信息网络安全 ›› 2023, Vol. 23 ›› Issue (12): 1-9.doi: 10.3969/j.issn.1671-1122.2023.12.001
针对品牌的网络钓鱼扩线与检测方案
- 北京大学软件与微电子学院,北京 100080
-
收稿日期:2023-08-15出版日期:2023-12-10发布日期:2023-12-13 -
通讯作者:文伟平 E-mail:weipingwen@pku.edu.cn -
作者简介:文伟平(1976—),男,湖南,教授,博士,主要研究方向为系统与网络安全、大数据与云安全、智能计算安全|朱一帆(1997—),男,湖北,硕士研究生,主要研究方向为网络与系统安全|吕子晗(1996—),男,河北,硕士研究生,主要研究方向为网络流量分析和恶意行为识别|刘成杰(1998—),男,湖南,博士研究生,主要研究方向为软件安全、漏洞挖掘和入侵检测 -
基金资助:国家自然科学基金(61872011)
Brand-Specific Phishing Expansion and Detection Solutions
WEN Weiping( ), ZHU Yifan, LYU Zihan, LIU Chengjie
), ZHU Yifan, LYU Zihan, LIU Chengjie
- School of Software and Microelectronics, Peking University, Beijing 100080, China
-
Received:2023-08-15Online:2023-12-10Published:2023-12-13
摘要:
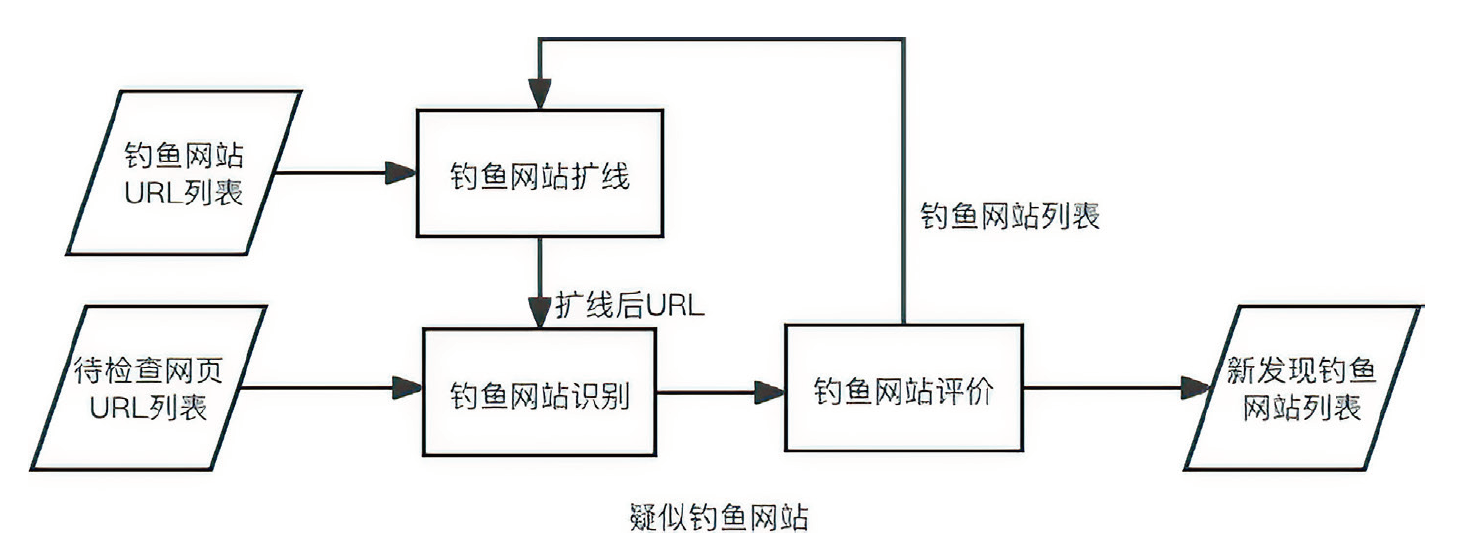
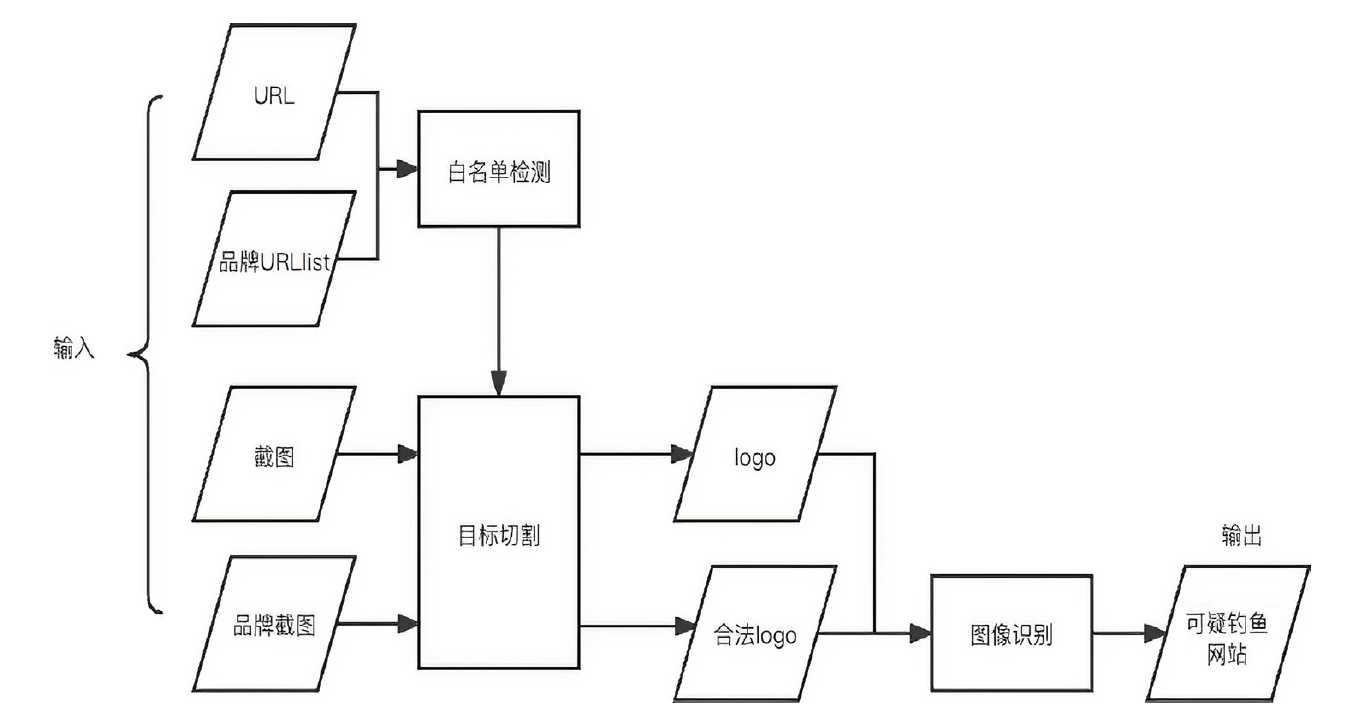
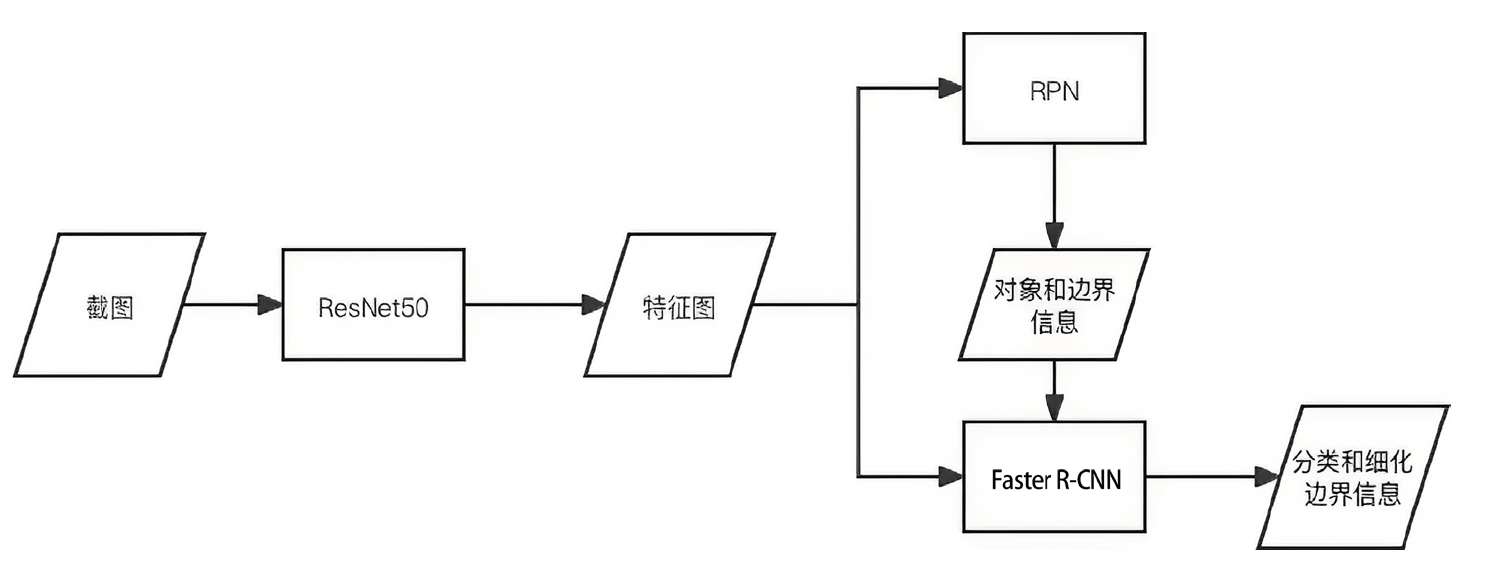
