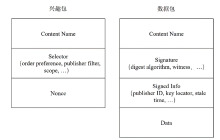
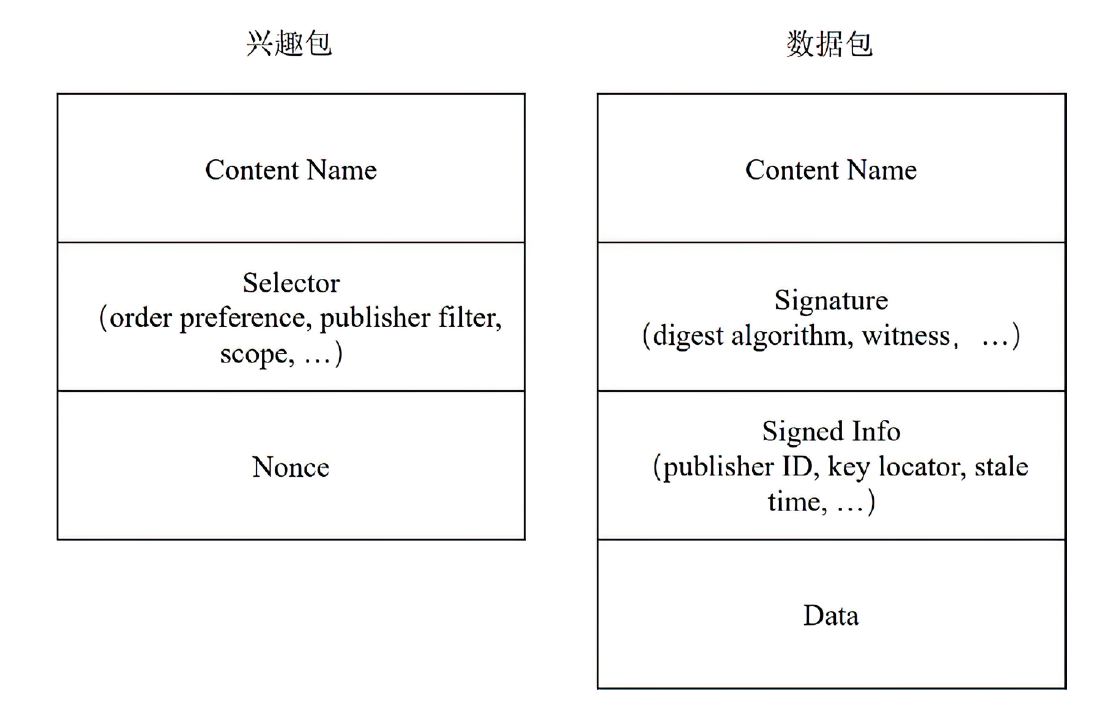
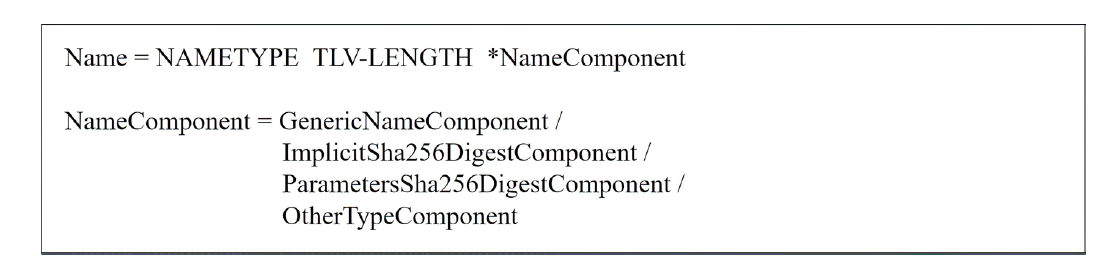
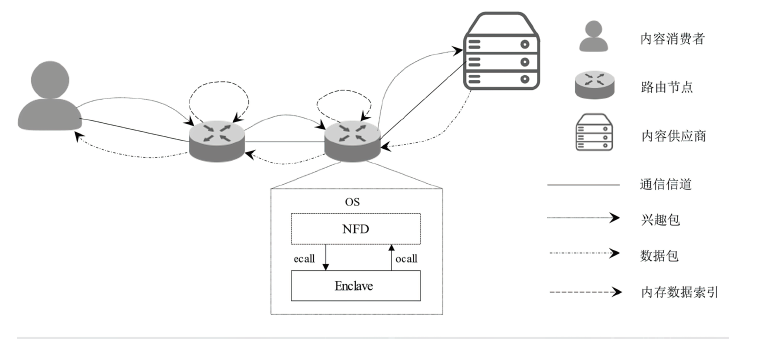
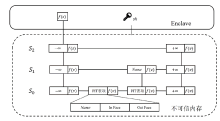
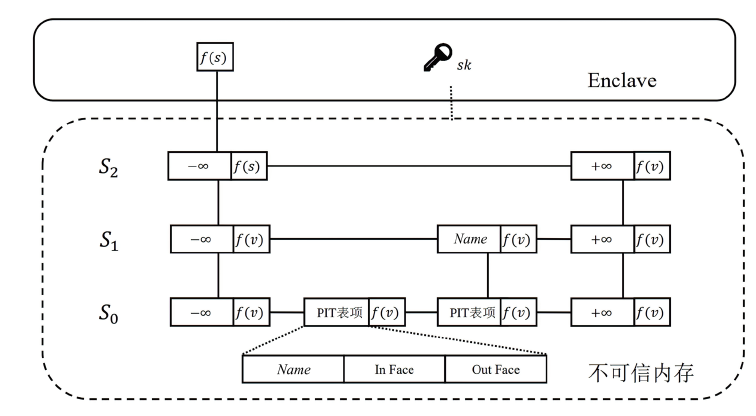
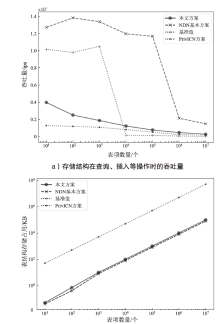
| [1] |
GHODSI A, SHENKER S, KOPONEN T, et al. Information-Centric Networking: Seeing the Forest for the Trees[C]// ACM.Proceedings of the 10th ACM Workshop on Hot Topics in Networks. New York: ACM, 2011: 1-6.
