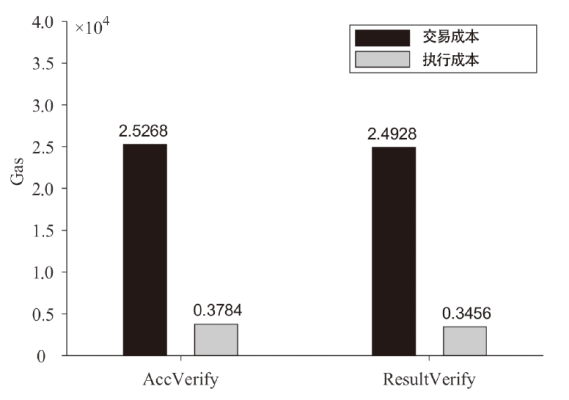
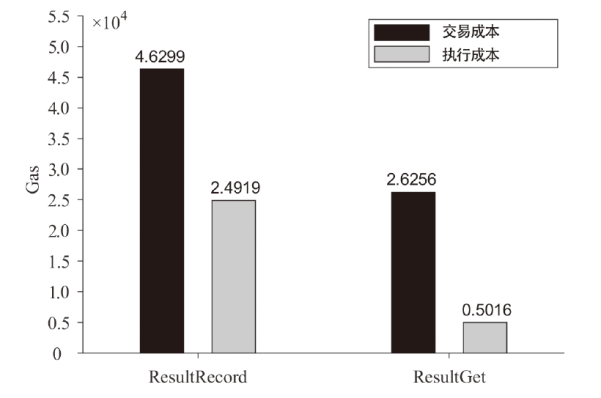
Netinfo Security ›› 2024, Vol. 24 ›› Issue (6): 863-878.doi: 10.3969/j.issn.1671-1122.2024.06.005
Previous Articles Next Articles
Verifiable and Revocable Attribute Encryption Scheme Based on Blockchain
GUO Rui1,2, YANG Xin1,2( ), WANG Junming1,2
), WANG Junming1,2
- 1. School of Cyberspace Security, Xi’an University of Posts and Telecommunications, Xi’an 710121, China
2. National Engineering Research Center for Secured Wireless, Xi’an University of Posts and Telecommunications, Xi’an 710121, China
-
Received:2024-03-06Online:2024-06-10Published:2024-07-05
CLC Number:
Cite this article
GUO Rui, YANG Xin, WANG Junming. Verifiable and Revocable Attribute Encryption Scheme Based on Blockchain[J]. Netinfo Security, 2024, 24(6): 863-878.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.06.005
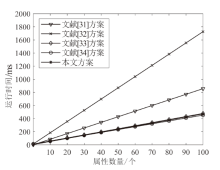
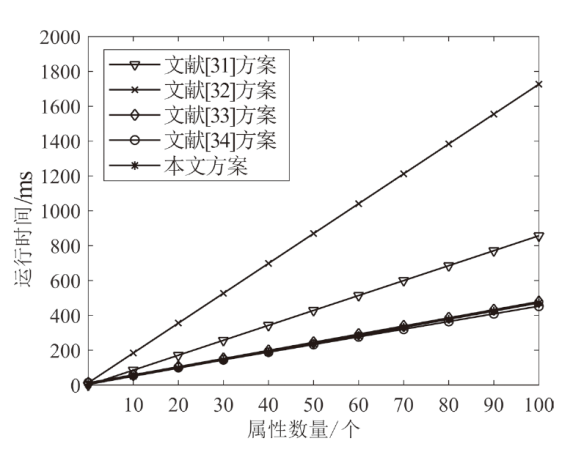
| 方案 算法开销 | 文献[ 方案 | 文献[ 方案 | 文献[ | 文献[ 方案 | 本文 方案 |
|---|---|---|---|---|---|
| 用户密钥 大小 | $2n\left| {{G}_{1}} \right|$ | $\begin{matrix} \left( 2n+2 \right)\left| {{G}_{1}} \right| \\ +n\left| {{Z}_{p}}^{*} \right| \\ \end{matrix}$ | $\left( n+3 \right)\left| {{G}_{1}} \right|$ | $n\left| {{G}_{1}} \right|$ | $n\left| {{G}_{1}} \right|$ |
| 转换密钥 大小 | $\left( n+2 \right)\left| {{G}_{1}} \right|+\left| {{G}_{2}} \right|$ | $\begin{matrix} \left( 2n+2 \right)\left| {{G}_{1}} \right|+ \\ n\left| {{Z}_{p}}^{*} \right| \\ \end{matrix}$ | $\left( n+3 \right)\left| {{G}_{1}} \right|$ | $\left( n+3 \right)\left| {{G}_{1}} \right|$ | $2n\left| {{G}_{1}} \right|$ |
| 密文 大小 | $\begin{align} & 3\left| I \right|\left| {{G}_{1}} \right|+(2\left| I \right|+ \\ & 2)\left| {{G}_{2}} \right|+2\left| I \right|\left| {{Z}_{p}}^{*} \right| \\ \end{align}$ | $\begin{matrix} \left( 3\left| I \right|+1 \right)\left| {{G}_{1}} \right| \\ +\left| {{G}_{2}} \right| \\ \end{matrix}$ | $\begin{matrix} \left( 2\left| I \right|+2 \right)\left| {{G}_{1}} \right| \\ +\left| {{G}_{2}} \right| \\ \end{matrix}$ | $\begin{align} & \left( 3\left| I \right|+2 \right)\left| {{G}_{1}} \right| \\ & +\left| {{G}_{2}} \right|+\left| {{Z}_{p}}^{*} \right| \\ \end{align}$ | $\begin{matrix} 2\left| I \right|\left| {{G}_{1}} \right|+ \\ \left| {{G}_{2}} \right| \\ \end{matrix}$ |
| 转换密文 大小 | $2\left| {{G}_{2}} \right|$ | $2\left| {{G}_{2}} \right|$ | $2\left| {{G}_{1}} \right|+\left| {{G}_{2}} \right|$ | $\left| {{G}_{2}} \right|$ | $\left| {{G}_{2}} \right|$ |
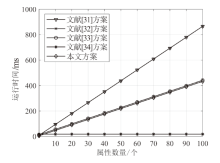
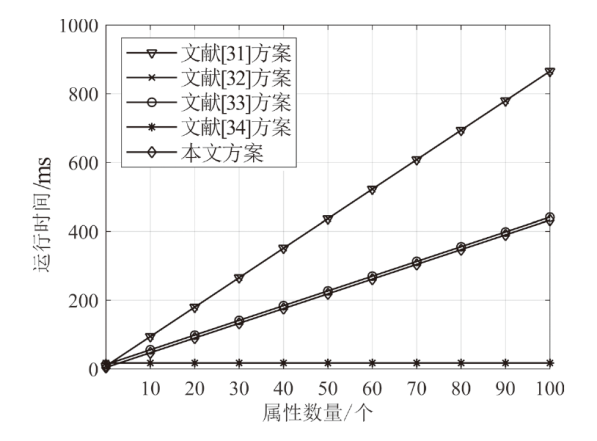
| 方案 算法 | 文献[ 方案 | 文献[ 方案 | 文献[ 方案 | 文献[ 方案 | 本文 方案 |
|---|---|---|---|---|---|
| 用户密钥 生成 | $2nE$ | $\left( 4n+3 \right)E$ | $\begin{align} & \left( n+3 \right)E+ \\ & M+nH \\ \end{align}$ | $\begin{align} & \left( n+1 \right)E+ \\ & nM+nH \\ \end{align}$ | $\begin{align} & P+\left( n+1 \right)E \\ & +nM+nH \\ \end{align}$ |
