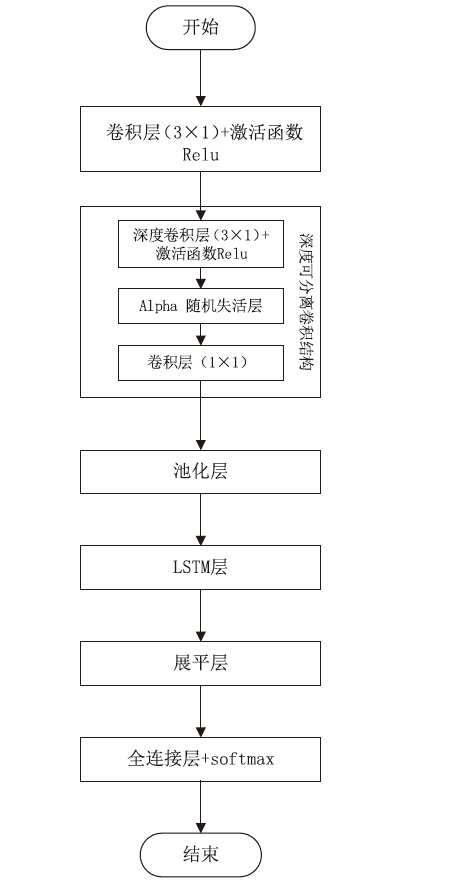
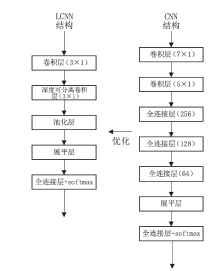
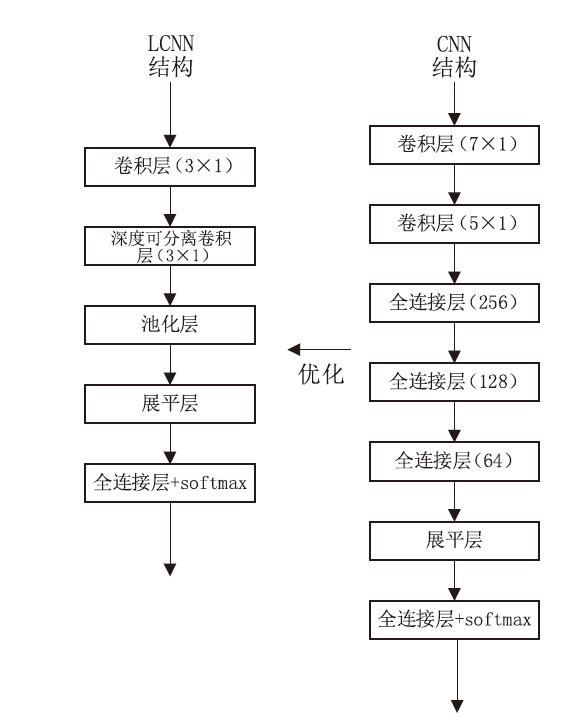
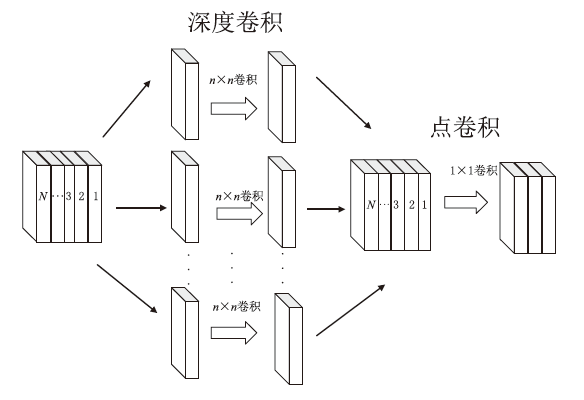
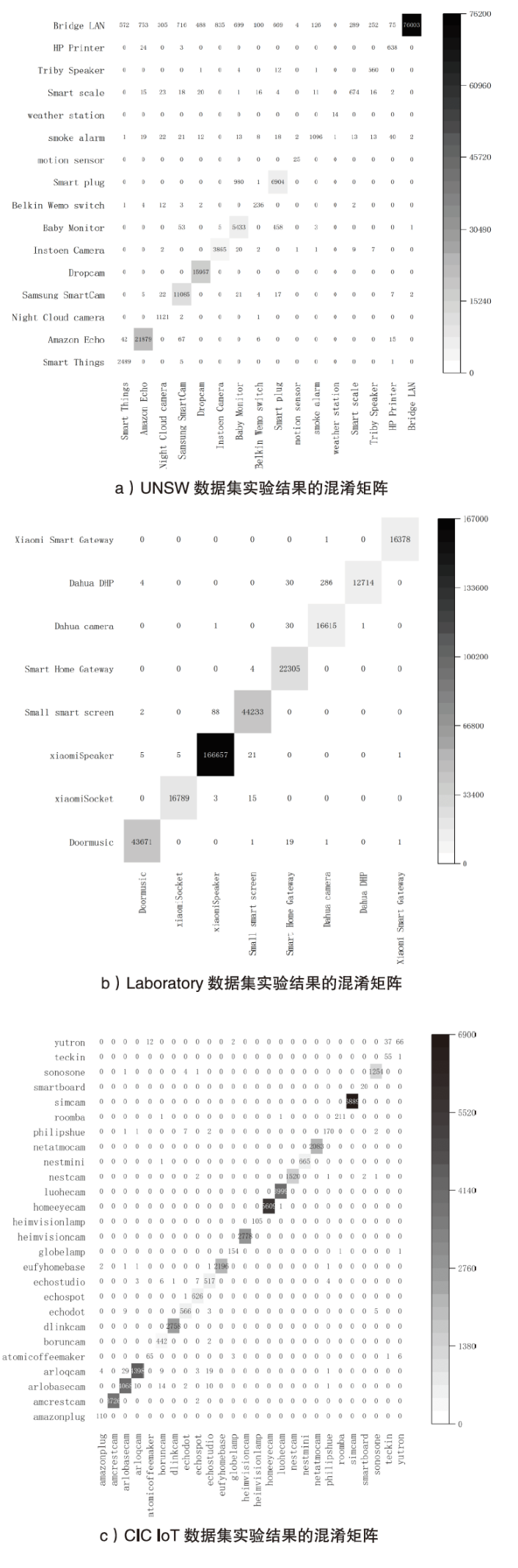
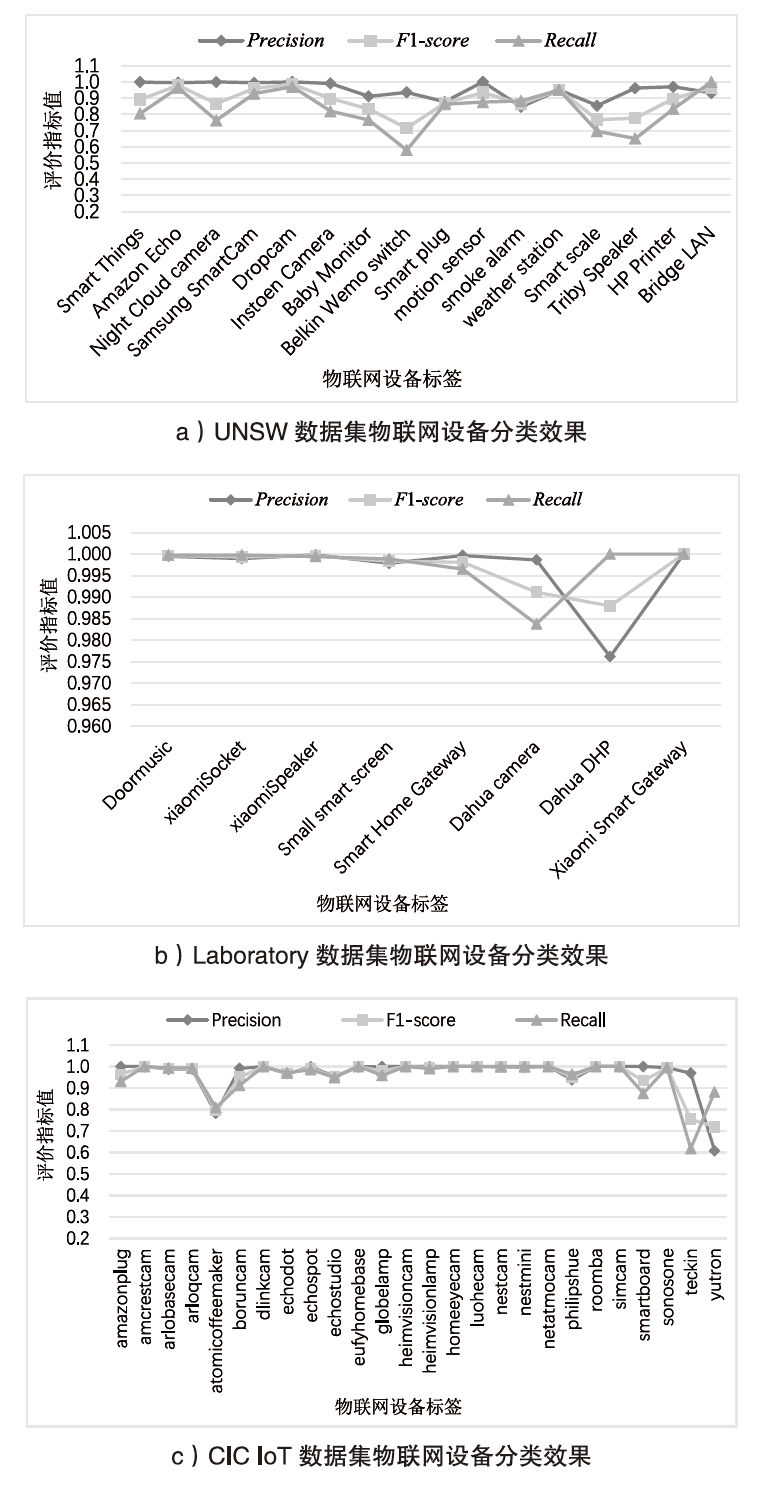
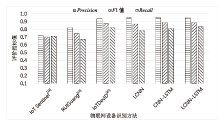
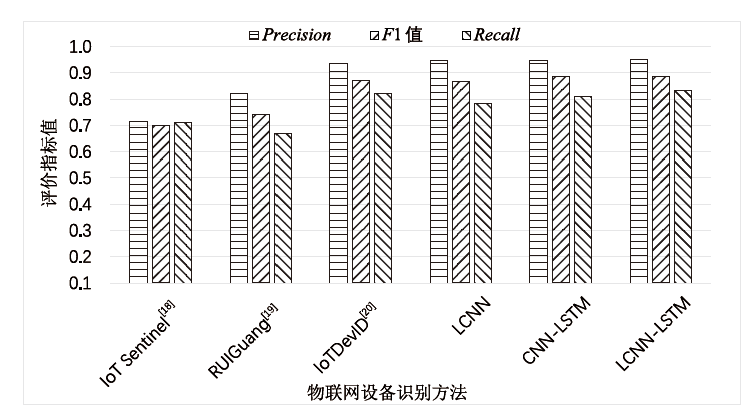
Netinfo Security ›› 2023, Vol. 23 ›› Issue (6): 43-54.doi: 10.3969/j.issn.1671-1122.2023.06.005
Previous Articles Next Articles
IoT Device Identification Method Based on LCNN and LSTM Hybrid Structure
- School of Artificial Intelligence and Computer Science, Jiangnan University, Wuxi 214122, China
-
Received:2023-03-15Online:2023-06-10Published:2023-06-20
CLC Number:
Cite this article
LI Zhihua, WANG Zhihao. IoT Device Identification Method Based on LCNN and LSTM Hybrid Structure[J]. Netinfo Security, 2023, 23(6): 43-54.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.06.005
| [1] | STATISTA R D. Internet of Things-Number of Connected Devices Worldwide 2015-2025[EB/OL]. (2016-11-27)[2023-03-02]. https://www.statista.com/statistics/471264/iot-number-of-connected-devices-worldwide/,2019. |
| [2] | NGUYEN-AN H, SILVERSTON T, YAMAZAKI T, et al. Entropy-Based IoT Devices Identification[C]// IEEE. 2020 21st Asia-Pacific Network Operations and Management Symposium (APNOMS). New York:IEEE, 2020: 73-78. |
