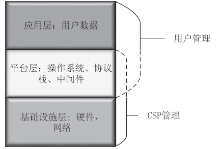
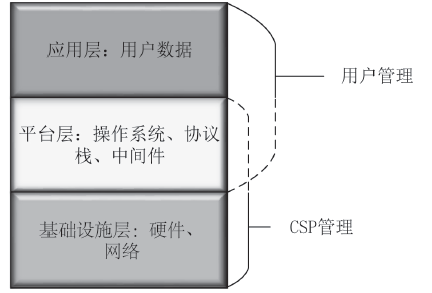
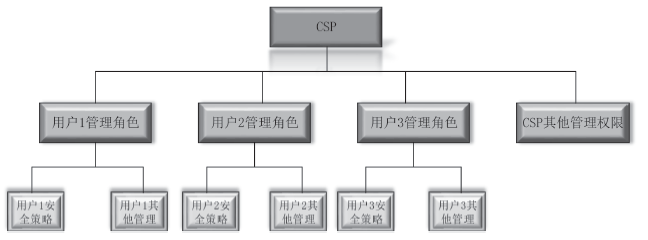
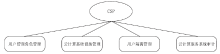
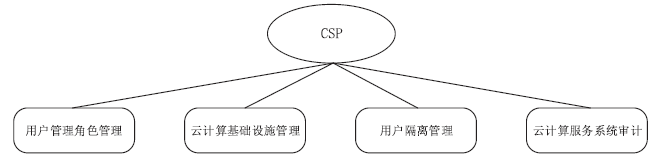
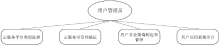
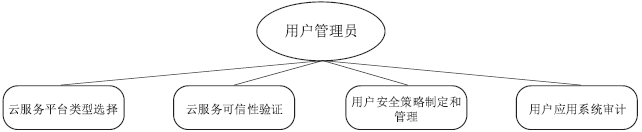
| [1] |
Jansen W, Grance T.Guidelines on security and privacy in public cloud computing[J]. NIST special publication, 2011, (800): 144.
|
| [2] |
Mell P, Grance T.The NIST definition of cloud computing[J]. 2011, (6): 20-23.
|
| [3] |
Brunette G, Mogull R.Security guidance for critical areas of focus in cloud computing v2. 1[J]. Cloud Security Alliance, 2009: 1-76.
|
| [4] |
Wüllenweber K, Weitzel T.An empirical exploration of how process standardization reduces outsourcing risks[C]//System Sciences, 2007. HICSS 2007. 40th Annual Hawaii International Conference on. IEEE, 2007: 240c-240c.
|
| [5] |
Ho C.Incomplete Thought—Cloudanatomy: Infrastructure, Metastructure & Infostructure[J]. 2009, (2): 59-64.
|
| [6] |
Peterson G.Don't Trust. And Verify: A Security Architecture Stack for the Cloud[J]. IEEE Security & Privacy, 2010 (5): 83-86.
|
| [7] |
Kaufman L M.Can a trusted environment provide security?[J]. Security & Privacy, IEEE, 2010, 8(1): 50-52.
|
| [8] |
Santos N, Gummadi K P, Rodrigues R.Towards trusted cloud computing[C]//Proceedings of the 2009 conference on Hot topics in cloud computing. 2009: 3.
|
| [9] |
Berger S, Cáceres R, Pendarakis D, et al.TVDc: managing security in the trusted virtual datacenter[J]. ACM SIGOPS Operating Systems Review, 2008, 42(1): 40-47.
|
| [10] |
Berger S, Cáceres R, Goldman K, et al. Security for the cloud infrastructure: Trusted virtual data center implementation[J]. IBM Journal of Research and Development, 2009, 53(4): 6: 1-6: 12.
|
| [11] |
Perez R, Sailer R, van Doorn L. vTPM: virtualizing the trusted platform module[C]//Proc. 15th Conf. on USENIX Security Symposium. 2006: 305-320.
|
| [12] |
Sailer R, Valdez E, Jaeger T, et al. sHype: Secure hypervisor approach to trusted virtualized systems[J]. Techn. Rep. RC23511, 2005.
|
| [13] |
F. John Krautheim and Dhananjay S. Phatak. Identifying Trusted Virtual Machines[C]//Xen Summit 2008, Boston, MA, June 24, 2008.
|
| [14] |
Chow R, Golle P, Jakobsson M, et al.Controlling data in the cloud: outsourcing computation without outsourcing control[C]//Proceedings of the 2009 ACM workshop on Cloud computing security. ACM, 2009: 85-90.
|
| [15] |
Cachin C, Keidar I, Shraer A.Trusting the cloud[J]. Acm Sigact News, 2009, 40(2): 81-86.
|
| [16] |
Wang C, Wang Q, Ren K, et al.Privacy-preserving public auditing for data storage security in cloud computing[C]//INFOCOM, 2010 Proceedings IEEE. Ieee, 2010: 1-9.
|
| [17] |
Khan K M, Malluhi Q.Establishing trust in cloud computing[J]. IT professional, 2010, 12(5): 20-27.
|
| [18] |
Sailer R, Zhang X, Jaeger T, et al.Design and Implementation of a TCG-based Integrity Measurement Architecture[C]//USENIX Security Symposium. 2004, 13: 16.
|
| [19] |
Seshadri A, Perrig A, Van Doorn L, et al.Swatt: Software-based attestation for embedded devices[C]//Security and Privacy, 2004. Proceedings. 2004 IEEE Symposium on. IEEE, 2004: 272-282.
|
| [20] |
Haldar V, Chandra D, Franz M.Semantic remote attestation: a virtual machine directed approach to trusted computing[C]//USENIX Virtual Machine Research and Technology Symposium. 2004, 2004.
|
| [21] |
Haldar V, Franz M.Symmetric behavior-based trust: A new paradigm for Internet computing[C]//Proceedings of the 2004 workshop on New security paradigms. ACM, 2004: 79-84.
|
| [22] |
Yoshihama S, Ebringer T, Nakamura M, et al.WS-Attestation: Efficient and fine-grained remote attestation on web services[C]//null. IEEE, 2005: 743-750.
|
| [23] |
Jaeger T, Sailer R, Shankar U.PRIMA: policy-reduced integrity measurement architecture[C]//Proceedings of the eleventh ACM symposium on Access control models and technologies. ACM, 2006: 19-28.
|
 ), HAN Zhen, CHENG Yang
), HAN Zhen, CHENG Yang