| 转换密钥 生成 | $\left( 2n+2 \right)E$ | $\left( 2n+2 \right)E$ | $\left( n+3 \right)E$ | $4E+M$ | $\left( n+1 \right)E$ |
| 加密 | $\begin{align} & \left( 3\left| I \right|+1 \right)P \\ & +\left( 9\left| I \right|+1 \right)E \\ \end{align}$ | $\begin{align} & P+(5\left| I \right|+ \\ & 2)E \\ \end{align}$ | $\begin{align} & P+(2\left| I \right|+ \\ & 2)E+(\left| I \right|+ \\ & 2)M+\left| I \right|H \\ \end{align}$ | $\begin{align} & \left| I \right|P+\left( 2\left| I \right|+4 \right)E \\ & +2\left| I \right|M+H \\ \end{align}$ | $\begin{align} & P+3\left| I \right|E+ \\ & \left| I \right|M \\ \end{align}$ |
| 外包解密 | $3\left| I \right|P+5\left| I \right|E$ | $\begin{align} & \left( 3\left| I \right|+1 \right)P \\ & +\left( \left| I \right|+1 \right)E \\ \end{align}$ | $\begin{align} & \left( 2\left| I \right|+2 \right)P+ \\ & 2\left| I \right|E+ \\ & \left( 2\left| I \right|+1 \right)M \\ \end{align}$ | $\begin{align} & \left( \left| I \right|+2 \right)P+ \\ & \left| I \right|E+\left| I \right|M \\ \end{align}$ | $2\left| I \right|P+2\left| I \right|E$ |
| 用户解密 | $E$ | $E$ | $P+E$ | $E$ | $E$ |
| 用户撤销 | — | $\begin{align} & nP+(2n+ \\ & 2)E \\ \end{align}$ | $\begin{align} & \left( n+1 \right)E+ \\ & 2nM+nH \\ \end{align}$ | — | $P+\left( n+1 \right)E$ |
| [1] | SUN Jianfei, XU Guowen, ZHANG Tianwei, et al. Share Your Data Carefree: An Efficient, Scalable and Privacy-Preserving Data Sharing Service in Cloud Computing[J]. IEEE Transactions on Cloud Computing, 2023, 11(1): 822-838. |
| [2] | LIU Jingwei, FAN Yue, SUN Rong, et al. Blockchain-Aided Privacy-Preserving Medical Data Sharing Scheme for E-Healthcare System[J]. IEEE Internet of Things Journal, 2023, 10(24): 21377-21388. |
| [3] | DENG Hua, QIN Zheng, WU Qianhong, et al. Achieving Fine-Grained Data Sharing for Hierarchical Organizations in Clouds[J]. IEEE Transactions on Dependable and Secure Computing, 2023, 20(2): 1364-1377. |
| [4] | SAHAI A, WATERS B. Fuzzy Identity-Based Encryption[C]// Springer. Advances in Cryptology - Eurocrypt 2005. Heidelberg: Springer, 2005: 457-473. |
| [5] | BETHENCOURT J, SAHAI A, WATERS B. Ciphertext-Policy Attribute-Based Encryption[C]// IEEE. Proceedings of The IEEE Symposium on Security and Privacy. New York: IEEE, 2007: 321-334. |
| [6] | GOYAL V, PANDEY O, SAHAI A, et al. Attribute-Based Encryption for Fine-Grained Access Control of Encrypted Data[C]// ACM. Proceedings of the 13th ACM Conference on Computer and Communications Security. New York: ACM, 2006: 89-98. |
| [7] | THUSHARA G A, BHANU S M. A Survey on Secured Data Sharing Using Ciphertext-Policy Attribute-Based Encryption in Cloud[C]// IEEE.Proceedings of the 8th International Conference on Smart Computing and Communications (ICSCC). New York: IEEE, 2021: 170-177. |
