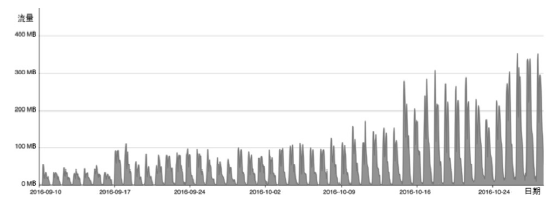
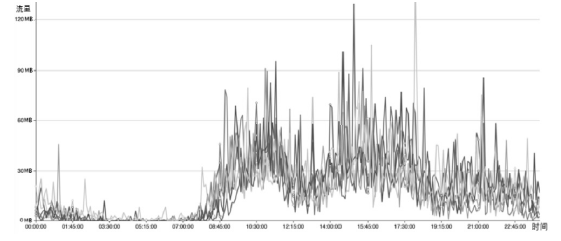
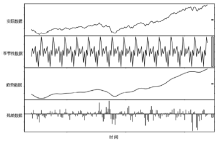
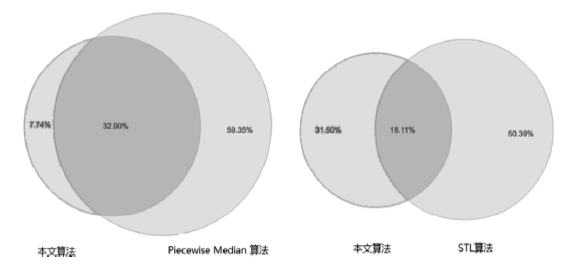
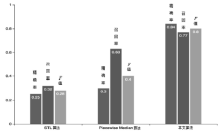
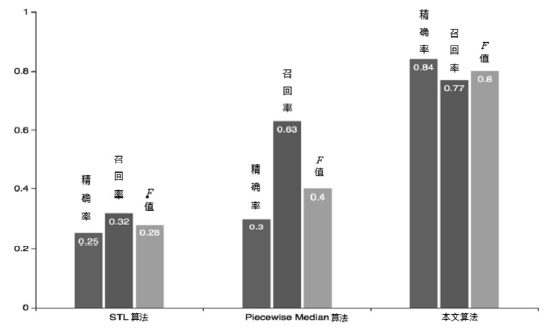
| [1] |
李鑫,张维纬,隋子畅,等. 新型SQL注入及其防御技术研究与分析[J]. 信息网络安全,2016(2):66-73.
|
| [2] |
AHMED M, MAHMOOD A N, HU Jiankun.A Survey of Network Anomaly Detection Techniques[J]. Journal of Network & Computer Applications, 2016(60):19-31.
|
| [3] |
MARCHETTI M, PIERAZZI F, COLAJANNI M, et al.Analysis of High Volumes of Network Traffic for Advanced Persistent Threat Detection[J]. Computer Networks, 2016(109):127-141.
|
| [4] |
LAKHINA A, CROVELLA M, DIOT C.Mining Anomalies Using Traffic Feature Distributions[C]//ACM.ACM SIGCOMM 2005 Conference on Applications, Technologies, Architectures, and Protocols for Computer Communications, August 22 - 26, 2005. Philadelphia, Pennsylvania, USA. New York: ACM, 2005:217-228.
|
| [5] |
KONDO S, SATO N.Botnet Traffic Detection Techniques by C&C Session Classification Using SVM[A]// Advances in Information and Computer Security[M]. Heidelberg:Springer-Verlag Berlin, Heidelberg, 2007:91-104.
|
| [6] |
ZHAO D, TRAORE I, SAYED B, et al.Botnet Detection Based on Traffic Behavior Analysis and Flow Intervals[J]. Computers & Security, 2013, 39(4):2-16.
|
| [7] |
陈明奇,洪学海,王伟,等. 关于网络安全和信息技术发展态势的思考[J]. 信息网络安全,2015(4):1-4.
|
| [8] |
VANIA J, MENIYA A, JETHVA H B. A Review on Botnet and Detection Technique[EB/OL]. ,2017-6-1.
