Netinfo Security ›› 2022, Vol. 22 ›› Issue (1): 27-36.doi: 10.3969/j.issn.1671-1122.2022.01.004
Previous Articles Next Articles
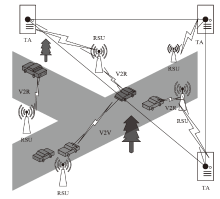
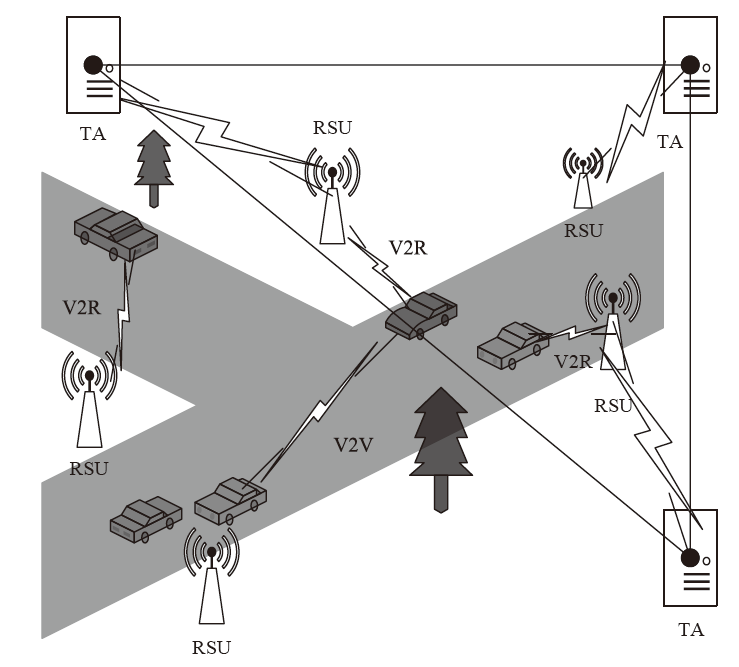
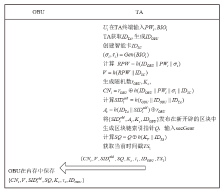
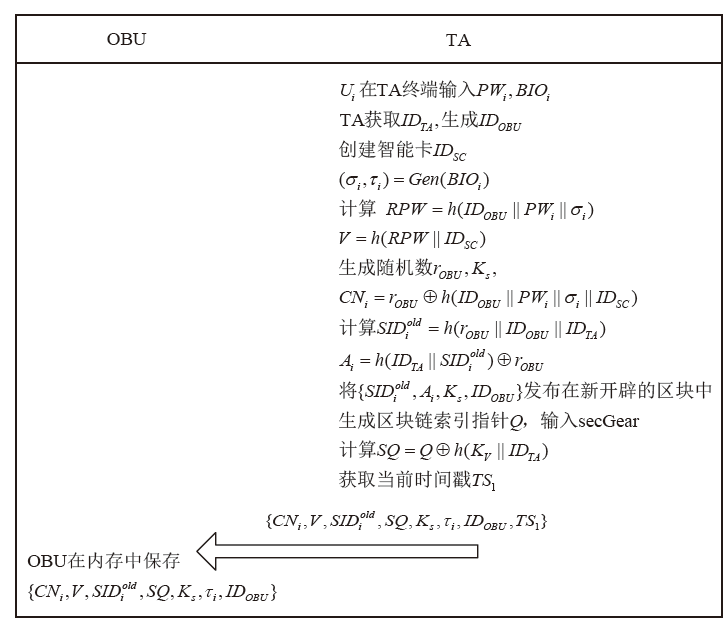
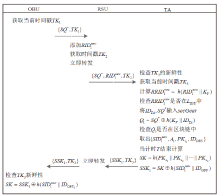
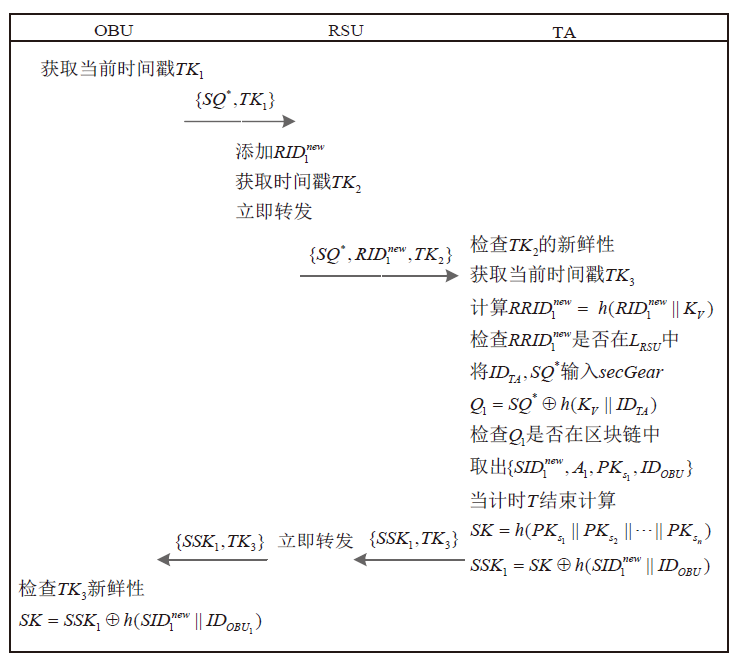
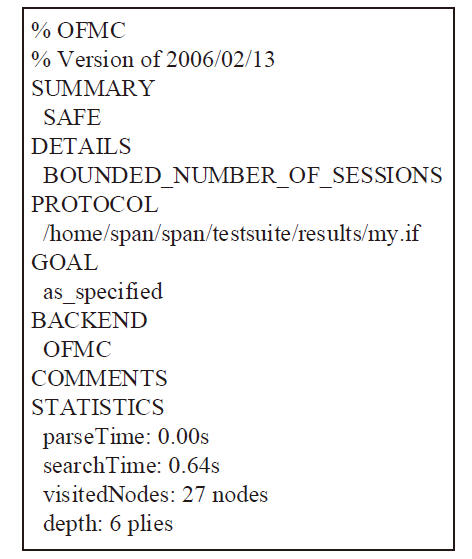
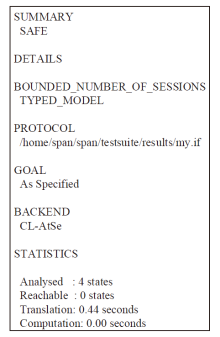
An Internet of Vehicles Authentication Protocol Based on Blockchain and secGear Framework
LIU Xin, WANG Jiayin, YANG Haorui, ZHANG Ruisheng( )
)
- School of Information Science & Engineering, Lanzhou University, Lanzhou 730000, China
-
Received:2021-07-26Online:2022-01-10Published:2022-02-16 -
Contact:ZHANG Ruisheng E-mail:zhangrs@lzu.edu.cn
CLC Number:
Cite this article
LIU Xin, WANG Jiayin, YANG Haorui, ZHANG Ruisheng. An Internet of Vehicles Authentication Protocol Based on Blockchain and secGear Framework[J]. Netinfo Security, 2022, 22(1): 27-36.
share this article