| [3] | LI Weiyuan, LI Qin, LIU Rongxin. IoT Devices Identification Based on Machine Learning[C]// IEEE. 2021 IEEE 21st International Conference on Communication Technology (ICCT). New York:IEEE, 2021: 770-777. |
| [4] | AMMAR N, NOIRIE L, TIXEUIL S. Autonomous Identification of IoT Device Types Based on a Supervised Classification[C]// IEEE. ICC 2020-2020 IEEE International Conference on Communications (ICC). New York:IEEE, 2020: 1-6. |
| [5] | ULLAH I, MAHMOUD Q H. Network Traffic Flow Based Machine Learning Technique for IoT Device Identification[C]// IEEE. 2021 IEEE International Systems Conference (SysCon). New York:IEEE, 2021: 1-8. |
| [6] | SUN Yizhen, FU Shupo, ZHANG Shigeng, et al. Accurate IoT Device Identification from Merely Packet Length[C]// IEEE. 2020 16th International Conference on Mobility, Sensing and Networking (MSN). New York:IEEE, 2020: 774-778. |
| [7] | ZHANG Liwu, GONG Liangliang, QIAN Hankun. An Effiective IoT Device Identification Using Machine Learning Algorithm[C]// IEEE. 2020 IEEE 6th International Conference on Computer and Communications (ICCC). New York:IEEE, 2020: 874-877. |
| [8] | NGUYEN T D, MARCHAL S, MIETTINEN M, et al. DIoT: A Federated Self-Learning Anomaly Detection system for IoT[C]// IEEE. 2019 IEEE 39th International Conference on Distributed Computing Systems (ICDCS). New York:IEEE, 2019: 756-767. |
