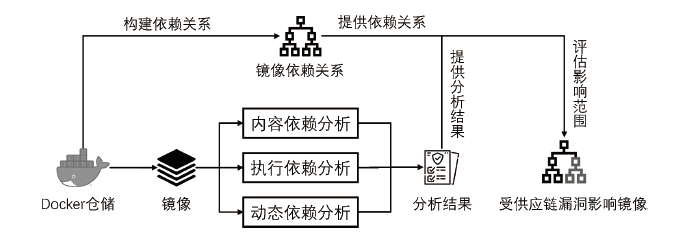
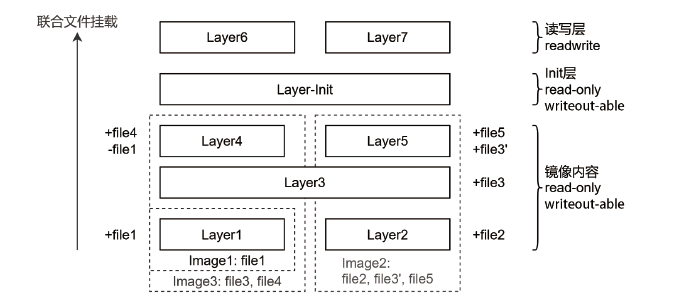
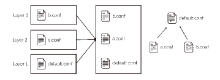
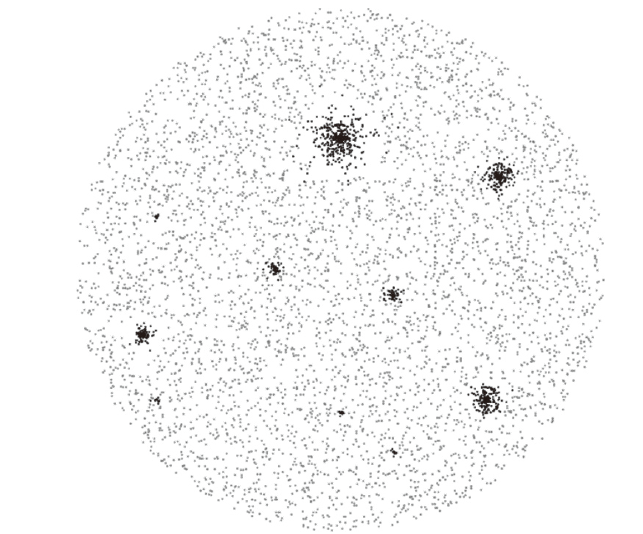
| [1] |
BAVOTA G, CANFORA G, DI P M, et al. The Evolution of Project Inter-Dependencies in a Software Ecosystem: the Case of Apache[C]// IEEE. 2013 IEEE International Conference on Software Maintenance. New York: IEEE, 2013: 280-289.
|
| [2] |
HE Xixun, ZHANG Yuqing, LIU Qixu. Survey of Software Supply Chain Security[J]. Journal of Cyber Security, 2020, 5(1): 57-73.
|
| [3] |
GADGE A. Is Open Source Software More Secure Than the Commercial Software?[EB/OL]. (2022-06-16)[2022-10-17]. https://www.ashnik.com/is-open-source-software-more-secure-than-the-commercial-software.
|
| [4] |
ELLISON R J, WOODY C. Supply-Chain Risk Management: Incorporating Security into Software Development[C]// IEEE. 2010 43rd Hawaii International Conference on System Sciences. New York: IEEE, 2010: 1-10.
|
| [5] |
LI Qiang, SONG Jinke, TAN Dawei, et al. Pdgraph: A Large-Scale Empirical Study on Project Dependency of Security Vulnerabilities[C]// IEEE. 2021 51st Annual IEEE/IFIP International Conference on Dependable Systems and Networks (DSN). New York:IEEE, 2021: 161-173.
|
| [6] |
Apache Log4j. Apache Log4j Security Vulnerabilities[EB/OL]. (2022-09-13)[2022-10-17]. https://logging.apache.org/log4j/2.x/security.html.
|
| [7] |
RED Hat. What is CI/CD?[EB/OL]. (2022-05-11)[2022-10-17]. https://www.redhat.com/en/topics/devops/what-is-ci-cd.
|
| [8] |
Docker. Develop Faster Run Anywhere[EB/OL]. (2022-10-25)[2022-10-30]. https://www.docker.com.
|
| [9] |
Sysdig. Sysdig 2021 Container Security and Usage Report: Shifting Left is Not Enough[EB/OL]. (2021-01-13)[2022-10-17]. https://sysdig.com/blog/sysdig-2021-container-security-usage-report.
