信息网络安全 ›› 2022, Vol. 22 ›› Issue (9): 46-54.doi: 10.3969/j.issn.1671-1122.2022.09.006
基于BiLSTM和注意力机制的智能合约漏洞检测方案
- 1.西安电子科技大学网络与信息安全学院,西安 710071
2.河北科技大学信息科学与工程学院,石家庄 050018
-
收稿日期:2022-06-28出版日期:2022-09-10发布日期:2022-11-14 -
通讯作者:于乃文 E-mail:yunaiwen@hebust.edu.cn -
作者简介:张光华(1979—),男,河北,教授,博士,主要研究方向为网络与信息安全|刘永升(1997—),男,河北,硕士研究生,主要研究方向为网络与信息安全|王鹤(1987—),女,河南,讲师,博士,主要研究方向为应用密码和量子密码协议|于乃文(1983—),女,河北,助理研究员,硕士,主要研究方向为计算机网络管理 -
基金资助:国家自然科学基金(U1836210)
Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism
ZHANG Guanghua1,2, LIU Yongsheng2, WANG He1, YU Naiwen2( )
)
- 1. School of Cyber Engineering, Xidian University, Xi’an 710071, China
2. School of Information Science and Engineering, Hebei University of Science Technology, Shijiazhuang 050018, China
-
Received:2022-06-28Online:2022-09-10Published:2022-11-14 -
Contact:YU Naiwen E-mail:yunaiwen@hebust.edu.cn
摘要:
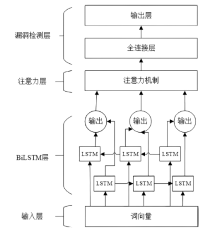
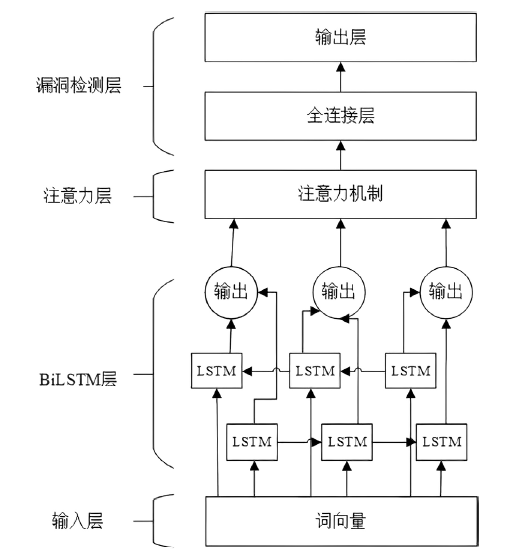
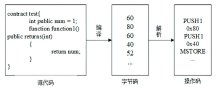
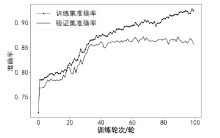
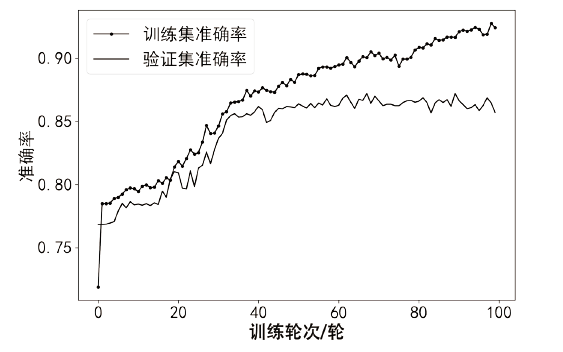
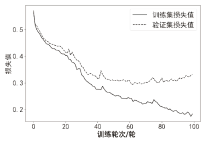
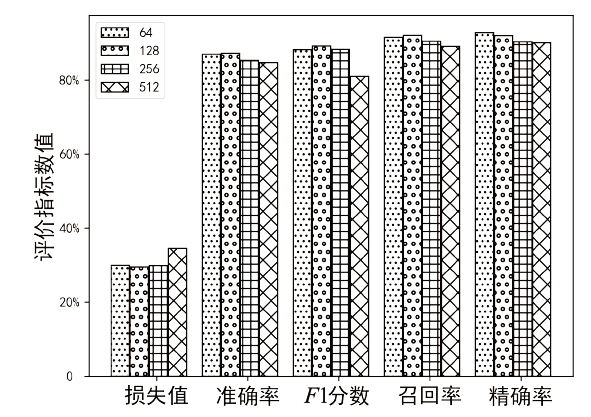
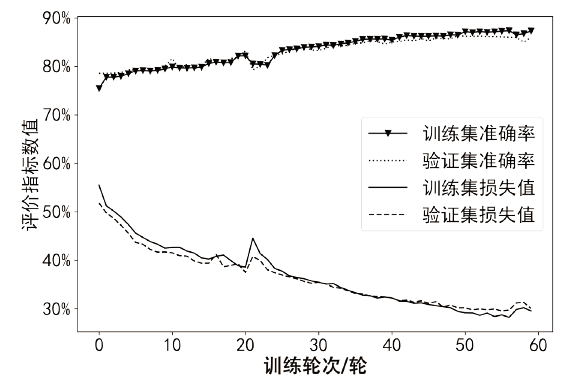
针对传统智能合约漏洞检测方案的检测准确率低以及采用深度学习的方案检测漏洞类型单一等问题,文章提出基于双向长短期记忆(Bi-Directional Long Short-Term Memory,BiLSTM)网络和注意力机制的智能合约漏洞检测方案。首先,利用Word2vec词嵌入技术对数据进行训练,通过训练获得操作码词向量表示;然后,通过将词向量传入BiLSTM来提取序列特征,并利用注意力机制为不同的特征赋予不同的权重以突出关键特征;最后,通过激活函数进行归一化处理,实现智能合约漏洞的检测与识别。文章在以太坊上收集了3000个智能合约,并利用这些合约对模型进行实验和评估。实验结果表明,与深度学习模型和传统工具相比,文章所提方案的精确率、召回率和F1分数均有一定提升,能够准确识别出4种类型的智能合约漏洞,准确率达86.34%。
中图分类号:
引用本文
张光华, 刘永升, 王鹤, 于乃文. 基于BiLSTM和注意力机制的智能合约漏洞检测方案[J]. 信息网络安全, 2022, 22(9): 46-54.
ZHANG Guanghua, LIU Yongsheng, WANG He, YU Naiwen. Smart Contract Vulnerability Detection Scheme Based on BiLSTM and Attention Mechanism[J]. Netinfo Security, 2022, 22(9): 46-54.
