| [1] |
XIAO Ya, FAN Zhijie, LAN Julong, et al.Discovery Method for Distributed Denial-of-Service Attack Behavior in SDNs Using a Feature-Pattern Graph Model[J]. Frontiers of Information Technology & Electronic Engineering, 2017, 38(2): 1195-1208.
|
| [2] |
LIU Yifan, ZHAO Bo, ZHAO Pengyuan, et al.A Survey: Typical Security Issues of Software-Defined Networking[J]. China Communications, 2019, 16(7): 13-31.
|
| [3] |
LIU Zhengpeng, HE Yupeng, WANG Wensheng, et al.DDoS Attack Detection Scheme Based on Entropy and PSO-BP Neural Network in SDN[J]. China Communications, 2019, 16(7): 144-155.
|
| [4] |
LI Saifei, CUI Yunhe, NI Yongfeng, et al.An Effective SDN Controller Scheduling Method to Defence DDoS Attacks[J]. Chinese Journal of Electronics, 2019, 28(2): 404-407.
|
| [5] |
CHEN Xingshu, HUA Qiang, WANG Yitong, et al.Research on Low-rate DDoS Attack of SDN Network in Cloud Environment[J]. Journal on Communications, 2019, 40(6): 210-222.
|
|
陈兴蜀,滑强,王毅桐,等.云环境下SDN网络低速率DDoS攻击的研究[J].通信学报,2019,40(6):210-222.
|
| [6] |
GUPTA B B, BADVE O P.Taxonomy of DoS and DDoS Attacks and Desirable Defense Mechanism in a Cloud Computing Environment[J]. Neural Computing and Applications, 2017, 28(12): 3655-3682.
|
| [7] |
AMJAD M,MITHUN M,SYED H A, et al.NBC-MAIDS: Naïve Bayesian Classification Technique in Multi-agent System-enriched IDS for Securing IoT against DDoS Attacks[J]. The Journal of Supercomputing, 2018, 74(10): 5156-5170.
|
| [8] |
SEMERCI M, CEMGIL A T, SANKUR B.An Intelligent Cyber Security System Against DDoS Attacks in SIP Networks[J]. Computer Networks, 2018, 136(5): 137-154.
|
| [9] |
BEHAL S, KUMAR K.Detection of DDoS Attacks and Flash Events Using Novel Information Theory Metrics[J]. Computer Networks, 2017, 116(4): 96-110.
|
| [10] |
ZHANG Long, WANG Jinsong.DDoS Attack Detection Model Based on Information Entropy and DNN in SDN[J]. Journal of Computer Research and Development, 2019, 56(5): 909-918.
|
|
张龙,王劲松. SDN中基于信息熵与DNN的DDoS攻击检测模型[J].计算机研究与发展,2019,56(5):909-918.
|
| [11] |
QIAN Hongyan, XUE Hao, CHEN Ming.UDM: NFV-based Prevention Mechanism against DDoS Attack on SDN Controller[J]. Journal on Communications, 2019, 40(3): 116-124.
|
|
钱红燕,薛昊,陈鸣. UDM:基于NFV的防止DDoS攻击SDN控制器的机制[J].通信学报,2019,40(3):116-124.
|
| [12] |
BERTINO E, ISLAM N.Botnets and Internet of Things Security[J]. Computer, 2017, 50(2): 76-79.
|
| [13] |
WANG K, DU M, MAHARJAN S, et al.Strategic Honeypot Game Model for Distributed Denial of Service Attacks in the Smart Grid[J]. IEEE Transactions on Smart Grid, 2017, 8(5): 2474-2482.
|
| [14] |
LI Chuanhuang, WU Yan, QIAN Zhengzhe, et al.DDoS Attack Detection and Defense Based on Hybrid Deep Learning Model in SDN[J]. Journal on Communications, 2018, 39(7): 176-187.
|
|
李传煌,吴艳,钱正哲,等. SDN 下基于深度学习混合模型的DDoS 攻击检测与防御[J].通信学报,2018,39(7):176-187.
|
| [15] |
TIAN Junfeng, QI Liuling.DDoS Attack Detection Method Based on Conditional Entropy and GHSOM in SDN[J]. Journal on Communications, 2019, 39(8): 140-149.
|
|
田俊峰,齐鎏岭. SDN中基于条件熵和GHSOM的DDoS攻击检测方法[J].通信学报,2018,39(8):140-149.
|
| [16] |
BAO Nan, ZUO Jiakuo, HU Han, et al.SDN Based Network Resource Selection Multi-objective Optimization Algorithm[J]. Journal on Communications, 2019, 40(2): 51-59.
|
|
鲍楠,左加阔,胡晗,等.基于SDN的网络资源选择多目标优化算法[J].通信学报,2019,40(2):51-59.
|
| [17] |
LIU Zhouzhou, LI Shining.Multi mobile Agent Itinerary Planning Based on Network Coverage and Multi-objective Discrete Social Spider Optimization Algorithm[J]. Journal on Communications, 2017, 38(6): 1-9.
|
|
刘洲洲,李士宁.基于网络覆盖和多目标离散群集蜘蛛算法的多移动agent规划[J].通信学报,2017,38(6):1-9.
|
| [18] |
HE Heng, HU Yan, ZHENG Lianghan, et al.Efficient DDoS Attack Detection and Prevention Scheme Based on SDN in Cloud Environment[J]. Journal on Communications, 2018, 39(4): 139-151.
|
|
何亨,胡艳,郑良汉,等.云环境中基于SDN的高效DDoS攻击检测与防御方案[J].通信学报,2018,39(4):139-151.
|
| [19] |
MA Ding, ZHUANG Lei, LAN Julong.Discrete Particle Swarm Optimization Based Multi-objective Service Path Constructing Algorithm[J]. Journal on Communications, 2017, 38(2): 94-105.
|
|
马丁,庄雷,兰巨龙.基于离散粒子群优化的多目标服务路径构建算法[J].通信学报,2017,38(2):94-105.
|
| [20] |
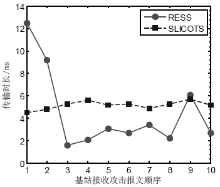
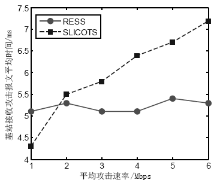
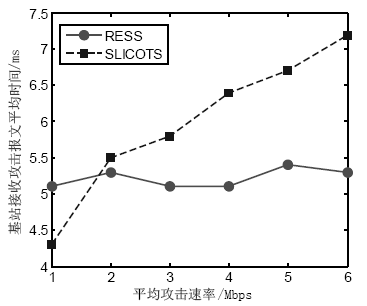
MOHAMMADI R, JAVIDAN R, CONTI M.SLICOTS: An SDN-Based Lightweight Countermeasure for TCP SYN Flooding Attacks[J]. IEEE Transactions on Network and Service Management, 2017, 14(6): 487-497.
|
 )
)