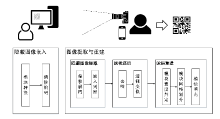
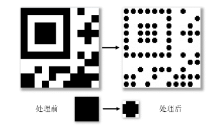
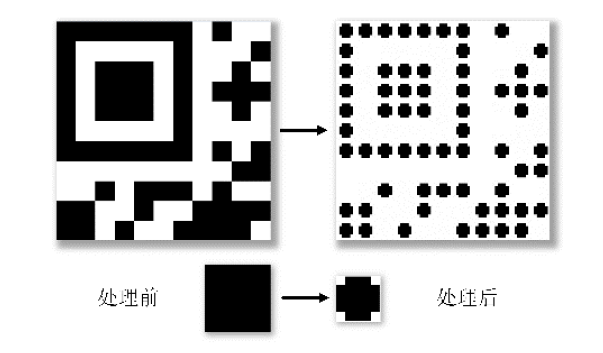
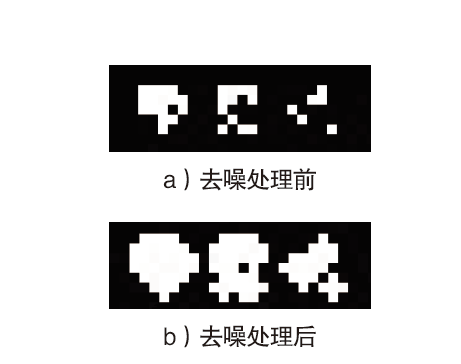
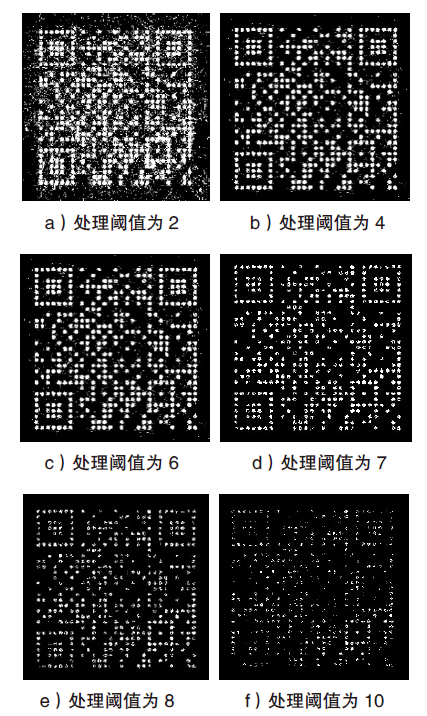
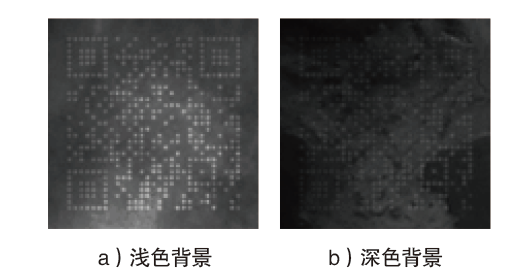
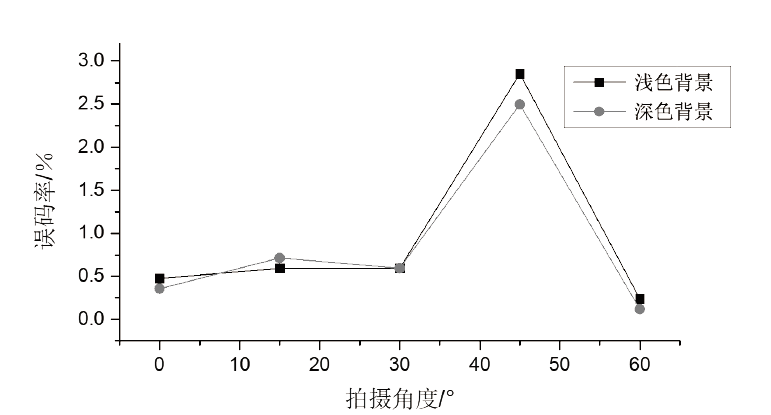
Netinfo Security ›› 2021, Vol. 21 ›› Issue (4): 31-38.doi: 10.3969/j.issn.1671-1122.2021.04.004
Previous Articles Next Articles
A Covert Channel Communication Method Based on Pixel Offset Encoding and Decoding Technique
SONG Yubo1,2( ), MA Wenhao1,2, HU Aiqun2,3,4, WANG Junbo2,3,4
), MA Wenhao1,2, HU Aiqun2,3,4, WANG Junbo2,3,4
- 1. School of Cyber Science and Engineering, Southeast University, Nanjing 211189, China
2. Network Communication and Security Purple Mountain Laboratory, Nanjing 211189, China
3. School of Information Science and Engineering, Southeast University, Nanjing 211189, China
4. National Mobile Communications Research Laboratory, Southeast University, Nanjing 211189, China
-
Received:2021-01-07Online:2021-04-10Published:2021-05-14 -
Contact:SONG Yubo E-mail:songyubo@seu.edu.cn
CLC Number:
Cite this article
SONG Yubo, MA Wenhao, HU Aiqun, WANG Junbo. A Covert Channel Communication Method Based on Pixel Offset Encoding and Decoding Technique[J]. Netinfo Security, 2021, 21(4): 31-38.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2021.04.004
| [1] | KUHN M G, ANDERSON R J. Soft Tempest: Hidden Data Transmission Using Electromagnetic Emanations[C]// Springer. 2nd International Workshop on Information Hiding, April 14-17, 1998, Portland, Oregon. Berlin: Springer, 1998: 124-142. |
| [2] | GURI M, KEDMA G, KACHLON A, et al. AirHopper: Bridging The Air-gap Between Isolated Networks and Mobile Phones Using Radio Frequencies[C]// IEEE. 2014 9th International Conference on Malicious and Unwanted Software: The Americas (MALWARE), October 28-30, 2014, Fajardo, PR, USA. New York: IEEE, 2014: 58-67. |
| [3] | GURI M, KACHLON A, HASSON O, et al. GSMem: Data Exfiltration from Air-gapped Computers over GSM Frequencies[C]// USENIX ASSOC. 24th USENIX Security Symposium, August 12-14, 2015, Washington, DC, USA. Berkeley: USENIX ASSOC, 2015: 849-864. |
| [4] | GURI M, MONITZ M, ELOVICI Y. USBee: Air-gap Covert-channel via Electromagnetic Emission from USB[C]// Endace. 2016 14th Annual Conference on Privacy, Security and Trust (PST), December 12-14, 2016, Auckland, New Zealand. New York: IEEE, 2016: 264-268. |
