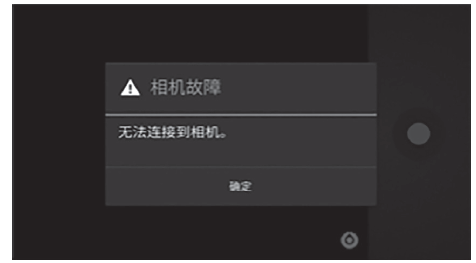
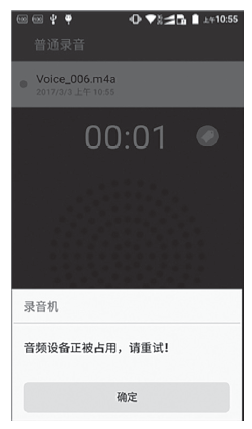
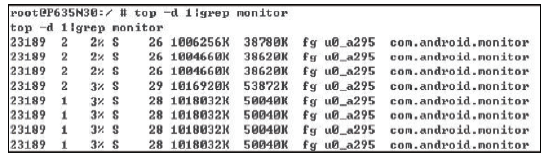
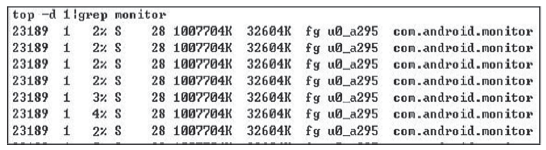
| [1] |
ZHOU Hang, YANG Yang, QIU Xuesong, et al.The Strategy of Probe Station Selection of Active Probing in WSNs[C]//IEEE. 16th Asia-Pacific Network Operations and Management Symposium, September 17-19, 2014, Hsinchu, Taiwan, China. New Jersey: IEEE, 2014: 1-4.
|
| [2] |
LI Yongxing, HENG Yang, HAO Ankang, et al.Detecting and Tracking Pseudo Base Stations in GSM Signal Hijacking and Frauds: a Visualized Approach[J]. Information Security and Computer Fraud, 2017, 5(1): 1-8.
|
| [3] |
ZHANG Yuan, YANG Min, XU Bingquan, et al.Vetting Undesirable Behaviors in Android APPs with Permission use Analysis[C]//ACM. 2013 ACM SIGSAC Conference on Computer & Communications Security, November 4-8, 2013, Berlin, Germany. New York: ACM, 2013: 611-622.
|
| [4] |
ZHAI Gaoshou, LIU Chen, XIANG Yong.Study and Implementation of Systematic Protection by Monitoring Abnormal Invocation of Linux Kernel Functions[J]. Netinfo Security, 2018, 18(3): 26-38.
|
|
翟高寿,刘晨,向勇. 基于内核函数监控的Linux系统防护方法的研究与实现[J]. 信息网络安全,2018,18(3):26-38.
|
| [5] |
LI Zhoujun, WU Chunming, WANG Xiao.Assessment of Android Application’s Risk Behavior Based on a Sandbox System[J]. Journal of Tsinghua University(Science & Technology), 2016, 56(5): 453-460.
|
|
李舟军,吴春明,王啸. 基于沙盒的Android应用风险行为分析与评估[J]. 清华大学学报 (自然科学版),2016,56(5):453-460.
|
| [6] |
SONG Xinlong, ZHENG Dong, YANG Zhonghuang.Mobile Device Management System Based on AOSP and SELinux[J]. Netinfo Security, 2017, 17(9): 103-106.
|
|
宋新龙,郑东,杨中皇. 基于AOSP与SELinux的移动设备管理系统[J]. 信息网络安全,2017,17(9):103-106.
|
| [7] |
ENCK W, GILBERT P, CHUN B G, et al.TaintDroid: an Information Flow Tracking System for Real-time Privacy Monitoring on Smartphones[J]. ACM Transactions on Computer Systems, 2012, 32(2): 1-29.
|
| [8] |
TAM K, KHAN S J, FATTORI A, et al. CopperDroid: Automatic Reconstruction of Android Malware Behaviors[EB/OL]>, 2018-3-11.
|
| [9] |
XU Rubin,SAÏDI H, ANDERSON R. Aurasium: Practical Policy Enforcement for Android Applications[C]//ACM. 21st USENIX Conference on Security Symposium, August 8-10, 2012, Bellevue, USA. New York: ACM, 2012: 27-40.
|
| [10] |
SINGH L, HOFMANN M.Dynamic Behavior Analysis of Android Applications for Malware Detection[C]//IEEE. 2017 International Conference on Intelligent Communication and Computational Techniques, December 22-23, 2017, Jaipur, India. New Jersey: IEEE, 2017: 1-7.
|
| [11] |
ZHENG Min, SUN Mingshen, LUI J C S. DroidTrace: a Ptrace Based Android Dynamic Analysis System with Forward Execution Capability[C]//IEEE. 2014 International Wireless Communications and Mobile Computing Conference, Auguest 4-8, 2014, Nicosia, Cyprus. Jersey: IEEE, 2014: 128-133.
|
| [12] |
WEN Weiping, TANG Yang, SHEN Li.An APP Sensitive Behaviors Detection Method Based on Android Kernel and Its Implementation[J]. Netinfo Security, 2016, 16(8): 18-23.
|
|
文伟平,汤炀,谌力. 一种基于Android内核的APP敏感行为检测方法及实现[J]. 信息网络安全,2016,16(8):18-23.
|
| [13] |
ISOHARA T, TAKEMORI K, KUBOTA A.Kernel-based Behavior Analysis for Android Malware Detection[C]//IEEE. 7th International Conference on Computational Intelligence and Security, December 3-4, 2011, Hainan, China. Jersey: IEEE, 2012: 1011-1015.
|
| [14] |
WEN Weiping, MEI Rui, NING Ge, et al.Malware Detection Technology Analysis and Applied Research of Android Platform[J]. Journal on Communications, 2014, 35(8): 78-85.
|
| [15] |
TAM K, FEIZOLLAH A, ANUAR N B, et al.The Evolution of Android Malware and Android Analysis Techniques[J]. ACM Computing Surveys, 2017, 49(4): 1-41.
|
| [16] |
SADEGHI A, BAGHERI H, GARCIA J, et al.A Taxonomy and Qualitative Comparison of Program Analysis Techniques for Security Assessment of Android Software[J]. IEEE Transactions on Software Engineering, 2017, 43(6): 492-530.
|
| [17] |
BHATTACHARYA A, GOSWAMI R T. Comparative Analysis of Different Feature Ranking Techniques in Data Mining-based Android Malware Detection[EB/OL]. , 2018-3-13.
|
| [18] |
OZSOY M, KHASAWNEH K N, DONOVICK C, et al.Hardware-based Malware Detection using Low Level Architectural Features[J]. IEEE Transactions on Computers, 2016, 65(11): 3332-3344.
|
| [19] |
LI Guizhi, HAN Zhen, ZHOU Qihui, et al.A Detecting System for Android Malicious Behavior Based on Binder Information Flow[J]. Netinfo Security, 2016, 16(2): 54-59.
|
|
李桂芝,韩臻,周启惠,等. 基于Binder信息流的Android恶意行为检测系统[J]. 信息网络安全,2016,16(2):54-59.
|
| [20] |
SALEHI M, DARYABAR F, TADAYON M H.Welcome to Binder: A Kernel Level Attack Model for the Binder in Android Operating System[C]//IEEE. 8th International Symposium on Telecommunications, September 27-28, 2016, Tehran, Iran. New Jersey: IEEE, 2017: 156-161.
|