表4
本文模型与机器学习方案的对比结果
| 模型 | RNN[ | LSTM[ | TextCNN[ | 本文模型 | |
|---|---|---|---|---|---|
| 整数溢出 漏洞 | 精确率 | 85.64% | 86.60% | 86.16% | 94.92% |
| 召回率 | 86.22% | 89.09% | 90.52% | 91.50% | |
| F1值 | 85.93% | 87.82% | 88.29% | 93.18% | |
| 可重入漏洞 | 精确率 | 75.00% | 69.39% | 64.86% | 76.39% |
| 召回率 | 27.55% | 36.69% | 54.23% | 65.48% | |
| F1值 | 40.30% | 47.86% | 59.07% | 70.51% | |
| 以太币锁定 漏洞 | 精确率 | 65.62% | 69.84% | 74.58% | 87.95% |
| 召回率 | 46.26% | 58.15% | 53.44% | 79.76% | |
| F1值 | 54.26% | 63.46% | 62.26% | 83.65% |
表5
本文模型与传统检测方案的对比结果
| 模型 | SmartCheck[ | Mythril[ | Slither[ | 本文模型 | |
|---|---|---|---|---|---|
| 整数溢出 漏洞 | 精确率 | 33.33% | 74.64% | — | 94.92% |
| 召回率 | 30.30% | 77.94% | — | 91.50% | |
| F1值 | 31.74% | 75.82% | — | 93.18% | |
| 可重入 漏洞 | 精确率 | 39.40% | 52.30% | 35.48% | 76.39% |
| 召回率 | 41.25% | 49.69% | 42.31% | 65.48% | |
| F1值 | 40.59% | 50.98% | 38.59% | 70.51% | |
| 以太币锁定 漏洞 | 精确率 | 85.18% | — | 59.18% | 87.95% |
| 召回率 | 26.13% | — | 56.86% | 79.76% | |
| F1值 | 39.98% | — | 57.99% | 83.65% |
| [1] | SZABO N. Smart Contracts: Building Blocks for Digital Markets[J]. EXTROPY: The Journal of Transhumanist Thought, 1996, 18(2): 28-30. |
| [2] | HU Tianyuan, LI Zecheng, LI Bixin, et al. Contractual Security and Privacy Security of Smart Contract: A System Mapping Study[J]. Chinese Journal of Computers, 2021, 44(12): 2485-2514. |
| 胡甜媛, 李泽成, 李必信, 等. 智能合约的合约安全和隐私安全研究综述[J]. 计算机学报, 2021, 44(12): 2485-2514. | |
| [3] | YANG Zheng, LEI Hang. Lolisa: Formal Syntax and Semantics for a Subset of the Solidity Programming Language in Mathematical Tool Coq[EB/OL]. (2018-05-27)[2022-05-25]. https://arxiv.org/abs/1803.09885. |
