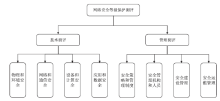
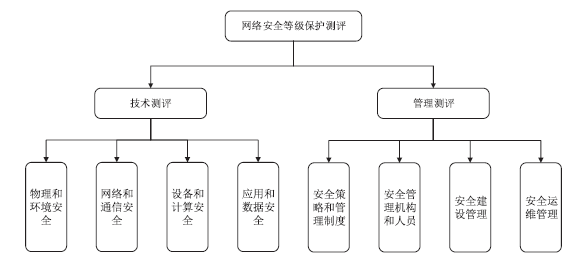
| [1] |
GUO Qiquan, et al.Training Course of Network Security Law and Network Security Classification Protection System (2018) [M]. Beijing: Publishing House of Electronics Industry, 2018.
|
| [2] |
ZHAO Yanling.The New Ideas and Technologies of American Cybersecurity Game-change program[J]. Netinfo Security, 2015, 15(9) : 50-53.
|
|
赵艳玲. 美国改变网络空间安全游戏规则的新理念与新技术[J]. 信息网络安全,2015,15(9):50-53.
|
| [3] |
ZHANG HuanGuo, HAN WenBao, LAI XueJia, et al.Survey on Cyberspace Security[J]. Science China Information Sciences, 2015, 58(11) :1-43.
|
| [4] |
LI Jing, LIU Hongmei, LIU Yangzi.Overview of Network Security Strategies of Major Foreign Countries[J]. China Infornation Security, 2012 (7) : 34-37.
|
|
李婧, 刘洪梅, 刘阳子. 国外主要国家网络安全战略综述[J]. 中国信息安全, 2012 (7) : 34-37.
|
| [5] |
ZHANG Y C, FENG S D, ZHAO S, et al. Research on Critical Information Infrastructure Security[J]. Modern Science & Technology of Telecommunications, 2015 (5).
|
| [6] |
Standardization Administration of the People's Republic of China. Information Security Technology—Evaluation Requirements for Classified Protection of Cybersecurity (draft) [S]. Beijing:Standards Press of China,2018.
|
| [7] |
Standardization Administration of the People's Republic of China. Information Security Technology—Baseline for Classified Protection of Cybersecurity (draft) [S]. Beijing:Standards Press of China,2018.
|
| [8] |
YI, NEN T .SSH: Secure Login Connections over the Internet[C]//Usenix.SSYM'96 Proceedings of the 6th Conference on USENIX Security Symposium, Focusing on Applications of Cryptography,July 22 - 25, 1996,San Jose, California.Berkeley: Usenix,1996 :4.
|
| [9] |
TIAN Yanwei, YANG Songru, LI Jie.Research on Risks and Countermeasures of Wireless WiFi Key APP[J]. Netinfo Security, 2017, 17(70): 80-84.
|
|
田延伟, 杨松儒, 李杰. 无线WiFi密钥APP风险隐患及对策研究[J]. 信息网络安全, 2017, 17(70): 80-84.
|
| [10] |
MILLER S K .Facing the Challenge of Wireless Security[J]. Computer, 2001, 34(7) :16-18.
|
| [11] |
ARBAUGH W A .Wireless Security is Different[J]. Computer, 2003, 36(8) :99-101.
|
| [12] |
LAWTON G .Web 2.0 Creates Security Challenges[J]. Computer, 2007, 40(10) :13-16.
|
| [13] |
MA Su’an, LUO Wen, ZHANG Jinxin.Establishing New Network Defense System for Responding to Advanced Network Threat[J]. Journal of Information Securyity Research, 2016, 2(4) : 377-382.
|
|
马苏安, 骆文, 张金鑫. 应对高级网络威胁建立新型网络防御系统[J]. 信息安全研究, 2016, 2(4) : 377-382.
|
| [14] |
LANGNER R .Stuxnet: Dissecting a Cyberwarfare Weapon[J]. IEEE Security & Privacy, 2011, 9(3) : 49-51.
|
| [15] |
ZHANG Jiawei, ZHANG Dongmei, HUANG Siqi.Design and Implementation of Anti APT Attack Trusted Software Base[J]. Netinfo Security, 2017 ,17(6) :49-55.
|
|
张家伟, 张冬梅, 黄偲琪. 一种抗APT攻击的可信软件基设计与实现[J]. 信息网络安全, 2017,17(6) :49-55.
|