近年来,无论是钓鱼攻击的数量还是其造成的损失都在不断增加,网络钓鱼攻击成为人们面临的主要网络安全威胁之一。当前,已有许多网络钓鱼检测方法被相继提出以抵御网络钓鱼攻击,但现有钓鱼检测方法多为被动检测,且容易引起大量误报。针对上述问题,文章提出一种钓鱼扩线方法。首先,根据钓鱼网站的信息从多维度进行分析,得到与之相关的其他网站,以找到更多还未被发现的钓鱼网站;然后,针对钓鱼网站的视觉仿冒特性,提出一种基于深度学习的网络钓鱼检测方法,将截图进行切割,得到判定为logo的区域,再使用EfficientNetV2挖掘视觉仿冒特性;最后,对疑似钓鱼网站进行综合评价,以降低误报率。通过对现有钓鱼网站进行实验验证,证明了文章所提方法的有效性。
中图分类号:
引用本文
文伟平, 朱一帆, 吕子晗, 刘成杰. 针对品牌的网络钓鱼扩线与检测方案[J]. 信息网络安全, 2023, 23(12): 1-9.
WEN Weiping, ZHU Yifan, LYU Zihan, LIU Chengjie. Brand-Specific Phishing Expansion and Detection Solutions[J]. Netinfo Security, 2023, 23(12): 1-9.
| [1] | ITU. Measuring Digital Development: Facts and Figures 2022[EB/OL]. (2023-08-01)[2023-08-14]. https://www.itu.int/en/ITU-D/Statistics/Pages/facts/default.aspx. |
| [2] | HULME G V, GOODCHILD J. Social Engineering: The Basics[EB/OL]. (2010-01-14)[2023-08-14]. https://www2. cso.com.au/article/print/625643/social-engineering-basics/. |
| [3] |
CATAL C, GIRAY G, TEKINERDOGAN B, et al. Applications of Deep Learning for Phishing Detection: A Systematic Literature Review[J]. Knowledge and Information Systems, 2022, 64(6): 1457-1500.
doi: 10.1007/s10115-022-01672-x pmid: 35645443 |
| [4] | Google. Google Safe Browsing[EB/OL]. (2021-11-14)[2023-08-14]. https://safebrowsing.google.com. |
| [5] | VERMA R, DYER K. On the Character of Phishing URLs: Accurate and Robust Statistical Learning Classifiers[C]// ACM. Proceedings of the 5th ACM Conference on Data and Application Security and Privacy(CODASPY’15). New York: ACM, 2015: 111-122. |
| [6] | KARIM A, SHAHROZ M, MUSTOFA K, et al. Phishing Detection System through Hybrid Machine Learning Based on URL[J]. IEEE Access, 2023(11): 36805-36822. |
| [7] | ALJOFEY A, JIANG Qingshan, QU Qiang, et al. An Effective Phishing Detection Model Based on Character Level Convolutional Neural Network from URL[EB/OL]. (2020-09-15)[2023-08-14]. https://www.mdpi.com/2079-9292/9/9/1514. |
| [8] |
SAFI A, SINGH S. A Systematic Literature Review on Phishing Website Detection Techniques[J]. Journal of King Saud University-Computer and Information Sciences, 2023, 35(2): 590-611.
