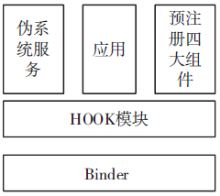
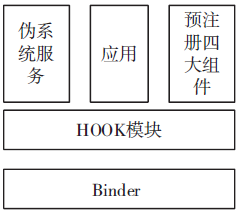
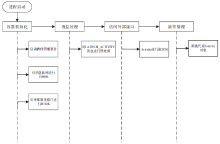
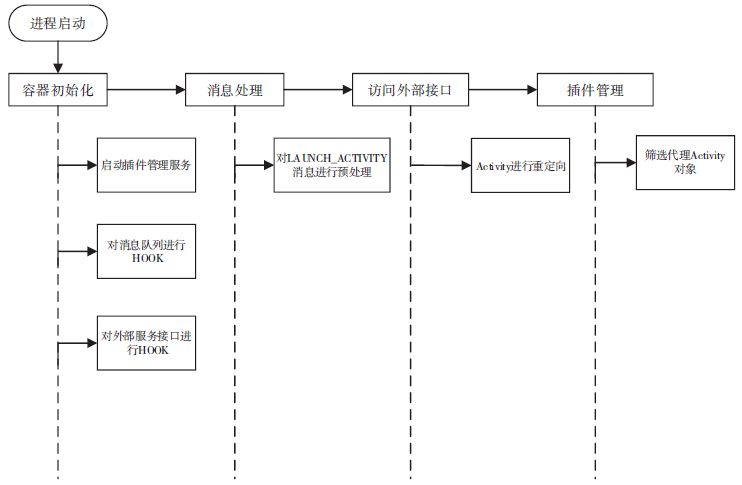
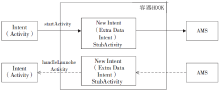
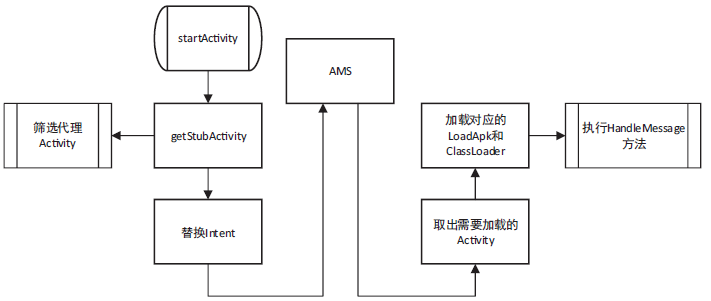
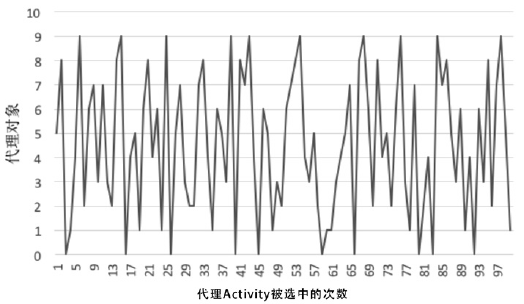
| [1] |
IDC. Smartphone OS Market Share, 2017 Q1[EB/OL].
|
| [2] |
蔡林,陈铁明. Android移动恶意代码检测的研究概述与展望[J]. 信息网络安全,2016(9):218-222.
|
| [3] |
DAI Guqian, GE Jigang, CAI Minghang, et al. SVM-based Malware Detection for Android Applications[EB/OL]. https://www.deepdyve.com/lp/association-for-computing-machinery/svm-based-malware-detection-for-android-applications-2HlS0vbpyG, 2015-6-22.
|
| [4] |
NAN Yuhong , YANG Min , YANG Zhemin , et al. UIPicker: User-input Privacy Identification in Mobile Applications[EB/OL]. .
|
| [5] |
BIANCHI A, CORBETTA J, INVERNIZZI L, et al. What the App is That? Deception and Countermeasures in the Android User Interface[EB/OL]. .
|
| [6] |
李汶洋. Android操作系统恶意软件检测技术研究[J]. 信息网络安全,2015(9):62-65.
|
| [7] |
REN Chuangang , ZHANG Yulong, XUE Hui , et al. Towards Discovering and Understanding Task Hijacking in Android[EB/OL]. .
|
| [8] |
徐强,梁彬,游伟,等. 基于SURF算法的Android恶意应用钓鱼登录界面检测[J]. 清华大学学报:自然科学版,2016(1):77-82.
|
| [9] |
SUN Mingshen, LI Mengmeng , LUI J C S , et al. DroidEagle: Seamless Detection of Visually Similar Android Apps[EB/OL]. .
|
| [10] |
余丽芳,杨天长,牛少彰. 一种增强型Android组件间安全访问控制方案[J]. 信息网络安全,2016(8):54-60.
|
| [11] |
CHEN Wenzhi, XU Lei, LI Guoxi, et al.A Lightweight Virtualization Solution for Android Devices[J]. IEEE Transactions on Computers, 2015, 64(10): 2741-2751.
|
| [12] |
YANG Zhemin, YANG Min, ZHANG Yuan, et al. AppIntent: Analyzing Sensitive Data Transmission in Android for Privacy Leakage Detection[EB/OL]. .
|
| [13] |
REN Yunlong , LI Yue, YUAN Fangfang , et al. Hijacking Activity Technology Analysis and Research in Android System[EB/OL]. .
|