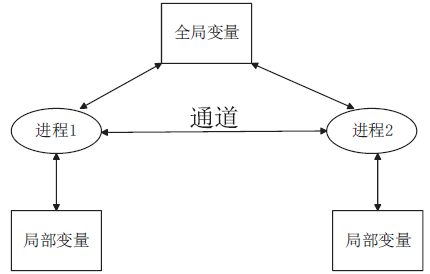
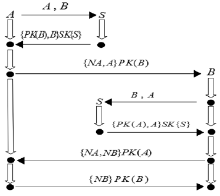
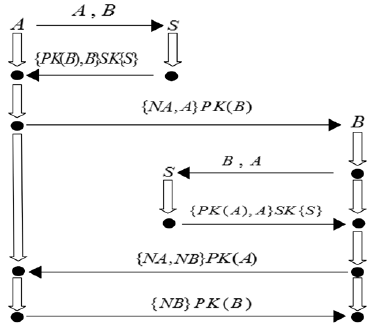
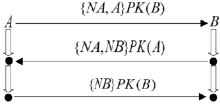
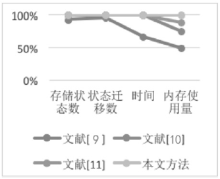
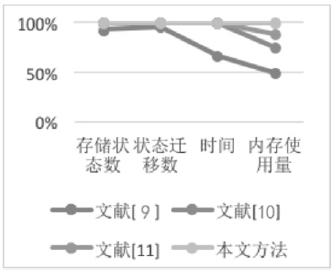
| [1] |
侯刚, 周宽久, 勇嘉伟,等. 模型检测中状态爆炸问题研究综述[J]. 计算机科学, 2013, 40(s1):77-86.
|
| [2] |
QING Sihan.Twenty Years Development of Security Protocols Research[J].Journal of Software, 2003,14(10) :1740-1752.
|
| [3] |
谢鸿波. 安全协议形式化分析方法的关键技术研究[D]. 成都:电子科技大学, 2011.
|
| [4] |
张玉婷,严承华. 一种基于双向认证协议的RFID标签认证技术研究[J].信息网络安全, 2016(1):64-69.
|
| [5] |
LOWE G.Breaking and Fixing the Needham-Schroeder Public-key Protocol Using FDR[C]// Springer. Proceeding TACAs '96 Proceedings of the Second International Workshop on Tools and Algorithms for Construction and Analysis of Systems, March 27-29, 1996, London, UK. London : Springer-Verlag, 1996:147-166.
|
| [6] |
高君丰, 张岳峰, 罗森林,等. 网络编码协议污点回溯逆向分析方法研究[J].信息网络安全, 2017(1):68-76.
|
| [7] |
POURPOUNEH M, RAMEZANIAN R.A Short Introduction to Two Approaches in Formal Verification of Security Protocols: Model Checking and Theorem Proving[J].The ISC International Journal of Information Security,2016, 8(1):3-24.
|
| [8] |
AVALLE M, PIRONTI A, SISTO R.Formal Verification of Security Protocol Implementations: a Survey[J]. Formal Aspects of Computing, 2014, 26(1):99-123.
|
| [9] |
王巧丽. SPIN模型检测的研究与应用[D]. 贵阳:贵州大学, 2006.
|
| [10] |
HENDA N B.Generic and Efficient Attacker Models in SPIN[M]. Washington: ACM , 2014 :77-86
|
| [11] |
SANTHIYA, PRIYADARSINI P S U. Formal Verification of Security Protocols Spin[J]. International Journal of Pharmacy & Technology, 2016, 8(4):19816-19823.
|
| [12] |
陈道喜, 张广泉, 陈冬火. NSPK协议的Spin模型检测[J]. 微电子学与计算机, 2008, 25(10):58-60.
|
| [13] |
KOMU B N, MZYECE M, DJOUANI K. SPIN-based Verification of Authentication Protocols in WiMAX Networks[EB/OL].,2017-10-20.
|
| [14] |
CLARKE E M, EMERSON E A, SIFAKIS J.Model Checking[J]. Lecture Notes in Computer Science, 1999, 164(2):305-349.
|
| [15] |
WANG Y, LIU Y.NSPK Protocol Security Model Checking System Builder[J]. International Journal of Security & Its Applications, 2015,9(7):307-316.
|
| [16] |
CHAUSSE N, XU H, DINGEL J,et al. Combining Model Checking and Discrete-event Supervisor Synthesis[EB/OL]. ,2017-10-30.
|
| [17] |
黄娜娜,万良,邓烜堃,等. 一种基于序列最小优化算法的跨站脚本漏洞检测技术[J].信息网络安全,2017(10):55-62.
|
| [18] |
RAMANUJAM R, SURESH S P.Decidability of Context-Explicit Security Protocols[J]. IOS Press, 2005 , 13(1): 135-165.
|
 ), Nana HUANG1,2, Kunpeng WANG1,2
), Nana HUANG1,2, Kunpeng WANG1,2