doi: 10.1016/j.jksuci.2023.01.004 URL |
| [9] |
FU A Y, LIU Wenyin, DENG Xiaotie. Detecting Phishing Web Pages with Visual Similarity Assessment Based on Earth Mover’s Distance (EMD)[J]. IEEE Transactions on Dependable and Secure Computing, 2006, 3(4): 301-311.
doi: 10.1109/TDSC.2006.50 URL |
| [10] | ABDELNABI S, KROMBHOLZ K, FRITZ M. VisualPhishNet: Zero-Day Phishing Website Detection by Visual Similarity[C]// ACM. Proceedings of the 2020 ACM SIGSAC Conference on Computer and Communications Security(CCS’20). New York: ACM, 2020: 1681-1698. |
| [11] | AFROZ S, GREENSTADT R. Phishzoo: Detecting Phishing Websites by Looking at Them[C]// IEEE. 2011 IEEE Fifth International Conference on Semantic Computing. New York: IEEE, 2011: 368-375. |
| [12] | BOZKIR A S, AYDOS M. LogoSENSE: A Companion HOG Based Logo Detection Scheme for Phishing Web Page and E-Mail Brand Recognition[EB/OL]. (2020-08-01)[2023-08-14]. https://www.sciencedirect.com/science/article/abs/pii/S0167404820301279. |
| [13] | CHANG E H, CHIEW K L, TIONG W K, et al. Phishing Detection via Identification of Website Identity[C]// IEEE. 2013 International Conference on IT Convergence and Security (ICITCS). New York: IEEE, 2013: 1-4. |
| [14] | WANG Ge, LIU He, BECERRA S, et al. Verilogo: Proactive Phishing Detection via Logo Recognition[EB/OL]. (2011-01-01)[2023-08-14]. https://hovav.net/ucsd/dist/verilogo.pdf. |
| [15] | YUN Lei, LI Dan, WANG Huanhuan. Summary of Research on Phishing Website Detection Technology[J]. Reliability and Environmental Testing of Electronic Products, 2021, 39(5): 114-119. |
| 云雷, 李丹, 王欢欢. 钓鱼网站检测技术研究综述[J]. 电子产品可靠性与环境试验, 2021, 39(5): 114-119. | |
| [16] | ASIRI S, XIAO Yang, ALZAHRANI S, et al. A Survey of Intelligent Detection Designs of HTML URL Phishing Attacks[J]. IEEE Access, 2023(11): 6421-6443. |
| [17] | BU S J, CHO S B. Deep Character-Level Anomaly Detection Based on a Convolutional Autoencoder for Zero-Day Phishing URL Detection[EB/OL]. (2021-06-17)[2023-08-14]. https://doi.org/10.3390/electronics10121492. |
| [18] | SOMESHA M, PAIS A R, RAO R S, et al. Efficient Deep Learning Techniques for the Detection of Phishing Websites[EB/OL]. (2020-06-17)[2023-08-14]. https://link.springer.com/article/10.1007/s12046-020-01392-4. |
| [19] | ADEBOWALE M A, LWIN K T, HOSSAIN M A. Intelligent Phishing Detection Scheme Using Deep Learning Algorithms[EB/OL]. (2020-06-04)[2023-08-14]. https://www.emerald.com/insight/content/doi/10.1108/JEIM-01-2020-0036/full/html. |
| [20] | HE Kaiming, ZHANG Xiangyu, REN Shaoqing, et al. Deep Residual Learning for Image Recognition[C]// IEEE. Proceedings of the IEEE Conference on Computer Vision and Pattern Recognition. New York: IEEE, 2016: 770-778. |
| [21] |
REN Shaoqing, HE Kaiming, GIRSHICK R, et al. Faster R-CNN: Towards Real-Time Object Detection with Region Proposal Networks[J]. IEEE Transactions on Pattern Analysis and Machine Intelligence, 2015, 39(6): 1137-1149.
