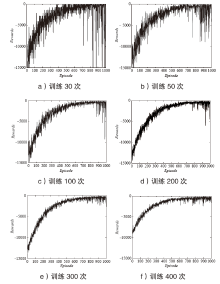
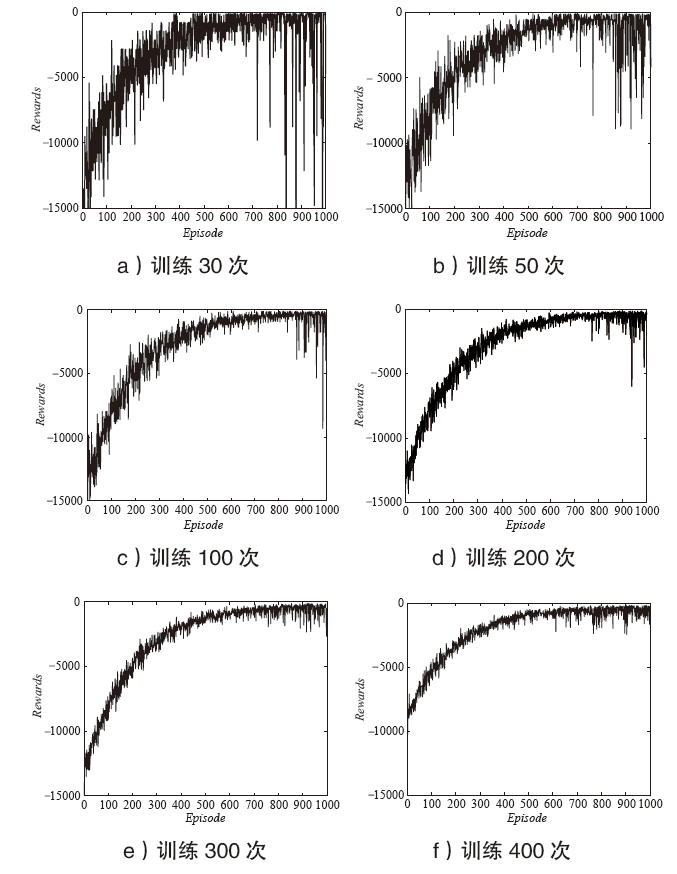
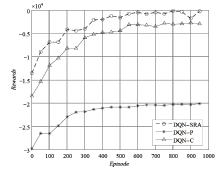
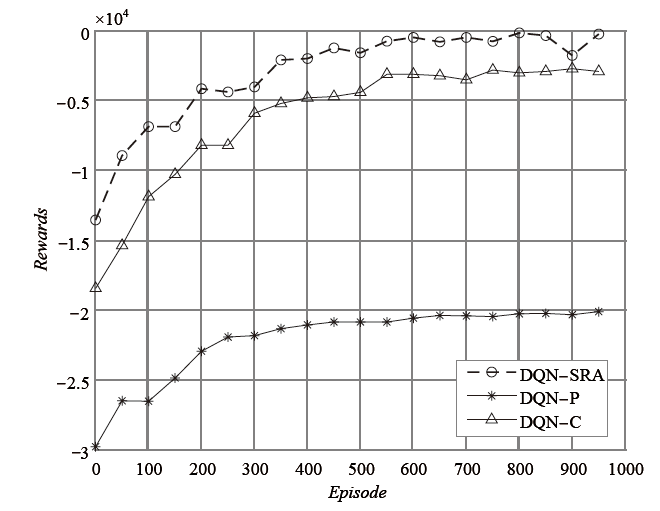
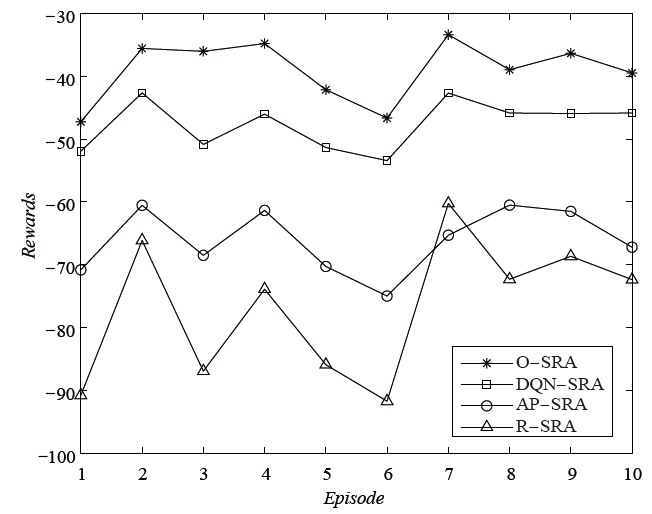
Netinfo Security ›› 2022, Vol. 22 ›› Issue (6): 44-52.doi: 10.3969/j.issn.1671-1122.2022.06.005
Previous Articles Next Articles
Security Resource Allocation Method for Internet of Things Based on Reinforcement Learning
ZHAO Hong1,2, LI Shan2, ZUO Peiliang2( ), WEI Zhanzhen2
), WEI Zhanzhen2
- 1. University of Science and Technology of China, Hefei 230026, China
2. Beijing Electronic Science and Technology Institute, Beijing 100070, China
-
Received:2022-02-21Online:2022-06-10Published:2022-06-30 -
Contact:ZUO Peiliang E-mail:zplzpl88@bupt.cn
CLC Number:
Cite this article
ZHAO Hong, LI Shan, ZUO Peiliang, WEI Zhanzhen. Security Resource Allocation Method for Internet of Things Based on Reinforcement Learning[J]. Netinfo Security, 2022, 22(6): 44-52.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.06.005
| [1] |
OMONI B, HUSSAIN R, JAVED M A, et al. Fog/Edge Computing-Based IoT(FECIoT): Architecture, Applications, and Research Issues[J]. IEEE Internet of Things Journal, 2019, 6(3): 4118-4149.
doi: 10.1109/JIOT.2018.2875544 URL |
| [2] | GUPTA S, GARG R, GUPTA N, et al. Energy-Effcient Dynamic Homomorphic Security Scheme for Fog Computing in IoT Networks[J]. Journal of Information Security and Applications, 2021, 58: 1-8. |
| [3] |
TARIQ N, ASIM M, AL-OBEIDAT F, et al. The Security of Big Data in Fog-Enabled IoT Applications Including Blockchain: A Survey[J]. Sensors, 2019, 19(8): 1788-1821.
doi: 10.3390/s19081788 URL |
