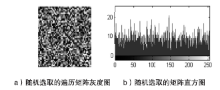
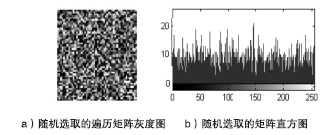
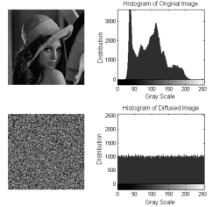
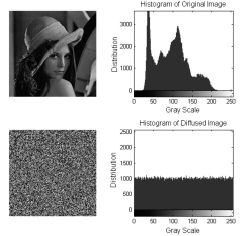
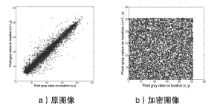
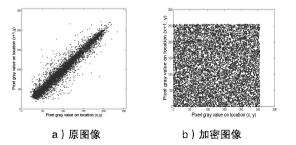
Netinfo Security ›› 2014, Vol. 14 ›› Issue (11): 18-25.doi: 10.3969/j.issn.1671-1122.2014.11.003
• Orginal Article • Previous Articles Next Articles
Authentication and Image Spatial Encryption Based on Ergodic Matrix and Hybrid Key System
ZHOU Xiao-yi, DUAN Yu-cong, FENG Wen-long, LI Yi-hong( )
)
- College of Information Science & Technology, Hainan University, Haikou Hainan 570228, China
-
Received:2014-09-23Online:2014-11-01Published:2020-05-18
CLC Number:
Cite this article
ZHOU Xiao-yi, DUAN Yu-cong, FENG Wen-long, LI Yi-hong. Authentication and Image Spatial Encryption Based on Ergodic Matrix and Hybrid Key System[J]. Netinfo Security, 2014, 14(11): 18-25.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2014.11.003
| [1] | Furht B, Kirovski D.Multimedia Security Handbook[M].Florida: CRC Press, 2005. |
| [2] | Acharya B, Panigrahy S.K., et al. Image Encryption Using Advanced Hill Cipher Algorithm[J]. International Journal of Recent Trends in Engineering, 2009,1(1): 663-667. |
| [3] | Öztürk I, Sogukpınar I.Analysis and Comparison of Image Encryption Algorithms[J]. World Academy of Science, Engineering and Technology,2005,(3): 26-30. |
| [4] | Diffie W, Hellman M E.New Directions in Cryptography[J]. IEEE Transactions on Information Theory,1976,22(6): 644-654. |
| [5] | Zhang L, Liao X, Wang X.An image encrypton approach based on chaotic maps[J]. Chaos, Solitions and Fractals,2005,(24): 759-765. |
| [6] | Fridrich J.Symmetric ciphers based on two-dimensional chaotic maps[J]. International Journal of Bifurcation and Chaos,1998, 8(6): 1259-1284. |
| [7] | Giesl J, Behal L, et al.Improving Chaos Image Encryption Speed[J]. International Journal of Future Communication and Networking ,2009,2(3): 23-36. |
| [8] | Miao Y, Chen G, et al.A novel fast image encryption scheme based on 3D chaotic baker maps[J]. International Journal of Bifurcation and Chaos,2004,14(10): 3613-3624. |
| [9] | Chen G, Mao Y, et al.A symmetric image encryption scheme based on 3D chaotic cat maps[J]. Chaos, Solitions and Fractals, 2004, (21): 749-761. |
| [10] | Guan Z, Huang F, et al.Chaos-based image encryption algorithm[J]. Physics Letters A, 2005, 346(1-3): 153-157. |
| [11] | Yang H, Wong K, et al.A fast image encryption and authentication scheme based on chaotic maps[J]. Communications in Nonlinear Science and Numerical Simulation, 2010, 15(11): 3507-3517. |
| [12] | Zhao Y, Wang L, et al.Information-Exchange Using the Ergodic Matrices in GF(2)[C]//Proceedings of the 2nd ACM symposium on Information, Computer and Communications Security ACNS 2004: 347-349. |
| [13] | Anonymous. Introduction to public-key cryptography[EB/OL]. . |
| [14] | Menezes A. J.,P. C. v. Oorschot, et al. (1996). Handbook of Applied Cryptography. United States, CRC Press: 816. |
| [15] | Lin Shen-yi, Chen Chih-shen, Li Liu, et al.Tensor product formulation for Hilbert space-filling curves[C]//Proceedings of Parallel Processing, Kaohsiung, 2003:99-106. |
| [16] | Josef S.Secure digital watermark generation based on chaotic Kolmogorov flows[C]//Security and Watermarking of Multimedia Content II, Proceedings of SPIE, 2000,(3971): 306-313. |
| [17] | Jormakka J. Symmetric and asymmetric cryptography overview[EB/OL]. . |
| [18] | 赵永哲,黄声烈,邢磊. 与计算能力无关之密码体制研究[J]. 现代情报,2003,(06):86-87. |
| [19] | 赵永哲,黄声烈,赵焱,等. 程序功能的局限性与密码系统[J]. 吉林大学学报(工学版), 2004,(03):173-177. |
| [20] | 赵永哲,黄声烈,姜占华. GF(2~k)上的遍历矩阵及其特性分析[J]. 小型微型计算机系统,2005,(12):73-77. |
| [21] | 孙永雄,赵永哲,杨永健,等.基于遍历矩阵的单向(陷门)函数的构造方案[J]. 吉林大学学报(信息科学版),2006,(05):102-103. |
| [22] | 周晓谊,赵永哲. 遍历矩阵及其单向限门函数在密码学中的应用[J]. 信息安全与通信保密,2006,(05):112-113,116. |
| [23] | Zhou X, Ma J, et al.BMQE system: an MQ euqations system based on ergodic matrix[C]// Proceedings of the International Conference on Security and Cryptography,2010: 431-435. |
| [24] | Zhou Xiao-yi, Ma Ji-xin, Du Wen-cai, et al.Cryptanalysis of the bisectional MQ equations system[C]// In Proceedings of the 2010 10th IEEE International Conference on Computer and Information Technology, CIT ’10, Washington, DC, USA, 2010:1038-1043. |
