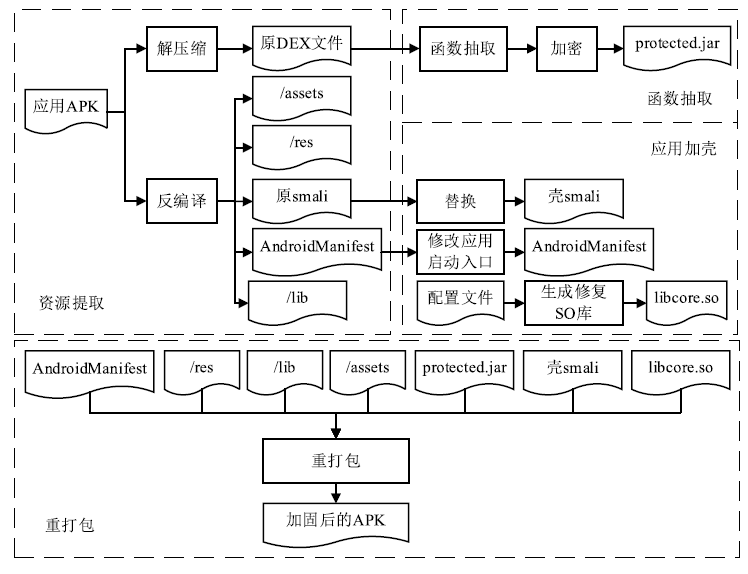
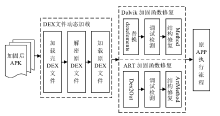
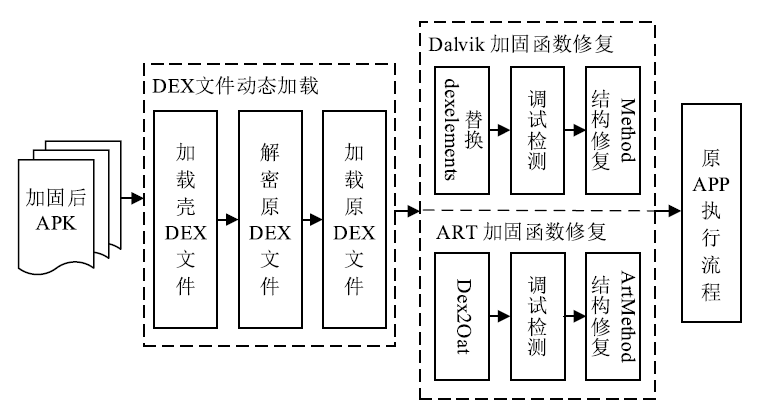
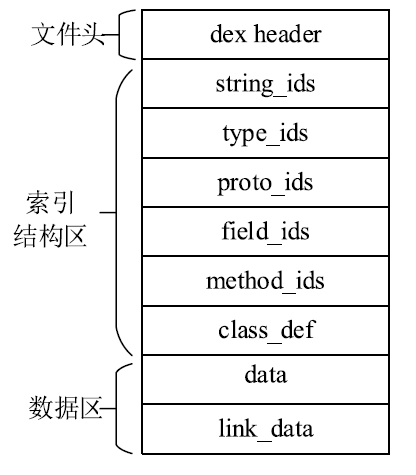
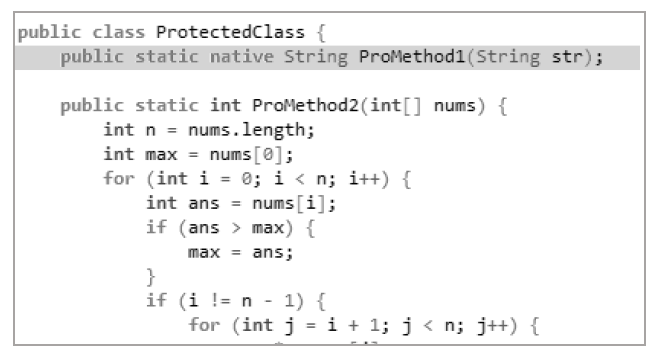
Netinfo Security ›› 2020, Vol. 20 ›› Issue (7): 60-69.doi: 10.3969/j.issn.1671-1122.2020.07.007
Previous Articles Next Articles
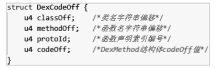
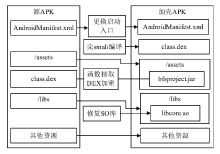
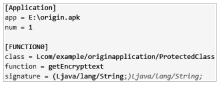
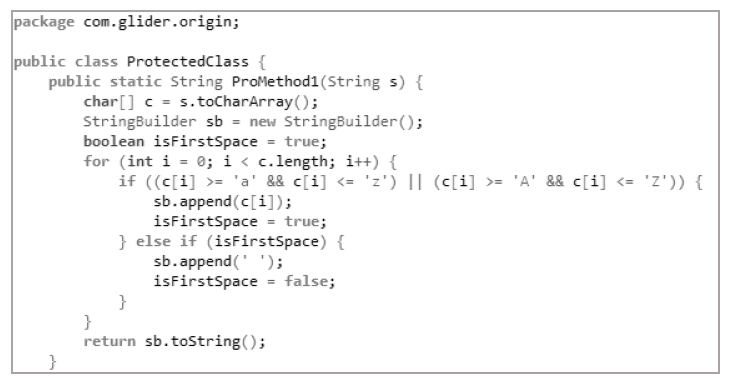
Research on Android Application DEX File Protection Method
YUAN Xiaoxiao1, LUO Senlin1, YANG Peng2( )
)
- 1. Information System & Security and Countermeasures Experiments Center, Beijing Institute of Technology, Beijing 100081, China
2. National Computer Network Emergency Response Technical Team Coordination Center of China, Beijing 100094, China
-
Received:2019-09-23Online:2020-07-10Published:2020-08-13 -
Contact:Peng YANG E-mail:yp@cert.org.cn
CLC Number:
Cite this article
YUAN Xiaoxiao, LUO Senlin, YANG Peng. Research on Android Application DEX File Protection Method[J]. Netinfo Security, 2020, 20(7): 60-69.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2020.07.007
| [1] | CHRISTIAN C, CLARK T, DOUGLAS L. A Taxonomy of Obfuscating Transformations[R]. New Zealand: University of Auckland, TR# 148, 1997. |
| [2] | SCHULZ P. Code Protection in Android[R]. Germany: Rheinische Friedrich-Wilhelms-Universitgt Bonn, TR# 110, 2012. |
| [3] | SHU Junliang, LI Juanru, ZHANG Yuanyuan, et al. Android APP Protection via Interpretation Obfuscation[C]// IEEE. 2014 IEEE 12th International Conference on Dependable, Autonomic and Secure Computing (DASC), August 20-22, 2014, Dalian, China. New York: IEEE, 2014: 63-68. |
| [4] | WANG Dejia, SONG Chao, LIU Jiajung. Deep Code Obfuscation Method for Android System Application : China, 103544414A[P]. 2014. |
| 汪德嘉, 宋超, 刘家郡. 一种Android 系统应用的深度代码混淆方法: 中国,103544414A[P]. 2014. | |
| [5] | LIU Fangyuan, MENG Xianjia, TANG Zhanyong, et al. Android Application Protection Method Based on Smali Code Obfuscation[J]. Journal of Shandong University, 2017,52(3):44-50. |
