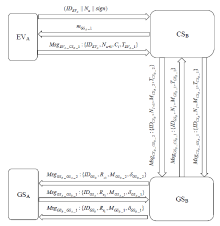
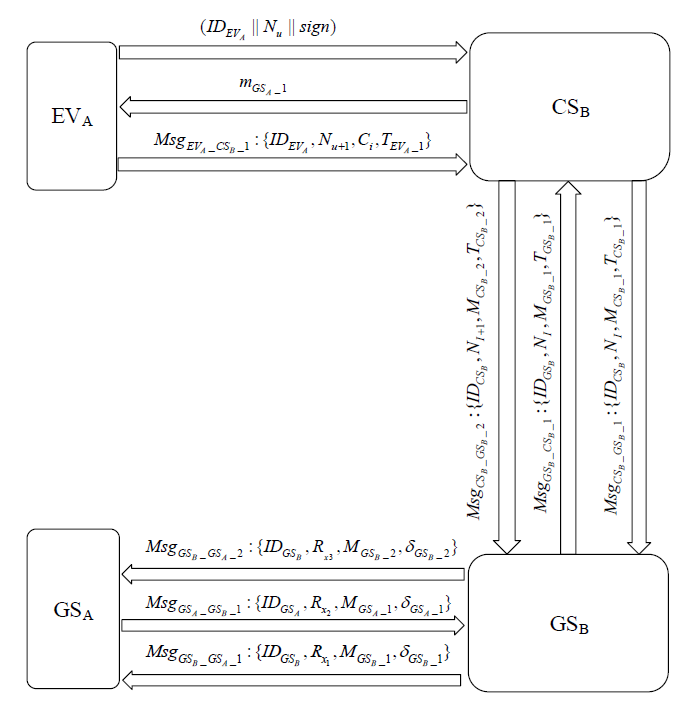
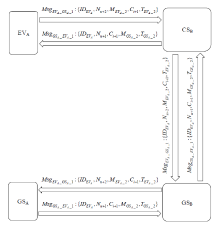
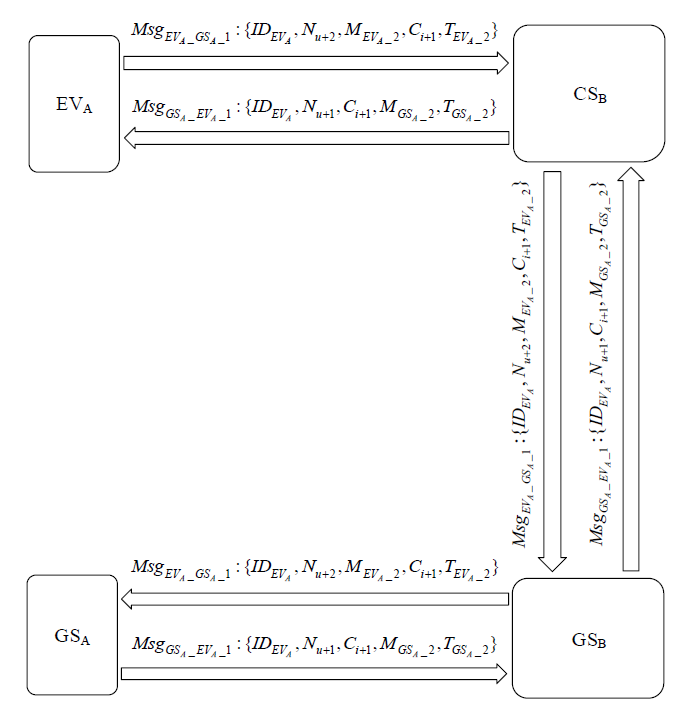
Netinfo Security ›› 2022, Vol. 22 ›› Issue (3): 20-28.doi: 10.3969/j.issn.1671-1122.2022.03.003
Previous Articles Next Articles
A Lightweight Cross-domain Mutual Authentication Scheme in V2G Networks
SHI Runhua( ), WANG Shuhao, LI Kunchang
), WANG Shuhao, LI Kunchang
- School of Control and Computer Engineering, North China Electric Power University, Beijing 102206, China
-
Received:2021-07-11Online:2022-03-10Published:2022-03-28 -
Contact:SHI Runhua E-mail:rhshi@ncepu.edu.cn
CLC Number:
Cite this article
SHI Runhua, WANG Shuhao, LI Kunchang. A Lightweight Cross-domain Mutual Authentication Scheme in V2G Networks[J]. Netinfo Security, 2022, 22(3): 20-28.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.03.003
| 符号 | 含义 | 符号 | 含义 |
|---|---|---|---|
| EVA | A域车辆 | $P{{K}_{G{{S}_{B}}}},S{{K}_{G{{S}_{B}}}}$ | GSB的公私钥对 |
| CSB | B域充电桩 | $P{{K}_{G{{S}_{A}}}},S{{K}_{G{{S}_{A}}}}$ | GSA的公私钥对 |
| GSA | A域服务器 | $h,{{H}_{1}}$ | 哈希函数 |
| GSB | B域服务器 | psw | 用户密码 |
| PKG | 密钥生成中心 | β | 用户指纹 |
| (C, R) | PUF产生的挑战响应对 | || | 连接操作符 |
| MAC | 消息认证码 | $\oplus $ | 异或操作符 |
| ${{k}_{C{{S}_{B}}\_G{{S}_{B}}}}$ | B域服务器和充电桩的会话密钥 | SM | 用户登录智能卡 |
| $Block\_D{{C}_{G{{S}_{B}}}}$ | GSB在区块链上的数字身份 | NU, NI | 随机数 |
| $Block\_D{{C}_{G{{S}_{A}}}}$ | GSA在区块链上的数字身份 | $MA{{C}_{{{k}_{C{{S}_{B}}\_G{{S}_{B}}}}}}$ | CSB和GSB间的消息认证码 |
| $P{{K}_{PKG}},S{{K}_{PKG}}$ | PKG的公私钥对 | $Ms{{g}_{P\_Q}}$ | 实体P到Q的消息 |
| [1] |
