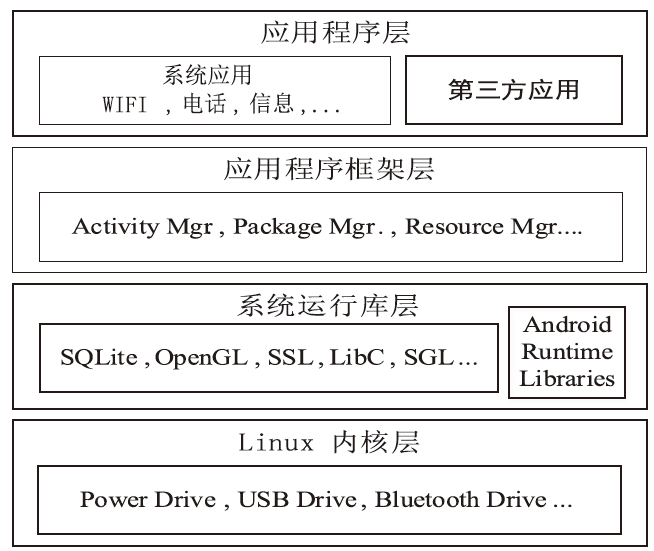
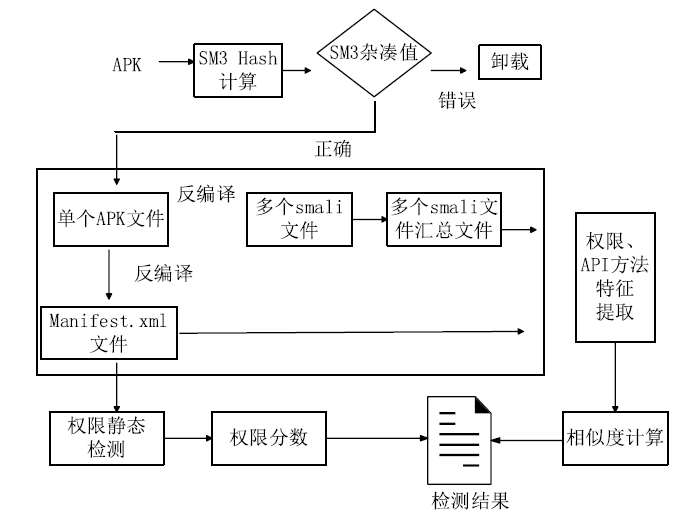
| [1] |
XIE Jiayun, FU Xiao, LUO Bin. Progress in Android Protection Technology[J]. Computer Engineering, 2018,44(2):163-170.
|
|
谢佳筠, 伏晓, 骆斌. Android防护技术研究进展[J]. 计算机工程, 2018,44(2):163-170.
|
| [2] |
PARVEZ F, AMMAR B, VIJAY L. Android Security: A Survey of Issues, Malware Penetration, and Defenses[J]. IEEE Communications Surveys & Tutorials, 2019,17(2):998-1022.
|
| [3] |
CHO J, KIM D, KIM H. User Credential Cloning Attacks in Android Applications: Exploiting Automatic Login on Android Apps and Mitigating Strategies[J]. IEEE Consumer Electronics Magazine, 2018,7(3):48-55.
|
| [4] |
OMAR M, MOHAMMED D, NGUYEN V, et al. Android Application Security[M]. Applying Methods of Scientific Inquiry Into Intelligence, Security, and Counterterrorism. NY: IGI Global, 2019.
|
| [5] |
G DATA: Q3 Global Android Malicious Samples in 2018 increased by 40% over the same period of last year[EB/OL]. http://www.199it.com/archives/793849.html, 2019-1-15.
|
|
G DATA:2018年Q3全球Android新恶意样本数量达320万个同比增加40%[EB/OL]. http://www.199it.com/archives/793849.html,2019-1-15.
|
| [6] |
PENG Lin. ISC2017 Tide Viewing Network Space Forum: International Consensus on Network Space Governance[J]. China Information Security, 2017 ( 10):90-94.
|
|
彭琳. ISC2017观潮网络空间论坛:汇聚网络空间治理的国际共识[J].中国信息安全, 2017(10):90-94.
|
| [7] |
ZHOU W, JIA Y, PENG A, et al. The Effect of Iot New Features on Security and Privacy: New Threats, Ex-Isting Solutions, and Challenges yet to be Solved[J]. IEEE Internet of Things Journal, 2018,30(6):1606-1616.
|
| [8] |
National Cryptographic Administration Department. SM3 Cryptographic Hash Algorithm[EB/OL]. http://www.oscca.gov.cn/UpFile/20101222141857786.pdf, 2019-1-15.
|
|
国家密码管理系. SM3密码杂凑算法[EB/OL]. http://www.oscca.gov.cn/UpFile/20101222141857786.pdf,2019-1-15.
|
| [9] |
MA Junli. Research on Malicious Behavior Detection and Classification Method of Android Applications[D]. Beijing:Beijing Jiaotong University, 2016.
|
|
马君丽. 安卓应用的恶意行为检测与归类方法研究[D]. 北京:北京交通大学, 2016.
|
| [10] |
KUMAR R, ZHANG X, KHAN R U, et al. Resea-Earch on Data Mining of Permission-Induced Risk for Android IoT Devices[J]. Applied Sciences, 2019,9(2):277.
|
| [11] |
ZHANG Zhenquan, LUO Xinmin, QI Chun. Comparison of Digital Signature Algorithms MD5 and SHA-1 and Optimization Implementation of AVR[J]. Network Security Technology and Application, 2005,5(7):64-67.
|
|
张振权, 罗新民, 齐春. 数字签名算法MD5和SHA-1的比较及其AVR优化实现[J]. 网络安全技术与应用, 2005,5(7):64-67.
|
| [12] |
YANG Zhonghuang, LIANG Shanqiang, ZHAN Weixiao. Remote Management of Mobile Devices Based on SEAndroid[J]. Journal of Xi’an University of Posts and Telecommunications, 2018,23(3):17-24.
|
|
杨中皇, 梁善强, 詹维骁. 基于SEAndroid的移动设备远程管理[J]. 西安邮电大学学报, 2018,23(3):17-24.
|
| [13] |
BAGHERI H, KANG E, MALEK S, et al. A Formal Approach for Detection of Security Flaws in the A-ndroid Permission System[J]. Formal Aspects of ComPuting, 2018,30(5):525-544.
|
| [14] |
MIN Luocxu, CAO Qinghua. Runtime-Based Behavior Dynamic Analysis System for Android Malware Detection[EB/OL]. https://www.researchgate.net/publication/266646301_Runtime-Based_Behavior_Dynamic_Analysis_System_for_Android_Malware_Detection, 2019 -1-15.
|
| [15] |
MAMMONE N, IERACITANO C, Adeli H, et al. Permutation Jaccard Distance-Based Hierarchical Clustering to Estimate EEG Network Density Modifications in MCI Subjects[J]. IEEE Transactions on Neural Networks and Learning Systems, 2018,9(9):1-14.
|
| [16] |
HUANG Meigen, ZENG Yunke. Detection Method of Android Stealing Privacy Malicious Applications Based on Permission Combination[J]. Computer Applications and Software, 2016,33(9):320-323, 333.
|
|
黄梅根, 曾云科. 基于权限组合的Android窃取隐私恶意应用检测方法[J]. 计算机应用与软件, 2016,33(9):320-323,333.
|