| [8] | ZHONG Hong, ZHOU Yiyuan, ZHANG Qinyang, et al. An Efficient and Outsourcing-Supported Attribute-Based Access Control Scheme for Edge-Enabled Smart Healthcare[J]. Future Generation Computer Systems, 2021, 115: 486-496. |
| [9] | GREEN M, HOHENBERGER S, WATERS B. Outsourcing the Decryption of ABE Ciphertexts[C]// USENIX. Proceedings of the 20th Usenix Conference on Security. Berlin:USENIX, 2011: 1-16. |
| [10] | LI Li, ZHU Jiangwen, YANG Chunyan. Overview of Research on the Revocable Mechanism of Attribute-Based Encryption[J]. Netinfo Security, 2023, 23(4): 39-50. |
| 李莉, 朱江文, 杨春艳. 基于属性加密的可撤销机制研究综述[J]. 信息网络安全, 2023, 23(4): 39-50. | |
| [11] | LI Tian, WANG huaqun, HE Debiao, et al. Blockchain-Based Privacy-Preserving and Rewarding Private Data Sharing for IoT[J]. IEEE Internet of Things Journal, 2022, 9(16): 15138-15149. |
| [12] | OLIVEIRA M T D, REIS L H A, VERGINADIS Y, et al. Smartaccess: Attribute-Based Access Control System for Medical Records Based on Smart Contracts[J]. IEEE Access, 2022(10): 117836-117854. |
| [13] | KRAWCZYK H, RABIN T. Chameleon Signatures[C]// NDSS. Proceedings of The Network and Distributed Systems Security Symposium (NDSS). New York: NDSS, 2000: 143-154. |
| [14] | QIN Baodong, DENG R H, LIU Shengli, et al. Attribute-Based Encryption with Efficient Verifiable Outsourced Decryption[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(7): 1384-1393. |
| [15] | WANG Huaqun, HE Debiao, HAN Jinguang. VOD-ADAC: Anonymous Distributed Fine-Grained Access Control Protocol with Verifiable Outsourced Decryption in Public Cloud[J]. IEEE Transactions on Services Computing, 2020, 13(3): 572-583. |
| [16] | QIU Tie, CHI Jiancheng, ZHOU Xiaobo, et al. Edge Computing in Industrial Internet of Things: Architecture, Advances and Challenges[J]. IEEE Communications Surveys & Tutorials, 2020, 22(4): 2462-2488. |
| [17] | ZHONG Hong, ZHOU Yiyuan, ZHANG Qingyang, et al. An Efficient and Outsourcing-Supported Attribute-Based Access Control Scheme for Edge-Enabled Smart Healthcare[J]. Future Generation Computer Systems, 2021, 115: 486-496. |
| [18] | ZHANG Wenfang, CHEN Zhen, LIU Xudong, et al. CP-ABE Scheme Supporting Fine-Grained Attribute Direct Revocation[J]. Journal of Software, 2019, 30(9): 2760-2771. |
| 张文芳, 陈桢, 刘旭东, 等. 支持细粒度属性直接撤销的CP-ABE方案[J]. 软件学报, 2019, 30(9):2760-2771. | |
| [19] |
SUN Lei, ZHAO Zhiyuan, WANG Jianhua, et al. Attribute-Based Encryption Scheme Supporting Attribute Revocation in Cloud Storage Environment[J]. Journal on Communications, 2019, 40(5): 47-56.
doi: 10.11959/j.issn.1000-436x.2019116 |
|
孙磊, 赵志远, 王建华, 等. 云存储环境下支持属性撤销的属性基加密方案[J]. 通信学报, 2019, 40(5):47-56.
doi: 10.11959/j.issn.1000-436x.2019116 |
|
| [20] | RAMU G, REDDY B E, JAYANTHI A, et al. Fine-Grained Access Control of EHRs in Cloud Using CP-ABE with User Revocation[J]. Health and Technology, 2019, 9(4): 487-96. |
