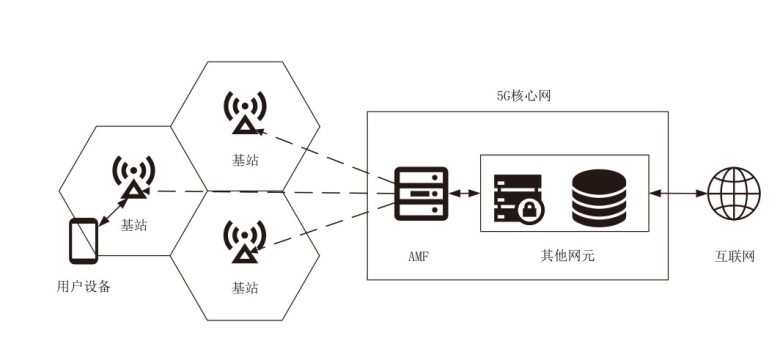
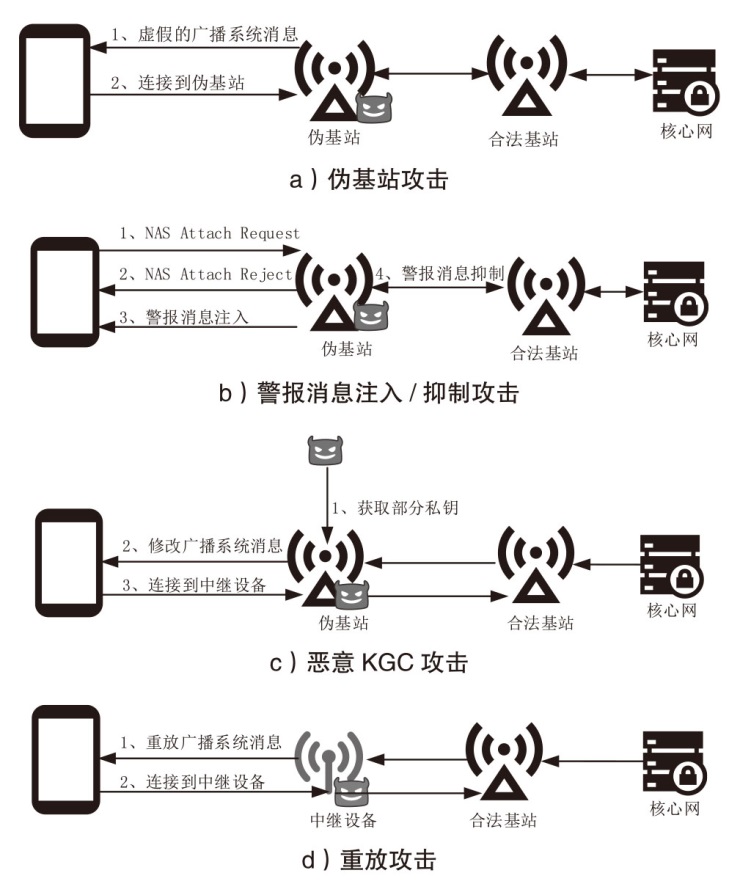
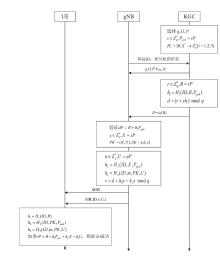
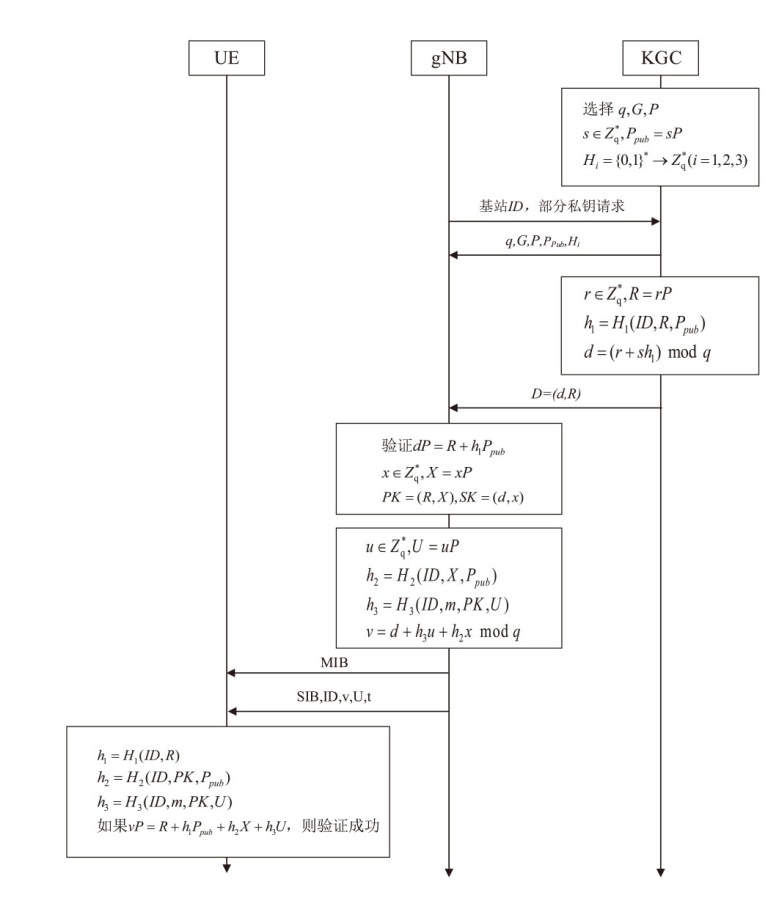
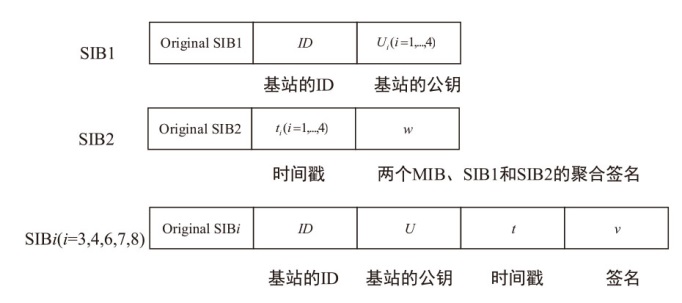
Netinfo Security ›› 2024, Vol. 24 ›› Issue (8): 1220-1230.doi: 10.3969/j.issn.1671-1122.2024.08.008
Previous Articles Next Articles
System Broadcast Information Authentication Protocol Based on Certificateless Signature for 5G Network
SUN Zhongxiu1,2, PENG Cheng1,2( ), FAN Wei1,2
), FAN Wei1,2
- 1. Institute of Information Engineering, Chinese Academy of Sciences, Beijing 100093, China
2. School of Cyber Security, University of Chinese Academy of Sciences, Beijing 100049, China
-
Received:2024-04-25Online:2024-08-10Published:2024-08-22
CLC Number:
Cite this article
SUN Zhongxiu, PENG Cheng, FAN Wei. System Broadcast Information Authentication Protocol Based on Certificateless Signature for 5G Network[J]. Netinfo Security, 2024, 24(8): 1220-1230.
share this article
Add to citation manager EndNote|Ris|BibTeX
URL: http://netinfo-security.org/EN/10.3969/j.issn.1671-1122.2024.08.008
| [1] | SHAIK A, BORGAONKAR R, ASOKAN N, et al. Practical Attacks against Privacy and Availability in 4G/LTE Mobile Communication Systems[EB/OL]. (2015-10-20)[2024-04-16]. https://ui.adsabs.harvard.edu/abs/2015arXiv151007563S/abstract. |
| [2] | 3GPP. Specification Number TR 33.809 Version 0.8.0, Study on 5G Security Enhancements against False Base Stations[EB/OL]. (2023-06-20)[2024-04-16]. https://portal.3gpp.org/desktopmodules/Specifications/SpecificationDetails.aspx?specificationId=3952. |
| [3] | SHAIK A, BORGAONKAR R, PARK S, et al. New Vulnerabilities in 4G and 5G Cellular Access Network Protocols: Exposing Device Capabilities[C]// ACM. Proceedings of the 12th Conference on Security and Privacy in Wireless and Mobile Networks. New York: ACM, 2019: 221-231. |
| [4] | BITSIKAS E, POPPER C. You Have Been Warned: Abusing 5G’s Warning and Emergency Systems[C]// ACM. Proceedings of the 38th Annual Computer Security Applications Conference. New York: ACM, 2022: 561-575. |
| [5] | 3GPP. 3GPP Specification Number TR 21.915 Version 15.0.0, Release Description; Release 15.[EB/OL]. (2018-03-20)[2024-04-06]. https://www.3gpp.org/ftp/Specs/archive/21_series/21.915/. |
| [6] | HA Man, CHEN Jing, LIU J K et al. Malicious KGC Attacks in Certificateless Cryptography[C]// ACM. Proceedings of the 2nd ACM Symposium on Information, Computer and Communications Security. New York: ACM, 2007: 302-311. |
