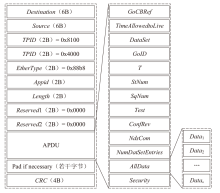
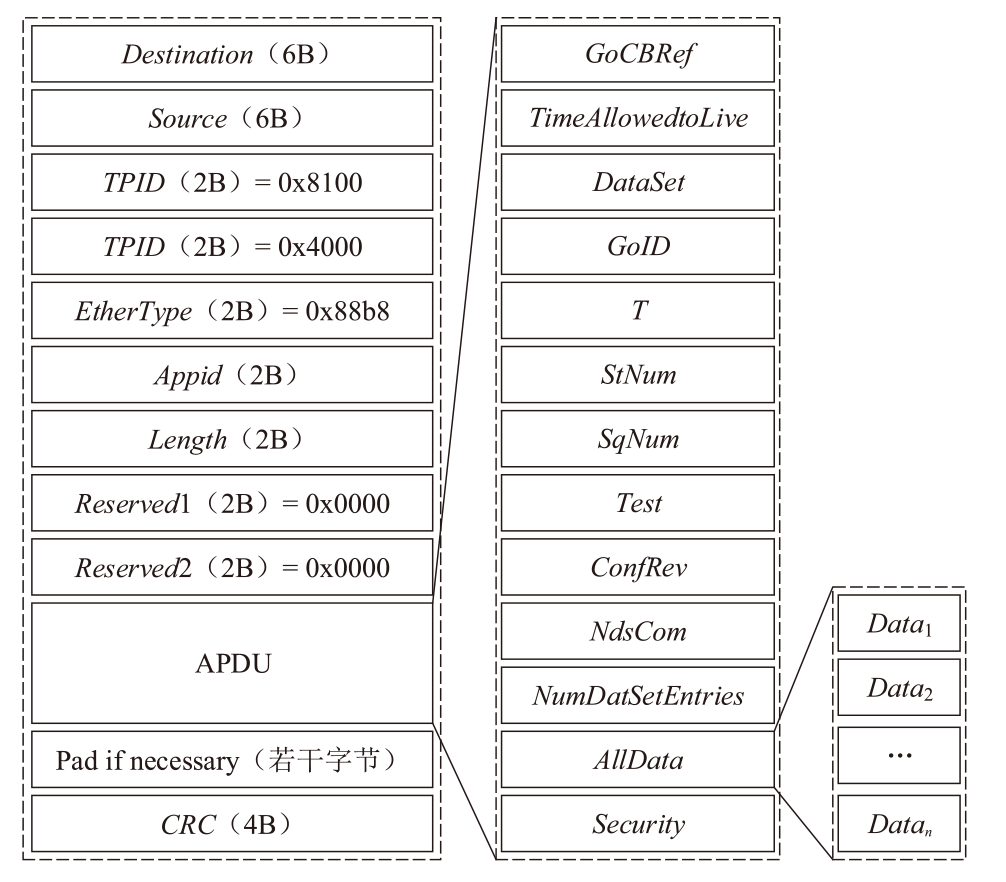
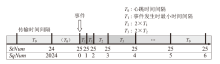
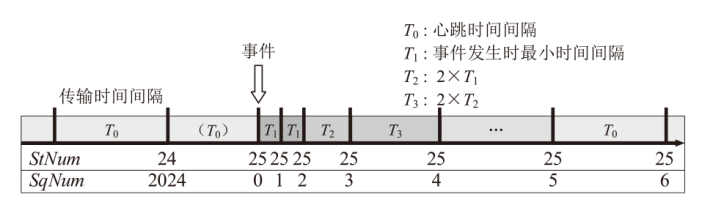
Netinfo Security ›› 2025, Vol. 25 ›› Issue (5): 689-699.doi: 10.3969/j.issn.1671-1122.2025.05.002
Previous Articles Next Articles
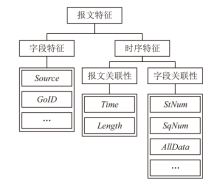
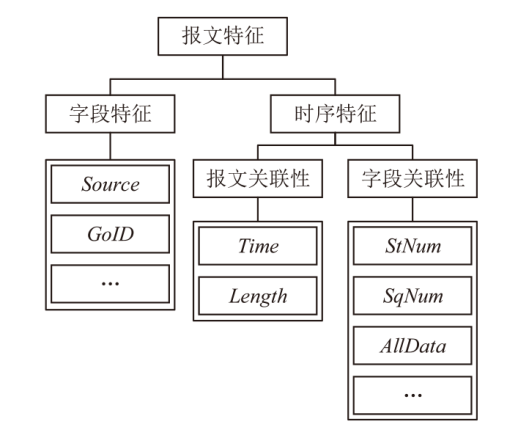
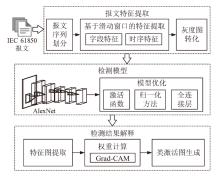
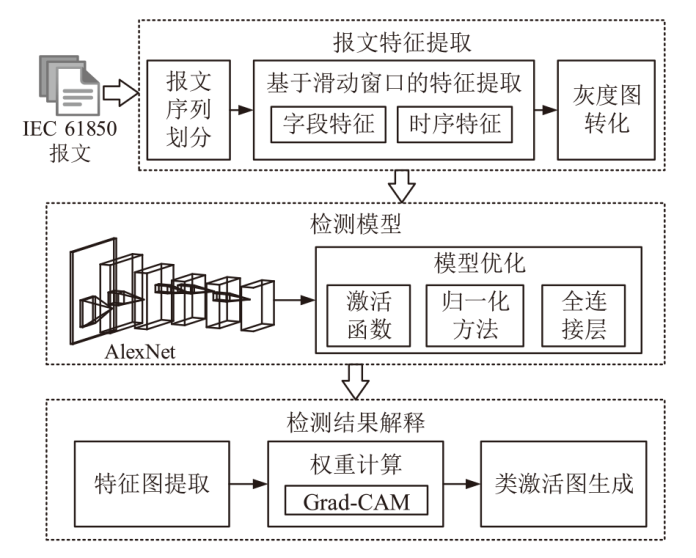
An Intelligent Detection Method for IEC 61850 Network Attacks Incorporating Temporal and Sequence Features
LI Jun’e1,2( ), MA Ziyu1,2, LU Qiuyu1,2, YU Kailong1,2
), MA Ziyu1,2, LU Qiuyu1,2, YU Kailong1,2
- 1. School of Cyber Science and Engineering, Wuhan University, Wuhan 430072, China
2. Key Laboratory of Aerospace Information Security and Trusted Computing of Ministry of Education, Wuhan University, Wuhan 430072, China
-
Received:2024-07-04Online:2025-05-10Published:2025-06-10
CLC Number:
Cite this article
LI Jun’e, MA Ziyu, LU Qiuyu, YU Kailong. An Intelligent Detection Method for IEC 61850 Network Attacks Incorporating Temporal and Sequence Features[J]. Netinfo Security, 2025, 25(5): 689-699.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2025.05.002
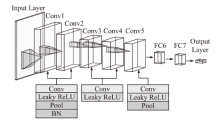
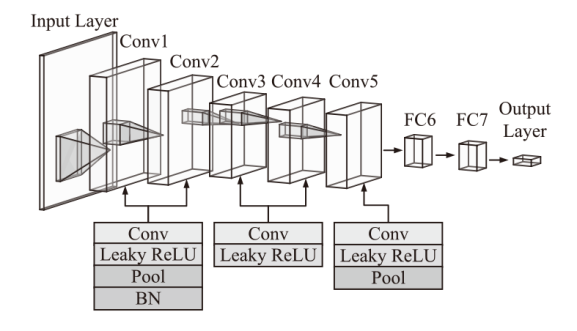
| 模型类型 | 激活函数 | 归一化 方法 | 全连接层 参数 | Acc | F1分数 | 训练时间/min | |
|---|---|---|---|---|---|---|---|
| FC6参数 | FC7参数 | ||||||
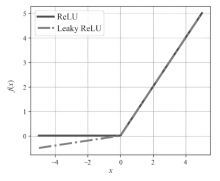
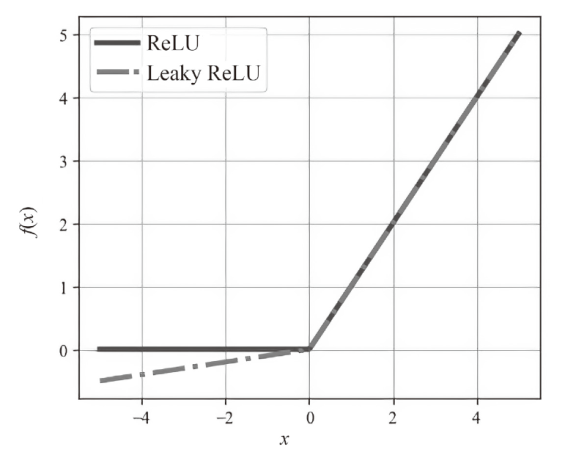
| 本文方法 | Leaky ReLU | 批归一化 | 1024 | 512 | 99.70% | 0.9969 | 209.84 |
| AlexNet | ReLU | LRN | 4096 | 1024 | 98.81% | 0.9881 | 370.65 |
| AlexNet-1 | Leaky ReLU | LRN | 4096 | 1024 | 99.55% | 0.9947 | 390.18 |