| [21] | WEI Jianghong, CHEN Xiaofeng, HUANG Xinyi, et al. RS-HABE: Revocable-Storage and Hierarchical Attribute-Based Access Scheme for Secure Sharing of E-Health Records in Public Cloud[J]. IEEE Transactions on Dependable and Secure Computing, 2021, 18(5): 2301-2315. |
| [22] | GUO Yuyan, LU Zhenhua, GE Hui, et al. Revocable Blockchain-Aided Attribute-Based Encryption with Escrow-Free in Cloud Storage[J]. IEEE Transactions on Computers, 2023, 72(7): 1901-1912. |
| [23] | LIU Jingwei, LI Xiaolu, YE Lin, et al. BPDS: A Blockchain Based Privacy-Preserving Data Sharing for Electronic Medical Records[C]// IEEE. Global Communications Conference. New York: IEEE, 2018: 1-6. |
| [24] | FAN Kai, PAN Qiang, ZHANG Kuan, et al. A Secure and Verifiable Data Sharing Scheme Based on Blockchain in Vehicular Social Networks[J]. IEEE Transactions on Vehicular Technology, 2020, 69(6): 5826-5835. |
| [25] | YAN Guanchen, JIANG Shunrong, LI Shengli, et al. Secure and Efficient Fuzzy Search for EHR Sharing Based on Consortium Blockchain[J]. Journal of Cryptologic Research, 2022, 9(5): 805-819. |
| [26] | WANG Zhiwei, CHEN Qinging, LIU Lei. Permissioned Blockchain-Based Secure and Privacy-Preserving Data Sharing Protocol[J]. IEEE Internet of Things Journal, 2023, 10(12): 10698-10707. |
| [27] | BEIMEL A. Secure Schemes for Secret Sharing and Key Distribution[EB/OL]. [2024-01-06]. https://www.researchgate.net/publication/243781866_Secure_Schemes_for_Secret_Sharing_and_Key_Distribution. |
| [28] | ROUSELAKIS Y, WATERS B. Practical Constructions and New Proof Methods for Large Universe Attribute-Based Encryption[C]// ACM.Proceedings of the 2013 ACM Conference on Computer & Communications Security. New York: ACM, 2013: 463-474. |
| [29] | BENALOH J, MARE M D. One-Way Accumulators: A Decentralized Alternative to Digital Signatures[C]// Springer. Advances in Cryptology—EUROCRYPT. Heidelberg: Springer, 2001: 274-285. |
| [30] | DE C A, IOVINO V. JPBC: Java Pairing Based Cryptography[C]// IEEE. 2011 IEEE Symposium on Computers and Communications (ISCC), New York: IEEE, 2011: 850-855. |
| [31] | DE S J, RUJ S. Efficient Decentralized Attribute-Based Access Control for Mobile Clouds[J]. IEEE Transactions on Cloud Computing, 2017, 8(1): 124-37. |
| [32] | MA Hui, ZHANG Rui, SUN Shuzhou, et al. Server-Aided Fine-Grained Access Control Mechanism with Robust Revocation in Cloud Computing[J]. IEEE Transactions on Services Computing, 2019, 15(1): 164-73. |
| [33] | ZHAO Jing, ZENG Peng, CHOO K K R. An Efficient Access Control Scheme with Outsourcing and Attribute Revocation for Fog-Enabled E-health[J]. IEEE Access, 2021, 9: 13789-13799. |
| [34] |
FAN Kai, XU Huiyue, GAO Longxiang, et al. Efficient and Privacy Preserving Access Control Scheme for Fog-Enabled IoT[J]. Future Generation Computer Systems, 2019, 99: 134-142.
