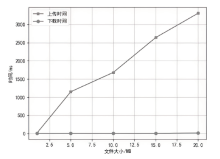
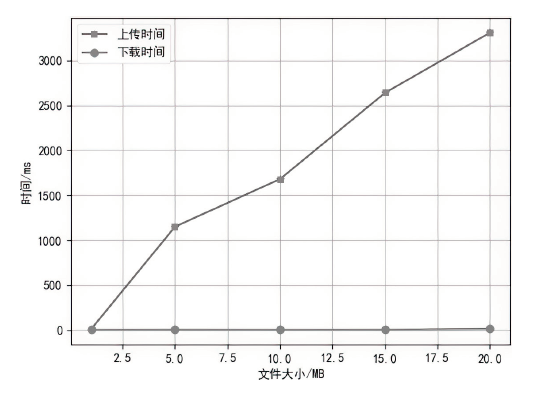
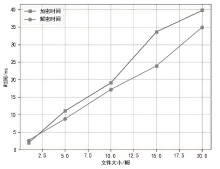
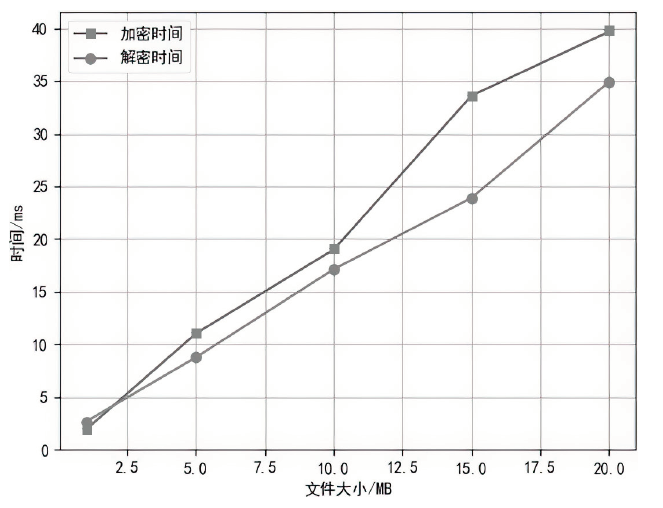
Netinfo Security ›› 2022, Vol. 22 ›› Issue (12): 67-75.doi: 10.3969/j.issn.1671-1122.2022.12.008
Previous Articles Next Articles
Data Privacy-Preserving Scheme on Blockchain for Heterogeneous Multi-Chain
WANG Sidie1, MA Zhaofeng1( ), LUO Shoushan1, XU Danheng2
), LUO Shoushan1, XU Danheng2
- 1. The School of Cyberspace Security, Beijing University of Posts and Telecommunications, Beijing 100876, China
2. Hangzhou Ancun Network Technology Co., Ltd., Hangzhou 310000, China
-
Received:2022-09-08Online:2022-12-10Published:2022-12-30 -
Contact:MA Zhaofeng E-mail:mzf@bupt.edu.cn
CLC Number:
Cite this article
WANG Sidie, MA Zhaofeng, LUO Shoushan, XU Danheng. Data Privacy-Preserving Scheme on Blockchain for Heterogeneous Multi-Chain[J]. Netinfo Security, 2022, 22(12): 67-75.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2022.12.008
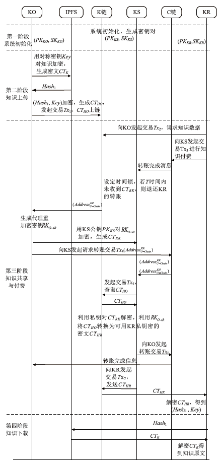
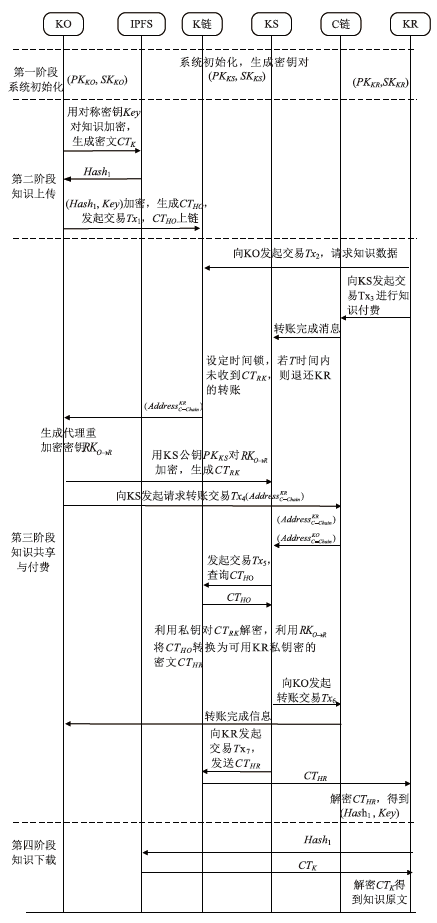
| 符号 | 含义 |
|---|---|
| 对称密钥 | |
| KO的公私钥对 | |
| KR的公私钥对 | |
| KS的公私钥对 | |
| 对称加密算法 | |
| 对称解密算法 | |
| 公钥加密算法 | |
| 解密算法 | |
| 知识原文 | |
| 对知识原文进行对称加密后的密文 | |
| 使用KO公钥对 | |
| 代理重加密密钥 | |
| 使用KS公钥对 | |
| 可用KR私钥解密的密文 | |
| 初始化算法 | |
| 密钥生成算法 | |
| 重加密密钥生成 | |
| 重加密算法 | |
| KR在C链上的地址 | |
| KO在C链上的地址 | |
| KS在C链上的地址 | |
| KR在K链上的地址 | |
| KO在K链上的地址 | |
| KS在K链上的地址 | |
| 区块链交易 | |
| 区块链交易ID | |
| 区块链交易数据内容 | |
| 区块链交易时间戳 |
| [1] | iiMedia New Economic Industry Research Center. 2022-2023 China Knowledge Payment Industry Research and Consumer Behavior Analysis Report[R]. Guangzhou: iiMedia Research, IM43243, 2022. |
| 艾媒新经济产业研究中心. 2022-2023年中国知识付费行业研究及消费者行为分析报告[R]. 广州:艾媒咨询,IM43243, 2022. | |
