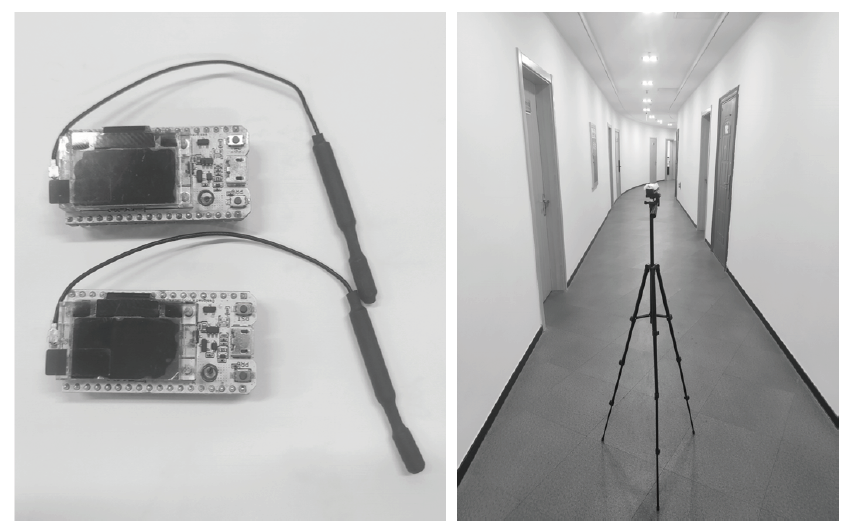
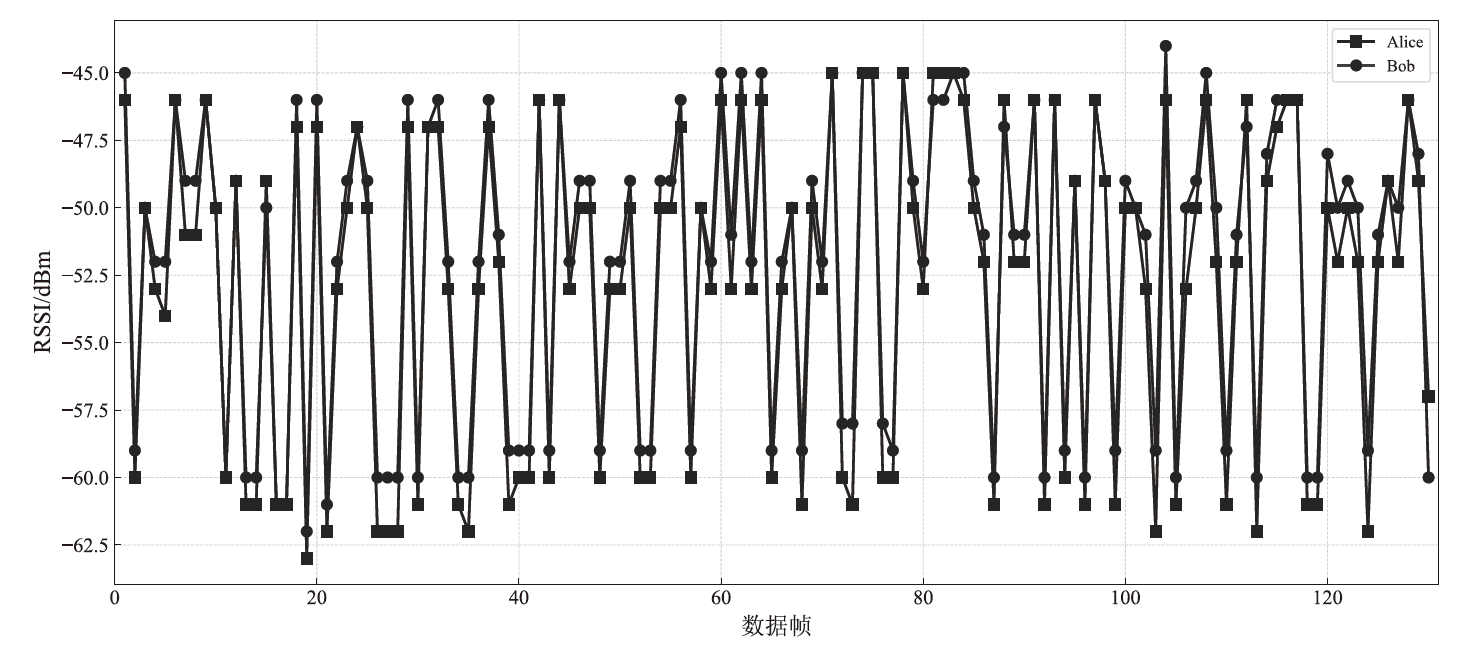
| [1] |
HERSHEY J E, HASSAN A A. Unconventional Cryptographic Keying Variable Management[J]. IEEE Transactions on Communications, 1995, 43(1): 3-6.
doi: 10.1109/26.385951
URL
|
| [2] |
XU Weitao, ZHANG Junqing, HUANG Shunqi, et al. Key Generation for Internet of Things: A Contemporary Survey[J]. ACM Computing Surveys, 2021, 54(1): 1-37.
