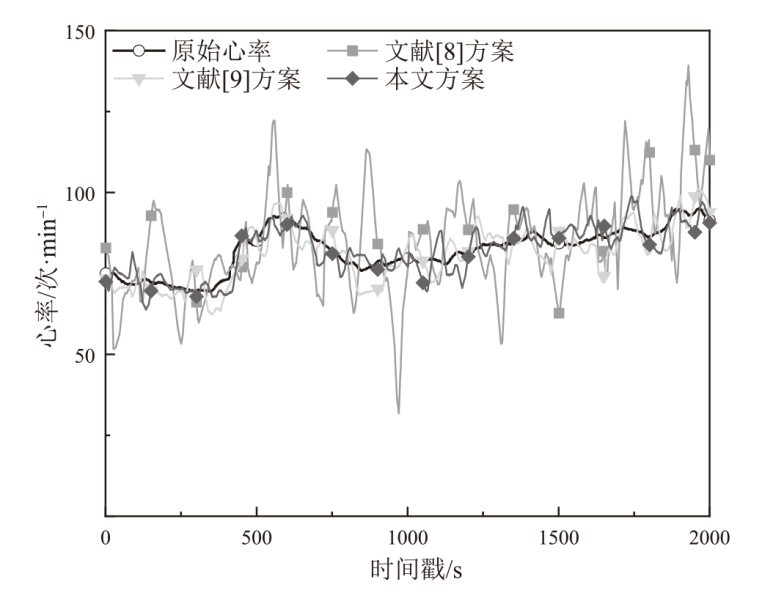
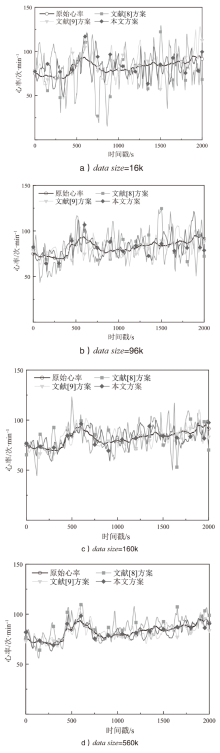
| [8] | KIM J W, JANG B, YOO H. Privacy-Preserving Aggregation of Personal Health Data Streams[EB/OL]. (2018-11-30)[2024-12-02]. https://doi.org/10.1371/journal.pone.0207639. |
| [9] | LI Zhangbing, WANG Baichuan, LI Jinsheng, et al. Local Differential Privacy Protection for Wearable Device Data[EB/OL]. (2022-08-17)[2024-12-02]. https://doi.org/10.1371/journal.pone.0272766. |
| [10] | DUCHI J C, JORDAN M I, WAINWRIGHT M J. Local Privacy and Statistical Minimax Rates[C]// IEEE. 2013 IEEE 54th Annual Symposium on Foundations of Computer Science. New York: IEEE, 2013: 429-438. |
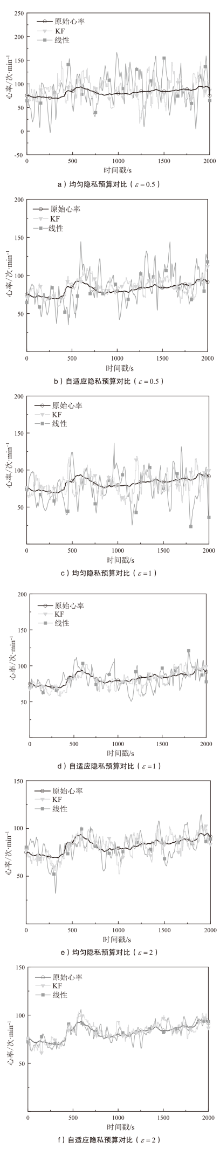
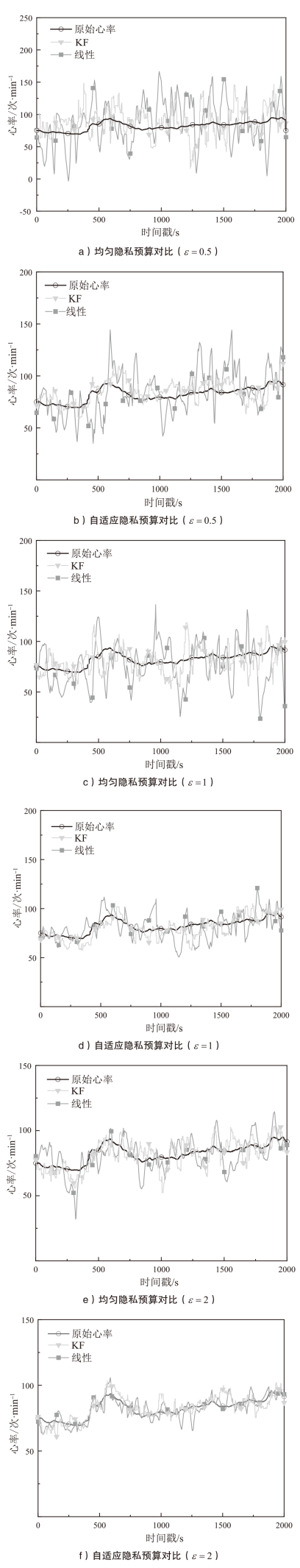
| [11] | KALMAN R E. A New Approach to Linear Filtering and Prediction Problems[J]. Journal of Basic Engineering, 1960, 82(1): 35-45. |
| [12] | HADIAN M, LIANG Xiaohui, ALTUWAIYAN T, et al. Privacy-Preserving Health Data Release with Pattern Consistency[C]// IEEE.GLOBECOM 2016-2016 IEEE Communications Society. New York: IEEE, 2016: 1-6. |
| [13] | PREMA K, SRIHARSHA A. Differential Privacy in Big Data Analytics for Haptic Applications[J]. International Journal of Computer Engineering & Technology, 2017, 8(3): 11-19. |
| [14] | ZHANG Jiajun, LIANG Xiaohui, ZHANG Zhikun, et al. Re-DPoctor: Real-Time Health Data Releasing with W-Day Differential Privacy[C]// IEEE. GLOBECOM 2017-2017 IEEE Global Communications Conference. New York: IEEE, 2017: 1-6. |
| [15] |
GUAN Zhitao, LYU Zefang, DU Xiaojiang, et al. Achieving Data Utility-Privacy Trade off in Internet of Medical Things, a Machine Learning Approach[J]. Future Generation Computer Systems, 2019, 98: 60-68.
doi: 10.1016/j.future.2019.01.058 |