| [2] | MA Zhaofeng. Blockchain Technology Development Guide[M]. Beijing: Tsinghua University Press, 2020. |
| 马兆丰. 区块链技术开发指南[M]. 北京: 清华大学出版社, 2020. | |
| [3] | NAKAMOTO S. Bitcoin: A Peer-to-Peer Electronic Cash System[EB/OL]. (2008-10-31) [2022-08-11]. https://bitcoin.org/bitcoin.pdf. |
| [4] |
MA Zhaofeng, JIANG Ming, GAO Hongmin, et al. Blockchain for Digital Rights Management[J]. Future Generation Computer Systems, 2018, 89: 746-764.
doi: 10.1016/j.future.2018.07.029 URL |
| [5] | ZHANG Ao, BAI Xiaoying. Summary of Research and Practice of Blockchain Privacy Protection[J]. Journal of Software, 2020, 31(5): 1406-1434. |
| 张奥, 白晓颖. 区块链隐私保护研究与实践综述[J]. 软件学报, 2020, 31(5):1406-1434. | |
| [6] | ZHAI Sheping, TONG Tong, BAI Xifang. Blockchain-Based Attribute Proxy Re-Encryption Data Sharing Scheme[EB/OL]. (2022-07-20) [2022-07-30]. https://kns.cnki.net/kcms/detail/detail.aspx?dbcode=CAPJ&dbname=CAPJLAST&filename=JSGG20220718008&uniplatform=NZKPT&v=ZhiUyUsnOHCXWbRHbSs-i8HmSbiwkIzqHUAONULUsvormF6Uk5li-idNDjCQyAle. |
| 翟社平, 童彤, 白喜芳. 基于区块链的属性代理重加密数据共享方案[EB/OL]. (2022-07-20) [2022-07-30]. https://kns.cnki.net/kcms/detail/detail.aspx?dbcode=CAPJ&dbname= CAPJLAST&filename=JSGG20220718008&uniplatform=NZKPT&v=ZhiUyUsnOHCXWbRHbSs-i8HmSbiwkIzqHUAONULUsvormF6Uk5li-idNDjCQyAle. | |
| [7] | LIU Shang, GUO Yinzhang. Multi-Authority Based CP-ABE Proxy Re-Encryption Scheme for Cloud Computing[J]. Chinese Journal of Network and Information Security, 2022, 8(3): 176-188. |
| [8] |
POURNAGHI S M, BAYAT M, FARJAMI Y. MedSBA: A Novel and Secure Scheme to Share Medical Data Based on Blockchain Technology and Attribute-Based Encryption[J]. Journal of Ambient Intelligence and Humanized Computing, 2020, 11(11): 4613-4641.
