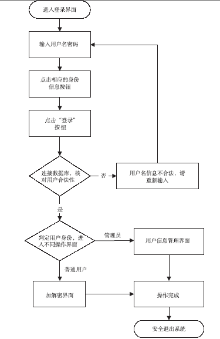
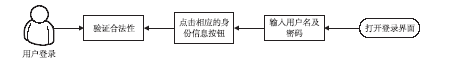
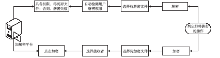
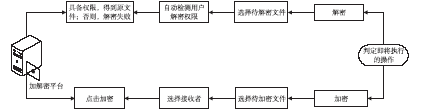
| [1] |
SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[EB/OL]. .
|
| [2] |
BONEH D, FRANKLIN M.Identity-based Encryption from the Weil Pairing[J]. Siam Journal on Computing, 2003, 32(3):213-229.
|
| [3] |
HORWITZ J, LYNN B. Toward Hierarchical Identity-Based Encryption[EB/OL]. .
|
| [4] |
GENTRY C, SILERBERG A.Hierarchical ID-Based Cryptography[J]. Lecture Notes in Computer Science, 2002, 82(4):548-566.
|
| [5] |
BONEH D, BOYEN X.Efficient Selectice-ID Secure Identity based Ncryption without Random Oracles[J]. Journal of Cryptology, 2004(4):223-238.
|
| [6] |
方巍,文学志,潘吴斌,等.云计算:概念、技术及应用研究综述[J].南京信息工程大学学报:自然科学版,2012(4):351-361.
|
| [7] |
DAN B, BOYEN X, GOH E J.Hierarchical Identity-based Encryption with Constant Size Ciphertext[C]//International Association for Cryptologic Research. 24th Annual International Conference on Theory and Applications of Cryptographic Techniques, May 22-26,2005, Computer Science Department of University of Aarhus, Aarhus, Denmark. Berlin: Springer, 2005: 440-456.
|
| [8] |
杨晨. 基于双线性对的密码协议的设计与分析[D].西安:西安电子科技大学,2007.
|
| [9] |
张席,杨玲.一个高效的基于身份的分层加密方案[J].计算机工程与应用,2012,48(24):101-105.
|
| [10] |
刘鹏. 云计算技术基础[M].北京:电子工业出版社,2011.
|
| [11] |
王庆波,金涬,何乐,等.虚拟化与云计算[M].北京:电子工业出版社,2010.
|
| [12] |
GUPTA R.Above the Clouds: A View of Cloud Computing[J]. Eecs Department University of California Berkeley,2009, 53(4) : 50-58.
|
| [13] |
李刚. 疯狂的Java讲义[M].北京:电子工业出版社,2014.
|
| [14] |
许春根,贡生.软件设计模式及其角色图的表示[J].计算机应用研究,2003,20(2):27-28.
|
| [15] |
岳旭平,王道顺.可重用Java数据库操作组件的设计和实现[J].计算机应用研究,2006,23(2):160-162.
|
| [16] |
谢文兰. 基于Java数据库技术实现用户注册与登录界面[J].湖南工程学院学报:自然科学版,2014,24(2):45-48.
|
| [17] |
王于愚,李祥.Java并发类库包的研究与应用[J].计算机应用,2006,26(S2):260-262.
|
| [18] |
赵洋,包文意,熊虎,等. 云计算里一种陷门无法识别的公钥搜索加密方案[J]. 信息网络安全,2016(1):1-5.
|
| [19] |
吕校春,李玲莉.基于Swing的Java GUI组件的开发[J].机械工程师,2008(5):129-131.
|
| [20] |
王晓哲. Java Swing组件技术[J].天津职业院校联合学报,2008,10(3):138-142.
|
| [21] |
苏碧霞. 探析JAVA Swing工具包在图形用户界面设计中的应用[J].信息与电脑:理论版,2013(5):143-144.
|
| [22] |
廖子渊,陈明志,邓辉. 基于评价可信度的云计算信任管理模型研究[J]. 信息网络安全,2016(2):33-39.
|