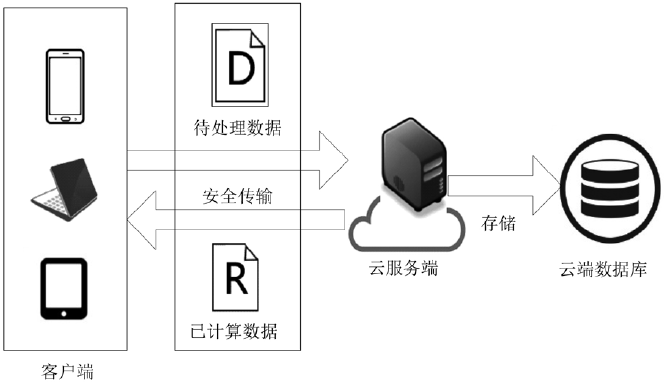
| [1] |
DIFFIE W, HELLMAN M.New Directions in Cryptography[J]. IEEE Transactions on Information Theory, 1976, 22(6): 644-654.
|
| [2] |
CHEN Xiaofeng, HUANG Xinyi, LI Jin, et al.New Algorithms for Secure Outsourcing of Large-scale Systems of Linear Equations[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(1): 69-78.
|
| [3] |
HOHENBERGER S, LYSYANSKAYA A.How to Securely Outsource Cryptographic Computations[C]//Springer. The Second International Conference on Theory of Cryptography, February 10-12, 2005, Cambridge, MA. Heidelberg: Springer, 2005: 264-282.
|
| [4] |
ATALLAH M J, FRIKKEN K B.Securely Outsourcing Linear Algebra Computations[C]//ACM. 5th ACM Symposium on Information, Computer and Communications Security, April 13-16, 2010, Beijing, China. New York: ACM, 2010: 48-59.
|
| [5] |
CHEN Xiofeng, LI Jin, MA Jianfeng, et al.New Algorithms for Secure Outsourcing of Modular Exponentiations[J]. IEEE Transactions on Parallel and Distributed Systems, 2014, 25(9): 2386-2396.
|
| [6] |
MA Xu, LI Jin, ZHANG Fangguo.Outsourcing Computation of Modular Exponentiations in Cloud Computing[J]. Cluster Computing, 2013, 16(4): 787-796.
|
| [7] |
GREEN M, HOHENBERGER S, WATERS B.Outsourcing the Decryption of ABE Ciphertexts[C]//ACM. 20th USENIX Conference on Security, August 8-12, 2011, San Francisco, CA. New York: ACM, 2011: 34.
|
| [8] |
LAI Junzuo, DENG R H, GUAN Chaowen, et al.Attribute-based Encryption With Verifiable Outsourced Decryption[J]. IEEE Transactions on Information Forensics and Security, 2013, 8(8): 1343-1354.
|
| [9] |
LIN Suqin, ZHANG Rui, MA Hui, et al.Revisiting Attribute-based Encryption with Verifiable Outsourced Decryption[J]. IEEE Transactions on Information Forensics and Security, 2015, 10(10): 2119-2130.
|
| [10] |
MAO Xianping, LAI Junzuo, MEI Qixiang, et al.Generic and Efficient Constructions of Attribute-based Encryption with Verifiable Outsourced Decryption[J]. IEEE Transactions on Dependable and Secure Computing, 2016, 13(5): 533-546.
|
| [11] |
MA Hui, ZHANG Rui, WAN Zhiguo, et al.Verifiable and Exculpable Outsourced Attribute-based Encryption for Access Control in Cloud Computing[J]. IEEE Transactions on Dependable and Secure Computing, 2017, 14(6): 679-692.
|
| [12] |
勇卿, 孙伟. 云计算中可撤销存储的外包加解密CP-ABE方案[J]. 信息网络安全,2017(6):6-13.
|
| [13] |
TRAN N L, SKHIRI S, ZIMÁNYI E. EQS: An Elastic and Scalable Message Queue for the Cloud[C]//IEEE. IEEE 5th International Conference on Cloud Computing Technology and Science, November 29-December 1, 2011, Athens, Greece. New Jersey: IEEE, 2011: 391-398.
|
| [14] |
ZOUNMEVO J A, AFSAHI A.An Efficient MPI Message Queue Mechanism For Large-scale Jobs[C]//IEEE. IEEE 18th International Conference on Parallel and Distributed Systems, December 17-19, 2012, Singapore. New Jersey: IEEE, 2012: 464-471.
|
| [15] |
DING Yong, XU Zheng, YE Jun, et al. Secure Outsourcing of Modular Exponentiations under Single Untrusted Programme Model[EB/OL]. .
|
| [16] |
WANG Yujue, WU Qianhong, WONG D S, et al.Securely Outsourcing Exponentiations with Single Untrusted Program for Cloud Storage[C]//Springer. 19th European Symposium on Research in Computer Security, September 7-11, 2014, Wroclaw, Poland. Heidelberg: Springer, 2014: 326-343.
|
| [17] |
李美云,李剑,黄超. 基于同态加密的可信云存储平台[J]. 信息网络安全,2012(9):35-40.
|