| AlexNet-2 | ReLU | 批归一化 | 4096 | 1024 | 99.49% | 0.9945 | 385.10 |
| AlexNet-3 | ReLU | LRN | 1024 | 512 | 98.95% | 0.9886 | 191.53 |
| AlexNet-4 | Leaky ReLU | 批归一化 | 4096 | 1024 | 99.68% | 0.9966 | 401.38 |
| AlexNet-5 | Leaky ReLU | LRN | 1024 | 512 | 99.51% | 0.9949 | 201.75 |
| AlexNet-6 | ReLU | 批归一化 | 1024 | 512 | 99.39% | 0.9938 | 199.68 |
| [1] | IEC 61850-7-420 Communication Networks and Systems for Power Utility Automation-Part 7-420: Basic Communication Structure-Distributed Energy Resources Logical Nodes[S]. London: International Electrotechnical Commission, 2009. |
| [2] | DL/T 860.7420 Communication Networks and Systems for Power Utility Automation Part 7-420: Basic Communication Structure-Distributed Energy Resources Logical Nodes[S]. Beijing: China Electric Power Press, 2012. |
| DL/T 860.7420 电力自动化通信网络和系统第7-420部分:基本通信结构—分布式能源逻辑节点[S]. 北京: 中国电力出版社, 2012. | |
| [3] | ZHANG Jie, LI Jun’e, CHEN Xiong, et al. A Security Scheme for Intelligent Substation Communications Considering Real-Time Performance[J]. Journal of Modern Power Systems and Clean Energy, 2019, 7(4): 948-961. |
| [4] | FIGUEROA-LORENZO S, AÑORGA J, ARRIZABALAGA S. A Survey of IIoT Protocols[J]. ACM Computing Surveys, 2021, 53(2): 1-53. |
| [5] | HABIB H F, LASHWAY C R, MOHAMMED O A. A Review of Communication Failure Impacts on Adaptive Microgrid Protection Schemes and the Use of Energy Storage as a Contingency[J]. IEEE Transactions on Industry Applications, 2018, 54(2): 1194-1207. |
| [6] | QUINCOZES S E, ALBUQUERQUE C, PASSOS D, et al. A Survey on Intrusion Detection and Prevention Systems in Digital Substations[EB/OL]. (2021-01-15)[2024-06-20]. https://doi.org/10.1016/j.comnet.2020.107679. |