| 刘方圆, 孟宪佳, 汤战勇, 等. 基于smali代码混淆的Android应用保护方法[J]. 山东大学学报(理学版), 2017,52(3):44-50. | |
| [6] | SU Yuanqing. Research on Android-based Software Protection Based on Dynamic Loading[D]. Xi'an: Xidian University, 2014. |
| 宿元庆. Android基于动态加载的软件保护研究[D]. 西安:西安电子科技大学, 2014. | |
| [7] | DONG Hang. Research on Mobile Application Monitoring and Protection Technology[D]. Beijing: Beijing University of Posts and Telecommunications, 2014. |
| 董航. 移动应用程序检测与防护技术研究[D]. 北京:北京邮电大学, 2014. | |
| [8] | ZHU Hongjun, CHEN Yaoguang, HUA Baojian, et al. An Android Application Reinforcement Solution[J]. Computer Application and Software, 2016,11(33):297-300, 320. |
| 朱洪军, 陈耀光, 华保健, 等. 一种Android应用加固方案[J]. 计算机应用与软件, 2016,11(33):297-300,320. | |
| [9] | KIM N K, SHIM J, CHO S, et al. Android Application Protection Against Static Reverse Engineering Based on MultiDexing[J]. Journal of Internet Services and Information Security, 2016,11(6):54-64. |
| [10] | ZHOU W, WANG Z, ZHOU Y Z. et al. DIVILAR: Diversifying Intermediate Language for Anti-repacking on Android Platform[C]// SIGSAC. 4th ACM Conference on Data and Application Security and Privacy, March 15-17, 2014, San Antonio Texas USA. New York: ACM, 2014: 199-210. |
| [11] | WANG Zehua. Research and Implementation of Android Software Security Hardening Technology[D]. Chengdu: University of Electronic Science and Technology of China, 2016. |
| 王泽华. Android软件安全加固技术研究与实现[D]. 成都:电子科技大学, 2016. | |
| [12] | LIU Jiajia. Research on An Application Protection Method Based on Virtual Machine Customization[D]. Nanjing: Nanjing University of Science and Technology, 2017. |
| 刘佳佳. 一种基于虚拟机定制的应用保护方法研究[D]. 南京:南京理工大学, 2017. | |
| [13] | Tencent Cloud. Tencent Legu[EB/OL]. https://www.qcloud.com/product/cr.html, 2017-3-9. |
| 腾讯云. 腾讯乐固[EB/OL]. https://www.qcloud.com/product/cr.html, 2017-3-9. | |
| [14] | Bangbang Safety. Bangbang Reinforcement[EB/OL]. http://www.bangcle.com, 2017-11-10. |
| 梆梆安全. 梆梆加固[EB/OL]. http://www.bangcle.com, 2017-11-10. | |