| [4] | SADIQUE K M, RAHMANI R, JOHANNESSON P. Fog Computing for Trust in the Internet of Things(IoT): A Systematic Literature Review[C]// IEEE. 2020 International Conference on Computer Science, Engineering and Applications(ICCSEA). New York:IEEE, 2020: 1-6. |
| [5] | FERRETTI L, MARCHETTI M, COLAJANNI M. Fog-Based Secure Communications for Low-Power IoT Devices[J]. ACM Transactions on Internet Technology, 2019, 19(2): 1-21. |
| [6] | AMOR A B, ABID M, MEDDEB A. A Secure Fog-Based Communication Scheme[C]// IEEE. 2017 International Conference on Internet of Things, Embedded Systems and Communications(IINTEC). New York:IEEE, 2017: 146-151. |
| [7] |
WU Yongpeng, KHISTI A, XIAO Chengshan, et al. A Survey of Physical Layer Security Techniques for 5G Wireless Networks and Challenges Ahead[J]. IEEE Journal on Selected Areas in Communications, 2018, 36(4): 679-695.
doi: 10.1109/JSAC.2018.2825560 URL |
| [8] |
ZOU Yulong, ZHU Jia, WANG Xianbin, et al. A Survey on Wireless Security: Technical Challenges, Recent Advances, and Future Trends[J]. Proceedings of the IEEE, 2016, 104(9): 1727-1765.
doi: 10.1109/JPROC.2016.2558521 URL |
| [9] | HADDAD S, OZGUR A, TELATAR E. Can Full-Duplex More Than Double the Capacity of Wireless Networks[C]// IEEE. 2017 IEEE International Symposium on Information Theory(ISIT). New York:IEEE, 2017: 963-967. |
| [10] |
LEI Hongjiang, YANG Zixuan, PARK K H, et al. Secrecy Outage Analysis for Cooperative NOMA Systems with Relay Selection Schemes[J]. IEEE Transactions on Communications, 2019, 67(9): 6282-6298.
doi: 10.1109/TCOMM.2019.2916070 URL |
| [11] |
WANG Zhenling, PENG Zhangyou. Secrecy Performance Analysis of Relay Selection in Cooperative NOMA Systems[J]. IEEE Access, 2019, 7: 86274-86287.