| [7] | YOO H, SHON T. Novel Approach for Detecting Network Anomalies for Substation Automation Based on IEC 61850[J]. Multimedia Tools and Applications, 2015, 74(1): 303-318. |
| [8] | USTUN T S, SUHAIL H S M, ULUTAS A, et al. Machine Learning-Based Intrusion Detection for Achieving Cybersecurity in Smart Grids Using IEC 61850 GOOSE Messages[J]. Symmetry, 2021, 13(5): 826-857. |
| [9] | WANG Sheng, TANG Chao, ZHANG Linghao, et al. Research on Network Security Abnormal Flow Analysis Method for IEC 61850 Intelligent Substation[J]. Journal of Chongqing University, 2022, 45(1): 1-8. |
| 王胜, 唐超, 张凌浩, 等. 面向IEC61850智能变电站的网络安全异常流量分析方法[J]. 重庆大学学报, 2022, 45(1): 1-8. | |
| [10] | IJEH V O, MORSI W G. Smart Grid Cyberattack Types Classification: A Fine Tree Bagging-Based Ensemble Learning Approach with Feature Selection[EB/OL]. (2024-06-01)[2024-06-20]. https://doi.org/10.1016/j.segan.2024.101291. |
| [11] | ZHOU Niancheng, LIAO Jianquan, WANG Qianggang, et al. Analysis and Prospect of Deep Learning Application in Smart Grid[J]. Automation of Electric Power Systems, 2019, 43(4): 180-191. |
| 周念成, 廖建权, 王强钢, 等. 深度学习在智能电网中的应用现状分析与展望[J]. 电力系统自动化, 2019, 43(4): 180-191. | |
| [12] | TIAN Weihong. Research and Implementation of Network Anomaly Detection Method in Smart Substation[D]. Shenyang: Chinese Academy of Sciences (Shenyang Institute of Computing Technology), 2020. |
| 田伟宏. 智能变电站网络异常检测方法的研究与实现[D]. 沈阳: 中国科学院大学(中国科学院沈阳计算技术研究所), 2020. | |
| [13] | WANG Xuelei, FIDGE C, NOURBAKHSH G, et al. Anomaly Detection for Insider Attacks from Untrusted Intelligent Electronic Devices in Substation Automation Systems[J]. IEEE Access, 2022, 10: 6629-6649. |
