Netinfo Security ›› 2023, Vol. 23 ›› Issue (3): 56-61.doi: 10.3969/j.issn.1671-1122.2023.03.006
Previous Articles Next Articles
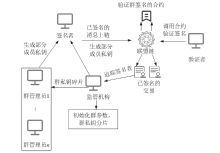
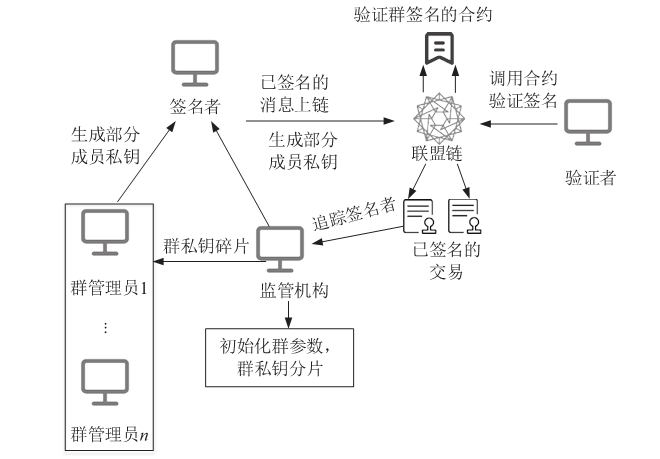
Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption
ZHANG Xuewang( ), ZHANG Hao, YAO Yaning, FU Jiali
), ZHANG Hao, YAO Yaning, FU Jiali
- School of Software Engineering, Chongqing University of Posts and Telecommunications, Chongqing 400065, China
-
Received:2022-10-28Online:2023-03-10Published:2023-03-14 -
Contact:ZHANG Xuewang E-mail:zhangxw@cqupt.edu.cn
CLC Number:
Cite this article
ZHANG Xuewang, ZHANG Hao, YAO Yaning, FU Jiali. Privacy Protection Scheme of Consortium Blockchain Based on Group Signature and Homomorphic Encryption[J]. Netinfo Security, 2023, 23(3): 56-61.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.03.006
| [1] | LI Juanjuan, YUAN Yong, WANG Feiyue. Blockchain-Based Digital Currency: The State of the Art and Future Trends[J]. Acta Automatica Sinica, 2021, 47(4): 715-729. |
| 李娟娟, 袁勇, 王飞跃. 基于区块链的数字货币发展现状与展望[J]. 自动化学报, 2021, 47(4):715-729. | |
| [2] | WANG Chenxu, CHENG Jiacheng, SANG Xinxin, et al. Data Privacy-Preserving for Blockchain: State of the Art and Trends[J]. Journal of Computer Research and Development, 2021, 58(10): 2099-2119. |
| 王晨旭, 程加成, 桑新欣, 等. 区块链数据隐私保护:研究现状与展望[J]. 计算机研究与发展, 2021, 58(10):2099-2119. | |
| [3] | YANG Yatao, CAI Juliang, ZHANG Xiaowei, et al. Privacy Preserving Scheme in Block Chain with Provably Secure Based on SM9 Algorithm[J]. Journal of Software, 2019, 30(6): 1692-1704. |
| 杨亚涛, 蔡居良, 张筱薇, 等. 基于SM9算法可证明安全的区块链隐私保护方案[J]. 软件学报, 2019, 30(6):1692-1704. | |
| [4] | YAO Qian, ZHANG Dawei. Survey on Identity Management in Blockchain[J]. Journal of Software, 2021, 32(7): 2260-2286. |
| 姚前, 张大伟. 区块链系统中身份管理技术研究综述[J]. 软件学报, 2021, 32(7):2260-2286. | |
| [5] | ZHU Liehuang, GAO Feng, SHEN Meng, et al. Survey on Privacy Preserving Techniques for Blockchain Technology[J]. Journal of Computer Research and Development, 2017, 54(10): 2170-2186. |
| 祝烈煌, 高峰, 沈蒙, 等. 区块链隐私保护研究综述[J]. 计算机研究与发展, 2017, 54(10):2170-2186. | |
| [6] | ZHU Bian, REN Guoheng, ZHU Hai, et al. Security Research of the Trusted Computing Enhance the P2P Technology in the Cloud Environment[J]. Journal of Chinese Computer Systems, 2015, 36(3): 534-538. |
| 朱变, 任国恒, 朱海, 等. 可信计算增强云环境下P2P技术的安全性研究[J]. 小型微型计算机系统, 2015, 36(3):534-538. | |
| [7] |
ZHANG Xuewang, LI Zhihong, LIN Jinzhao. Privacy Protection Scheme Based on Fair Blind Signature and Hierarchical Encryption for Consortium Blockchain[J]. Journal on Communications, 2022, 43(8): 131-141.