|
| [10] |
Banyanops. Banyan Collector: A Framework to Peek Inside Containers[EB/OL]. (2019-08-24)[2022-10-17]. https://github.com/banyanops/collector.
|
| [11] |
ROBIO E G. Dagda[EB/OL]. (2021-07-28)[2022-10-17]. https://github.com/eliasgranderubio/dagda.
|
| [12] |
Quay. Clair[EB/OL]. (2022-10-28)[2022-10-30]. https://github.com/quay/clair.
|
| [13] |
SHU Rui, GU Xiaohui, ENCK W. A Study of Security Vulnerabilities on Docker Hub[C]// ACM. 7th ACM on Conference on Data and Application Security and Privacy. New York: ACM, 2017: 269-280.
|
| [14] |
KWON S, LEE J H. Divds: Docker Image Vulnerability Diagnostic System[J]. IEEE Access, 2020(8): 42666-42673.
|
| [15] |
LIU Peiyu, JI Shouling, FU Lirong, et al. Understanding the Security Risks of Docker Hub[C]// Springer. European Symposium on Research in Computer Security. Berlin:Springer, 2020: 257-276.
|
| [16] |
Sonatype. 2021 State of the Software Supply Chain Report[EB/OL]. (2021-08-01)[2022-10-17]. https://www.sonatype.com/resources/state-of-the-software-supply-chain-2021.
|
| [17] |
ZIMMERMANN M, STAICU C A, TENNY C, et al. Small World with High Risks: A Study of Security Threats in the Npm Ecosystem[C]// USENIX. 28th USENIX Security Symposium (USENIX Security 19). Berkeley:USENIX, 2019: 995-1010.
|
| [18] |
OHM M, PLATE H, SYKOSCH A, et al. Backstabber’s Knife Collection: A Review of Open Source Software Supply Chain Attacks[C]// Springer. International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment. Berlin:Springer, 2020: 23-43.
|
| [19] |
VU D L, MASSACCI F, PASHCHENKO I, et al. Lastpymile: Identifying the Discrepancy Between Sources and Packages[C]// ACM. 29th ACM Joint Meeting on European Software Engineering Conference and Symposium on the Foundations of Software Engineering. New York: ACM, 2021: 780-792.
|
| [20] |
CONTRAST Security. The Contrast Secure Code Platform[EB/OL]. (2022-02-15)[2022-10-17]. https://www.contrastsecurity.com.
|
| [21] |
MEND. Your Code We Cure[EB/OL]. (2022-05-25)[2022-10-17]. https://www.mend.io.
|
| [22] |
Sonatype. Code Smarter Fix Faster Be Secure[EB/OL]. (2021-06-30)[2022-10-17]. https://www.sonatype.com.
|
| [23] |
Docker. Generate the SBOM for Docker Images[EB/OL]. (2022-04-06)[2022-10-17]. https://docs.docker.com/engine/sbom/.
|
| [24] |
Anchore. Syft[EB/OL]. (2022-10-29)[2022-10-31]. https://github.com/anchore/syft.
|
| [25] |
Anchore. Grype[EB/OL]. (2022-10-28)[2022-10-31]. https://github.com/anchore/grype.
|
| [26] |
Snyk. Snyk CLI[EB/OL]. (2022-10-27)[2022-10-31]. https://github.com/snyk/cli.
|
| [27] |
SHUBHAM S. Apache Log4j: Return of the JNDI[EB/OL]. (2021-12-25)[2022-10-17]. https://dev.to/shubhamsah/apache-log4j-return-of-the-jndi-292o.
|
| [28] |
XMIRROR, ISC, China Telecom Research Institute. White Paper on Software Supply Chain Security Governance and Operation(2022)[EB/OL]. (2022-08-19)[2022-10-17]. https://www.xmirror.cn/resurce/Uploads/upfile/20220819/62ff585edcb2a.pdf.
|
|
悬镜安全, ISC, 中国电信研究院. 软件供应链安全治理与运营白皮书 (2022)[EB/OL]. (2022-08-19)[2022-10-17]. https://www.xmirror.cn/resurce/Uploads/upfile/20220819/62ff585edcb2a.pdf.
|
| [29] |
CHEN Libo, XIA Yihang, MA Zhenbang, et al. SEAF: A Scalable, Efficient, and Application-Independent Framework for Container Security Detection[EB/OL]. (2022-10-14)[2022-10-17]. https://www.sciencedirect.com/science/article/pii/S221421262200196X.
|
 )
)