| [14] | ABU N A, MORSI W G. Detection of Cyber-Attacks and Power Disturbances in Smart Digital Substations Using Continuous Wavelet Transform and Convolution Neural Networks[EB/OL]. (2024-04-01)[2024-06-20]. https://doi.org/10.1016/j.epsr.2024.110157. |
| [15] | DUAN Yujing, ZHANG Yupeng. Enhancing Smart Grid Security:A Novel Approach for Efficient Attack Detection Using SMART Framework[EB/OL]. (2024-01-24)[2024-06-20]. https://doi.org/10.1016/j.measen.2023.101015. |
| [16] | HONG J H, LIU C C, GOVINDARASU M. Detection of Cyber Intrusions Using Network-Based Multicast Messages for Substation Automation[C]// IEEE. 2014 IEEE Innovative Smart Grid Technologies. New York: IEEE, 2014: 1-5. |
| [17] | RASHID M T A, YUSSOF S, YUSOFF Y, et al. A Review of Security Attacks on IEC 61850 Substation Automation System Network[C]// IEEE. Proceedings of the 6th International Conference on Information Technology and Multimedia. New York: IEEE, 2014: 5-10. |
| [18] | ZHOU Feiyan, JIN Linpeng, DONG Jun. Review of Convolutional Neural Network[J]. Chinese Journal of Computers, 2017, 40(6): 1229-1251. |
| 周飞燕, 金林鹏, 董军. 卷积神经网络研究综述[J]. 计算机学报, 2017, 40(6): 1229-1251. | |
| [19] | LECUN Y, BOTTOU L, BENGIO Y, et al. Gradient-Based Learning Applied to Document Recognition[J]. Proceedings of the IEEE, 1998, 86(11): 2278-2324. |
| [20] | KRIZHEVSKY A, SUTSKEVER I, HINTON G E. ImageNet Classification with Deep Convolutional Neural Networks[J]. Communications of the ACM, 2017, 60(6): 84-90. |
| [21] | SIMONYAN K, ZISSERMAN A. Very Deep Convolutional Networks for Large-Scale Image Recognition[EB/OL]. (2015-04-10)[2024-06-20]. https://doi.org/10.48550/arXiv.1409.1556. |
| [22] |
GUO Mingang, GONG He. Research on AlexNet Improvement and Optimization Method[J]. Computer Engineering and Applications, 2020, 56(20): 124-131.