|
| [3] |
OU Minsheng, LIAO Wei, YUAN Zhiming, et al. Research on Key Generation in Marine Environment Based on VHF Channel Characteristics[J]. Netinfo Security, 2015, 15(10): 80-85.
|
|
欧敏晟, 廖巍, 袁志民, 等. 海上基于超短波信道特征的密钥生成技术研究[J]. 信息网络安全, 2015, 15(10):80-85.
|
| [4] |
MATHUR S, TRAPPE W, MANDAYAM N, et al. Radio-Telepathy: Extracting a Secret Key from an Unauthenticated Wireless Channel[C]// ACM. 14th Annual International Conference on Mobile Computing and Networking. New York: ACM, 2008: 128-139.
|
| [5] |
ZENG Kai, WU D, CHAN An, et al. Exploiting Multiple-Antenna Diversity for Shared Secret Key Generation in Wireless Networks[C]// IEEE. IEEE INFOCOM. New York: IEEE, 2010: 1-9.
|
| [6] |
JANA S, PREMNATH S N, CLARK M, et al. On the Effectiveness of Secret Key Extraction from Wireless Signal Strength in Real Environments[C]// ACM. 15th Annual International Conference on Mobile Computing and Networking. New York: ACM, 2009: 321-332.
|
| [7] |
LIU Hongbo, WANG Yang, YANG Jie, et al. Fast and Practical Secret Key Extraction by Exploiting Channel Response[C]// IEEE. IEEE INFOCOM. New York: IEEE, 2013: 3048-3056.
|
| [8] |
XU Weitao, JHA S, HU Wen. LoRa-Key: Secure Key Generation System for LoRa-Based Network[J]. IEEE Internet of Things Journal, 2019, 6(4): 6404-6416.
doi: 10.1109/JIOT.2018.2888553
|
| [9] |
PATWARI N, CROFT J, JANA S, et al. High-Rate Uncorrelated Bit Extraction for Shared Secret Key Generation from Channel Measurements[J]. IEEE Transactions on Mobile Computing, 2010, 9(1): 17-30.
doi: 10.1109/TMC.2009.88
URL
|
| [10] |
YASUKAWA S, IWAI H, SASAOKA H. Adaptive Key Generation in Secret Key Agreement Scheme Based on the Channel Characteristics in OFDM[C]// IEEE. 2008 International Symposium on Information Theory and Its Applications. New York: IEEE, 2008: 1-6.
|
| [11] |
MARGELIS G, FAFOUTIS X, OIKONOMOU G, et al. Physical Layer Secret-Key Generation with Discreet Cosine Transform for the Internet of Things[C]// IEEE. 2017 IEEE International Conference on Communications(ICC). New York: IEEE, 2017: 1-6.
|
| [12] |
WU Yang, SUN Yongmei, ZHAN Lei, et al. Low Mismatch Key Agreement Based on Wavelet-Transform Trend and Fuzzy Vault in Body Area Network[EB/OL]. (2013-06-06)[2023-04-11]. https://journals.sagepub.com/doi/10.1155/2013/912873.
|
| [13] |
ZHANG Junqing, LI Guyue, MARSHALL A, et al. A New Frontier for IoT Security Emerging From Three Decades of Key Generation Relying on Wireless Channels[J]. IEEE Access, 2020, 8: 138406-138446.
doi: 10.1109/Access.6287639
URL
|
| [14] |
ZHANG Junqing, RAJENDRAN S, SUN Zhi, et al. Physical Layer Security for the Internet of Things: Authentication and Key Generation[J]. IEEE Wireless Communications, 2019, 26(5): 92-98.
doi: 10.1109/MWC.2019.1800455
|
| [15] |
JUNEJO A K, BENKHELIFA F, WONG B, et al. LoRa-LiSK: A Lightweight Shared Secret Key Generation Scheme for LoRa Networks[J]. IEEE Internet of Things Journal, 2022, 9(6): 4110-4124.
doi: 10.1109/JIOT.2021.3103009
URL
|
| [16] |
RUOTSALAINEN H, ZHANG Junqing, GREBENIUK S. Experimental Investigation on Wireless Key Generation for Low Power Wide Area Networks[J]. IEEE Internet of Things Journal, 2019, 7(3): 1745-1755.
doi: 10.1109/JIoT.6488907
URL
|
| [17] |
LI Guyue, HU Aiqun, SHI Le. Secret Key Extraction in Wireless Channel[J]. Journal of Cryptologic Research, 2014, 1(3): 211-224.
|
| [18] |
SUI Lei, GUO Yuanbo, JIANG Wenbo, et al. Research on Key Generation and Extraction Based on Wireless Channel Characteristics[J]. Computer Science, 2015, 42(2): 137-141.
doi: 10.11896/j.issn.1002-137X.2015.02.030
|
|
隋雷, 郭渊博, 姜文博, 等. 基于无线信道特征的密钥生成与提取研究[J]. 计算机科学, 2015, 42(2):137-141.
doi: 10.11896/j.issn.1002-137X.2015.02.030
|
 ), MIAO Kaitao, CHEN Wen, WU Changfan
), MIAO Kaitao, CHEN Wen, WU Changfan