| [7] | HUSSAIN S R, ECHEVERRIA M, CHOWDHURY O, et al. Privacy Attacks to the 4G and 5G Cellular Paging Protocols Using Side Channel Information[J]. Network and Distributed Systems Security (NDSS) Symposium, 2019(8): 1-12. |
| [8] | SHAIK A, BORGAONKAR R, PARK S, et al. On the Impact of Rogue Base Stations in 4G/LTE Self Organizing Networks[C]// ACM. Proceedings of the 11th ACM Conference on Security & Privacy in Wireless and Mobile Networks. New York: ACM, 2018: 75-86. |
| [9] | LEE G, LEE J. This is Your President Speaking: Spoofing Alerts in 4G LTE Networks[C]// ACM. Proceedings of the 17th Annual International Conference on Mobile Systems, Applications, and Services. New York: ACM, 2019: 404-416. |
| [10] | KIM M, PARK J G, MOON D S, et al. Long-Term Evolution Vulnerability Focusing on System Information Block Messages[C]// IEEE. 2020 International Conference on Information and Communication Technology Convergence (ICTC). New York: IEEE, 2020: 837-842. |
| [11] | JIN Jian, LIAN Changliang, XU Ming. Rogue Base Station Detection Using A Machine Learning Approach[C]// IEEE. 2019 28th Wireless and Optical Communications Conference (WOCC). New York: IEEE, 2019: 1-5. |
| [12] | SINGLA A, HUSSAIN S R, CHOWDHURY O, et al. Protecting the 4G and 5G Cellular Paging Protocols against Security and Privacy Attacks[J]. Proceedings on Privacy Enhancing Technologies, 2020(6): 1-9. |
| [13] | LOTTO A, SINGH V, RAMASUBRAMANIAN B, et al. Baron: Base-Station Authentication through Core Network for Mobility Management in 5G Networks[C]// ACM. Proceedings of the 16th ACM Conference on Security and Privacy in Wireless and Mobile Networks. New York: ACM, 2023: 133-144. |
| [14] | HUSSAIN S R, ECHEVERRIA M, SINGLA A, et al. Insecure Connection Bootstrapping in Cellular Networks: The Root of All Evil[C]// ACM. Proceedings of the 12th Conference on Security and Privacy in Wireless and Mobile Networks. New York: ACM, 2019: 1-11. |
| [15] | SINGLA A, BEHNIA R, HUSSAIN S R, et al. Look Before You Leap: Secure Connection Bootstrapping for 5G Networks to Defend against Fake Base-Stations[C]// ACM. Proceedings of the 2021 ACM Asia Conference on Computer and Communications Security. New York: ACM, 2021: 501-515. |
| [16] | SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]//Springer. Advances in Cryptology:Proceedings of CRYPTO. Heidelberg: Springer, 1985: 47-53. |
| [17] | AL-RIYAMI S S, PATERSON K G. Certificateless Public Key Cryptography[C]// Springer. International Conference on the Theory and Application of Cryptology and Information Security. Heidelberg: Springer, 2003: 452-473. |
