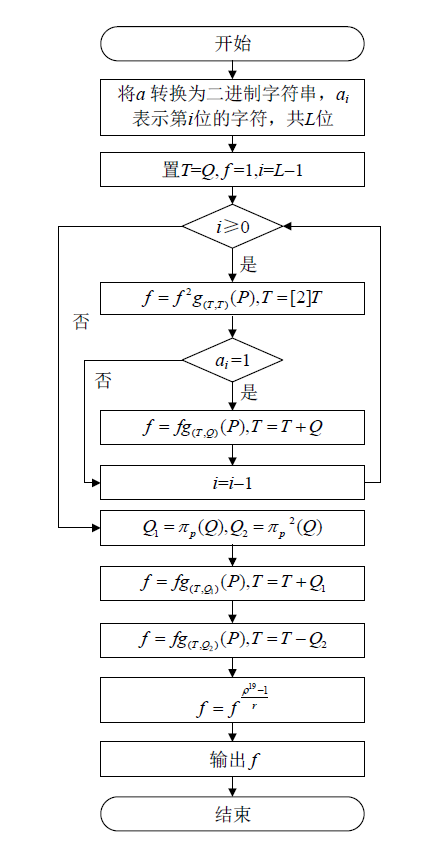
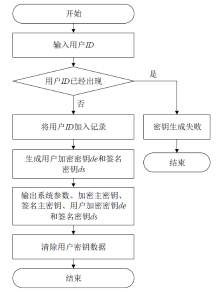
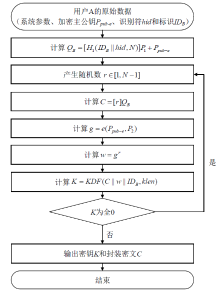
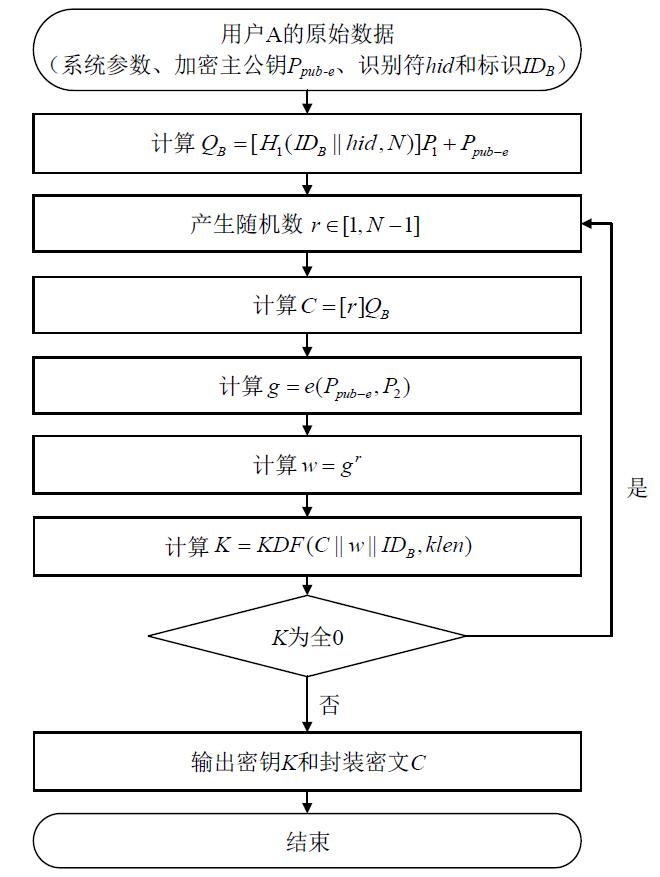
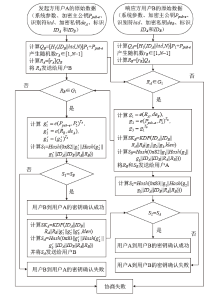
| [1] |
GUPTA S, GUPTA V. Revocable Key Identity Based Cryptography without Key Escrow Problem[C]// IEEE. 2016 International Conference on Computing, Communication and Automation(ICCCA). New York:IEEE, 2016: 443-448.
|
| [2] |
SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]// Springer. CRYPTO 1984 on Advances in Cryptology. Heidelberg: Springer, 1984: 47-53.
|
| [3] |
SONG Fei, SHIYuanbing, HUANGMinghao. A Method of Industrial Internet Entity Mutual Trust Combining PKI and IBE Technology System[C]// IEEE. 2020 3rd International Conference on Artificial Intelligence and Big Data(ICAIBD). New York:IEEE, 2020: 304-308.
|
| [4] |
TANAKA H. A Realization Schemes for the Identity-Based Cryptosystems[C]// Springer. Conference on the Theory and Application of Cryptographic Techniques. Heidelberg: Springer, 1987: 341-349.
|
| [5] |
TSUJII S, ITOH T. An ID-Based Cryptosystem Based on the Discrete Logarithm Problem[J]. IEEE Journal on Selected Areas in Communications, 1989, 7(4): 467-473.
doi: 10.1109/49.17709
URL
|
| [6] |
BONEH D, FRANKLIN M. Identity-Based Encryption from the Weil Pairing[C]// Springer. 21st Auunal International Cryptology Conference on Advances in Cryptology. Heidelberg: Springer, 2001: 213-229.
|
| [7] |
HORWITZ J, LYNN B. Towards Hierarchical Identity-Based Encryption[C]// Springer. International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2002: 466-481.
|
| [8] |
GENTRY C, SILVERBERG A. Hierarchical ID-Based Cryptography[J]. Advances in Cryptology-Asiacrypt, 2002, 82(4): 548-566.
|
| [9] |
WATERS B R. Efficient Identity-Based Encryption without Random Oracles[C]// Springer. 24th Annual International Conference on Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2005: 114-127.
|
| [10] |
BONEH D, BOYEN X. Secure Identity Based Encryption without Random Oracles[C]// Springer. Annual International Cryptology Conference. Heidelberg: Springer, 2004: 443-459.
|
| [11] |
NACCACHE D. Secure and Practical Identity-Based Encryption[J]. IET Information Security, 2007, 1(2): 59-64.
doi: 10.1049/iet-ifs:20055097
URL
|
| [12] |
BONEH D, BOYEN X. Anonymous Hierarchical Identity-Based Encryption(Without Random Oracles)[C]// Springer. International Conference on Advances in Cryptology. Heidelberg: Springer, 2006: 290-307.
|
| [13] |
BONEH D, GENTRY C, HAMBURG M. Space-Efficient Identity Based Encryption without Pairings[C]// IEEE. 48th Annual IEEE Symposium on Foundations of Computer Science. New York: IEEE, 2007: 647-657.
|
| [14] |
GB/T 38635. 1-2020 Information Security Technology-Identity-Based Cryptographic Algorithms SM9[S]. Beijing: Standards Press of China, 2020.
|
|
GB/T 38635. 1-2020 信息安全技术 SM9标识密码算法[S]. 北京: 标准出版社, 2020.
|
| [15] |
BARRETO P, NAEHRIG M. Pairing-Friendly Elliptic Curves of Prime Order[C]// Springer. Selected Areas in Cryptography. Heidelberg: Springer, 2005: 319-331.
|
| [16] |
YUAN Feng, CHENG Chaohui. Overview on SM9 Identity-Based Cryptographic Algorithm[J]. Journal of Information Security Research, 2016, 2(11): 1008-1027.
|