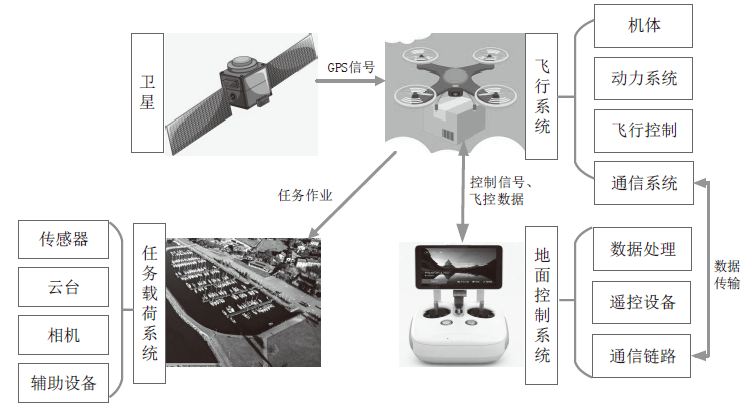
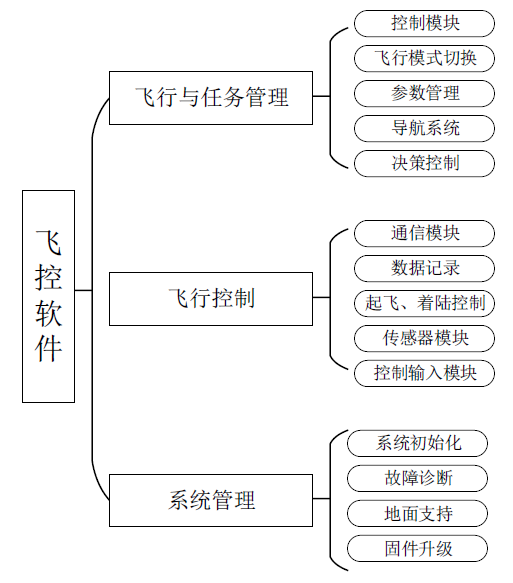
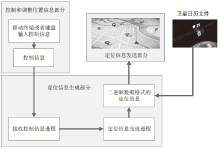
Netinfo Security ›› 2022, Vol. 22 ›› Issue (3): 10-19.doi: 10.3969/j.issn.1671-1122.2022.03.002
Previous Articles Next Articles
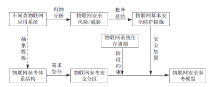
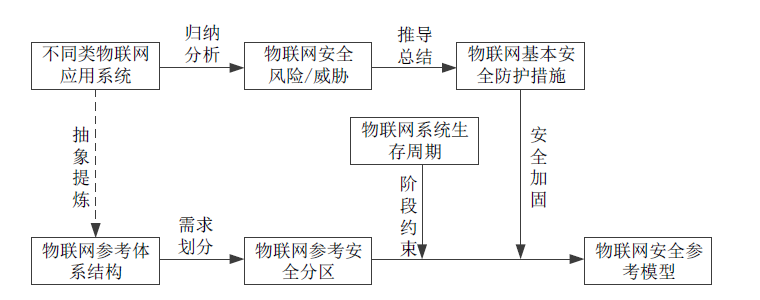
The Security Reference Model of the Multi-rotor UAV System
LI Guoqi1, HONG Sheng2,3( ), LAN Xueting1, ZHANG Hong1
), LAN Xueting1, ZHANG Hong1
- 1. School of Reliability and Systems Engineering, Beihang University, Beijing 100191, China
2. School of Cyber Science and Technology, Beihang University, Beijing 100191, China
3. School of Information Engineering, Nanchang University, Nanchang 330031, China
-
Received:2021-08-24Online:2022-03-10Published:2022-03-28 -
Contact:HONG Sheng E-mail:shenghong@buaa.edu.cn
CLC Number:
Cite this article
LI Guoqi, HONG Sheng, LAN Xueting, ZHANG Hong. The Security Reference Model of the Multi-rotor UAV System[J]. Netinfo Security, 2022, 22(3): 10-19.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.03.002
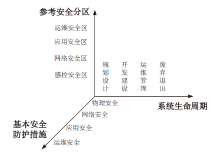
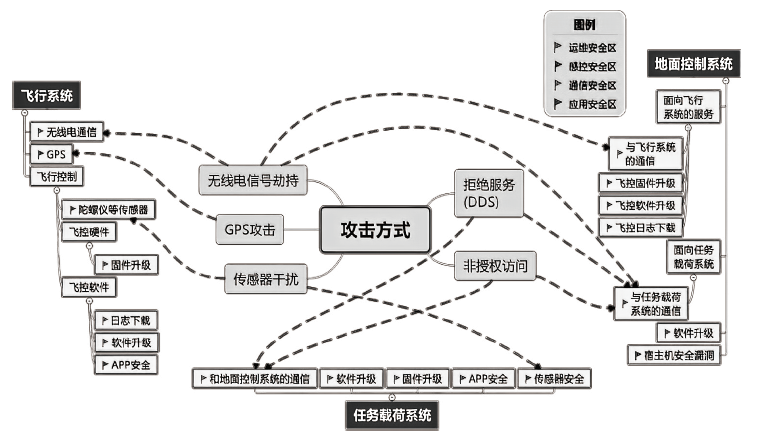
| 参考安全 分区 | 涉及功能点 | 可攻击方式 | 安全防护措施 | 对飞行安全影响类别 |
|---|---|---|---|---|
| 运维安全区 | 飞控硬件固件升级 | 植入后门 | 加强版本控制、流程管理合规 | A |
| 飞控硬件 | 恶意改造,如植入后门芯片、引出后门端子 | 确保硬件物理安全,加强安保 | A | |
| 飞控软件升级维护 | 植入后门 | 加强版本控制、流程管理合规 | A | |
| 离线导出飞行日志 | 数据丢失 | 流程管理合规 | D | |
| 通信安全区 | 无线电通信 | 伪装攻击 | 接入设备与网络时保证唯一标识 | A |
| 篡改攻击 | 对终端进行身份鉴别机制 | A | ||
| 中间人攻击、 重放攻击 | 禁用闲置端口、设置访问控制 | A | ||
| 感控安全区 | 惯性测量单位或加速度计等 | 共振干扰 | 增加减振垫,采用多版本非相似的冗余传感器 | C |
| 基于GPS的自动飞行 | GPS干扰 | 增加抗干扰防护罩,换用北斗导航 | C | |
| GPS欺骗 | 增加抗干扰防护罩,换用北斗导航 | B | ||