| [5] | LEE E, KIM H, YOON J W. Various Threat Models to Circumvent Air-gapped Systems for Preventing Network Attack[C]// WISA. International Workshop on Information Security Applications, August 20-22, 2015, Jeju Island, Korea. Switzerland: Springer, 2015: 187-199. |
| [6] | GURI M, SOLEWICZ Y, DAIDAKULOV A, et al. Fansmitter: Acoustic Data Exfiltration from (Speakerless) Air-gapped Computers[EB/OL]. https://www.sciencedirect.com/science/article/pii/S0167404820300080?via%3Dihub, April 2020/, 2020-09-03. |
| [7] | GURI M, SOLEWICZ Y, DAIDAKULOV A, et al. Acoustic Data Exfiltration from Speakerless Air-gapped Computers via Covert Hard-drive Noise[C]// Ctr Cyber & InformatSecur. 22nd European Symposium on Research in Computer Security, September 11-15, 2017, Oslo, Norway. Switzerland: Springer, 2017: 98-115. |
| [8] | GURI M, MONITZ M, MIRSKI Y, et al. Bitwhisper: Covert Signaling Channel Between Air-gapped Computers Using Thermal Manipulations[C]// IEEE. 2015 IEEE 28th Computer Security Foundations Symposium, July 13-17, 2015, Univ Verona, Italy. New York: IEEE, 2015: 276-289. |
| [9] | SEPETNITSKY V, GURI M, ELOVICI Y. Exfiltration of Information from Air-gapped Machines Using Monitor's LED Indicator[C]// IEEE. 2014 IEEE Joint Intelligence and Security Informatics Conference, September 24-26, 2014, Hague, Netherlands. New York: IEEE, 2014: 264-267. |
| [10] | GURI M, ZADOV B, ELOVICI Y. LED-it-GO: Leaking (a lot of) Data from Air-gapped Computers via the (Small) Hard Drive LED[C]// DIMVA. International Conference on Detection of Intrusions and Malware, and Vulnerability Assessment, July 6-7, 2017, Bonn, Germany. Switzerland: Springer, 2017: 161-184. |
| [11] | GURI M, ZADOV B, DAIDAKULOV A, et al. Xled: Covert Data Exfiltration from Air-gapped Networks via Switch and Router LEDs[C]// IEEE. 2018 16th Annual Conference on Privacy, Security and Trust (PST), August 28-30, 2018, Belfast, United Kingdom. New York: IEEE, 2018: 1-12. |
| [12] | GURI M, BYKHOVSKY D. Air-jumper: Covert Air-gap Exfiltration/Infiltration Via Security Cameras & Infrared (IR)[J]. Computers & Security, 2019,19(82):15-29. |
| [13] | JO K, GUPTA M, NAYAR S K. DisCo: Display-camera Communication Using Rolling Shutter Sensors[J]. ACM Transactions on Graphics (TOG), 2016,35(5):1-13. |
| [14] | GURI M, HASSON O, KEDMA G, et al. An Optical Covert-channel to Leak Data Through an Air-gap[C]// Endace. 14th Annual International Conference on Privacy, Security and Trust (PST), December 12-14, 2016, Auckland, New Zealand. New York: IEEE, 2016: 642-649. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||