| [18] | WANG Liangliang, CHEN Kefei, LONG Yu, et al. An Efficient Pairing-Free Certificateless Signature Scheme for Resource-Limited Systems[J]. Science China (Information Sciences), 2017, 60(11): 11-23. |
| [19] | THUMBUR G, RAO G S, REDDY P V, et al. Efficient Pairing-Free Certificateless Signature Scheme for Secure Communication in Resource-Constrained Devices[J]. IEEE Communications Letters, 2020, 24(8): 1641-1645. |
| [20] | XU Zhiyan, LUO Min, KHAN M K, et al. Analysis and Improvement of a Certificateless Signature Scheme for Resource-Constrained Scenarios[J]. IEEE Communications Letters, 2020, 25(4): 1074-1078. |
| [21] | KHAN M, ALHAKAMI H, ULLAH I, et al. A Resource-Friendly Certificateless Proxy Signcryption Scheme for Drones in Networks Beyond 5G[J]. Drones, 2023, 7(5): 321-332. |
| [22] | ALMAZROI A, ALDHAHRI E, AL-SHAREEDA M, et al. ECA-VFog: An Efficient Certificateless Authentication Scheme for 5G-Assisted Vehicular Fog Computing[J]. Plos One, 2023, 18(6): 87-91. |
| [23] | DOLEV D, YAO A. On the Security of Public Key Protocols[J]. IEEE Transactions on Information Theory, 1983, 29(2): 198-208. |
| [24] | 3GPP. Specification Number TS 38.104 Version 15.9.0, Base Station (BS) Radio Transmission and Reception[EB/OL]. (2020-04-09)[2024-04-16]. https://www.3gpp.org/ftp/Specs/archive/38_series/38.104/. |
| [25] | BONEH D, GENTRY C, LYNN B, et al. Aggregate and Verifiably Encrypted Signatures from Bilinear Maps[C]// Springer. Advances in Cryptology—EUROCRYPT 2003:International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2003: 416-432. |
| [26] | ZHAO Yunlei. Aggregation of Gamma-Signatures and Applications to Bitcoin[EB/OL]. (2018-04-21)[2024-04-16]. https://eprint.iacr.org/2018/414.pdf. |
| [27] | SRS. SRSRAN_Project[EB/OL]. (2023-02-22)[2024-04-24]. https://github.com/srsran/srsRAN_Project. |
| [28] | NIST. NIST Report on Cryptographic Key Length and Cryptoperiod[EB/OL]. (2020-05-24)[2024-04-06]. https://www.keylength.com/en/4/. |
| [29] | YAVUZ A A, MUDGERIKAR A, SINGLA A, et al. Real-Time Digital Signatures for Time-Critical Networks[J]. IEEE Transactions on Information Forensics and Security, 2017, 12(11): 2627-2639. |
| [1] | HUANG Wangwang, ZHOU Hua, WANG Daiqiang, ZHAO Qi. Design of Reconfigurable Key Security Authentication Protocol for IoT Based on National Cryptography SM9 [J]. Netinfo Security, 2024, 24(7): 1006-1014. |
