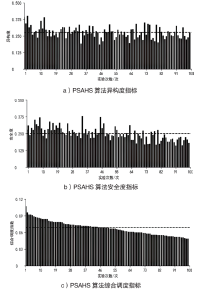
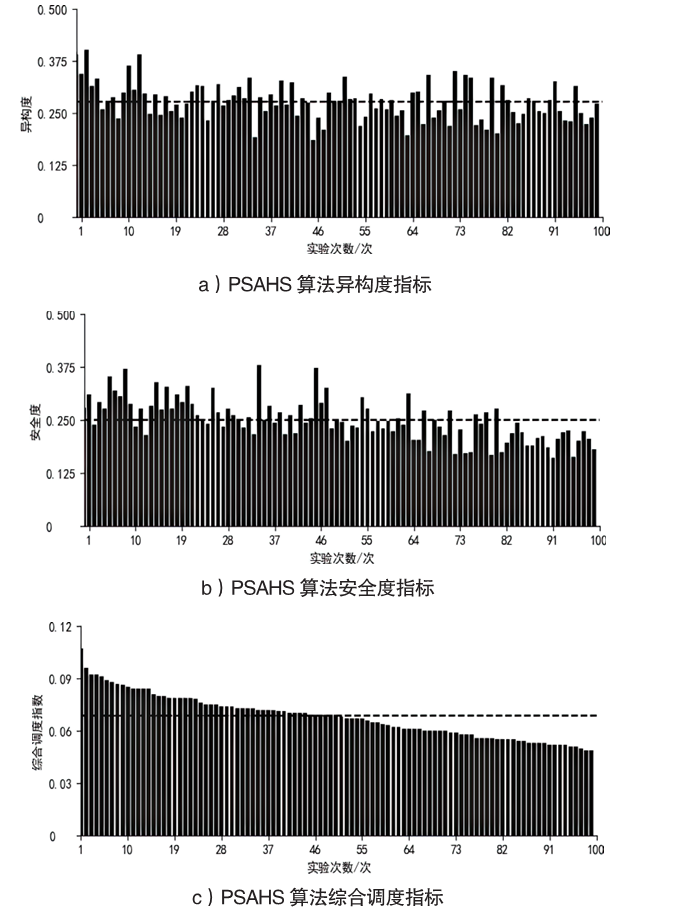
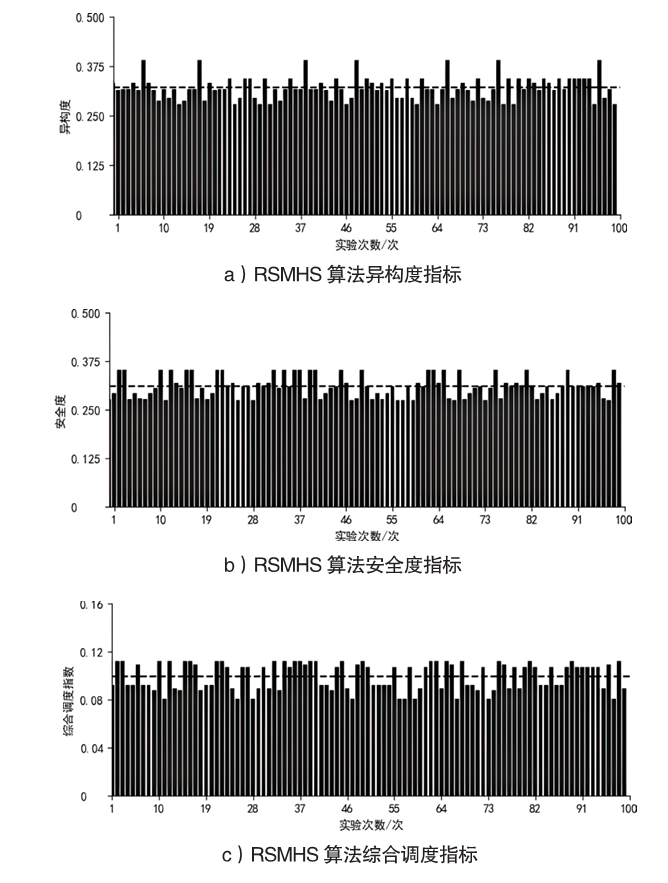
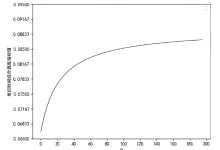
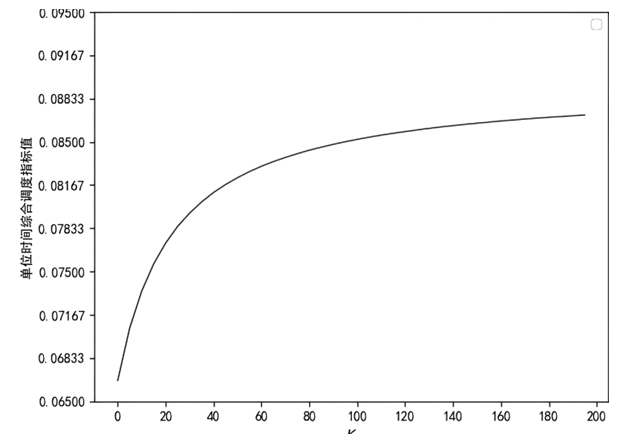
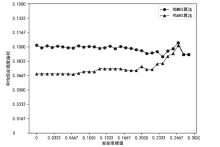
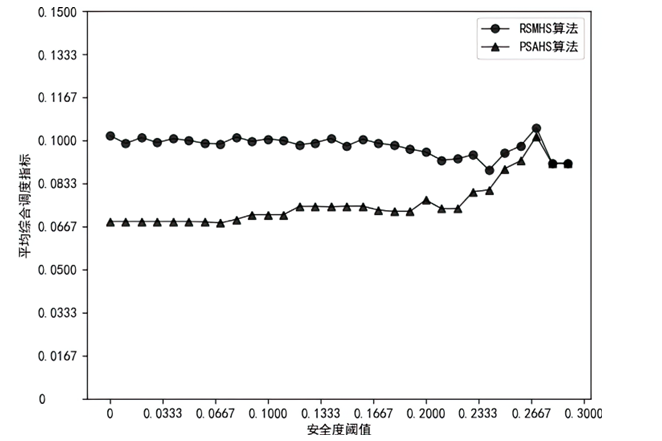
Netinfo Security ›› 2023, Vol. 23 ›› Issue (3): 45-55.doi: 10.3969/j.issn.1671-1122.2023.03.005
Previous Articles Next Articles
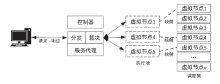
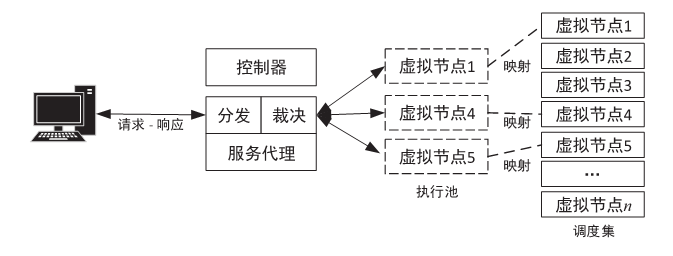
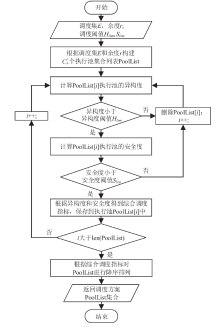
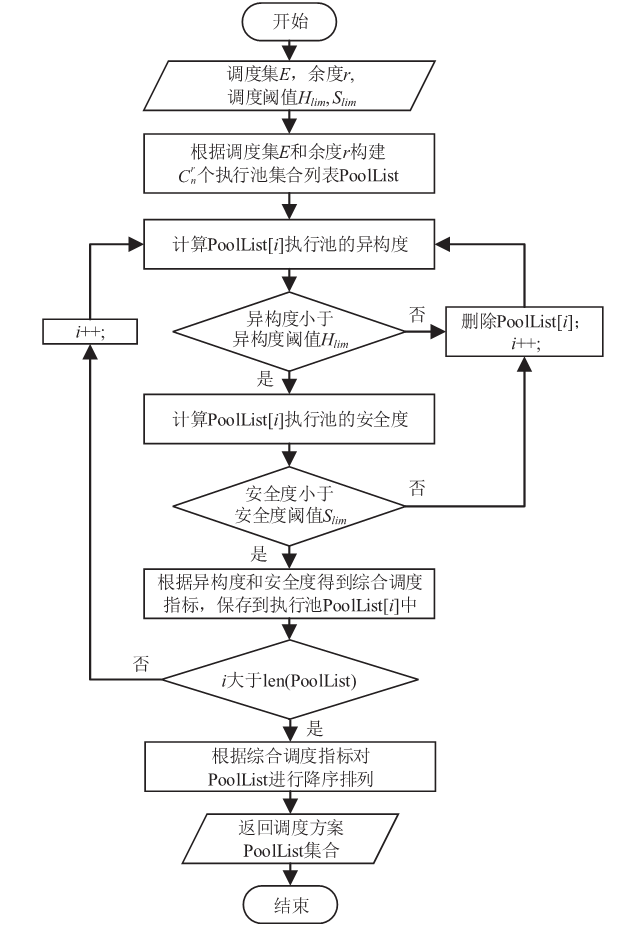
Secure Scheduling Algorithm for Heterogeneous Executors for Mimic Clouds
WANG Ruimin1, XING Yongxu1, SONG Wei2, ZHANG Jianhui3,4( )
)
- 1. School of Computer and Artificial Intelligence, Zhengzhou University, Zhengzhou 450001, China
2. Henan Academy of Big Data of Zhengzhou University, Zhengzhou 450052, China
