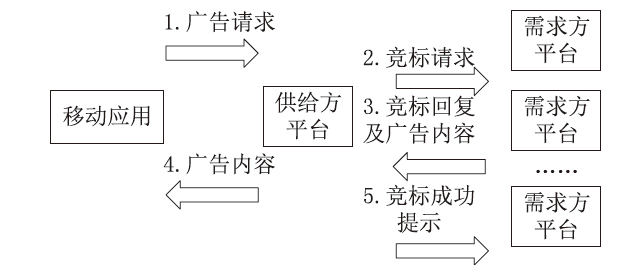
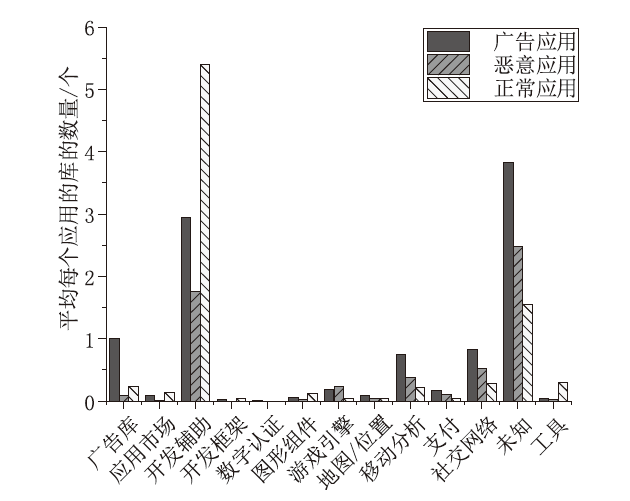
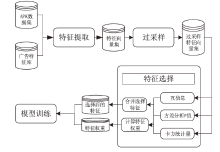
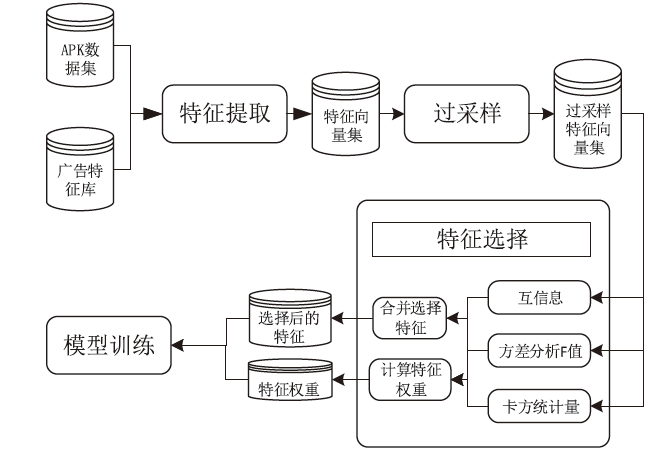
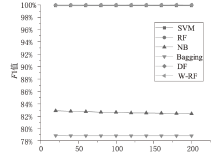
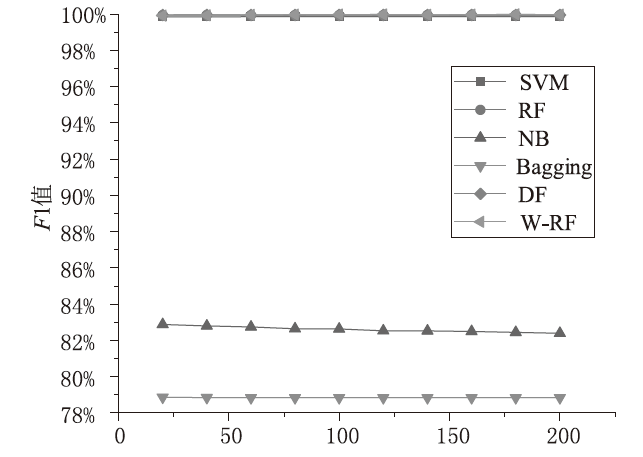
Netinfo Security ›› 2023, Vol. 23 ›› Issue (2): 85-95.doi: 10.3969/j.issn.1671-1122.2023.02.010
Previous Articles Next Articles
Static Detection Method of Android Adware Based on Improved Random Forest Algorithm
HU Zhijie1, CHEN Xingshu2( ), YUAN Daohua1, ZHENG Tao2
), YUAN Daohua1, ZHENG Tao2
- 1. School of Computer Science, Sichuan University, Chengdu 610065, China
2. School of Cyber Science and Engineering, Sichuan University, Chengdu 610207, China
-
Received:2022-10-19Online:2023-02-10Published:2023-02-28 -
Contact:CHEN Xingshu E-mail:chenxsh@scu.edu.cn
CLC Number:
Cite this article
HU Zhijie, CHEN Xingshu, YUAN Daohua, ZHENG Tao. Static Detection Method of Android Adware Based on Improved Random Forest Algorithm[J]. Netinfo Security, 2023, 23(2): 85-95.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2023.02.010
| [1] | STATCOUNTER. Mobile Operating System Market Share Worldwide[EB/OL]. (2021-09-01)[2022-09-01]. https://gs.statcounter.com/os-market-share/mobile/worldwide. |
| [2] | CHEBYSHEV V. Mobile Malware Evolution 2020[EB/OL]. (2020-03-01)[2022-09-01]. https://securelist.com/mobile-malware-evolution-2020/101029/. |
| [3] | DARTMOUTH. A Course on Android Malware Analysis[EB/OL]. (2020-12-14)[2022-09-01]. https://www.youtube.com/watch?v=CwCOGf4Uunk. |
| [4] | NDAGI J Y, ALHASSAN J K. Machine Learning Classification Algorithms for Adware in Android Devices: A Comparative Evaluation and Analysis[C]// IEEE. 2019 15th International Conference on Electronics, Computer and Computation. New York: IEEE, 2019: 1-6. |
| [5] | IDESES I, NEUBERGER A. Adware Detection and Privacy Control in Mobile Devices[C]// IEEE. Electrical & Electronics Engineers in Israel. New York: IEEE, 2014: 1-5. |
| [6] | LEE K, PARK H. Malicious Adware Detection on Android Platform Using Dynamic Random Forest[C]// Springer. 13th International Conference on Innovative Mobile and Internet Services in Ubiquitous Computing. Berlin:Springer, 2019: 609-617. |
| [7] |
SURESH S, DI T F, POTIKA K, et al. An Analysis of Android Adware[J]. Journal of Computer Virology and Hacking Techniques, 2019, 15(3): 147-160.
doi: 10.1007/s11416-018-0328-8 URL |
| [8] | BAGUI S, BENSON D. Android Adware Detection Using Machine Learning[J]. International Journal of Cyber Research and Education, 2021, 3(2): 1-19 |
| [9] | LIU Bin, NATH S, GOVINDAN R, et al. DECAF: Detecting and Characterizing Ad Fraud in Mobile Apps[C]// USENIX. 11th USENIX Symposium on Networked Systems Design and Implementation. Berkeley: USENIX, 2014: 57-70. |