doi: 10.11959/j.issn.1000-436x.2022162 |
|
张学旺, 黎志鸿, 林金朝. 基于公平盲签名和分级加密的联盟链隐私保护方案[J]. 通信学报, 2022, 43(8):131-141.
doi: 10.11959/j.issn.1000-436x.2022162 |
|
| [8] | HONG Xuan, ZHANG Xuxia. Forward Secure Group Signature Scheme Based on Chinese Remainder Theorem[J]. Application Research of Computers, 2020, 37(9): 2806-2810. |
| 洪璇, 张绪霞. 基于中国剩余定理的前向安全群签名方案[J]. 计算机应用研究, 2020, 37(9):2806-2810. | |
| [9] | CHEN Yameng, CHENG Xiangguo, WANG Shuo, et al. Research on Certificateless Group Signature Scheme Based on Bilinear Pairings[J]. Netinfo Security, 2017, 17(3): 53-58. |
| 陈亚萌, 程相国, 王硕, 等. 基于双线性对的无证书群签名方案研究[J]. 信息网络安全, 2017, 17(3):53-58. | |
| [10] | YE Qing, ZHAO Nannan, ZHAO Zongqu, et al. Efficient Fully Dynamic Group Signature Scheme from Lattice[J]. Computer Engineering, 2021, 47(2): 160-167, 175. |
| 叶青, 赵楠楠, 赵宗渠, 等. 格上高效的完全动态群签名方案[J]. 计算机工程, 2021, 47(2):160-167,175. | |
| [11] | LI Li, DU Huina, LI Tao. Blockchain Supervisable Privacy Protection Scheme Based on Group Signature and Attribute Encryption[J]. Computer Engineering, 2022, 48(6): 132-138. |
| 李莉, 杜慧娜, 李涛. 基于群签名与属性加密的区块链可监管隐私保护方案[J]. 计算机工程, 2022, 48(6):132-138. | |
| [12] | BONEH D, BOYEN X, SHACHAM H. Short Group Signatures[C]// Springer. Advances in Cryptology-CRYPTO 2004. Heidelberg: Springer, 2004: 41-55. |
| [13] | CHAUM D, HEYST E. Group Signatures[C]// Springer. Advances in Cryptology-EUROCRYPT’91. Heidelberg:Springer, 1991: 257-265. |
| [14] |
SHAMIR A. How to Share A Secret[J]. Communications of the ACM, 1979, 22(11): 612-613.
doi: 10.1145/359168.359176 URL |
| [15] | BLAKLEY G R. Safeguarding Cryptographic Keys[EB/OL]. [2022-03-19]. https://ieeexplore.ieee.org/document/8817296. |
| [16] |
RIVEST R L, SHAMIR A, ADLEMAN L. A Method for Obtaining Digital Signatures and Public-Key Cryptosystems[J]. Communications of the ACM, 1978, 21(2): 120-126.
doi: 10.1145/359340.359342 URL |
| [17] | LI Zongyu, GUI Xiaolin, GU Yingjie, et al. Survey on Homomorphic Encryption Algorithm and Its Application in the Privacy-Preserving for Cloud Computing[J]. Journal of Software, 2018, 29(7): 1830-1851. |
| 李宗育, 桂小林, 顾迎捷, 等. 同态加密技术及其在云计算隐私保护中的应用[J]. 软件学报, 2018, 29(7):1830-1851. | |
| [18] | PAILLIER P. Public-Key Cryptosystems Based on Composite Degree Residuosity Classes[C]// Springer. International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 1999: 223-238. |
| [19] |
LIU Y H, CHEN R J. An Asymptotically Perfect Secret Sharing Scheme Based on the Chinese Remainder Theorem[J]. International Journal of Computer Mathematics, 2017, 94(9): 1890-1915.
doi: 10.1080/00207160.2016.1274738 URL |
| [20] |
ZHANG Xi, WANG Jian. Public Integrity Auditing for Shared Data in Cloud Supporting User Identity Tracking[J]. Computer Science, 2020, 47(6): 303-309.