3. School of Cyber Science and Engineering, Zhengzhou University, Zhengzhou 450002, China
4. Songshan Laboratory, Zhengzhou 450001, China
-
Received:2022-11-27Online:2023-03-10Published:2023-03-14 -
Contact:ZHANG Jianhui E-mail:ndsczjh@163.com
CLC Number:
Cite this article
WANG Ruimin, XING Yongxu, SONG Wei, ZHANG Jianhui. Secure Scheduling Algorithm for Heterogeneous Executors for Mimic Clouds[J]. Netinfo Security, 2023, 23(3): 45-55.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.03.005
| [1] | ZHANG Yuqing, WANG Xiaofei, LIU Xuefeng, et al. Survey on Cloud Computing Security[J]. Journal of Software, 2016, 27(6): 1328-1348. |
| 张玉清, 王晓菲, 刘雪峰, 等. 云计算环境安全综述[J]. 软件学报, 2016, 27(6): 1328-1348. | |
| [2] | PU Liming, WEI Hongquan, LI Xing, et al. Mimic Cloud Service Architecture for Cloud Applications[J]. Chinese Journal of Network and Information Security, 2021, 7(1): 101-112. |
| [3] | CHEN Fucai, ZHOU Mengli, LIU Wenyan, et al. Feedback Control Method for Mimic Defense in Cloud Environment[J]. Netinfo Security, 2021, 21(1): 49-56. |
| [4] | WU Jiangxing. Research on Cyber Mimic Defense[J]. Journal of Cyber Security, 2016, 1(4): 1-10. |
| [5] | WU Jiangxing. Cyberspace Mimic Defense[M]. Beijing: Science Press, 2018. |
| 邬江兴. 网络空间拟态防御原理[M]. 北京: 科学出版社, 2018. | |
| [6] | PU Liming. Research on the Key Technologies of Mimic Cloud Service Architecture[D]. Zhengzhou: Information Engineering University, 2021. |
| 普黎明. 拟态云服务架构及关键技术研究[D]. 郑州: 战略支援部队信息工程大学, 2021. | |
| [7] |
SONG Ke, LIU Qinrang, WEI Shuai, et al. Endogenous Security Architecture of Ethernet Switch Based on Mimic Defense[J]. Journal on Communications, 2020, 41(5): 18-26.
doi: 10.11959/j.issn.1000-436x.2020098 |
|
宋克, 刘勤让, 魏帅, 等. 基于拟态防御的以太网交换机内生安全体系结构[J]. 通信学报, 2020, 41(5): 18-26.