LI Fangxing, QIAO Wei, SUN Hongbin, et al. Smart Transmission Grid: Vision and Framework[J]. IEEE Transactions on Smart Grid, 2010, 1(2):168-177.
doi: 10.1109/TSG.2010.2053726 URL |
| [2] |
KEMPTON W, TOMIC J. Vehicle-to-grid Power Fundamentals: Calculating Capacity and Net Revenue[J]. Journal of Power Sources, 2005, 144(1):268-279.
doi: 10.1016/j.jpowsour.2004.12.025 URL |
| [3] |
PARK J, KIM H, CHOI J Y. Improving TCP Performance in Vehicle-to-Grid(V2G) Communication[J]. Electronics, 2019, 8(11):1206-1223.
doi: 10.3390/electronics8111206 URL |
| [4] | SAXENA N, GRIJALVA S, CHUKWUKA V, et al. Network Security and Privacy Challenges in Smart Vehicle-to-Grid[J]. IEEE Wireless Communications, 2017, 24(4):88-98. |
| [5] |
GUO Huaqun, WU Yongdong, BAO Feng, et al. UBAPV2G: A Unique Batch Authentication Protocol for Vehicle-to-Grid Communications[J]. IEEE Transactions on Smart Grid, 2011, 2(4):707-714.
doi: 10.1109/TSG.2011.2168243 URL |
| [6] |
LIU Hong, NING Huansheng, ZHANG Yan, et al. Aggregated-proofs Based Privacy-preserving Authentication for V2G Networks in the Smart Grid[J]. IEEE Transactions on Smart Grid, 2012, 3(4):1722-1733.
doi: 10.1109/TSG.2012.2212730 URL |
| [7] |
LIU Hong, NING Huansheng, ZHANG Yan, et al. Role-dependent Privacy Preservation for Secure V2G Networks in the Smart Grid[J]. IEEE Transactions on Information Forensics and Security, 2013, 9(2):208-220.
doi: 10.1109/TIFS.2013.2295032 URL |
| [8] |
SAXENA N, CHOI B J. Authentication Scheme for Flexible Charging and Discharging of Mobile Vehicles in the V2G Networks[J]. IEEE Transactions on Information Forensics and Security, 2016, 11(7):1438-1452.