| [10] | DONG Feng, WANG Haoyu, LI Li, et al. FraudDroid: Automated Ad Fraud Detection for Android Apps[C]// ACM. 26th ACM Joint Meeting on European Software Engineering Conference/ Symposium on the Foundations of Software Engineering. New York: ACM, 2018: 257-268. |
| [11] | LIU Tianming, WANG Haoyu, LI Li, et al. MadDroid: Characterising and Detecting Devious Ad Content for Android Apps[C]// ACM. 29th World Wide Web Conference. New York: ACM, 2020: 1715-1726. |
| [12] | DOGTIEV A. Top Mobile Advertising Companies (2021)[EB/OL]. (2021-12-23)[2022-09-27]. https://www.businessofapps.com/ads. |
| [13] | DOGTIEV A. Real Time Bidding Advertising Networks[EB/OL]. (2021-12-23)[2022-08-26]. https://www.businessofapps.com/ads/real-time-bidding-rtb/. |
| [14] | TREND MICRO. Mobile Ad Fraud Schemes: How They Work, and How to Defend Against Them[EB/OL]. (2019-04-26)[2022-07-17]. https://www.trendmicro.com/vinfo/us/security/news/mobile-safety/mobile-ad-fraud-schemes-how-they-work-and-how-to-defend-against-them. |
| [15] | WANG Haoyu, GUO Yao, MA Ziang, et al. WuKong: a Scalable and Accurate Two-Phase Approach to Android App Clone Detection[C]// ACM. 2015 International Symposium on Software Testing & Analysis. New York: ACM, 2015: 71-82. |
| [16] | GOLOVIN I, KIVVA A. Aggressive in-App Advertising in Android[EB/OL]. (2020-05-25)[2022-09-01]. https://securelist.com/in-app-advertising-in-android/97065/. |
| [17] | GOLOVIN I, KIVVA A. An Advertising Dropper in Google Play[EB/OL]. (2019-08-27)[2022-09-16]. https://securelist.com/dropper-in-google-play/92496/. |
| [18] | MA Ziang, WANG Haoyu, GUO Yao, et al. LibRadar: Fast and Accurate Detection of Third-Party Libraries in Android Apps[C]// IEEE. 2016 IEEE/ACM 38th International Conference on Software Engineering Companion. New York: IEEE, 2017: 653-656. |
| [19] | LI Li, BISSYANDE T F, KLEIN J, et al. An Investigation into the Use of Common Libraries in Android Apps[C]// IEEE. 2016 IEEE 23rd International Conference on Software Analysis, Evolution, and Reengineering. New York: IEEE, 2016: 403-414. |
| [20] | HAN Hui, WANGWenyuan, MAOBinghuan. Borderline-SMOTE: A New Over-Sampling Method in Imbalanced Data Sets Learning[C]// Springer. 2005 International Conference on Intelligent Computing. Berlin:Springer, 2005: 878-887. |
| [21] | HE Haibo, BAI Yang, GARCIA E A, et al. ADASYN: Adaptive Synthetic Sampling Approach for Imbalanced Learning[C]// IEEE. 2008 International Joint Conference on Neural Networks. New York: IEEE, 2008: 1322-1328. |