| [1] | TIAN Ye. Our Country will Establish a Vehicle Intelligent Management Standard System in Phases[J]. Industrial Economy Review, 2020, 7(3):10-11. |
| 田野. 我国将分阶段建立车辆智能管理标准体系[J]. 工业经济论坛, 2020, 7(3):10-11. | |
| [2] |
KUMARI S, KARUPPIAH M, LI Xiong, et al. An Enhanced and Secure Trust-extended Authentication Mechanism for Vehicular Ad-hoc Networks[J]. Security and Communication Networks, 2016, 9(17):4255-4271.
doi: 10.1002/sec.v9.17 URL |
| [3] | ALI I, GERVAIS M, AHENE E, et al. A Blockchain-based Certificateless Public Key Signature Scheme for Vehicle-to-Infrastructure Communication in VANETs[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S1383762119302103, 2021-04-11. |
| [4] | LIU Xin, ZHANG Ruisheng. A Robust Authentication Scheme with Continuously Updated Information for Vehicular Sensor Networks[EB/OL]. https://www.researchgate.net/publication/328891961_A_Robust_Authentication_Scheme_With_Continuously_Updated_Information_for_Vehicular_Sensor_Networks, 2021-04-11. |
| [5] |
YU S J, LEE J Y, LEE K K, et al. Secure Authentication Protocol for Wireless Sensor Networks in Vehicular Communications[J]. Sensors, 2018, 18(10):3191-3204.