doi: 10.11959/j.issn.1000-436x.2020098 |
|
| [8] | ZHENG Jiesheng, WU Guangcai, WEN Bojian, et al. Research on SDN-Based Mimic Server Defense Technology[C]// ACM. Proceedings of the 2019 International Conference on Artificial Intelligence and Computer Science. New York: ACM, 2019: 163-169. |
| [9] | LI Chuanhuang, REN Yunfang, TANG Zhongyun, et al. Mimic Defense Method for Service Deployment in SDN[J]. Journal on Communications, 2018, 39(S2): 121-130. |
| 李传煌, 任云方, 汤中运, 等. SDN中服务部署的拟态防御方法[J]. 通信学报, 2018, 39(S2): 121-130. | |
| [10] |
HU Hongchao, WANG Zhenpeng, CHENG Guozhen, et al. MNOS: A Mimic Network Operating System for Software Defined Networks[J]. IET Information Security, 2017, 11(6): 345-355.
doi: 10.1049/ise2.v11.6 URL |
| [11] | TONG Qing, ZHANG Zheng, ZHANG Weihua, et al. Design and Implementation of Mimicry Defense Web Server[J]. Journal of Software, 2017, 28(4): 883-897. |
| 仝青, 张铮, 张为华, 等. 拟态防御Web服务器设计与实现[J]. 软件学报, 2017, 28(4): 883-897. | |
| [12] |
GUO Wei, WU Zhaoqi, ZHANG Fan, et al. Scheduling Sequence Control Method Based on Sliding Window in Cyberspace Mimic Defense[J]. IEEE Access, 2019, 8: 1517-1533.
doi: 10.1109/Access.6287639 URL |
| [13] | WU Zhaoqi, WEI Jin. Heterogeneous Executors Scheduling Algorithm for Mimic Defense Systems[C]// IEEE. 2019 IEEE 2nd International Conference on Computer and Communication Engineering. New York: IEEE, 2019: 279-284. |
| [14] | YAO Dong, ZHANG Zheng, ZHANG Gaofei, et al. A Survey on Multi-Variant Execution Security Defense Technology[J]. Journal of Cyber Security, 2020, 5(5): 77-94. |
| [15] |
ZHU Zhengbin, LIU Qinrang, LIU Dongpei, et al. Research Progress of Mimic Multi-Execution Scheduling Algorithm[J]. Journal on Communications, 2021, 42(5): 179-190.
doi: 10.11959/j.issn.1000-436x.2021072 |
|
朱正彬, 刘勤让, 刘冬培, 等. 拟态多执行体调度算法研究进展[J]. 通信学报, 2021, 42(5): 179-190.
doi: 10.11959/j.issn.1000-436x.2021072 |
|
| [16] |
LIU Qinrang, LIN Senjie, GU Zeyu. Heterogeneous Redundancies Scheduling Algorithm for Mimic Security Defense[J]. Journal on Communications, 2018, 39(7): 188-198.
doi: 10.11959/j.issn.1000-436x.2018124 |
|
刘勤让, 林森杰, 顾泽宇. 面向拟态安全防御的异构功能等价体调度算法[J]. 通信学报, 2018, 39(7): 188-198.
doi: 10.11959/j.issn.1000-436x.2018124 |
|
| [17] |
PU Liming, LIU Shuxin, DING Ruihao, et al. Heterogeneous Executor Scheduling Algorithm for Mimic Cloud Service[J]. Journal on Communications, 2020, 41(3): 17-24.
doi: 10.11959/j.issn.1000-436x.2020052 |
|
普黎明, 刘树新, 丁瑞浩, 等. 面向拟态云服务的异构执行体调度算法[J]. 通信学报, 2020, 41(3): 17-24.
doi: 10.11959/j.issn.1000-436x.2020052 |
|
| [18] | GAO Yan, ZI Chenchen, FENG Sifeng, et al. Security Scheduling Algorithm for Web Gateways Based on Mimicry Defense Theory[J]. Journal of Chinese Computer Systems, 2021, 42(9): 1913-1919. |
| 高岩, 资郴琛, 冯四风, 等. 面向拟态防御理论构造Web网关的安全调度算法[J]. 小型微型计算机系统, 2021, 42(9): 1913-1919. | |
| [19] |
GARCIA M, BESSANI A, GASHI I, et al. Analysis of Operating System Diversity for Intrusion Tolerance[J]. Software: Practice and Experience, 2014, 44(6): 735-770.