| [15] | LIU Huiming. Android Application Automatic Localization and Obfuscation Sysytem[J]. Microelectronics and Computer, 2016,33(10):50-62. |
| 刘惠明. 安卓应用自动原生化及混淆系统[J]. 微电子学与计算机, 2016,33(10):50-62. | |
| [16] | MULLINER C. Android DDI: Introduction to Dynamic Dalvik Instrumentation[EB/OL]. https://github.com/crmulliner/ddi, 2019-5-11. |
| [17] | Hey-Rays . IDA[EB/OL]. https://www.hex-rays.com/products/ida/index.shtml, 2015-5-27. |
| [18] | Google. Apktool[EB/OL]. http://www.softpedia.com/get/Programming/Debuggers-Dec-ompilers-Dissase-mblers/ApkTool.html, 2017-9-22. |
| [19] | Android Open Source. Dalvik Executable File Format[EB/OL]. https://source.androi-d.google.cn/devices/tech/dalvik/dexformat?hl=zh-cn, 2017-8-23. |
| [20] | Lambdalang . DexExtractor[EB/OL]. https://github.com/lambdalang/DexExtractor, 2015-7-11. |
| [21] | Oracle. Java[EB/OL]. http://www.java.com, 2019-5-12. |
| [22] | Android Open Source Project. Dalvik and Dalvik Virtual Machine[EB/OL]. http://code.google.com/p/dalvik/, 2019-5-12. |
| [23] | Android Open Source Project. Bytecode for the Dalvik VM[EB/OL]. http://source.android.com/tech/dalvik/dalvik-bytecode.html, 2019-5-12. |
| [24] | RYSZARD W, CONNOR T. Apktool[EB/OL]. https://ibotpeaibot.github.io/Apktool/, 2019-5-3. |
| [25] | SKYLOT . Dex to Java Decompiler[EB/OL]. https://github.com/skylot/jadx, 2019-5-12. |
| [26] | SWEETSCAPE SOFTWARE. 010 Editor[EB/OL]. https://www.sweetscape.com/010editor/, 2019-4-26. |
| [1] | Liuyang HOU, Senlin LUO, Limin PAN, Ji ZHANG. Multi-feature Android Malware Detection Method [J]. Netinfo Security, 2020, 20(1): 67-74. |
| [2] | Xin SONG, Kai ZHAO, Linlin ZHANG, Wenbo FANG. Research on Android Malware Detection Based on Random Forest [J]. Netinfo Security, 2019, 19(9): 1-5. |
| [3] | Liping DING, Xuehua LIU, Guangxuan CHEN, Yin LI. Overview of Digital Forensics Technologies of RAM in Android Devices [J]. Netinfo Security, 2019, 19(2): 10-17. |
| [4] | Zhongyuan QIN, Junrui ZHANG, Qunfang ZHANG, Zhiyong SONG. Android Terminals Control Technology Based on Inject and Hook [J]. Netinfo Security, 2018, 18(9): 66-73. |