doi: 10.3778/j.issn.1002-8331.1907-0135 |
|
郭敏钢, 宫鹤. AlexNet改进及优化方法的研究[J]. 计算机工程与应用, 2020, 56(20): 124-131.
doi: 10.3778/j.issn.1002-8331.1907-0135 |
|
| [23] | IOFFE S, SZEGEDY C. Batch Normalization: Accelerating Deep Network Training by Reducing Internal Covariate Shift[C]// ACM. Proceedings of the 32nd International Conference on International Conference on Machine Learning. New York: ACM, 2015: 448-456. |
| [24] |
CHENG Xiaohui, LI Yu, KANG Yanping. Double Standard Pruning of Convolution Network Based on Feature Extraction of Intermediate Graph[J]. Computer Engineering, 2023, 49(3): 105-112.
doi: 10.19678/j.issn.1000-3428.0064206 |
|
程小辉, 李钰, 康燕萍. 基于中间图特征提取的卷积网络双标准剪枝[J]. 计算机工程, 2023, 49(3): 105-112.
doi: 10.19678/j.issn.1000-3428.0064206 |
|
| [25] |
RUDIN C. Stop Explaining Black Box Machine Learning Models for High Stakes Decisions and Use Interpretable Models Instead[J]. Nature Machine Intelligence, 2019, 1(5): 206-215.
doi: 10.1038/s42256-019-0048-x pmid: 35603010 |
| [26] | ZHOU Bolei, KHOSLA A, LAPEDRIZA A, et al. Learning Deep Features for Discriminative Localization[C]// IEEE. 2016 IEEE Conference on Computer Vision and Pattern Recognition (CVPR). New York: IEEE, 2016: 2921-2929. |
| [27] | SELVARAJU R R, COGSWELL M, DAS A, et al. Grad-CAM: Visual Explanations from Deep Networks via Gradient-Based Localization[C]// IEEE. 2017 IEEE International Conference on Computer Vision (ICCV). New York: IEEE, 2017: 618-626. |
| [28] | ZEMANEK S, HACKER I, WOLSING K, et al. PowerDuck: A GOOSE Data Set of Cyberattacks in Substations[C]// ACM. Proceedings of the 15th Workshop on Cyber Security Experimentation and Test. New York: ACM, 2022: 49-53. |
| [29] | GASPAR J, CRUZ T, LAM C T, et al. Smart Substation Communications and Cybersecurity: A Comprehensive Survey[J]. IEEE Communications Surveys & Tutorials, 2023, 25(4): 2456-2493. |
| [1] | Liangchen CHEN, Baoxu LIU, Shu GAO. Research on Traffic Data Sampling Technology in Network Attack Detection [J]. Netinfo Security, 2019, 19(8): 22-28. |
| [2] | Yuming XIA, Shaoyong HU, Shaomin ZHU, Lili LIU. Research on the Method of Network Attack Detection Based on Convolution Neural Network [J]. Netinfo Security, 2017, 17(11): 32-36. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||