| 应用安全区 | 飞控软件APP | 植入后门 | 充分验证,开发流程合规 | A |
| 参考安全 分区 | 涉及功能点 | 可攻击方式 | 安全防护措施 | 对飞行安全影响类别 |
|---|---|---|---|---|
| 运维安全区 | 飞控固件升级工具软件 | 植入后门 | 加强版本控制、流程管理合规 | A |
| 飞控软件升级工具软件 | 植入后门 | 加强版本控制、流程管理合规 | A | |
| 飞控日志下载工具软件 | 植入后门,窃取数据 | 流程管理合规 | D | |
| 地面控制系统软件升级 | 植入后门 | 加强版本控制、流程管理合规 | A | |
| 通信安全区 | 与飞行系统的无线电 通信 | 伪装攻击 | 接入设备与网络时保证唯一标识 | A |
| 篡改攻击 | 对终端实行身份鉴别机制 | A | ||
| 中间人攻击、重放攻击 | 禁用闲置端口、设置访问控制 | A | ||
| 与任务载荷系统的通信 | 嗅探密码法 | 密码不以明文显示 | D | |
| 劫持信号法 | 数据传输隐私性保护,数据加密 | D | ||
| 拒绝服务 | 增加网络分流保护 | D | ||
| 黑洞攻击 | 让网络中的节点与网络中其他节点以一种独特的方式进行通信 | D | ||
| 应用安全区 | 宿主机APP | 非法登录 | 系统用户进行身份 识别 | A |
| 过期账号 登录 | 制定定期删除等管理制度 | A | ||
| 越权登录 | 限制默认账户的访问权限 | A | ||
| 特权盗取 | 遵循最小特权原则 | A | ||
| 恶意代码 攻击 | 及时更新补丁程序 | A |
| 参考安全 分区 | 涉及功能点 | 可攻击方式 | 安全防护措施 | 对飞行安全影响类别 |
|---|---|---|---|---|
| 运维安全区 | 固件升级 | 植入 后门 | 加强版本控制、流程管理合规 | D |
| 软件升级 | 植入 后门 | 加强版本控制、流程管理合规 | D | |
| 通信安全区 | 和地面控制系统的通信 | 非法 登录 | 系统用户进行身份识别 | D |
| 过期账号登录 | 制定定期删除等管理制度 | D | ||
| 越权 登录 | 限制默认账户的访问权限 | D | ||
| 特权 盗取 | 遵循最小特权原则 | D | ||
| 拒绝 服务 | 增加网络分流保护 | D | ||
| 感控安全区 | 传感器安全 | 传感器干扰 | 增加抗干扰防护或增加冗余设备 | C |
| 载荷设备 | 摄像头模块 攻击 | 对载荷状态数据与遥测数据进行监控与加密 | D | |
| APP安全 | 植入 后门 | 充分验证,开发流程合规 | C |
| [1] | GAO Jun, LI Xingzhao, WU Chunjuan, et al. Preliminary Study on Optimal Flight Parameters of Multi-rotor Plant Protection UAV in Different Growth Periods of Wheat[J]. China Plant Protection, 2021, 41(1):77-81, 101. |
| 高军, 李兴钊, 吴春娟, 等. 多旋翼植保无人机在小麦不同生育期飞防飞行参数优选初探[J]. 中国植保导刊, 2021, 41(1):77-81, 101. | |
| [2] | YANG Shuaiyu. Feasibility Review and Analysis of Unmanned Multi-rotor Aircraft Involved in China’s Commercial Logistics Terminal Distribution Mechanism[J]. China’s Strategic Emerging Industries, 2018, 10(42):1-2. |