doi: 10.1007/s12652-020-01710-y URL |
| [9] | SHAMSHAD S, MAHMOOD K, KUMARI S, et al. A Secure Blockchain-Based E-Health Records Storage and Sharing Scheme[EB/OL]. [2022-07-11]. https://doi.org/10.1016/j.jisa.2020.102590. |
| [10] |
ZHANG Xiaohong, SUN Lanlan. Attribute Proxy Re-Encryption for Ciphertext Storage Sharing Scheme on Blockchain[J]. Journal of System Simulation, 2020, 32(6): 1009-1020.
doi: 10.16182/j.issn1004731x.joss.18-0658 |
|
张小红, 孙岚岚. 属性代理重加密的区块链密文云存储共享研究[J]. 系统仿真学报, 2020, 32(6):1009-1020.
doi: 10.16182/j.issn1004731x.joss.18-0658 |
|
| [11] | SHAO Qifeng, JIN Cheqing, ZHANG Zhao, et al. Blockchain: Architecture and Research Progress[J]. Chinese Journal of Computers, 2018, 41(5): 969-988. |
| 邵奇峰, 金澈清, 张召, 等. 区块链技术:架构及进展[J]. 计算机学报, 2018, 41(5):969-988. | |
| [12] |
MA Zhaofeng, WANG Lingyun, ZHAO Weizhe. Blockchain-Driven Trusted Data Sharing with Privacy Protection in IoT Sensor Network[J]. IEEE Sensors Journal, 2021, 21(22): 25472-25479.
doi: 10.1109/JSEN.2020.3046752 URL |
| [13] | XIA Xiaolei, REN Yingzhi. Summary of Technical Application of Blockchain in the Field of Shared Data[J]. China Invention & Patent, 2020, 17(10): 35-41. |
| 夏晓蕾, 任盈之. 区块链在共享数据领域的技术应用综述[J]. 中国发明与专利, 2020, 17(10):35-41. | |
| [14] | LI Peng. Implementation of Data Sharing Platform Based on Blockchain Technology[J]. Network Security Technology and Application, 2022(6): 64-65. |
| 李鹏. 基于区块链技术的数据共享平台的实现[J]. 网络安全技术与应用, 2022(6):64-65. | |
| [15] | CHU Chunyan. Research on the Application of Blockchain Technology in Government Data Sharing[J]. Electronic Technology & Software Engineering, 2022(11): 250-253. |
| 褚春燕. 区块链技术在政府数据共享中的应用研究[J]. 电子技术与软件工程, 2022(11):250-253. | |
| [16] | PANG Zhen, YAO Yuan, ZHANG Xiaoqin. Secure Storage and Sharing of Medical Data Based on Blockchain[J]. Netinfo Security, 2021, 21(S1): 168-172. |
| 庞震, 姚远, 张晓琴. 基于区块链的医疗数据安全存储与共享方案[J]. 信息网络安全, 2021, 21(S1):168-172. | |
| [17] |
WANG Shangping, ZHANG Yinglong, ZHANG Yaling. A Blockchain-Based Framework for Data Sharing with Fine-Grained Access Control in Decentralized Storage System[J]. IEEE Access, 2018, 6: 38437-38450.
doi: 10.1109/ACCESS.2018.2851611 URL |
| [18] |
SHE Wei, HUO Lijuan, ZHAO Tian, et al. A Double Steganography Model Combining Blockchain and Interplanetary File System[J]. Peer-to-Peer Networking and Applications, 2021, 14(5): 3029-3042.
doi: 10.1007/s12083-021-01143-0 URL |
| [19] | BLAZE M, BLEUMER G, STRAUSS M. Divertible Protocols and Atomic Proxy Cryptography[C]// Springer. International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 1998: 127-144. |
| [20] |
ATENIESE G, FU K, GREEN M, et al. Improved Proxy Re-Encryption Schemes with Applications to Secure Distributed Storage[J]. ACM Transactions on Information and System Security, 2009, 9(1): 1-30.
doi: 10.1145/1127345.1127346 URL |
| [21] |
DU Ruizhong, ZHANG Tianhe, SHI Pengliang. Ciphertext Policy Hidden Access Control Scheme Based on Blockchain and Supporting Data Sharing[J]. Journal on Communications, 2022, 43(6): 168-178.