| [9] | YIN Feihong, LI Yang, WANG Yuchen, et al. IoT etei: End-to-End IoT Device Identification Method[C]// IEEE. 2021 IEEE Conference on Dependable and Secure Computing (DSC). New York:IEEE, 2021: 1-8. |
| [10] | CHEN Qinggang, DU Yanhui, HAN Yi, et al. IoT Device Recognition Model Based on Depthwise Separable Convolution[J]. Netinfo Seurity, 2021, 21(9): 67-73. |
| 陈庆港, 杜彦辉, 韩奕, 等. 基于深度可分离卷积的物联网设备识别模型[J]. 信息网络安全, 2021, 21(9): 67-73. | |
| [11] |
QING Guangwei, WANG Huifang, GUO Liang, et al. Device Type Identification via Network Traffic and Lightweight Convolutional Neural Network for Internet of Things[J]. IEEE Access, 2020, 8: 200219-200228.
doi: 10.1109/Access.6287639 URL |
| [12] |
RADHAKRISHNAN S V, ULUAGAC A S, BEYAH R. GTID: A Technique for Physical Device and Device Type Fingerprinting[J]. IEEE Transactions on Dependable and Secure Computing, 2014, 12(5): 519-532.
doi: 10.1109/TDSC.2014.2369033 URL |
| [13] |
KOHNO T, BROIDO A, CLAFFY K C. Remote Physical Device Fingerprinting[J]. IEEE Transactions on Dependable and Secure Computing, 2005, 2(2): 93-108.
doi: 10.1109/TDSC.2005.26 URL |
| [14] | LANZE F, PANCHENKO A, BRAATZ B, et al. Clock Skew Based Remote Device Fingerprinting Demystified[C]// IEEE. 2012 IEEE Global Communications Conference (GLOBECOM). New York:IEEE, 2012: 813-819. |