doi: 10.1109/TIFS.2016.2532840 URL |
| [9] | TSENG H R. A Secure and Privacy-preserving Communication Protocol for V2G Networks [C]//IEEE. 2012 IEEE Wireless Communications and Networking Conference(WCNC), April 1-4, 2012, Paris, France. New Jersey: IEEE, 2012: 2706-2711. |
| [10] |
ABDALLAH A, SHEN X S. Lightweight Authentication and Privacy-preserving Scheme for V2G Connections[J]. IEEE Transactions on Vehicular Technology, 2016, 66(3):2615-2629.
doi: 10.1109/TVT.2016.2577018 URL |
| [11] |
SHEN Jian, ZHOU Tianqi, WEI Fushan, et al. Privacy-preserving and Lightweight Key Agreement Protocol for V2G in the Social Internet of Things[J]. IEEE Internet of Things Journal, 2017, 5(4):2526-2536.
doi: 10.1109/JIOT.2017.2775248 URL |
| [12] |
GOPE P, SIKDAR B. An Efficient Privacy-preserving Authentication Scheme for Energy Internet-based Vehicle-to-Grid Communication[J]. IEEE Transactions on Smart Grid, 2019, 10(6):6607-6618.
doi: 10.1109/TSG.5165411 URL |
| [13] |
BANSAL G, NAREN N, CHAMOLA V, et al. Lightweight Mutual Authentication Protocol for V2G Using Physical Unclonable Function[J]. IEEE Transactions on Vehicular Technology, 2020, 69(7):7234-7246.
doi: 10.1109/TVT.25 URL |
| [14] | GARG S, KAUR K, KADDOUM G, et al. An Efficient Blockchain-based Hierarchical Authentication Mechanism for Energy Trading in V2G Environment [C]//IEEE. 2019 IEEE International Conference on Communications Workshops(ICC Workshops), May 20-24, 2019, Shanghai, China. New Jersey: IEEE, 2019: 1-6. |
| [15] |
WANG Huaqun, WANG Qihua, HE Debiao, et al. BBARS: Blockchain-based Anonymous Rewarding Scheme for V2G Networks[J]. IEEE Internet of Things Journal, 2019, 6(2):3676-3687.
doi: 10.1109/JIOT.2018.2890213 |
| [16] |
AITZHAN Z, SVETINOVIC D. Security and Privacy in Decentralized Energy Trading through Multi-signatures, Blockchain and Anonymous Messaging Streams[J]. IEEE Transactions on Dependable and Secure Computing, 2016, 15(5):840-852.
doi: 10.1109/TDSC.8858 URL |
| [17] | PATIL A S, HAMZA R, HASSAN A, et al. Efficient Privacy-preserving Authentication Protocol Using PUFs with Blockchain Smart Contracts[EB/OL]. https://www.sciencedirect.com/science/article/pii/S0167404820302340, 2021-11-12. |
| [18] | LIU Donglan, LI Dong, LIU Xin, et al. Research on a Cross-domain Authentication Scheme Based on Consortium Blockchain in V2G Networks of Smart Grid [C]//IEEE. 2nd IEEE Conference on Energy Internet and Energy System Integration(EI2), October 20-22, 2018, Beijing, China. New Jersey: IEEE, 2018: 1-5. |
| [19] | MAES R. Physically Unclonable Functions: Concept and Constructions[M]. Heidelberg: Springer, 2013. |
| [20] | CHEN Q, CSABA G, LUGIL P, et al. The Bistable Ring PUF: A New Architecture for Strong Physical Unclonable Functions [C]//IEEE. 2011 IEEE International Symposium on Hardware-oriented Security and Trust, June 5-6, 2011, San Diego, CA, USA. New Jersey: IEEE, 2011: 134-141. |
| [21] | PANDEY S, DEYATI S, SINGH A, et al. Noise-resilient SRAM Physically Unclonable Function Design for Security [C]//IEEE. IEEE 25th Asian Test Symposium(ATS), Noveber 21-24, 2016, Hiroshima, Japan. New Jersey: IEEE, 2016: 55-60. |
| [22] |
CHUANG K H, BURY E, DEGRAEVE R, et al. A Physically Unclonable Function Using Soft Oxide Breakdown Featuring 0% Native BER and 51.8 fJ/bit in 40-nm CMOS[J]. IEEE Journal of Solid-state Circuits, 2019, 54(10):2765-2776.
