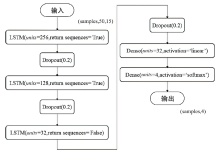
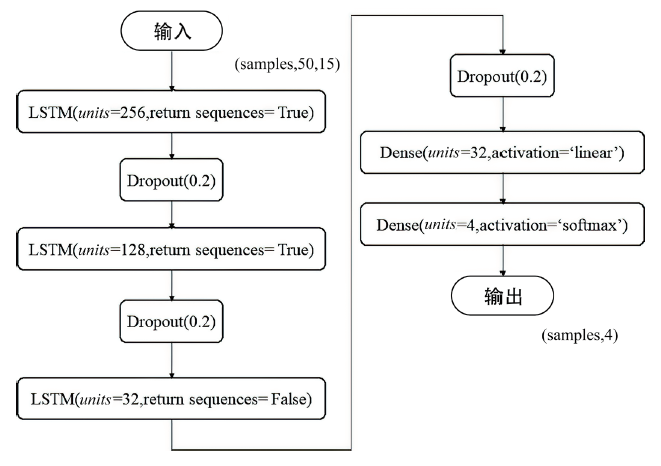
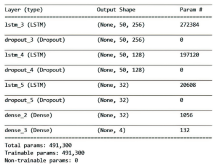
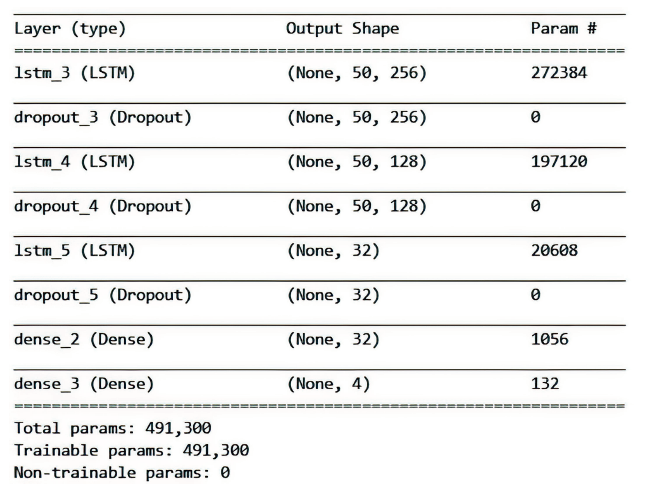
Netinfo Security ›› 2022, Vol. 22 ›› Issue (12): 57-66.doi: 10.3969/j.issn.1671-1122.2022.12.007
Previous Articles Next Articles
Research on LSTM-Based CAN Intrusion Detection Model
YIN Ying1,2( ), ZHOU Zhihong1,2, YAO Lihong3
), ZHOU Zhihong1,2, YAO Lihong3
- 1. Institute of Cyber Science and Technology, Shanghai Jiao Tong University, Shanghai 200240, China
2. Shanghai Key Laboratory of Integrated Administration Technologies for Information Security, Shanghai 200240, China
3. School of Cyber Science and Engineering, Shanghai Jiao Tong University, Shanghai 200240, China
-
Received:2022-10-09Online:2022-12-10Published:2022-12-30 -
Contact:YIN Ying E-mail:yyin@sjtu.edu.cn
CLC Number:
Cite this article
YIN Ying, ZHOU Zhihong, YAO Lihong. Research on LSTM-Based CAN Intrusion Detection Model[J]. Netinfo Security, 2022, 22(12): 57-66.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.12.007
| [1] | Upstream. Upstream’s 2022 Global Automotive Cybersecurity Report[EB/OL]. (2022-01-26) [2022-09-08]. https://upstream.auto/2022report/. |
| [2] | XIA Ziyan, ZHOU Zhitong, LI Xiang, et al. Feasibility Study on Automobile Electronic Control System of ECU Intrusion and Virus[J]. Netinfo Security, 2014, 14(9): 193-195. |
| 夏子焱, 周之童, 李响, 等. 汽车ECU电控系统入侵与汽车病毒编写的可行性研究[J]. 信息网络安全, 2014, 14(9):193-195. | |
| [3] | FENG Cong. Research on the Governance and Law Enforcement of Network Security of Intelligent Connected Vehicles[J]. Netinfo Security, 2020(S1):44-47. |
| 冯聪. 智能网联汽车网络安全问题的治理与执法探索[J]. 信息网络安全, 2020(S1):44-47. | |
| [4] | Security Guest. 360 Network Attack and Defense Lab Has Revealed a Second High Risk Vulnerability in a Tesla Vehicle-The Ability to Open the Vehicle Without a Key[EB/OL]. (2015-01-21) [2022-09-08]. https://anyun.org/a/yejiezixun/2015/0129/4460.html. |
| 安全客. 360网络攻防实验室公布第二例特斯拉高危漏洞—无需钥匙开启车辆[EB/OL].(2015-01-21) [2022-09-08]. https://anyun.org/a/yejiezixun/2015/0129/4460.html. | |
| [5] | Tencent Technology. Tencent Cohen Lab Successfully Invaded Tesla Remotely for the First Time in the World[EB/OL]. (2016-09-20) [2022-09-08]. https://news.mydrivers.com/1/500/500287.htm. |
| 腾讯科技. 腾讯科恩实验室成功远程入侵特斯拉为全球首次[EB/OL].(2016-09-20) [2022-09-08]. https://news.mydrivers.com/1/500/500287.htm. | |
| [6] | LI Yilin, YAN Zheng, XIE Haomeng. Survey of Privacy Preservation in VANET[J]. Netinfo Security, 2019, 19(4): 63-72. |
| 李怡霖, 闫峥, 谢皓萌. 车载自组织网络的隐私保护综述[J]. 信息网络安全, 2019, 19(4):63-72. | |
| [7] |
CHOI W, JO H J, WOO S, et al. Identifying ECUs Using Inimitable Characteristics of Signals in Controller Area Networks[J]. IEEE Transactions on Vehicular Technology, 2018, 67(6): 4757-4770.