doi: 10.3390/s18103191 URL |
| [6] | SADRI M J, RAJABZADEH ASAAR M. A Lightweight Anonymous Two-factor Authentication Protocol for Wireless Sensor Networks in Internet of Vehicles[EB/OL]. https://onlinelibrary.wiley.com/doi/10.1002/dac.4511, 2020-07-09. |
| [7] |
VASUDEV H, DESHPANDE V, DAS D, et al. A Lightweight Mutual Authentication Protocol for V2V Communication in Internet of Vehicles[J]. IEEE Transactions on Vehicular Technology, 2020, 69(6):6709-6717.
doi: 10.1109/TVT.25 URL |
| [8] | LI Kang, LAU W F, AU M H, et al. Efficient Message Authentication with Revocation Transparency Using Blockchain for Vehicular Networks[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S0045790620305760, 2021-05-11. |
| [9] | BAGGA P, SUTRALA A K, DAS A K, et al. Blockchain-based Batch Authentication Protocol for Internet of Vehicles[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S1383762120301569, 2021-06-11. |
| [10] |
XU Zisang, LIANG Wei, LI K C, et al. A Blockchain-based Roadside Unit-assisted Authentication and Key Agreement Protocol for Internet of Vehicles[J]. Journal of Parallel and Distributed Computing, 2021, 149(6):29-39.
doi: 10.1016/j.jpdc.2020.11.003 URL |
| [11] |
KANG Jiawen, XIONG Zehui, NIYATO D, et al. Toward Secure Blockchain-enabled Internet of Vehicles: Optimizing Consensus Management Using Reputation and Contract Theory[J]. IEEE Transactions on Vehicular Technology, 2019, 68(3):2906-2920.
doi: 10.1109/TVT.2019.2894944 URL |
| [12] | LIU Feng, YANG Jie, LI Zhibin, et al. A Secure Multi-party Computation Protocol for Universal Data Privacy Protection Based on Blockchain[J]. Journal of Computer Research and Development, 2021, 58(2):281-290. |
| 刘峰, 杨杰, 李志斌, 等. 一种基于区块链的泛用型数据隐私保护的安全多方计算协议[J]. 计算机研究与发展, 2021, 58(2):281-290. | |
| [13] | Huawei. secGear[EB/OL]. https://gitee.com/src-openeuler/secGear#introduction, 2021-05-11. |
| [14] | WANG Jinwen, JIANG Yong, LI Qi, et al. Survey of Research on SGX Technology Application[J]. Network New Media Technology, 2017, 6(5):3-9. |
| 王进文, 江勇, 李琦, 等. SGX技术应用研究综述[J]. 网络新媒体技术, 2017, 6(5):3-9. | |
| [15] | WANG Xiyou. Secure Isolation Based on ARM TrustZone Reaearch and Application[D]. Chengdu: University of Electronic Science and Technology of China, 2013. |
| 王熙友. ARM TrustZone安全隔离技术研究与应用[D]. 成都:电子科技大学, 2013. | |
| [16] | MA Li. Industry Data through the Crisis Development Prospects in Dingli-“2018 Transport Industry Development Statistical Bulletin” Published[J]. China Road Transport, 2019(5):14-16. |
| 马力. 行业数据透危机发展前景在定力—《2018年交通运输行业发展统计公报》公布[J]. 中国道路运输, 2019(5):14-16. | |
| [17] | SUKHWANI H, MARTÍNEZ J M, CHANG Xiaolin, et al. Performance Modeling of PBFT Consensus Process for Permissioned Blockchain Network(Hyperledger Fabric)[C]//IEEE. 36th IEEE Symposium on Reliable Distributed Systems (SRDS), September 26-29, 2017, Hong Kong, China. New Jersey: IEEE, 2017: 253-255. |
| [18] |
LIU Xin, ZHANG Ruisheng, ZHAO Mingqi. A Robust Authentication Scheme with Dynamic Password for Wireless Body Area Networks[J]. Computer Networks, 2019, 161(10):220-234.
doi: 10.1016/j.comnet.2019.07.003 URL |
| [19] | CUI Jie, XU Wenyu, HAN Yibo, et al. Secure Mutual Authentication with Privacy Preservation in Vehicular Ad Hoc Networks[EB/OL]. https://www.sciencedirect.com/science/article/abs/pii/S2214209619302475, 2021-04-11. |
| [20] |
YING Bidi, NAYAK A. Anonymous and Lightweight Authentication for Secure Vehicular Networks[J]. IEEE Transactions on Vehicular Technology, 2017, 66(12):10626-10636.