doi: 10.1016/j.future.2019.04.003 |
| [1] | LING Zhi, YANG Ming, YU Jiangyin. Research on Power Security Trading Platform Based on IPFS and Blockchain Technology [J]. Netinfo Security, 2024, 24(6): 968-976. |
| [2] | TIAN Zhao, NIU Yajie, SHE Wei, LIU Wei. A Reputation Evaluation Method for Vehicle Nodes in V2X [J]. Netinfo Security, 2024, 24(5): 719-731. |
| [3] | SHI Runhua, YANG Jingyi, WANG Pengbo, LIU Huawei. Online/Off line Cross-Domain Identity Authentication Scheme Based on Blockchain in Vehicle to Grid [J]. Netinfo Security, 2024, 24(4): 587-601. |
| [4] | HU Haiyang, LIU Chang, WANG Dong, WEI Xu. Clean Energy Data Traceability Mechanism Based on Blockchain [J]. Netinfo Security, 2024, 24(4): 626-639. |
| [5] | XUE Mingzhu, HU Liang, WANG Ming, WANG Feng. TAP Rule Processing System Based on Federated Learning and Blockchain Technology [J]. Netinfo Security, 2024, 24(3): 473-485. |
| [6] | ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment [J]. Netinfo Security, 2024, 24(2): 179-187. |
| [7] | HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain [J]. Netinfo Security, 2024, 24(2): 229-238. |
| [8] | WU Haotian, LI Yifan, CUI Hongyan, DONG Lin. Federated Learning Incentive Scheme Based on Zero-Knowledge Proofs and Blockchain [J]. Netinfo Security, 2024, 24(1): 1-13. |
| [9] | ZHU Guocheng, HE Debiao, AN Haoyang, PENG Cong. The Proxy Voting Scheme Based on the Blockchain and SM9 Digital Signature [J]. Netinfo Security, 2024, 24(1): 36-47. |
| [10] | GONG Pengfei, XIE Sijiang, CHENG Andong. The Multi-Leader Consensus Algorithm Based on Improvements to HotStuff [J]. Netinfo Security, 2023, 23(9): 108-117. |
| [11] | ZHOU Quan, CHEN Minhui, WEI Kaijun, ZHENG Yulong. Blockchain Access Control Scheme with SM9-Based Attribute Encryption [J]. Netinfo Security, 2023, 23(9): 37-46. |
| [12] | ZHAO Jiahao, JIANG Jiajia, ZHANG Yushu. Cross-Chain Data Consistency Verification Model Based on Dynamic Merkle Hash Tree [J]. Netinfo Security, 2023, 23(9): 95-107. |
| [13] | SHAO Zhenzhe, JIANG Jiajia, ZHAO Jiahao, ZHANG Yushu. An Improved Weighted Byzantine Fault Tolerance Algorithm for Cross-Chain System [J]. Netinfo Security, 2023, 23(8): 109-120. |
| [14] | QIN Sihang, DAI Weiqi, ZENG Haiyan, GU Xianjun. Secure Sharing of Power Application Data Based on Blockchain [J]. Netinfo Security, 2023, 23(8): 52-65. |
| [15] | PENG Hanzhong, ZHANG Zhujun, YAN Liyue, HU Chenglin. Research on Intrusion Detection Mechanism Optimization Based on Federated Learning Aggregation Algorithm under Consortium Chain [J]. Netinfo Security, 2023, 23(8): 76-85. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||