doi: 10.1109/JSSC.4 URL |
| [23] |
LU Xuyang, HONG Lingyu, SENGUPTA K. CMOS Optical PUFs Using Noise-immune Process-sensitive Photonic Crystals Incorporating Passive Variations for Robustness[J]. IEEE Journal of Solid-state Circuits, 2018, 53(9):2709-2721.
doi: 10.1109/JSSC.4 URL |
| [24] |
WANG Weiche, YONA Y, DIGGAVI S N, et al. Design and Analysis of Stability-guaranteed PUFs[J]. IEEE Transactions on Information Forensics and Security, 2017, 13(4):978-992.
doi: 10.1109/TIFS.2017.2774761 URL |
| [25] | BRON M, HANKERSON D, LOPEZ J, et al. Software Implementation of the NIST Elliptic Curves over Prime Fields [C]//Springer. 2001 Cryptographers’ Track at the RSA Conference, April 8-12, 2001, San Francisco, CA, USA. Heidelberg: Springer, 2001: 250-265. |
| [26] |
JOHNSON D, MENEZES A, VANSTONE S. The Elliptic Curve Digital Signature Algorithm(ECDSA)[J]. International Journal of Information Security, 2001, 1(1):36-63.
doi: 10.1007/s102070100002 URL |
| [1] | FENG Yiting, MA Zhaofeng, XU Danheng, DUAN Pengfei. Evaluation Method for Cross-Chain Security Strength Access [J]. Netinfo Security, 2023, 23(1): 84-92. |
| [2] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| [3] | HU Yi, SHE Kun. Blockchain and Smart Contract Based Dual-Chain Internet of Vehicles System [J]. Netinfo Security, 2022, 22(8): 26-35. |
| [4] | HUANG Baohua, ZHAO Weihong, PENG Li, XIE Tongyi. Efficient Blockchain PKI Model Based on MPT Index [J]. Netinfo Security, 2022, 22(8): 72-80. |
| [5] | KELEKET GOMA Christy Junior Yannick, YI Wenzhe, WANG Juan. A Lightweight Trusted Execution Environment Construction Method for Fabric Chaincode Based on SGX [J]. Netinfo Security, 2022, 22(7): 73-83. |
| [6] | YU Kechen, GUO Li, YIN Hongwei, YAN Xuesong. The High-Value Data Sharing Model Based on Blockchain and Game Theory for Data Centers [J]. Netinfo Security, 2022, 22(6): 73-85. |
| [7] | FENG Jingyu, ZHANG Qi, HUANG Wenhua, HAN Gang. A Cyber Threat Intelligence Sharing Scheme Based on Cross-Chain Interaction [J]. Netinfo Security, 2022, 22(5): 21-29. |
| [8] | LIU Jiawei, MA Zhaofeng, WANG Shushuang, LUO Shoushan. Research on the Restricted Sharing Technology of Private Credit Data Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 54-63. |
| [9] | CUI Haoyu, MA Limin, WANG Jiahui, ZHANG Wei. Research on the Security Model of Multi-Authority for Attribute Encryption Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 84-93. |
| [10] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 22(3): 78-84. |
| [11] | WANG Jian, ZHANG Yunjia, LIU Jiqiang, CHEN Zhihao. Blockchain-based Mechanism for Judicial Data Management and Electronic Evidence Storage [J]. Netinfo Security, 2022, 22(2): 21-31. |
| [12] | LIU Feng, YANG Chengyi, YU Xincheng, QI Jiayin. Spectral Graph Convolutional Neural Network for Decentralized Dual Differential Privacy [J]. Netinfo Security, 2022, 22(2): 39-46. |
| [13] | HOU Yutong, MA Zhaofeng, LUO Shoushan. Research and Implementation of Data Security Sharing and Controlled Distribution Technology Based on Blockchain [J]. Netinfo Security, 2022, 22(2): 55-63. |
| [14] | WANG Yong, CHEN Lijie, ZHONG Meiling. Progress in Blockchain Solutions Based on Zero-Knowledge Proof [J]. Netinfo Security, 2022, 22(12): 47-56. |
| [15] | WANG Sidie, MA Zhaofeng, LUO Shoushan, XU Danheng. Data Privacy-Preserving Scheme on Blockchain for Heterogeneous Multi-Chain [J]. Netinfo Security, 2022, 22(12): 67-75. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||