doi: 10.1109/TVT.2017.2744182 URL |
| [21] | ALAZZAWI M A, LU H, YASSIN A A, et al. Robust Conditional Privacy-preserving Authentication Based on Pseudonym Root with Cuckoo Filter in Vehicular Ad Hoc Networks[J]. KSII Transactions on Internet and Information Systems, 2019, 13(12):6121-6144. |
| [22] | LIU Xin, ZHANG Ruisheng, LIU Qidong. A Temporal Credential-based Mutual Authentication with Multiple-password Scheme for Wireless Sensor Networks[EB/OL]. https://journals.plos.org/plosone/article?id=10.1371/journal.pone.0170657, 2017-01-30. |
| [1] | WANG Jian, ZHANG Yunjia, LIU Jiqiang, CHEN Zhihao. Blockchain-based Mechanism for Judicial Data Management and Electronic Evidence Storage [J]. Netinfo Security, 2022, 22(2): 21-31. |
| [2] | LIU Feng, YANG Chengyi, YU Xincheng, QI Jiayin. Spectral Graph Convolutional Neural Network for Decentralized Dual Differential Privacy [J]. Netinfo Security, 2022, 22(2): 39-46. |
| [3] | HOU Yutong, MA Zhaofeng, LUO Shoushan. Research and Implementation of Data Security Sharing and Controlled Distribution Technology Based on Blockchain [J]. Netinfo Security, 2022, 22(2): 55-63. |
| [4] | FENG Jingyu, WANG Tao, YU Tingting, ZHANG Wenbo. A Secure Medical Data Sharing Scheme Based on Multi-clouds and Multi-chains Collaboration [J]. Netinfo Security, 2022, 22(1): 9-18. |
| [5] | WANG Yuedong, XIONG Yan, HUANG Wenchao, WU Jianshuang. A Formal Analysis Scheme for 5G Private Network Authentication Protocol [J]. Netinfo Security, 2021, 21(9): 1-7. |
| [6] | SUN Li. Research and Application of Information Protection Mechanism for Online Education Resource Alliance [J]. Netinfo Security, 2021, 21(9): 32-39. |
| [7] | CHEN Kaijie, XIONG Yan, HUANG Wenchao, WU Jianshuang. A Formal Analysis Method of PoS Consensus Protocol Based on Byzantine Fault Tolerance [J]. Netinfo Security, 2021, 21(8): 35-42. |
| [8] | LIU Xin, YANG Haorui, GUO Zhenbin, WANG Jiayin. An Authentication Protocol Achieving Online Registration and Privilege Separation for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(7): 1-9. |
| [9] | REN Tao, JIN Ruochen, LUO Yongmei. Network Intrusion Detection Algorithm Integrating Blockchain and Federated Learning [J]. Netinfo Security, 2021, 21(7): 27-34. |
| [10] | LIU Xin, GUO Zhenbin, SONG Yuchen. An Authentication Scheme Based on SGX for Industrial Internet of Things [J]. Netinfo Security, 2021, 21(6): 1-10. |
| [11] | WU Yi, ZHONG Sheng. Research on Raft Consensus Algorithm for Blockchain [J]. Netinfo Security, 2021, 21(6): 36-44. |
| [12] | LI Peng, ZHENG Tiantian, XU He, ZHU Feng. RFID Security Authentication Protocol Based on Blockchain Technology [J]. Netinfo Security, 2021, 21(5): 1-11. |
| [13] | ZHOU Yousheng, ZHONG Tianqi. Blockchain-based Fair Exchange Scheme [J]. Netinfo Security, 2021, 21(5): 19-30. |
| [14] | LIU Zi’ang, HUANG Yuanyuan, MA Jiali, ZHOU Rui. Design and Implementation of Monitoring Platform for Medical Data Abuse Based on Blockchain [J]. Netinfo Security, 2021, 21(5): 58-66. |
| [15] | LU Xiaofeng, FU Songbing. A Trusted Data Access Control Scheme Combining Attribute-based Encryption and Blockchain [J]. Netinfo Security, 2021, 21(3): 7-8. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||