| 杨帅宇. 无人驾驶多旋翼飞行器介入中国商业物流末端配送机制的可行性综述分析[J]. 中国战略新兴产业, 2018, 10(42):1-2. | |
| [3] | TAN Jinshi, SU Yunzhong, ZU Weiguo. Application of Multi-rotor UAV in Surveying of Open-pit Mining Area[J]. Mine Surveying, 2020, 48(3):101-104, 109. |
| 谭金石, 速云中, 祖为国. 多旋翼无人机在露天矿区测绘中的应用[J]. 矿山测量, 2020, 48(3):101-104, 109. | |
| [4] | UAV Research Group of Forward Looking Industry Research Institute. Development Status and Prospect Analysis of UAV Industry in China[J]. Dual Use Technologies & Products, 2020, 34(7):10-19. |
| 前瞻产业研究院无人机研究小组. 我国无人机行业发展现状与前景分析[J]. 军民两用技术与产品, 2020, 34(7):10-19. | |
| [5] | WU Zhijun, WANG Hui. The Difference between Security and Safety[J]. Netinfo Security, 2013, 13(8):84-86. |
| 吴志军, 王慧. 信息安全中Safety与Security的比较研究[J]. 信息网络安全, 2013, 13(8):84-86. | |
| [6] | BOUSTRAS G, WARING A. Towards a Reconceptualization of Safety and Security, Their Interactions, and Policy Requirements in a 21st Century Context[J]. Safety Science, 2020, 132(12):1-14. |
| [7] | ZHANG Jiyong. Review of UAV Information Security Research[J]. Digital Technology & Application, 2020, 38(2):185-187. |
| 张继永. 无人机信息安全研究综述[J]. 数字技术与应用, 2020, 38(2):185-187. | |
| [8] | XU Bingfeng, HUANG Zhiqiu, HU Jun, et al. Model-driven Safety Dependence Verification for Component-based Airborne Software Supporting Airworthiness Certification[J]. Acta Aeronautica ET Astronautica Sinica, 2012, 33(5):796-808. |
| 徐丙凤, 黄志球, 胡军, 等. 面向适航认证的模型驱动机载软件构件的安全性验证[J]. 航空学报, 2012, 33(5):796-808. | |
| [9] |
CLOTHIER R A, PALMER J L, WALKER R A, et al. Definition of an Airworthiness Certification Framework for Civil Unmanned Aircraft Systems[J]. Safety Science, 2011, 49(6):871-885.
