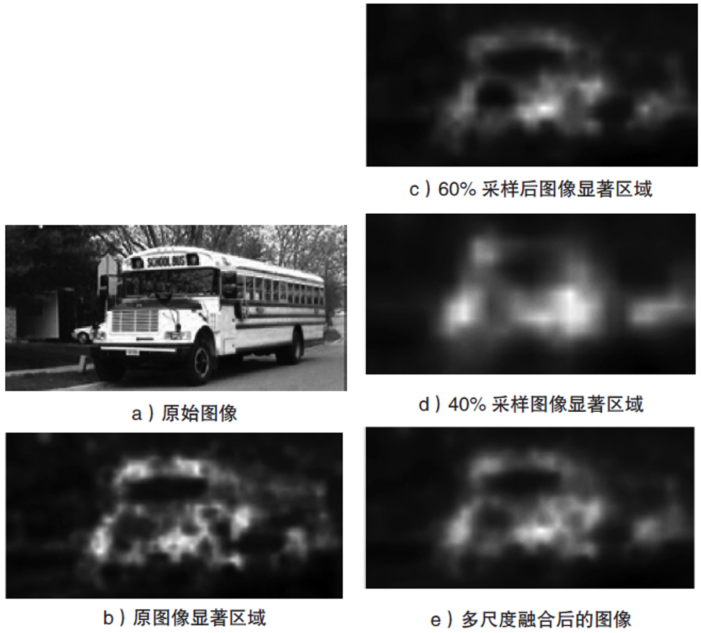
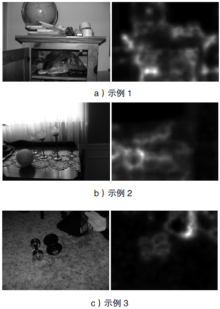
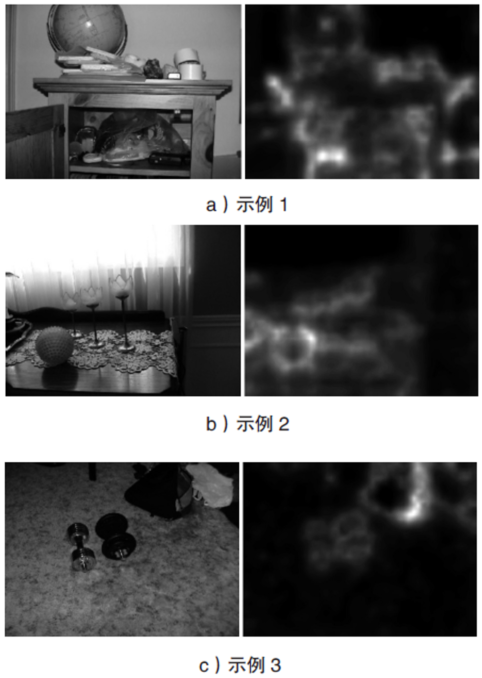
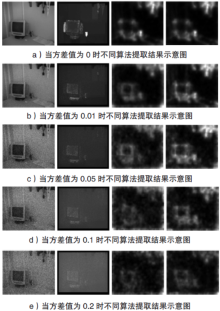
Netinfo Security ›› 2018, Vol. 18 ›› Issue (2): 54-60.doi: 10.3969/j.issn.1671-1122.2018.02.008
• Orginal Article • Previous Articles Next Articles
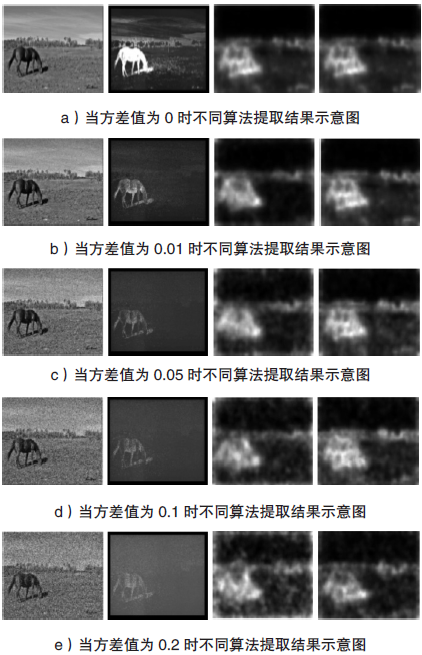
An Adaptive Adjusting Kernel Function-Based Extraction Method for Image Salient Area
Hongtao GAO1( ), Wei LU2, Yuwang YANG2
), Wei LU2, Yuwang YANG2
- 1. Department of Cyber Crime Investigation, Criminal Investigation Police University of China, Shenyang Liaoning 110035, China
2. School of Computer Science and Engineering, Nanjing University of Science and Technology, Nanjing Jiangsu 210094, China
-
Received:2017-12-31Online:2018-02-20Published:2020-05-11
CLC Number:
Cite this article
Hongtao GAO, Wei LU, Yuwang YANG. An Adaptive Adjusting Kernel Function-Based Extraction Method for Image Salient Area[J]. Netinfo Security, 2018, 18(2): 54-60.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2018.02.008
| [1] | BRUCE N D B,TSOTSOS J K.Saliency, Attention, and Visual Search: An Information Theoretic Approach[J].Journal of Vision, 2009, 9(3):1-24. |
| [2] | GAO D,MAHADEVAN V,VASONCELOS N.On the Plausibility of the Discriminant Center-surround Hypothesis for Visual Saliency[J].Journal of Vision, 2008, 8(7):1-18. |
| [3] | ITTI L,KOCH C,NIEBUR E.A Model of Saliency-based Visual Attention for Rapid Scene Analysis[J].IEEE Transactions on Pattern Analysis and Machine Intelligence, 1998, 20(11):1254-1259. |
| [4] | SEO H,MILANFAR P.Static and Space-time Visual Saliency Detection by Self-Resemblance[J].Journal of Vision, 2009, 9(12): 1-27. |
| [5] | 浮欣,卢玉华,邵子健 . 公共安全视频监控系统信息安全模拟实验平台技术研究[J].信息网络安全,2016(9):56-59. |
| [6] | RATHU E,KANNALA J,SALO M,et al. Segmenting Salient Objects from Images and Videos[EB/OL].,2017-11-15. |
| [7] | 李海洋, 何东健.一种自适应空间邻域的显著图获取方法研究[J].计算机应用研究,2013, 30(6):1882-1884. |
| [8] | 张鹏,王润生.基于视点转移和视区追踪的图像显著区域检测[J].软件学报,2004,15(6):891-898. |
| [9] | 王璐,陆霞,蔡自兴.基于局部显著区域的自然场景识别[J].中国图象图形学报,2008,13(8):1594-1600. |
| [10] | 刘亚春,王景中. 基于人脸检测的网络图像内容过滤技术研究[J].信息网络安全,2014(3):7-11. |
| [11] | TAKEDA H,FARIUS S,MILANFAR P.Kernel Regression for Image Processing and Reconstruction[J].IEEE Transactions on Image Processing A Publication of the IEEE Signal Processing Society,2007, 16(2):349-366. |
| [12] | SEO H J,MILANFAR P.Training-free, Generic Object Detection Using Locally Adaptive Regression Kernels[J]. IEEE Transactions on Pattern Analysis & Machine Intelligence, 2010, 32(9):1688-1704. |
| [13] | SEO H J,MILANFAR P.Detection of Human Actions From A Single Example[J].IEEE International Conference on Computer Vision, 2009,30(2):1965-1970. |
| [14] | SEO H J,MILANFAR P.Action Recognition from One Example[J].IEEE Transactions on Pattern Analysis & Machine Intelligence, 2011, 33(5):867-882 |