doi: 10.1109/TVT.2018.2810232 URL |
| [8] | NILSSON D K, LARSON U E, JONSSON E. Efficient in-Vehicle Delayed Data Authentication Based on Compound Message Authentication Codes[C]// IEEE. 2008 IEEE 68th Vehicular Technology Conference. New York: IEEE, 2008: 1-5. |
| [9] | HAZEM A, FAHMY H A. LCAP-a Lightweight Can Authentication Protocol for Securing in-Vehicle Networks[EB/OL]. (2012-06-20) [2022-09-08]. http://www.eece.cu.edu.eg/-hfahmy/publish/escar2012.pdf. |
| [10] | GMIDEN M, GMIDEN M H, TRABELSI H. An Intrusion Detection Method for Securing in-Vehicle CAN Bus[C]// IEEE. 2016 17th International Conference on Sciences and Techniques of Automatic Control and Computer Engineering (STA). New York: IEEE, 2016: 176-180. |
| [11] | MARCHETTI M, STABILI D. Anomaly Detection of CAN Bus Messages through Analysis of ID Sequences[C]// IEEE. 2017 IEEE Intelligent Vehicles Symposium (IV). New York: IEEE, 2017: 1577-1583. |
| [12] | MÜTER M, ASAJ N. Entropy-Based Anomaly Detection for in-Vehicle Networks[C]// IEEE. 2011 IEEE Intelligent Vehicles Symposium (IV). New York: IEEE, 2011: 1110-1115. |
| [13] | STABILI D, MARCHETTI M, COLAJANNI M. Detecting Attacks to Internal Vehicle Networks through Hamming Distance[C]// IEEE. 2017 AEIT International Annual Conference. New York: IEEE, 2017: 1-6. |
| [14] | CHO K T, SHIN K G. Fingerprinting Electronic Control Units for Vehicle Intrusion Detection[C]// USENIX. 25th USENIX Security Symposium (USENIX Security 16). Berkeley:USENIX, 2016: 911-927. |
| [15] | SEO E, SONG H M, KIM H K. Gids: GAN Based Intrusion Detection System for in-Vehicle Network[C]// IEEE. 2018 16th Annual Conference on Privacy, Security and Trust (PST). New York: IEEE, 2018: 1-6. |
| [16] |
ZHU Konglin, CHEN Zhicheng, PENG Yuyang, et al. Mobile Edge Assisted Literal Multi-Dimensional Anomaly Detection of in-Vehicle Network Using LSTM[J]. IEEE Transactions on Vehicular Technology, 2019, 68(5): 4275-4284.
doi: 10.1109/TVT.2019.2907269 URL |
| [17] | GAZDAG A, NEUBRANDT D, BUTTYÁN L, et al. Detection of Injection Attacks in Compressed CAN Traffic Logs[C]// Springer. 2018 Security and Safety Interplay of Intelligent Software Systems. New York: Springer, 2018: 111-124. |
| [18] | KANG M J, KANG J W. Intrusion Detection System Using Deep Neural Network for in-Vehicle Network Security[EB/OL]. (2016-06-07) [2022-09-08]. https://pubmed.ncbi.nlm.nih.gov/27271802/. |
| [19] | MO Xiuliang, CHEN Pengyuan, WANG Jianing, et al. Anomaly Detection of Vehicle CAN Network Based on Message Content[C]// Springer. International Conference on Security and Privacy in New Computing Environments. New York: Springer, 2019: 96-104. |
| [20] | SONG H M, WOO J, KIM H K. In-Vehicle Network Intrusion Detection Using Deep Convolutional Neural Network[EB/OL]. (2019-10-03) [2022-09-08]. https://www.sciencedirect.com/science/article/abs/pii/S2214209619302451. |
| [21] |
HOCHREITER S, SCHMIDHUBER J. Long Short-Term Memory[J]. Neural Computation, 1997, 9(8): 1735-1780.