|
| [2] |
FURDEK M, WOSINSKA L, GOŚCIEŃ R, et al. An Overview of Security Challenges in Communication Networks[C]// IEEE. 2016 8th International Workshop on Resilient Networks Design and Modeling (RNDM). New York:IEEE, 2016: 43-50.
|
| [3] |
AHLGREN B, DANNEWITZ C, IMBRENDA C, et al. A Survey of Information-Centric Networking[J]. IEEE Communications Magazine, 2012, 50(7): 26-36.
|
| [4] |
BERTINO E, NABEEL M. Securing Named Data Networks: Challenges and the Way Forward[C]// ACM. Proceedings of the 23nd ACM on Symposium on Access Control Models and Technologies. New York: ACM, 2018: 51-59.
|
| [5] |
BARDHI E, CONTI M, LAZZERETTI R, et al. Security and Privacy of IP-ICN Coexistence: A Comprehensive Survey[EB/OL]. (2022-09-06)[2023-03-20]. https://arxiv.org/abs/2209.02835.
|
| [6] |
JACOBSON V, SMETTERS D K, THORNTON J D, et al. Networking Named Content[J]. Communications of the ACM, 2012, 55(1): 117-124.
|
| [7] |
GRAMPP F T, MORRIS R H. The Unix System: Unix Operating System Security[J]. AT&T Bell Laboratories Technical Journal, 1984, 63(8): 1649-1672.
|
| [8] |
FOTIOU N, POLYZOS G C. Name-Based Security for Information-Centric Networking Architectures[J]. Future Internet, 2019, 11(11): 1-13.
doi: 10.3390/fi11010001
URL
|
| [9] |
WU Danye, XU Zhiwei, CHEN Bo, et al. What if Routers are Malicious? Mitigating Content Poisoning Attack in NDN[C]// IEEE. IEEE International Conference on Trust, Security and Privacy in Computing and Communications (TrustCom). New York:IEEE, 2016: 481-488.
|
| [10] |
COSTAN V, DEVADAS S. Intel SGX Explained[EB/OL]. (2016-01-31)[2023-03-20]. https://ia.cr/2016/086.
|
| [11] |
ZHANG Zhiyi, WON S Y, ZHANG Lixia. Investigating the Design Space for Name Confidentiality in Named Data Networking[C]// IEEE. MILCOM 2021-2021 IEEE Military Communications Conference (MILCOM). New York:IEEE, 2021: 570-576.
|
| [12] |
CHAABANE A, DE CRISTOFARO E, KAAFAR M A, et al. Privacy in Content-Oriented Networking: Threats and Countermeasures[J]. ACM SIGCOMM Computer Communication Review, 2013, 43(3): 25-33.
doi: 10.1145/2500098.2500102
URL
|
| [13] |
BRODER A, MITZENMACHER M. Network Applications of Bloom Filters: A Survey[J]. Internet Mathematics, 2004, 1(4): 485-509.
doi: 10.1080/15427951.2004.10129096
URL
|
| [14] |
BERNARDINI C, MARCHAL S, ASGHAR M R, et al. PrivICN: Privacy-Preserving Content Retrieval in Information-Centric Networking[J]. Computer Networks, 2019, 149: 13-28.
doi: 10.1016/j.comnet.2018.11.012
URL
|
| [15] |
GUO Xian, CHEN Cheng, ZHANG Majiang, et al. Privacy-Aware Transmission Scheme Based on Homomorphic Proxy Re-Encryption for NDN[J]. International Journal of Security and Networks, 2018, 13(1): 58-70.
doi: 10.1504/IJSN.2018.090646
URL
|
| [16] |
BONEH D, DI CRESCENZO G, OSTROVSKY R, et al. Public Key Encryption with Keyword Search[C]// Springer. International Conference on the Theory and Applications of Cryptographic Techniques. Berlin:Springer, 2004: 506-522.
|
| [17] |
KO K T, HLAING H H, MAMBO M. A PEKS-Based NDN Strategy for Name Privacy[J]. Future Internet, 2020, 12(8): 1-22.
doi: 10.3390/fi12010001
URL
|
| [18] |
DIBENEDETTO S, GASTI P, TSUDIK G, et al. ANDaNA: Anonymous Named Data Networking Application[EB/OL]. (2012-01-10)[2023-03-20]. https://arxiv.org/abs/1112.2205.
|
| [19] |
SYVERSON P, DINGLEDINE R, MATHEWSON N. Tor: The Second Generation Onion Router[C]// USENIX. Proceedings of the 13th USENIX Security Symposium. San Diego: USENIX, 2004: 303-320.
|
| [20] |
GOODRISH M T, TAMASSIA R, SCHWERIN A. Implementation of an Authenticated Dictionary with Skip Lists and Commutative Hashing[C]// IEEE. Proceedings DARPA Information Survivability Conference and Exposition II. DISCEX'01. New York:IEEE, 2001, 2: 68-82.
|
| [21] |
SPRING N, MAHAJAN R, WETHERALL D. Measuring ISP Topologies with Rocketfuel[J]. ACM SIGCOMM Computer Communication Review, 2002, 32(4): 133-145.
doi: 10.1145/964725.633039
URL
|