| [16] | HAN Song, ZHAO Shuai, LI Qinghua, et al. PPM-HDA: Privacy-Preserving and Multifunctional Health Data Aggregation with Fault Tolerance[J]. IEEE Transactions on Information Forensics and Security, 2016, 11(9): 1940-1955. |
| [17] | UKIL A, JARA A J, MARIN L. Data-Driven Automated Cardiac Health Management with Robust Edge Analytics and Derisking[EB/OL]. (2019-06-18)[2024-12-01]. https://doi.org/10.3390/s19122733. |
| [18] | SALEHEEN N, CHAKRABORTY S, ALI N, et al. mSieve: Differential Behavioral Privacy in Time Series of Mobile Sensor Data[C]// ACM. The 2016 ACM International Joint Conference. New York: ACM, 2016: 706-717. |
| [19] | STEIL J, HAGESTEDT I, HUANG M X. Privacy Aware Eye Tracking Using Differential Privacy[C]// ACM. The 11th ACM Symposium. New York: ACM, 2019: 1-9. |
| [20] | BOZKIR E, GUNLU O, FUHL W, et al. Differential Privacy for Eye Tracking with Temporal Correlations[EB/OL]. (2021-08-17)[2024-12-01]. https://doi.org/10.1371/journal.pone.0255979. |
| [21] | ZHANG Siqi, LI Xiaohui. Differential Privacy Medical Data Publishing Method Based on Attribute Correlation[EB/OL]. (2022-09-21)[2024-12-01]. https://doi.org/10.1038/s41598-022-19544-3. |
| [22] | YUAN Danni, ZHU Xiaoyan, WEI Mingkui, et al. Collaborative Deep Learning for Medical Image Analysis with Differential Privacy[C]// IEEE. Global Communications Conference. New York: IEEE, 2019: 1-6. |
| [23] | ZHANG Zhenjiang, HAN Bowen, CHAO Hanchi, et al. A New Weight and Sensitivity Based Variable Maximum Distance to Aver-Age Vector Algorithm for Wearable Sensor Data Privacy Protection[J]. IEEE Access, 2019: 104045-101056. |
| [24] | TU Zixuan, LIU Shubo, XIONG Xingxing, et al. Differential Privacy Mean Publishing of Digital Stream Data for Wearable Devices[J]. Computer Application, 2020, 40(6): 1692-1697. |
|
涂子璇, 刘树波, 熊星星, 等. 可穿戴设备的数值型流数据差分隐私均值发布[J]. 计算机应用, 2020, 40(6): 1692-1697.