doi: 10.1016/j.ssci.2011.02.004 URL |
| [10] | HUANG Zhiqiu, XU Bingfeng, KAN Shuanglong, et al. Survey on Embedded Software Safety Analysis Standards, Methods and Tools for Airborne System[J]. Journal of Software, 2014, 25(2):200-218. |
| 黄志球, 徐丙凤, 阚双龙, 等. 嵌入式机载软件安全性分析标准、方法及工具研究综述[J]. 软件学报, 2014, 25(2):200-218. | |
| [11] | HE Daojing, DU Xiao, QIAO Yinrong, et al. A Survey on Cyber Security of Unmanned Aerial Vehicles[J]. Chinese Journal of Computers, 2019, 42(5):1076-1094. |
| 何道敬, 杜晓, 乔银荣, 等. 无人机信息安全研究综述[J]. 计算机学报, 2019, 42(5):1076-1094. | |
| [12] | WANG Yuheng. Development History and Configuration Analysis of Multi-rotor UAV[J]. Public Communication of Science & Technology, 2019, 11(22):142-144. |
| 王宇恒. 多旋翼无人机的发展历程及构型分析[J]. 科技传播, 2019, 11(22):142-144. | |
| [13] |
GUARINO N. Formal Ontology, Conceptual Analysis and Knowledge Representation[J]. International Journal of Human-computer Studies, 1995, 43(5):625-640.
doi: 10.1006/ijhc.1995.1066 URL |
| [14] | WANG Zhixiang, XIAO Junmo. Design and Implementation of a Multi-level Reference Model for Firewall[J]. Journal of University of Electronic Science and Technology of China, 2003, 32(2):184-187. |
| 王志祥, 肖军模. 防火墙多级安全参考模型的设计与实现[J]. 电子科技大学学报, 2003, 32(2):184-187. | |
| [15] | HUANG Chengwei, JIA Yubo, CAI Hao. A Security Reverence Frameworkfor Mobile Agent[J]. Computer Applications and Software, 2010, 27(11):40-42, 98. |
| 黄成伟, 贾宇波, 蔡浩. 一种移动Agent安全参考模型[J]. 计算机应用与软件, 2010, 27(11):40-42, 98. | |
| [16] | YANG Jincui, FANG Binxing, ZHAI Lidong, et al. Research Towards IoT-oriented Universal Control System Security Model[J]. Journal on Communications, 2012, 33(11):49-56. |
| 杨金翠, 方滨兴, 翟立东, 等. 面向物联网的通用控制系统安全模型研究[J]. 通信学报, 2012, 33(11):49-56. | |
| [17] | GB/T 37044-2018 Information Security Technology—Security Reference Model and Generic Requirements for Internet of Things[S] Beijing: Standards Press of China, 2018. |
| GB/T 37044-2018信息安全技术—物联网安全参考模型及通用要求[S]. 北京: 中国标准出版社, 2018. | |
| [18] | GAO Qing, YUAN Liang, WU Jinqiang. Attitude Control of a Quadrotor UAV Based on New LQR[J]. Manufacturing Automation, 2014, 36(10):13-16. |
| 高青, 袁亮, 吴金强. 基于新型LQR的四旋翼无人机姿态控制[J]. 制造业自动化, 2014, 36(10):13-16. | |
| [19] | XU Jing, CAI Chenxiao, LI Yongqi, et al. Dual-loop Path Tracking and Control for Quad-rotor Miniature Unmanned Aerial Vehicles[J]. Control Theory & Applications, 2015, 32(10):1335-1342. |
| 许璟, 蔡晨晓, 李勇奇, 等. 小型四旋翼无人机双闭环轨迹跟踪与控制[J]. 控制理论与应用, 2015, 32(10):1335-1342. | |
| [20] | HUANG Yixin. Research on Attitude Control Method of Four Rotor Aircraft[D]. Chengdu: Southwest Jiaotong University, 2014. |
| 黄依新. 四旋翼飞行器姿态控制方法研究[D]. 成都:西南交通大学, 2014. | |
| [21] | LING Jinfu. Research on Flight Control Algorithm of Four Rotor Aircraft[D]. Nanchang: Nanchang University, 2013. |
| 凌金福. 四旋翼飞行器飞行控制算法的研究[D]. 南昌:南昌大学, 2013. | |
| [22] | BAI Jingjie. Research on Sliding Mode Control Algorithm of Four Rotor Aircraft[D]. Harbin: Harbin University of Technology, 2015. |
| 白敬洁. 四旋翼飞行器的滑模控制算法研究[D]. 哈尔滨:哈尔滨理工大学, 2015. | |
| [23] |
SADEGHZADEH I, ABDOLHOSSEINI M, ZHANG Youmin. Payload Drop Application Using an Unmanned Quadrotor Helicopter Based on Gain-scheduled PID and Model Predictive Control[J]. Unmanned Systems, 2014, 2(1):39-52.