doi: 10.1109/TPAMI.2016.2577031 URL |
| [22] | ABDILLAH R, SHUKUR Z, MOHD M, et al. Performance Evaluation of Phishing Classification Techniques on Various Data Sources and Schemes[J]. IEEE Access, 2023(11): 38721-38738. |
| [23] | TAN Mingxing, LE Q V. Efficientnetv2: Smaller Models and Faster Training[C]// PMLR. International Conference on Machine Learning. New York: PMLR, 2021: 10096-10106. |
| [24] |
DAVOUDI M R, YARI A R. Improving the Feature Section Method Based on Genetic Algorithm to Increase the Efficiency of Detecting Phishing Websites[J]. Automatic Control and Computer Sciences, 2023, 57(3): 213-221.
doi: 10.3103/S0146411623030045 |
| [25] | LIN Yun, LIU Ruofan, DIVAKARAN D M, et al. Phishpedia: A Hybrid Deep Learning Based Approach to Visually Identify Phishing Webpages[C]// USENIX. In 30th USENIX Security Symposium. Berlin:USENIX, 2021: 3793-3810. |
| [26] | WANG Jing, MIN Weiqing, HOU Sujuan, et al. Logo-2K+: A Large-Scale Logo Dataset for Scalable Logo Classification[C]// IEEE. Proceedings of the AAAI Conference on Artificial Intelligence. New York: IEEE, 2020, 34(4): 6194-6201. |
| [1] | 薛羽, 张逸轩. 深层神经网络架构搜索综述[J]. 信息网络安全, 2023, 23(9): 58-74. |
| [2] | 刘宇啸, 陈伟, 张天月, 吴礼发. 基于稀疏自动编码器的可解释性异常流量检测[J]. 信息网络安全, 2023, 23(7): 74-85. |
| [3] | 蒋英肇, 陈雷, 闫巧. 基于双通道特征融合的分布式拒绝服务攻击检测算法[J]. 信息网络安全, 2023, 23(7): 86-97. |
| [4] | 赵彩丹, 陈璟乾, 吴志强. 基于多通道联合学习的自动调制识别网络[J]. 信息网络安全, 2023, 23(4): 20-29. |
| [5] | 谭柳燕, 阮树骅, 杨敏, 陈兴蜀. 基于深度学习的教育数据分类方法[J]. 信息网络安全, 2023, 23(3): 96-102. |
| [6] | 徐占洋, 程洛飞, 程建春, 许小龙. 一种使用Bi-ADMM优化深度学习模型的方案[J]. 信息网络安全, 2023, 23(2): 54-63. |
| [7] | 陈得鹏, 刘肖, 崔杰, 仲红. 一种基于双阈值函数的成员推理攻击方法[J]. 信息网络安全, 2023, 23(2): 64-75. |
| [8] | 刘军, 武志超, 吴建, 谭振华. 一种融合图像空间特征注意力机制的恶意代码识别模型[J]. 信息网络安全, 2023, 23(12): 29-37. |
| [9] | 廖丽云, 张伯雷, 吴礼发. 基于代价敏感学习的物联网异常检测模型[J]. 信息网络安全, 2023, 23(11): 94-103. |
| [10] | 贾凡, 康舒雅, 江为强, 王光涛. 基于NLP及特征融合的漏洞相似性算法评估[J]. 信息网络安全, 2023, 23(1): 18-27. |
| [11] | 高博, 陈琳, 严迎建. 基于CNN-MGU的侧信道攻击研究[J]. 信息网络安全, 2022, 22(8): 55-63. |
| [12] | 郑耀昊, 王利明, 杨婧. 基于网络结构自动搜索的对抗样本防御方法研究[J]. 信息网络安全, 2022, 22(3): 70-77. |
| [13] | 郭森森, 王同力, 慕德俊. 基于生成对抗网络与自编码器的网络流量异常检测模型[J]. 信息网络安全, 2022, 22(12): 7-15. |
| [14] | 张郅, 李欣, 叶乃夫, 胡凯茜. 融合多重风格迁移和对抗样本技术的验证码安全性增强方法[J]. 信息网络安全, 2022, 22(10): 129-135. |
| [15] | 刘烁, 张兴兰. 基于双重注意力的入侵检测系统[J]. 信息网络安全, 2022, 22(1): 80-86. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||