|
| [9] |
BAHAA-ELDIN A M. Time Series Analysis based Models for Network Abnormal Traffic Detection[C]//IEEE.International Conference on Computer Engineering & Systems, November 29- December 1, 2011. Cairo, Egypt.NJ:IEEE, 2011:64-70.
|
| [10] |
陈善雄,彭茂玲,彭喜化. 一种基于偏最小二乘的网络入侵检测方法分析[J]. 信息网络安全,2016(1):6-10.
|
| [11] |
WÄLCHLI M, BRAUN T. Efficient Signal Processing and Anomaly Detection in Wireless Sensor Networks[A]// Applications of Evolutionary Computing[M]. Heidelberg: Springer-Verlag Berlin, Heidelberg, 2009:81-86.
|
| [12] |
BEREZIŃSKI P, JASIUL B, SZPYRKA M. An Entropy-based Network Anomaly Detection Method[J]. Entropy, 2015, 17(4):2367-2408.
|
| [13] |
CORBYN J.Time Series Analysis with Applications in R[J]. Journal of the Royal Statistical Society: Series A (Statistics in Society), 2011, 174(2):507.
|
| [14] |
HUANG S J, SHIH K R.Short-term Load Forecasting via ARMA Model Identification Including Non-Gaussian Process Considerations[J]. IEEE Transactions on Power Systems, 2003, 18(2): 673-679.
|
| [15] |
WEST M.Time Series Decomposition[J]. Biometrika, 1997,84(2): 489-494.
|
| [16] |
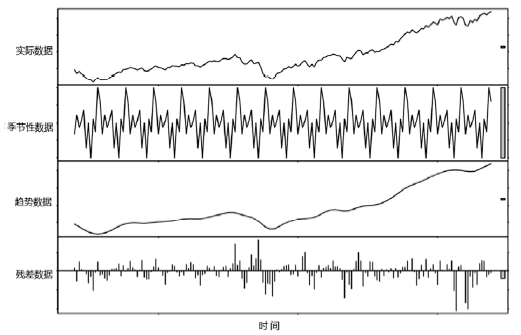
CLEVELAND R B, CLEVELAND W S.STL: A Seasonal-Trend Decomposition Procedure Based on Loess[J]. Journal of Official Statistics, 1990, 6(1):3-33.
|
| [17] |
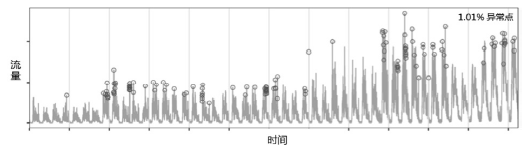
ROSNER B.Percentage Points for a Generalized ESD Many-Outlier Procedure[EB/OL]. ,2017-6-1.
|
| [18] |
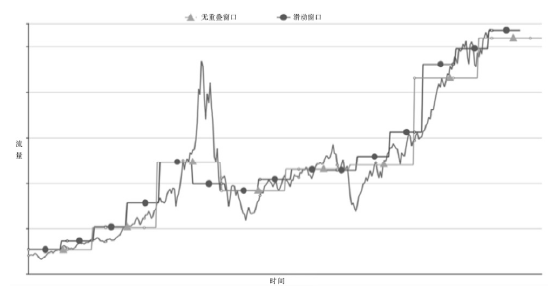
LIU Haiqin, KIM M S.Real-Time Detection of Stealthy DDoS Attacks Using Time-Series Decomposition[C]//IEEE.Communications (ICC), 2010 IEEE International Conference on, May 23-27, 2010. Cape Town, South Africa.NJ:IEEE, 2010: 1-6.
|
| [19] |
VALLIS O, HOCHENBAUM J, KEJARIWAL A. A Novel Technique for Long-Term Anomaly Detection in the Cloud[EB/OL]. ,2017-6-1.
|
| [20] |
Yahoo Finance.^IXIC Summary for NASDAQ composite[EB/OL]., 2017-6-13.
|
 )
)