doi: 10.1142/S2301385014500034 URL |
| [24] | KHATOON S, GUPTA D, DAS L K. PID&LQR Control for a Quadrotor: Modeling and Simulation [C]//IEEE. 2014 International Conference on Advances in Computing, Communications and Informatics(ICACCI), September 24-27, 2014, Noida, India. New York: IEEE, 2014: 796-802. |
| [25] | YANG Xiaochuan, LIU Gang, WANG Yuntao, et al. Overview of Pixhawk Open Source Flight Control Project and its Aviation Application Prospect[J]. Aerodynamic Missile Journal, 2018, 47(4):25-32. |
| 杨小川, 刘刚, 王运涛, 等. Pixhawk开源飞控项目概述及其航空应用展望[J]. 飞航导弹, 2018, 47(4):25-32. | |
| [26] | CHEN Zijie, LIU Yonghui, ZHAO Houbao, et al. Implementation of Constructing High Reliability Multi-rotor Controller Based on PX4[J]. Software Industry and Engineering, 2014, 14(6):38-42. |
| 陈子杰, 刘永辉, 赵厚宝, 等. 基于PX4构建高可靠多旋翼控制器的实现方法[J]. 软件产业与工程, 2014, 14(6):38-42. | |
| [27] | ZHANG Haijun, CHEN Yinghui. Research and Implementation of Flight Control System of Quadrotor Unmanned Aerial Vehicle[J]. Computer Measurement & Control, 2019, 27(5):105-108, 113. |
| 张海军, 陈映辉. 四旋翼无人机飞控系统的研究与实现[J]. 计算机测量与控制, 2019, 27(5):105-108, 113. | |
| [28] |
MILLER J, MINEAR P, NIESSNER A, et al. Intelligent Unmanned Air Vehicle Flight Systems[J]. Journal of Aerospace Computing, Information, and Communication, 2007, 4(5):816-835.
doi: 10.2514/1.26553 URL |
| [29] | GORAJ Z. UAV Platform Designed in WUT for Border Surveillance [C]//AIAA. AIAA Infotech, May 7-10, 2007, Rohnert Park, CA, USA. Reston: AIAA, 2007: 1-18. |
| [30] | SUN Jie, XIE Wenhan, BAI Ruijie. UAV Oblique Photogrammetric System and Its Application[J]. Science of Surveying and Mapping, 2019, 44(6):145-150. |
| 孙杰, 谢文寒, 白瑞杰. 无人机倾斜摄影技术研究与应用[J]. 测绘科学, 2019, 44(6):145-150. | |
| [31] | LI Bo, LI Xiaomin, YANG Sen. Research Status and Key Technologies of Four Rotor UAV in the United States[J]. Aerodynamic Missile Journal, 2018, 47(2):25-30. |
| 李博, 李小民, 杨森. 美国四旋翼无人机研究现状与关键技术[J]. 飞航导弹, 2018, 47(2):25-30. | |
| [32] | YUAN Sheng. The More Intelligent, the More “Uneasy”-Geekpwn 2015 Carnival[J]. China Information Security, 2015, 71(11):122-124. |
| 袁胜 .越智能, 越“不安”—记GeekPwn 2015嘉年华[J]. 中国信息安全, 2015, 71(11):122-124. | |
| [33] |
KOUBAA A, ALLOUCH A, ALAJLAN M, et al. Micro Air Vehicle Link(MAVlink) in a Nutshell: A Survey[J]. IEEE Access, 2019, 7(6):87658-87680.