| [5] | Xinlong SONG, Dong ZHENG, Zhonghuang YANG. Mobile Device Management System Based on AOSP and SELinux [J]. Netinfo Security, 2017, 17(9): 103-106. |
| [6] | Debing LU, Haoliang CUI, Wen ZHANG, Shaozhang NIU. Application Security Reinforcement Scheme Based on Intent Filter [J]. Netinfo Security, 2017, 17(11): 67-73. |
| [7] | Jiajia LIU, Yan YU, Hengwei HU, Jiashun WU. Research on a Protection Mechanism Based on Virtual Machine Customization [J]. Netinfo Security, 2017, 17(1): 63-67. |
| [8] | Qing LEI, Lihua JING, Deming ZHAO, Jilong ZHENG. Research on the Technology of Gun Detection System for Android APP Videos Based on Deep Learning [J]. Netinfo Security, 2016, 16(9): 149-153. |
| [9] | Weiping WEN, Yang TANG, Li SHEN. An APP Sensitive Behaviors Detection Method Based on Android Kernel and Its Implementation [J]. Netinfo Security, 2016, 16(8): 18-23. |
| [10] | Lifang YU, Tianchang YANG, Shaozhang NIU. An Enhanced Security Access Control Scheme for Inter-component Communication in Android [J]. Netinfo Security, 2016, 16(8): 54-60. |
| [11] | Lewei QU, Senlin LUO, Zhipeng SUN, Shuai ZHU. Research on the Method of Data Integrity Detecting on Android System [J]. Netinfo Security, 2016, 16(8): 61-67. |
| [12] | Jiawang ZHANG, Yanwei LI. Research and Design on Malware Detection System Based on N-gram Algorithm [J]. Netinfo Security, 2016, 16(8): 74-80. |
| [13] | Jingya YANG, Senlin LUO, Shuai ZHU, Lewei QU. Research on Method of Android System Malware Behavior Monitoring Based on Multi-level and Cross-view Analysis [J]. Netinfo Security, 2016, 16(7): 40-46. |
| [14] | Yameng LI, Jingsha HE. Research on Different Versions of YAFFS2 File Recovery Algorithm Based on Hash [J]. Netinfo Security, 2016, 16(5): 51-57. |
| [15] | Weiping WEN, Han ZHANG, Xianglei CAO. Design and Implementation of the Scheme of Obfuscation Based on the Recombination of the Android Executable File [J]. Netinfo Security, 2016, 16(5): 71-77. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||