| [2] | ZHAI Peng, HE Jingsha, ZHANG Yu. An Identity Authentication Method Based on SM9 and Blockchain in the IoT Environment [J]. Netinfo Security, 2024, 24(2): 179-187. |
| [3] | LIU Qin, ZHANG Biao, TU Hang. Certificateless Blind Signature Scheme Based on twisted Edwards Curve [J]. Netinfo Security, 2022, 22(8): 19-25. |
| [4] | WANG Shushuang, MA Zhaofeng, LIU Jiawei, LUO Shoushan. Research and Implementation of Cross-Chain Security Access and Identity Authentication Scheme of Blockchain [J]. Netinfo Security, 2022, 22(6): 61-72. |
| [5] | WU Kehe, CHENG Rui, JIANG Xiaochen, ZHANG Jiyu. Security Protection Scheme of Power IoT Based on SDP [J]. Netinfo Security, 2022, 22(2): 32-38. |
| [6] | WU Kehe, CHENG Rui, ZHENG Bihuang, CUI Wenchao. Research on Security Communication Protocol of Power Internet of Things [J]. Netinfo Security, 2021, 21(9): 8-15. |
| [7] | SHEN Zhuowei, GAO Peng, XU Xinyu. Design of DDS Secure Communication Middleware Based on Security Negotiation [J]. Netinfo Security, 2021, 21(6): 19-25. |
| [8] | WANG Jian, ZHAO Manli, CHEN Zhihao, SHI Bo. An Authentication Scheme for Conditional Privacy Preserving Based on Pseudonym in Intelligent Transportation [J]. Netinfo Security, 2021, 21(4): 49-61. |
| [9] | LI Tong, ZHOU Xiaoming, REN Shuai, XU Jian. Light-weight Mutual Authentication Protocol for Mobile Edge Computing [J]. Netinfo Security, 2021, 21(11): 58-64. |
| [10] | XIAO Shuai, ZHANG Hanlin, XIAN Hequn, CHEN Fei. A Password Authentication Key Agreement Protocol for IoT Devices [J]. Netinfo Security, 2021, 21(10): 83-89. |
| [11] | LIU Xiaofen, CHEN Xiaofeng, LIAN Guiren, LIN Song. Authenticated Multiparty Quantum Secret Sharing Protocol with d-level Single Particle [J]. Netinfo Security, 2020, 20(3): 51-55. |
| [12] | LIU Lijuan, LI Zhihui, ZHI Danli. A Multi-party Quantum Key Distribution Protocol with Quantum Identity Authentication [J]. Netinfo Security, 2020, 20(11): 59-66. |
| [13] | Fuyou ZHANG, Qiongxiao WANG, Li SONG. Research on Unified Identity Authentication System Based on Biometrics [J]. Netinfo Security, 2019, 19(9): 86-90. |
| [14] | Shun ZHANG, Zhangkai CHEN, Fengyu LIANG, Runhua SHI. A Quantum Identity Authentication Based on Bell State [J]. Netinfo Security, 2019, 19(11): 43-48. |
| [15] | Wei HU, Qiuhan WU, Shengli LIU, Wei FU. Design of Secure eID and Identity Authentication Agreement in Mobile Terminal Based on Guomi Algorithm and Blockchain [J]. Netinfo Security, 2018, 18(7): 7-9. |
| Viewed | ||||||
|
Full text |
|
|||||
|
Abstract |
|
|||||