doi: 10.1002/spe.v44.6 URL |
| [20] | ZHANG Jiexin, PANG Jianmin, ZHANG Zheng, et al. Executors Scheduling Algorithm for Web Server with Mimic Structure[J]. Computer Engineering, 2019, 45(8): 14-21. |
| 张杰鑫, 庞建民, 张铮, 等. 面向拟态构造Web服务器的执行体调度算法[J]. 计算机工程, 2019, 45(8): 14-21. |
| [1] | WANG Yan, ZHANG Kunpeng, JI Zhicheng. Intelligent Optimization and Decision Method of Cloud Resources Based on Trusted Service [J]. Netinfo Security, 2023, 23(2): 35-44. |
| [2] | LIU Jue, CHENG Kaixin, YANG Weiwei. Research on Physical Layer Security Technologies for Smart Eavesdropper Attack [J]. Netinfo Security, 2023, 23(2): 45-53. |
| [3] | XIA Yihang, ZHANG Zhilong, WANG Muzi, CHEN Libo. Dependency-Based Vulnerability Detection Method in Container Supply Chain [J]. Netinfo Security, 2023, 23(2): 76-84. |
| [4] | JIN Zhigang, LIU Kai, WU Xiaodong. A Review of IDS Research in Smart Grid AMI Field [J]. Netinfo Security, 2023, 23(1): 1-8. |
| [5] | FENG Yiting, MA Zhaofeng, XU Danheng, DUAN Pengfei. Evaluation Method for Cross-Chain Security Strength Access [J]. Netinfo Security, 2023, 23(1): 84-92. |
| [6] | LIU Qin, ZHANG Biao, TU Hang. Certificateless Blind Signature Scheme Based on twisted Edwards Curve [J]. Netinfo Security, 2022, 22(8): 19-25. |
| [7] | HU Yi, SHE Kun. Blockchain and Smart Contract Based Dual-Chain Internet of Vehicles System [J]. Netinfo Security, 2022, 22(8): 26-35. |
| [8] | YU Chengli, ZHANG Yang, JIA Shijie. Research on Data Security Threats and Protection of Key Technologies in Cloud Environment [J]. Netinfo Security, 2022, 22(7): 55-63. |
| [9] | HONG Sheng, LI Lei, YUAN Yidong, GAO Xinyan. Research on Cooperative Security Technology of Side Channel in Processor Microarchitecture Storage System [J]. Netinfo Security, 2022, 22(6): 26-37. |
| [10] | ZHAO Hong, LI Shan, ZUO Peiliang, WEI Zhanzhen. Security Resource Allocation Method for Internet of Things Based on Reinforcement Learning [J]. Netinfo Security, 2022, 22(6): 44-52. |
| [11] | YU Kechen, GUO Li, YIN Hongwei, YAN Xuesong. The High-Value Data Sharing Model Based on Blockchain and Game Theory for Data Centers [J]. Netinfo Security, 2022, 22(6): 73-85. |
| [12] | WANG Juan, WANG Yunru, WENG Bin, GONG Jiaxin. Survey on Application of Machine Learning in Disassembly on x86 Binaries [J]. Netinfo Security, 2022, 22(6): 9-25. |
| [13] | SUN Pengyu, TAN Jinglei, LI Chenwei, ZHANG Hengwei. Network Security Defense Decision-Making Method Based on Time Differential Game [J]. Netinfo Security, 2022, 22(5): 64-74. |
| [14] | JIN Bo, TANG Qianjin, TANG Qianlin. Interpretation of the Top 10 Development Trends of Network Security in 2022 by CCF Computer Security Professional Committee [J]. Netinfo Security, 2022, 22(4): 1-6. |
| [15] | LI Guoqi, HONG Sheng, LAN Xueting, ZHANG Hong. The Security Reference Model of the Multi-rotor UAV System [J]. Netinfo Security, 2022, 22(3): 10-19. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||