doi: 10.1109/Access.6287639 URL |
| [34] | WU Ying, LIU Zhaoliang, KANG Lingzhou, et al. Security Analysis of MAVLink Communication Protocol[J]. Communications Technology, 2019, 52(4):946-950. |
| 吴颖, 刘照亮, 康令州, 等. MAVLink链路通信协议安全分析[J]. 通信技术, 2019, 52(4):946-950. | |
| [35] | ZHANG Linghao, WANG Sheng, ZHOU Hui, et al. Secure Communication Scheme of Unmanned Aerial Vehicle System Based on MAVLink Protocol[J]. Journal of Computer Applications, 2020, 40(8):2286-2292. |
| 张凌浩, 王胜, 周辉, 等. 基于MAVLink协议的无人机系统安全通信方案[J]. 计算机应用, 2020, 40(8):2286-2292. | |
| [36] | WANG Xiaoli, ZHAO Shubo, WANG Rui, et al. Implementation of Wireless Communication System Based on GNU Radio and HackRF[J]. Foreign Electronic Measurement Technology, 2018, 37(3):13-17. |
| 王晓丽, 赵树波, 王锐, 等. 基于GNU Radio与HackRF的无线通信系统实现[J]. 国外电子测量技术, 2018, 37(3):13-17. | |
| [37] |
GUMMINENI M, PAOPOLIPALLI T. Implementation of Reconfigurable Transceiver Using GNU Radio and HackRF One[J]. Wireless Personal Communications, 2020, 112(2):889-905.
doi: 10.1007/s11277-020-07080-0 URL |
| [38] | LIU Yachuan, KOU Yanhong. Research and Design of Synchronous GPS Spoofing Signal Generation Technology[J]. Journal of Beijing University of Aeronautics and Astronautics, 2020, 46(4):814-821. |
| 柳亚川, 寇艳红. 同步式GPS欺骗干扰信号生成技术研究与设计[J]. 北京航空航天大学学报, 2020, 46(4):814-821. | |
| [39] | YI Shuming, YOU Ling, LI Xian. An Improved Civilian GPS Asynchronous Spoofing Technology[J]. Telecommunication Engineering, 2021, 61(2):149-156. |
| 易曙明, 游凌, 李显. 一种改进的民用GPS异步欺骗技术[J]. 电讯技术, 2021, 61(2):149-156. | |
| [40] |
JOSE K A, SUH W D, XAVIER P B, et al. Surface Acoustic Ware MEMS Gyrocope[J]. Wave Motion, 2002, 36(4):367-381.
doi: 10.1016/S0165-2125(02)00030-6 URL |
| [41] | DEAN R N, CASTRO S T, FLOWERS G T, et al. A Characterization of the Performance of a MEMS Gyroscope in Acoustically Harsh Environments[J]. IEEE Transations on Industrial Electronics, 2011, 58(7):2591-2596. |
| [42] | SON Y, SHIN H, KIM D, et al. Rocking Drones with Intentional Sound Noise on Gyroscopic Sensors [C]//USENIX. The 24th USENIX Security Symposium, August 12-14, 2015, Washington, USA. Berkeley: USENIX, 2015: 881-896. |
| [43] | LI Guoqi. Software FMEA for Safety-critical System Based on Co-analysis of System Model and Software Model[J]. IEICE Transactions on Information & Systems, 2012, 95(12):3101-3105. |
| [44] | CHEN Chunmou. Research and Simulation of WSN Network Anti-DDoS Scheme Based on Traffic Threshold Decision Adaptive Mechanism[J]. Foreign Electronic Measurement Technology, 2020, 39(1):59-62. |
| 陈春谋. 基于流量阈值裁决分割机制的WSN网络抗DDoS算法研究[J]. 国外电子测量技术, 2020, 39(1):59-62. | |
| [45] |
HU Ronghua, DONG Xiaomei, WANG Daling. Defense Mechanism Against Node Replication Attacks and Sybil Attacks in Wireless Sensor Networks[J]. Acta Electronica Sinica, 2015, 43(4):743-752.
doi: 10.3969/j.issn.0372-2112.2015.04.017 |
|
胡蓉华, 董晓梅, 王大玲. 无线传感器网络节点复制攻击和女巫攻击防御机制研究[J]. 电子学报, 2015, 43(4):743-752.