doi: 10.11959/j.issn.1000-436x.2022119 |
|
杜瑞忠, 张添赫, 石朋亮. 基于区块链且支持数据共享的密文策略隐藏访问控制方案[J]. 通信学报, 2022, 43(6):168-178.
doi: 10.11959/j.issn.1000-436x.2022119 |
|
| [22] | YANG Geng, GUO Rui, ZHUANG Chaoyuan, et al. Dynamically Updatable Attribute Based Proxy Re-Encryption Scheme in Cloud[J]. Journal of Cyber Security, 2022, 7(3): 43-55. |
| [23] | MA Zhaofeng, WANG Lingyun, WANG Xiaochang, et al. Blockchain-Enabled Decentralized Trust Management and Secure Usage Control of IoT Big Data[J]. IEEE Internet of Things Journal, 2020, 183: 4000-4003. |
| [24] | SHERLZP. GORECRYPT[EB/OL].(2020-04-05) [2022-08-05]. https://github.com/SherLzp/goRecrypt. |
| [1] | ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism [J]. Netinfo Security, 2022, 22(9): 46-54. |
| [2] | HU Yi, SHE Kun. Blockchain and Smart Contract Based Dual-Chain Internet of Vehicles System [J]. Netinfo Security, 2022, 22(8): 26-35. |
| [3] | HUANG Baohua, ZHAO Weihong, PENG Li, XIE Tongyi. Efficient Blockchain PKI Model Based on MPT Index [J]. Netinfo Security, 2022, 22(8): 72-80. |
| [4] | KELEKET GOMA Christy Junior Yannick, YI Wenzhe, WANG Juan. A Lightweight Trusted Execution Environment Construction Method for Fabric Chaincode Based on SGX [J]. Netinfo Security, 2022, 22(7): 73-83. |
| [5] | YU Kechen, GUO Li, YIN Hongwei, YAN Xuesong. The High-Value Data Sharing Model Based on Blockchain and Game Theory for Data Centers [J]. Netinfo Security, 2022, 22(6): 73-85. |
| [6] | FENG Jingyu, ZHANG Qi, HUANG Wenhua, HAN Gang. A Cyber Threat Intelligence Sharing Scheme Based on Cross-Chain Interaction [J]. Netinfo Security, 2022, 22(5): 21-29. |
| [7] | LIU Jiawei, MA Zhaofeng, WANG Shushuang, LUO Shoushan. Research on the Restricted Sharing Technology of Private Credit Data Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 54-63. |
| [8] | CUI Haoyu, MA Limin, WANG Jiahui, ZHANG Wei. Research on the Security Model of Multi-Authority for Attribute Encryption Based on Blockchain [J]. Netinfo Security, 2022, 22(5): 84-93. |
| [9] | SHI Runhua, WANG Shuhao, LI Kunchang. A Lightweight Cross-domain Mutual Authentication Scheme in V2G Networks [J]. Netinfo Security, 2022, 23(3): 20-28. |
| [10] | CHEN Binjie, WEI Fushan, GU Chunxiang. Blockchain Abnormal Transaction Detection with Privacy-preserving Based on KNN [J]. Netinfo Security, 2022, 23(3): 78-84. |
| [11] | WANG Jian, ZHANG Yunjia, LIU Jiqiang, CHEN Zhihao. Blockchain-based Mechanism for Judicial Data Management and Electronic Evidence Storage [J]. Netinfo Security, 2022, 22(2): 21-31. |
| [12] | LIU Feng, YANG Chengyi, YU Xincheng, QI Jiayin. Spectral Graph Convolutional Neural Network for Decentralized Dual Differential Privacy [J]. Netinfo Security, 2022, 22(2): 39-46. |
| [13] | HOU Yutong, MA Zhaofeng, LUO Shoushan. Research and Implementation of Data Security Sharing and Controlled Distribution Technology Based on Blockchain [J]. Netinfo Security, 2022, 22(2): 55-63. |
| [14] | WANG Yong, CHEN Lijie, ZHONG Meiling. Progress in Blockchain Solutions Based on Zero-Knowledge Proof [J]. Netinfo Security, 2022, 22(12): 47-56. |
| [15] | ZHANG Xuewang, YAO Yaning, LI Zhihong, ZHANG Hao. Data Sharing Scheme Based on Consortium Blockchain and Asmuth-Bloom Secret Sharing Algorithm [J]. Netinfo Security, 2022, 22(11): 17-23. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||