| [15] | FENG Xuan, LI Qiang, ZHU Hongsong, et al. Active Profiling of Physical Devices at Internet Scale[C]// IEEE. 2016 25th International Conference on Computer Communication and Networks (ICCCN). New York:IEEE, 2016: 1-9. |
| [16] | AMMAR N, NOIRIE L, TIXEUIL S. Network-Protocol-Based IoT Device Identification[C]// IEEE. 2019 Fourth International Conference on Fog and Mobile Edge Computing (FMEC). New York:IEEE, 2019: 204-209. |
| [17] |
YU Changhong, LU Ya, WANG Haixin, et al. IoT Device Traffic Classification Algorithm Based on Sliding Time Window[J]. Computer Engineering, 2022, 10(8): 1-13.
doi: 10.1007/BF01206535 URL |
| 余长宏, 陆雅, 王海鑫, 高明. 基于滑动时间窗的物联网设备流量分类算法[J]. 计算机工程: 2022, 10(8): 1-13. | |
| [18] | MIETTINEN M, MARCHAL S, HAFEEZ I, et al. IoT Sentinel: Automated Device-Type Identification for Security Enforcement in IoT[C]// IEEE. 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS). New York:IEEE, 2017: 2177-2184. |
| [19] | LI Ruiguang, DUAN Pengyu, SHEN Meng, et al. Traffic Classification Algorithm of Internet of Things Devices Based on Random Forest[J]. Journal of Beijing University of Aeronautics and Astronautics, 2022, 48(2): 233-239. |
| 李锐光, 段鹏宇, 沈蒙, 等. 基于随机森林的物联网设备流量分类算法[J]. 北京航空航天大学学报, 2022, 48(2): 233-239. | |
| [20] |
KOSTAS K, JUST M, Lones M A. IoTDevID: A Behavior-Based Device Identification Method for the IoT[J]. IEEE Internet of Things Journal, 2022, 9(23): 23741-23749.