doi: 10.11772/j.issn.1001-9081.2019111929 |
|
| [25] | KIFER D, LIN Bingrong. Towards an Axiomatization of Statistical Privacy and Utility[C]// ACM. The Twenty-Ninth ACM SIGMOD-SIGACT-SIGART Symposium on Principles of Database Systems. New York: ACM, 2010: 147-158. |
| [26] | REISS A, STRICKER D. Introducing New Benchmarked Dataset for Activity Monitoring[C]// IEEE. The 16th International Symposium on Wearable Computers, ISWC 2012. New York: IEEE, 2012: 108-109. |
| [1] | HU Yuhan, YANG Gao, CAI Hongye, FU Junsong. Privacy Protection of Data Transmission Paths in 3D Distributed Wireless Intelligent Systems [J]. Netinfo Security, 2025, 25(4): 536-549. |
| [2] | HE Ke, WANG Jianhua, YU Dan, CHEN Yongle. Adaptive Sampling-Based Machine Unlearning Method [J]. Netinfo Security, 2025, 25(4): 630-639. |
| [3] | LI Jiadong, ZENG Haitao, PENG Li, WANG Xiaoding. An Anonymous Routing Federated Learning Framework for Data Privacy Protection [J]. Netinfo Security, 2025, 25(3): 494-503. |
| [4] | WEN Jinming, LIU Qing, CHEN Jie, WU Yongdong. Research Current Status and Challenges of Fully Homomorphic Cryptography Based on Learning with Errors [J]. Netinfo Security, 2024, 24(9): 1328-1351. |
| [5] | LIN Zhanhang, XIANG Guangli, LI Zhenpeng, XU Ziyi. Privacy Protection Scheme of Feedforward Neural Network Based on Homomorphic Encryption [J]. Netinfo Security, 2024, 24(9): 1375-1385. |
| [6] | FU Yanming, LU Shenglin, CHEN Jiayuan, QIN Hua. Dynamic Task Allocation for Crowd Sensing Based on Deep Reinforcement Learning and Privacy Protection [J]. Netinfo Security, 2024, 24(3): 449-461. |
| [7] | XU Jianfeng, ZHANG Wei, TU Min, WEI Qingting, LAI Zhanqing, WANG Qianqian. A k-Anonymity Completion Method Generated Based on Semantic Fusion Trajectories [J]. Netinfo Security, 2024, 24(12): 1911-1921. |
| [8] | PEI Bingsen, LI Xin, FAN Zhijie, JIANG Zhangtao. Design and Implementation of a Cross-Domain Secure Sharing Transmission Control System for Video Surveillance Data [J]. Netinfo Security, 2024, 24(11): 1721-1730. |
| [9] | GU Haiyan, LIU Qi, MA Zhuo, ZHU Tao, QIAN Hanwei. Research on Data Noise Addition Method Based on Availability [J]. Netinfo Security, 2024, 24(11): 1731-1738. |
| [10] | SONG Yuhan, ZHU Yuefei, WEI Fushan. An Anomaly Detection Scheme for Blockchain Transactions Based on AdaBoost Model [J]. Netinfo Security, 2024, 24(1): 24-35. |
| [11] | XU Ke, LI Jiayi, JIANG Xinghao, SUN Tanfeng. A Video Gait Privacy Protection Algorithm Based on Sparse Adversarial Attack on Silhouette [J]. Netinfo Security, 2024, 24(1): 48-59. |
| [12] | YU Huifang, QIAO Yifan, MENG Ru. Attribute-Based Anti-Quantum Threshold Ring Signcryption Scheme for Blockchain-Based Finance [J]. Netinfo Security, 2023, 23(7): 44-52. |
| [13] | TANG Yu, ZHANG Chi. A Privacy Protection Scheme for Information-Centric Networking Based on Intel SGX [J]. Netinfo Security, 2023, 23(6): 55-65. |
| [14] | DU Weidong, LI Min, HAN Yiliang, WANG Xu’an. An Efficient Versatile Homomorphic Encryption Framework Based on Ciphertext Conversion Technique [J]. Netinfo Security, 2023, 23(4): 51-60. |
| [15] | YIN Shu, CHEN Xingshu, ZHU Yi, ZENG Xuemei. Anonymous Domain Name Algorithm Based on Character Space Construction [J]. Netinfo Security, 2023, 23(4): 80-89. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||