doi: 10.11896/jsjkx.190600079 |
|
张茜, 王箭. 用户身份可追踪的云共享数据完整性审计方案[J]. 计算机科学, 2020, 47(6):303-309.
doi: 10.11896/jsjkx.190600079 |
|
| [21] | ZHU Ziqiang, YAO Zhongyuan, ZHU Weihua, et al. Anonymous and Traceable Data Trading Scheme Based on Blockchain[J]. Journal of Applied Sciences, 2022, 40(4): 653-665. |
| 朱自强, 姚中原, 祝卫华, 等. 匿名可追溯的区块链数据交易方案[J]. 应用科学学报, 2022, 40(4): 653-665. | |
| [22] |
ZHANG Xiaoyu, ZHANG Lina. Blockchain Traceability Scheme Based on Hierarchical Security QR Code[J]. Computer Engineering and Applications, 2022, 58(20): 98-107.
doi: 10.3778/j.issn.1002-8331.2110-0011 |
|
张晓宇, 张丽娜. 分级安全二维码下区块链溯源方案设计[J]. 计算机工程与应用, 2022, 58(20):98-107.
doi: 10.3778/j.issn.1002-8331.2110-0011 |
| [1] | GUO Rui, WEI Xin, CHEN Li. An Outsourceable and Policy-Hidden Attribute-Based Encryption Scheme in the IIoT System [J]. Netinfo Security, 2023, 23(3): 1-12. |
| [2] | ZHOU Quan, ZENG Zhikang, WANG Kemeng, CHEN Menglong. Location Privacy Protection Scheme for Group Signature with Backward Unlinkability [J]. Netinfo Security, 2023, 23(3): 62-72. |
| [3] | YU Jing, YUAN Shuguang, YUAN Yulin, CHEN Chi. A Robust Watermarking Technology Based on k-Anonymity Dataset [J]. Netinfo Security, 2022, 22(9): 11-20. |
| [4] | ZHANG Xuewang, LIU Yufan. Identity Traceable Anonymous Authentication Scheme for Nodes in the Perception Layer of IoT [J]. Netinfo Security, 2022, 22(9): 55-62. |
| [5] | QIN Baodong, YU Peihang, ZHENG Dong. Decision Tree Classification Model Based on Double Trapdoor Homomorphic Encryption [J]. Netinfo Security, 2022, 22(7): 9-17. |
| [6] | LIU Jiawei, MA Zhaofeng, WANG Shushuang, LUO Shoushan. Research on the Restricted Sharing Technology of Private Credit Data Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 54-63. |
| [7] | LYU Guohua, HU Xuexian, YANG Ming, XU Min. Ship AIS Trajectory Classification Algorithm Based on Federated Random Forest [J]. Netinfo Security, 2022, 22(4): 67-76. |
| [8] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 22(3): 78-84. |
| [9] | LYU Kewei, CHEN Chi. Research on Proactive Generation Protocol of Beaver Triples [J]. Netinfo Security, 2022, 22(12): 16-24. |
| [10] | ZHANG Xuewang, YAO Yaning, LI Zhihong, ZHANG Hao. Data Sharing Scheme Based on Consortium Blockchain and Asmuth-Bloom Secret Sharing Algorithm [J]. Netinfo Security, 2022, 22(11): 17-23. |
| [11] | LIANG Guangjun, XIN Jianfang, NI Xueli, MA Zhuo. Research on Smart Speaker Security and Forensics [J]. Netinfo Security, 2022, 22(10): 108-113. |
| [12] | GU Haiyan, JIANG Tong, MA Zhuo, ZHU Jipeng. Research of Improved k-Anonymity Algorithm and Its Application in Privacy Protection [J]. Netinfo Security, 2022, 22(10): 52-58. |
| [13] | XU Shuo, ZHANG Rui, XIA Hui. Privacy-preserving Strategies for Federated Learning Based on Data Attribute Modification [J]. Netinfo Security, 2022, 22(1): 55-63. |
| [14] | JIN Shuting, HE Jingsha, ZHU Nafei, PAN Shijia. Research on Privacy Protection Access Control Mechanism Based on Ontology Reasoning [J]. Netinfo Security, 2021, 21(8): 52-61. |
| [15] | LIU Lu, LI Zhihui, LU Dianjun, YAN Chenhong. Quantum Secret Sharing Scheme Based on Linear Codes [J]. Netinfo Security, 2021, 21(8): 62-69. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||