doi: 10.1109/ACCESS.2019.2925380 |
| [12] | GOMEZ G, MARTIN-VEGA F J, LOPEZ-MARTINEZ F J, et al. Physical Layer Security in Uplink NOMA Multi-Antenna Systems with Randomly Distributed Eavesdroppers[EB/OL]. (2017-09-14) [2022-01-13]. https://arxiv.org/abs/1709.04693. |
| [13] | FENG Youhong, YAN Shihao, YANG Zhen, et al. User and Relay Selection with Artificial Noise to Enhance Physical Layer Security[EB/OL]. (2017-12-06) [2021-01-25]. https://arxiv.org/abs/1712.02104v2. |
| [14] |
LV Lu, DING Zhiguo, NI Qiang, et al. Secure MISO-NOMA Transmission with Artificial Noise[J]. IEEE Transactions on Vehicular Technology, 2018, 67(7): 6700-6705.
doi: 10.1109/TVT.2018.2811733 URL |
| [15] |
YAN Shihao, ZHOU Xiangyun, YANG Nan, et al. Secret Channel Training to Enhance Physical Layer Security with a Full-Duplex Receiver[J]. IEEE Transactions on Information Forensics and Security, 2018, 13(11): 2788-2800.
doi: 10.1109/TIFS.2018.2834301 URL |
| [16] |
SOHRABI R, ZHU Qiping, HUA Yingbo. Secrecy Analyses of a Full-Duplex MIMOME Network[J]. IEEE Transactions on Signal Processing, 2019, 67(23): 5968-5982.
doi: 10.1109/TSP.2019.2949501 URL |
| [17] | MOBASHERI M, KIM Y, KIM W. Toward Developing Fog Decision Making on the Transmission Rate of Various IoT Devices Based on Reinforcement Learning[J]. IEEE Internet of Things Magazine, 2020, 3: 38-42. |
| [18] | FAN Qiang, ANSARI N. Towards Workload Balancing in Fog Computing Empowered IoT[J]. IEEE Transactions on Network Science& Engineering, 2020, 7: 253-262. |
| [19] |
LIU Mengyu, LIU Yuan. Price-Based Distributed Offloading for Mobile-Edge Computing with Computation Capacity Constraints[J]. IEEE Wireless Communications Letters, 2018, 7(3): 420-423.
doi: 10.1109/LWC.2017.2780128 URL |
| [20] |
XI Linhan, WANG Ying, WANG Yang, et al. Deep Reinforcement Learning-Based Service-Oriented Resource Allocation in Smart Grids[J]. IEEE Access, 2021, 9: 77637-77648.
doi: 10.1109/ACCESS.2021.3082259 URL |
| [21] |
WEI Yifei, YU F R, SONG Mei, et al. Joint Optimization of Caching, Computing, and Radio Resources for Fog-Enabled IoT Using Natural Actor-Critic Deep Reinforcement Learning[J]. IEEE Internet of Things Journal, 2019, 6(2): 2061-2073.
doi: 10.1109/JIOT.2018.2878435 |
| [22] |
WYNER A D. The Wire-Tap Channel[J]. Bell System Technical Journal, 1975, 54: 1355-1387.
doi: 10.1002/j.1538-7305.1975.tb02040.x URL |
| [23] |
LI Wei, GHOGHO M, CHEN Bin, et al. Secure Communication via Sending Artificial Noise by the Receiver: Outage Secrecy Capacity/Region Analysis[J]. IEEE Communications Letters, 2012, 16(10): 1628-1631.
doi: 10.1109/LCOMM.2012.081612.121344 URL |
| [24] |
CHEN Xing, LIU Guizhong. Energy-Efficient Task Offloading and Resource Allocation via Deep Reinforcement Learning for Augmented Reality in Mobile Edge Networks[J]. IEEE Internet of Things Journal, 2021, 8(13): 10843-10856.
doi: 10.1109/JIOT.2021.3050804 URL |
| [25] |
GOUDARZI M, WU Hanming, PALANISWAMI M S, et al. An Application Placement Technique for Concurrent IoT Applications in Edge and Fog Computing Environments[J]. IEEE Transactions on Mobile Computing, 2021, 20(4): 1298-1311.