doi: 10.3969/j.issn.0372-2112.2015.04.017 |
|
| [46] | FENG Dengguo, XU Jing, LAN Xiao. Study on 5G Mobile Communication Network Security[J]. Journal of Software, 2018, 29(6):1813-1825. |
| 冯登国, 徐静, 兰晓. 5G移动通信网络安全研究[J]. 软件学报, 2018, 29(6):1813-1825. | |
| [47] | LI Guoqi, LAN Xueting, ZHANG Hong, et al. Analysis of the Effects of Information Security Attacks on the Flight Safety of a Typical Multi-rotor UAV [C]//IEEE. The 11th International Conference on Quality, Reliability, Risk, Maintenance, and Safety Engineering, October 27-30, 2021, Chengdu, China. New York: IEEE, 2021: 59-71. |
| [1] | PENG Cheng, FAN Wei, ZHU Dali, YANG Fen. Research on Man-in-the-Middle Attack Detection in LTE Access Network Based on Weighted Bayesian Classifier [J]. Netinfo Security, 2023, 23(2): 1-10. |
| [2] | QIN Zhongyuan, GE Zhenwei, PAN Jingwei, CHEN Liquan. Research on Integrity Measurement Scheme Based on Virtual Trusted Platform Module [J]. Netinfo Security, 2023, 23(2): 11-18. |
| [3] | ZHAO Jia, GAO Ta, ZHANG Jiancheng. Method of Local Differential Privacy Method for High-Dimensional Data Based on Improved Bayesian Network [J]. Netinfo Security, 2023, 23(2): 19-25. |
| [4] | LI Yuancheng, LUO Hao, WANG Qingle, LI Jianbin. An Advanced Persistent Threat Model of New Power System Based on ATT&CK [J]. Netinfo Security, 2023, 23(2): 26-34. |
| [5] | WANG Yan, ZHANG Kunpeng, JI Zhicheng. Intelligent Optimization and Decision Method of Cloud Resources Based on Trusted Service [J]. Netinfo Security, 2023, 23(2): 35-44. |
| [6] | LIU Jue, CHENG Kaixin, YANG Weiwei. Research on Physical Layer Security Technologies for Smart Eavesdropper Attack [J]. Netinfo Security, 2023, 23(2): 45-53. |
| [7] | XU Zhanyang, CHENG Luofei, CHENG Jianchun, XU Xiaolong. A Scheme of Optimizing Deep Learning Model Using Bi-ADMM [J]. Netinfo Security, 2023, 23(2): 54-63. |
| [8] | CHEN Depeng, LIU Xiao, CUI Jie, ZHONG Hong. Research on Membership Inference Attack Method Based on Double Threshold Function [J]. Netinfo Security, 2023, 23(2): 64-75. |
| [9] | XIA Yihang, ZHANG Zhilong, WANG Muzi, CHEN Libo. Dependency-Based Vulnerability Detection Method in Container Supply Chain [J]. Netinfo Security, 2023, 23(2): 76-84. |
| [10] | HU Zhijie, CHEN Xingshu, YUAN Daohua, ZHENG Tao. Static Detection Method of Android Adware Based on Improved Random Forest Algorithm [J]. Netinfo Security, 2023, 23(2): 85-95. |
| [11] | WANG Ming, XING Yongheng, WANG Feng. Unsupervised Matrix Factorization Based Trigger Action Programming Rules Recommendation [J]. Netinfo Security, 2023, 23(2): 96-103. |
| [12] | LI Jiyu, FU Zhangjie, ZHANG Yubin. An Image Information Hiding Algorithm Based on Cross-Domain Adversarial Adaptation [J]. Netinfo Security, 2023, 23(1): 93-102. |
| [13] | LIU Qin, GUO Kaiyuan, TU Hang. Task Data Migration Solution Based on SM2 and SM4 Under TEE [J]. Netinfo Security, 2023, 23(1): 9-17. |
| [14] | FENG Yiting, MA Zhaofeng, XU Danheng, DUAN Pengfei. Evaluation Method for Cross-Chain Security Strength Access [J]. Netinfo Security, 2023, 23(1): 84-92. |
| [15] | SHEN Chuanxin, WANG Yongjie, XIONG Xinli. DNS Covert Channel Detection Based on Graph Attention Network [J]. Netinfo Security, 2023, 23(1): 73-83. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||