doi: 10.1109/JIOT.2022.3191951 URL |
| [21] | HOWARD A G, ZHU Menglong, CHEN Bo, et al. Mobilenets: Efficient Convolutional Neural Networks for Mobile Vision Applications[EB/OL]. (2017-04-17)[2023-03-02]. http://arxiv.org/abs/1704.04861, 2017-04-17. |
| [22] |
GREFF K, SRIVASTAVA R K, KOUTNÍK J, et al. LSTM: A Search Space Odyssey[J]. IEEE Transactions on Neural Networks and Learning Systems, 2016, 28(10): 2222-2232.
doi: 10.1109/TNNLS.2016.2582924 URL |
| [23] | SIVANATHAN A, SHERRATT D, GHARAKHEILI H H, et al. Characterizing and Classifying IoT Traffic in Smart Cities and Campuses[C]// IEEE. 2017 IEEE Conference on Computer Communications Workshops (INFOCOM WKSHPS). New York:IEEE, 2017: 559-564. |
| [24] | DADKHAH S, MAHDIKHANI H, DANSO P K, et al. Towards the Development of a Realistic Multidimensional IoT Profiling Dataset[C]// IEEE. 2022 19th Annual International Conference on Privacy, Security & Trust (PST). New York:IEEE, 2022: 1-11. |
| [1] | TAN Liuyan, RUAN Shuhua, YANG Min, CHEN Xingshu. Educational Data Classification Based on Deep Learning [J]. Netinfo Security, 2023, 23(3): 96-102. |
| [2] | LIU Xiangyu, LU Tianliang, DU Yanhui, WANG Jingxiang. Lightweight IoT Intrusion Detection Method Based on Feature Selection [J]. Netinfo Security, 2023, 23(1): 66-72. |
| [3] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| [4] | ZHANG Xuewang, LIU Yufan. Identity Traceable Anonymous Authentication Scheme for Nodes in the Perception Layer of IoT [J]. Netinfo Security, 2022, 22(9): 55-62. |
| [5] | GAO Bo, CHEN Lin, YAN Yingjian. Research on Side Channel Attack Based on CNN-MGU [J]. Netinfo Security, 2022, 22(8): 55-63. |
| [6] | ZHAO Hong, LI Shan, ZUO Peiliang, WEI Zhanzhen. Security Resource Allocation Method for Internet of Things Based on Reinforcement Learning [J]. Netinfo Security, 2022, 22(6): 44-52. |
| [7] | ZHANG Guanghua, YAN Fengru, ZHANG Dongwen, LIU Xuefeng. Insider Threat Detection Model Based on LSTM-Attention [J]. Netinfo Security, 2022, 22(2): 1-10. |
| [8] | YIN Ying, ZHOU Zhihong, YAO Lihong. Research on LSTM-Based CAN Intrusion Detection Model [J]. Netinfo Security, 2022, 22(12): 57-66. |
| [9] | HAN Li, SONG Jixiang, SUN Shimin. Moving Target Defense Mechanism Research Based on Device Address in SD-IoT [J]. Netinfo Security, 2022, 22(11): 36-46. |
| [10] | LI Tong, REN Shuai, WANG Gang, MENG Qingyu. Cloud-edge-device Collaborative Integrity Verification Scheme Based on Chameleon Authentication Tree for Streaming Data [J]. Netinfo Security, 2022, 22(1): 37-45. |
| [11] | CHEN Qinggang, DU Yanhui, HAN Yi, LIU Xiangyu. IoT Device Recognition Model Based on Depthwise Separable Convolution [J]. Netinfo Security, 2021, 21(9): 67-73. |
| [12] | WU Kehe, CHENG Rui, ZHENG Bihuang, CUI Wenchao. Research on Security Communication Protocol of Power Internet of Things [J]. Netinfo Security, 2021, 21(9): 8-15. |
| [13] | LI Qun, DONG Jiahan, GUAN Zhitao, WANG Chao. A Clustering and Classification-based Malicious Attack Detection Method for Internet of Things [J]. Netinfo Security, 2021, 21(8): 82-90. |
| [14] | LIU Xin, GUO Zhenbin, SONG Yuchen. An Authentication Scheme Based on SGX for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(6): 1-10. |
| [15] | LI Tong, ZHOU Xiaoming, REN Shuai, XU Jian. Light-weight Mutual Authentication Protocol for Mobile Edge Computing [J]. Netinfo Security, 2021, 21(11): 58-64. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||