| [22] | SEBASTI’AN S, CABALLERO J. AVclass2: Massive Malware Tag Extraction from AV Labels[C]// ACM. Annual Computer Security Applications Conference. New York: ACM, 2020: 42-53. |
| [1] | LIU Xiangyu, LU Tianliang, DU Yanhui, WANG Jingxiang. Lightweight IoT Intrusion Detection Method Based on Feature Selection [J]. Netinfo Security, 2023, 23(1): 66-72. |
| [2] | ZHANG Mengjie, WANG Jian, HUANG Kaijie, YANG Gang. A Static Detection Method of ROP Traffic Based on Bytes Fluctuation Characteristics [J]. Netinfo Security, 2022, 22(7): 64-72. |
| [3] | QIN Baodong, YU Peihang, ZHENG Dong. Decision Tree Classification Model Based on Double Trapdoor Homomorphic Encryption [J]. Netinfo Security, 2022, 22(7): 9-17. |
| [4] | WANG Juan, WANG Yunru, WENG Bin, GONG Jiaxin. Survey on Application of Machine Learning in Disassembly on x86 Binaries [J]. Netinfo Security, 2022, 22(6): 9-25. |
| [5] | TANG Ming, LI Cong, LI Yongbo, YUE Tianyu. Study on Static Detection of Timing Side Channel for RISC-V Architecture [J]. Netinfo Security, 2022, 22(4): 7-19. |
| [6] | NIU Yinuo, ZHANG Yifei, GAO Neng, MA Cunqing. Design of Log-Based Anomaly Detection System Based on Temporal and Logical Relationship [J]. Netinfo Security, 2022, 22(11): 1-6. |
| [7] | TONG Xin, JIN Bo, WANG Jingya, YANG Ying. A Multi-View and Multi-Task Learning Detection Method for Android Malware [J]. Netinfo Security, 2022, 22(10): 1-7. |
| [8] | DUAN Xiaoyi, LI You, LINGHU Yunxing, HU Ronglei. Research on the Method of Side Channel Attack Based on RF Algorithm [J]. Netinfo Security, 2022, 22(1): 19-26. |
| [9] | GUO Chun, CAI Wenyan, SHEN Guowei, ZHOU Xuemei. Research on SQL Injection Attacks Detection Method Based on the Truncated Key Payload [J]. Netinfo Security, 2021, 21(7): 43-53. |
| [10] | MA Xiao, CAI Manchun, LU Tianliang. Malicious Domain Name Training Data Generation Technology Based on Improved CNN Model [J]. Netinfo Security, 2021, 21(10): 69-75. |
| [11] | XU Yu, ZHOU You, LIN Lu, ZHANG Cong. Applied Research of Unsupervised Machine Learning in Game Anti-fraud [J]. Netinfo Security, 2020, 20(9): 32-36. |
| [12] | YUAN Xiaoxiao, LUO Senlin, YANG Peng. Research on Android Application DEX File Protection Method [J]. Netinfo Security, 2020, 20(7): 60-69. |
| [13] | ZHENG Dong, ZHAO Yue. Android Malware Detection Based on SM3 and Multi-feature [J]. Netinfo Security, 2020, 20(6): 17-25. |
| [14] | GUO Chun, CHEN Changqing, SHEN Guowei, JIANG Chaohui. A Ransomware Classification Method Based on Visualization [J]. Netinfo Security, 2020, 20(4): 31-39. |
| [15] | DU Yifeng, GUO Yuanbo. A Dynamic Access Control Method for Fog Computing Based on Trust Value [J]. Netinfo Security, 2020, 20(4): 65-72. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||