pmid: 9377276 |
| [22] | MALHOTRA P, VIG L, SHROFF G, et al. Long Short Term Memory Networks for Anomaly Detection in Time Series[EB/OL]. (2015-04-22) [2022-09-08]. https://www.researchgate.net/publication/304782562_Long_Short_Term_Memory_Networks_for_Anomaly_Detection_in_Time_Series. |
| [23] | MARKOVITZ M, WOOL A. Field Classification, Modeling and Anomaly Detection in Unknown CAN Bus Networks[J]. Vehicular Communications, 2017(9): 43-52. |
| [24] | LIU Xin, WANG Jiayin, YANG Haorui, et al. An Internet of Vehicles Authentication Protocol Based on Blockchain and SecGear Framework[J]. Netinfo Security, 2022, 22(1): 27-36. |
| 刘忻, 王家寅, 杨浩睿, 等. 一种基于区块链和SecGear框架的车联网认证协议[J]. 信息网络安全, 2022, 22(1):27-36. | |
| [25] | HCRL. Car Hacking for Intrusion Detection[EB/OL]. (2018-08-01) [2022-09-08]. https://ocslab.hksecurity.net/Dataset/CAN-intrusion-dataset. |
| [1] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| [2] | ZHANG Xinglan, FU Juanjuan. Auxiliary Entropy Reduction Based Intrusion Detection Model for Ordinary Differential Equations [J]. Netinfo Security, 2022, 22(6): 1-8. |
| [3] | WANG Haoyang, LI Wei, PENG Siwei, QIN Yuanqing. An Intrusion Detection Method of Train Control System Based on Ensemble Learning [J]. Netinfo Security, 2022, 22(5): 46-53. |
| [4] | ZHANG Guanghua, YAN Fengru, ZHANG Dongwen, LIU Xuefeng. Insider Threat Detection Model Based on LSTM-Attention [J]. Netinfo Security, 2022, 22(2): 1-10. |
| [5] | SHEN Zhuowei, FAN Linli, HUA Tong, WANG Kexiang. Role Mining Scheme with Abnormal Permission Configuration [J]. Netinfo Security, 2022, 22(11): 7-16. |
| [6] | BAI Hongpeng, DENG Dongxu, XU Guangquan, ZHOU Dexiang. Research on Intrusion Detection Mechanism Based on Federated Learning [J]. Netinfo Security, 2022, 22(1): 46-54. |
| [7] | HE Hongyan, HUANG Guoyan, ZHANG Bing, JIA Damiao. Intrusion Detection Model Based on Extra Trees-recursive Feature Elimination and LightGBM [J]. Netinfo Security, 2022, 22(1): 64-71. |
| [8] | LIU Shuo, ZHANG Xinglan. Intrusion Detection System Based on Dual Attention [J]. Netinfo Security, 2022, 22(1): 80-86. |
| [9] | LI Qun, DONG Jiahan, GUAN Zhitao, WANG Chao. A Clustering and Classification-based Malicious Attack Detection Method for Internet of Things [J]. Netinfo Security, 2021, 21(8): 82-90. |
| [10] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| [11] | DU Ye, WANG Zimeng, LI Meihong. Industrial Control Intrusion Detection Method Based on Optimized Kernel Extreme Learning Machine [J]. Netinfo Security, 2021, 21(2): 1-9. |
| [12] | WANG Huazhong, CHENG Qi. Research on Intrusion Detection of Industrial Control System Based on Improved Whale Algorithm [J]. Netinfo Security, 2021, 21(2): 53-60. |
| [13] | SHEN Yeming, LI Beibei, LIU Xiaojie, OUYANG Yuankai. Research on Active Learning-based Intrusion Detection Approach for Industrial Internet [J]. Netinfo Security, 2021, 21(1): 80-87. |
| [14] | LI Qiao, LONG Chun, WEI Jinxia, ZHAO Jing. A Hybrid Model of Intrusion Detection Based on LMDR and CNN [J]. Netinfo Security, 2020, 20(9): 117-121. |
| [15] | XU Guotian. Research on K-Nearest Neighbor High Speed Matching Algorithm in Network Intrusion Detection [J]. Netinfo Security, 2020, 20(8): 71-80. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||