| [15] | 杨连群,温晋英,刘树发,等. 一种改进的图分割算法在用户行为异常检测中的应用[J].信息网络安全,2016(6):35-40. |
| [1] | WEN Weiping, ZHANG Shichen, WANG Han, SHI Lin. Linux Malicious Application Detection Scheme Based on Virtual Machine Introspection [J]. Netinfo Security, 2024, 24(5): 657-666. |
| [2] | LI Zhihua, CHEN Liang, LU Xulin, FANG Zhaohui, QIAN Junhao. Lightweight Detection Method for IoT Mirai Botnet [J]. Netinfo Security, 2024, 24(5): 667-681. |
| [3] | YANG Zhipeng, WANG Juan, MA Chenjun, KANG Yunfeng. Python Sandbox Escape Defense Mechanism Based on Third-Party Library Isolation [J]. Netinfo Security, 2024, 24(5): 682-693. |
| [4] | GU Guomin, CHEN Wenhao, HUANG Weida. A Covert Tunnel and Encrypted Malicious Traffic Detection Method Based on Multi-Model Fusion [J]. Netinfo Security, 2024, 24(5): 694-708. |
| [5] | SHEN Zhuowei, WANG Renbo, SUN Xianjun. A Hierarchical Lightweight Authentication Scheme Based on Merkle Tree and Hash Chain [J]. Netinfo Security, 2024, 24(5): 709-718. |
| [6] | TIAN Zhao, NIU Yajie, SHE Wei, LIU Wei. A Reputation Evaluation Method for Vehicle Nodes in V2X [J]. Netinfo Security, 2024, 24(5): 719-731. |
| [7] | SHI Runhua, DENG Jiapeng, YU Hui, KE Weiyang. Electronic Voting Scheme Based on Public Key Cryptography of Quantum Walks [J]. Netinfo Security, 2024, 24(5): 732-744. |
| [8] | GUO Jiansheng, GUAN Feiting, LI Zhihui. A Dynamic (t,n) Threshold Quantum Secret Sharing Scheme with Cheating Identification [J]. Netinfo Security, 2024, 24(5): 745-755. |
| [9] | LI Yuxin, HUANG Wenchao, WANG Jionghan, XIONG Yan. Analysis Method of Monero Payment Protocol Based on Tamarin [J]. Netinfo Security, 2024, 24(5): 756-766. |
| [10] | ZHANG Shuya, CHEN Liangguo, CHEN Xingshu. An Automatic Discovery Method for Heuristic Log Templates [J]. Netinfo Security, 2024, 24(5): 767-777. |
| [11] | ZHANG Changlin, TONG Xin, TONG Hui, YANG Ying. A Survey of Large Language Models in the Domain of Cybersecurity [J]. Netinfo Security, 2024, 24(5): 778-793. |
| [12] | WANG Wei, HU Yongtao, LIU Qingtao, WANG Kailun. Research on Softwaization Techniques for ERT Trusted Root Entity in Railway Operation Environment [J]. Netinfo Security, 2024, 24(5): 794-801. |
| [13] | GUO Zimeng, ZHU Guangjie, YANG Yijie, SI Qun. Research on Railway Network Security Performance Based on APT Characteristics [J]. Netinfo Security, 2024, 24(5): 802-811. |
| [14] | ZHANG Hao, XIE Dazhi, HU Yunsheng, YE Junwei. A Review of Network Anomaly Detection Based on Semi-Supervised Learning [J]. Netinfo Security, 2024, 24(4): 491-508. |
| [15] | WANG Jian, CHEN Lin, WANG Kailun, LIU Jiqiang. Application Layer DDoS Detection Method Based on Spatio-Temporal Graph Neural Network [J]. Netinfo Security, 2024, 24(4): 509-519. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||