| [25] | 宋严,赵永哲. I-HFEM公钥密码方案在数字签名应用上的特性研究[J]. 长春师范学院学报,2013,(08):23-26. |
| [26] | Ismail I A, Amin M, et al.A digital image encryption algorithm based a composition of two chaotic logisitc maps[J]. International Journal of Network Security,2010,11(1): 1-10. |
| [27] | Runger G C, Eaton M L.Most powerful invariant permutation tests[J]. Journal of Multivariate Analysis,1992,42(2): 202-209. |
| [28] | Miyamoto M, Tanaka K, et al.Truncated baker transformation and its extension to image encryption[C]// Proceedings of SPIE on Advanced Materials and Optical System for Chemical, 1999,(3858): 13-25. |
| [29] | Parberry I.Scalability of a neural network for the Knight's tour problem[]J. Neurocomputing 1996,12(1,15): 19-33. |
| [30] | Parberry I.An efficient algorithm for the Knight's tour problem[J]. Discrete Applied Mathematics,1997,73(3,21): 251-260. |
| [31] | Shannon C.Communication theory of secrecy systems[J]. Bell System Technical Journal,1949,28(4): 656-715. |
| [32] | Zhao Y.,S. Pei, et al. Using the Ergodic Matrices over Finite Field to Construct the Dynamic Encryptor[J]. Journal of Chinese Computer Systems, 2007,(11): 2010-2014. |
| [33] | Ye Guo-dong.Image scrambling encryption algorithm of pixel bit based on chaos map[J]. Pattern Recognition Letters,2010,(31) :347-354. |
| [34] | Lian S, Sun J, et al.A block cipher based on a suitable use of the chaotic standard map[J]. Chaos, Solitions and Fractals,2005,(26):177-129. |
| [1] | DONG Yunyun, ZHU Yuling, YAO Shaowen. High-Quality Full-Size Image Steganography Method Based on Improved U-Net and Hybrid Attention Mechanism [J]. Netinfo Security, 2024, 24(7): 1050-1061. |
| [2] | HE Yefeng, QUAN Jiahui, LIU Yan. A Location Privacy Protection Scheme Based on Hybrid Blockchain [J]. Netinfo Security, 2024, 24(2): 229-238. |
| [3] | WU Wei, XU Shasha, GUO Sensen, LI Xiaoyu. Research on Hybrid Recommendation Algorithm for Points of Interest in Location-Based Social Network [J]. Netinfo Security, 2023, 23(9): 75-84. |
| [4] | LI Li, ZHU Jiangwen, YANG Chunyan. Overview of Research on the Revocable Mechanism of Attribute-Based Encryption [J]. Netinfo Security, 2023, 23(4): 39-50. |
| [5] | LIU Xingbin, LIU Cong. Image Encryption Algorithm Based on Cascade Chaotic System and Quantum Baker Map [J]. Netinfo Security, 2023, 23(12): 49-58. |
| [6] | TONG Xiaojun, MAO Ning, ZHANG Miao, WANG Zhu. Image Encryption Algorithm Based on Henon Mapping and Improved Lifting Wavelet Transform [J]. Netinfo Security, 2022, 22(9): 31-39. |
| [7] | WANG Qing, XU Guotian. An Encryption Algorithm Based on Improved Logistic Mapping and Dual-Image Blending [J]. Netinfo Security, 2022, 22(12): 76-86. |
| [8] | LI Dan, YAN Ting, GUO Rui. Quantum Color Image Encryption Algorithm Based on Alternating Quantum Walk [J]. Netinfo Security, 2021, 21(6): 45-51. |
| [9] | ZHENG Hongying, LI Lin, XIAO Di. Secret Image Transmission and Tamper Recovery Based on Compressed Sensing for Fog Computing [J]. Netinfo Security, 2021, 21(4): 10-20. |
| [10] | LUO Wenhua, CHENG Jiaxing. Hybrid DDoS Attack Distributed Detection System Based on Hadoop Architecture [J]. Netinfo Security, 2021, 21(2): 61-69. |
| [11] | GU Zhaojun, REN Yitong, LIU Chunbo, WANG Zhi. Intranet Log Anomaly Detection Model Based on Conformal Prediction [J]. Netinfo Security, 2020, 20(3): 45-50. |
| [12] | Yulei ZHANG, Guangping LUO, Huan WANG, Xiangzhen LIU. TPKC-CLPKC Heterogeneous Hybrid Signcryption Scheme under 5G Network [J]. Netinfo Security, 2019, 19(5): 30-37. |
| [13] | Donghui MEI, Hongling LI. Research on Load Balancing of Virtual Machine Based on Multiple Objective Hybrid Particle Swarm Optimization [J]. Netinfo Security, 2018, 18(2): 78-83. |
| [14] | Xiaoming CHEN, Weiqing YOU, Wenxi LI, Hao JIANG. The Application of a Kind of Reversible Matrix in Secure Communication [J]. Netinfo Security, 2017, 17(5): 7-7. |
| [15] | Fei CHEN, Yifan Si, Yiliang HAN. Hybird Attribute-based Encryption Signature Scheme for PHR System [J]. Netinfo Security, 2016, 16(12): 46-50. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||