doi: 10.1109/TMC.2020.2967041 URL |
| [26] | ZUO Peiliang, WANG Chen, YAO Ze, et al. An Intelligent Routing Algorithm for LEO Satellites Based on Deep Reinforcement Learning[C]// IEEE. IEEE 94nd Vehicular Technology Conference(VTC2021-Fall). New York:IEEE, 2021: 1-5. |
| [27] |
YU Yiding, WANG Taotao, LIEW S C. Deep-Reinforcement Learning Multiple Access for Heterogeneous Wireless Networks[J]. IEEE Journal on Selected Areas in Communications, 2019, 37: 1277-1290.
doi: 10.1109/JSAC.2019.2904329 |
| [28] |
GU Bo, ZHANG Xu, LIN Ziqi, et al. Deep Multi-Agent Reinforcement Learning-Based Resource Allocation for Internet of Controllable Things[J]. IEEE Internet of Things Journal, 2021, 8: 3066-3074.
doi: 10.1109/JIOT.2020.3023111 URL |
| [29] | LANGE S, RIEDMILLER M. Deep Auto-Encoder Neural Networks in Reinforcement Learning[C]// IEEE. International Joint Conference on Neural Networks(IJCNN). New York:IEEE, 2010: 1-8. |
| [1] | LI Tong, REN Shuai, WANG Gang, MENG Qingyu. Cloud-edge-device Collaborative Integrity Verification Scheme Based on Chameleon Authentication Tree for Streaming Data [J]. Netinfo Security, 2022, 22(1): 37-45. |
| [2] | CHEN Qinggang, DU Yanhui, HAN Yi, LIU Xiangyu. IoT Device Recognition Model Based on Depthwise Separable Convolution [J]. Netinfo Security, 2021, 21(9): 67-73. |
| [3] | WU Kehe, CHENG Rui, ZHENG Bihuang, CUI Wenchao. Research on Security Communication Protocol of Power Internet of Things [J]. Netinfo Security, 2021, 21(9): 8-15. |
| [4] | LI Qun, DONG Jiahan, GUAN Zhitao, WANG Chao. A Clustering and Classification-based Malicious Attack Detection Method for Internet of Things [J]. Netinfo Security, 2021, 21(8): 82-90. |
| [5] | LIU Xin, GUO Zhenbin, SONG Yuchen. An Authentication Scheme Based on SGX for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(6): 1-10. |
| [6] | LIU Jing*, ZHANG Yuchen, ZHANG Hongqi. Automatic Intrusion Response Decision-making Method Based on Q-Learning [J]. Netinfo Security, 2021, 21(6): 26-35. |
| [7] | LI Tong, ZHOU Xiaoming, REN Shuai, XU Jian. Light-weight Mutual Authentication Protocol for Mobile Edge Computing [J]. Netinfo Security, 2021, 21(11): 58-64. |
| [8] | DING Jupeng, YI Zhiling, WANG Jintao, YANG Hui. Comparative Research of Benchmark Security Capacity of Visible Light Communication Physical Links [J]. Netinfo Security, 2020, 20(5): 65-71. |
| [9] | LIU Jianwei, HAN Yiran, LIU Bin, YU Beiyuan. Research on 5G Network Slicing Security Model [J]. Netinfo Security, 2020, 20(4): 1-11. |
| [10] | LANG Weimin, ZHANG Han, ZHAO Yifeng, YAO Jinfang. A Blockchain-based Behavior Regulation and Activities Management Scheme for Internet of Things [J]. Netinfo Security, 2020, 20(2): 22-29. |
| [11] | FENG Yan, LIU Nian, XIE Sijiang. A Bi-directional Use Scheme of Quantum Key Pool [J]. Netinfo Security, 2020, 20(12): 40-46. |
| [12] | FAN Bo, GONG Gangjun, SUN Shuxian. Research on Dynamic Security System of Distribution IoT Based on Classified Protection of Cybersecurity 2.0 [J]. Netinfo Security, 2020, 20(11): 10-14. |
| [13] | HU Die, MA Dongtang, GONG Ming, MA Zhao. A Physical Layer Security Authentication Method Based on PUF [J]. Netinfo Security, 2020, 20(1): 61-66. |
| [14] | A-yong YE, Junlin JIN, Lingyu MENG, Ziwen ZHAO. Research on Access Control for Privacy Protection of Mobile Terminals [J]. Netinfo Security, 2019, 19(8): 51-60. |
| [15] | Qiongqiong DUAN, Dinghua XIANG, Hongzhou SHI. Design on the Blockchain-based Authentication for Smart Objects [J]. Netinfo Security, 2018, 18(9): 95-101. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||