| [4] | MEHAR M I, SHIER C L, GIAMBATTISTA A, et al. Understanding a Revolutionary and Flawed Grand Experiment in Blockchain: The DAO Attack[J]. Journal of Cases on Information Technology (JCIT), 2019, 21(1): 19-32. |
| [5] | PALLADINO S. The Parity Wallet Hack Explained[EB/OL]. (2017-07-19)[2022-05-25]. https://blog.openzeppelin.com/on-the-parity-wallet-multisig-hack-405a8c12e8f7. |
| [6] | HESSENAUER S. Batch Overflow Bug on Ethereum ERC20 Token Contracts and SafeMath[EB/OL]. (2018-04-26)[2022-05-25]. http://blog.matryx.ai/batch-overflow-bug-on-ethereum-erc20-token-contracts-and-safemath-f9ebcc137434. |
| [7] | LUU L, CHU D H, OLICKEL H, et al. Making Smart Contracts Smarter[C]// ACM. 2016 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2016: 254-269. |
| [8] | NIKOLIC I, KOLLURI A, SERGEY I, et al. Finding the Greedy, Prodigal, and Suicidal Contracts at Scale[C]// ACM. 34th Annual Computer Security Applications Conference. New York: ACM, 2018: 653-663. |
| [9] | TORRES C F, SCHÜTTE J, STATE R. Osiris: Hunting for Integer Bugs in Ethereum Smart Contracts[C]// ACM. 34th Annual Computer Security Applications Conference. New York: ACM, 2018: 664-676. |
| [10] | MUELLER B. MYTHRIL: A Framework for Bug Hunting on the Ethereum Blockchain[EB/OL]. (2017-07-11)[2022-05-25]. https://mythx.io/. |
| [11] | TSANKOV P, DAN A, DRACHSLER C D, et al. Securify: Practical Security Analysis of Smart Contracts[C]// ACM. 2018 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2018: 67-82. |
| [12] | JIANG Bo, LIU Ye, CHAN W K. Contractfuzzer: Fuzzing Smart Contracts for Vulnerability Detection[C]// IEEE. 2018 33rd IEEE/ACM International Conference on Automated Software Engineering (ASE). New York: IEEE, 2018: 259-269. |
| [13] | HE Jingxuan, BALUNOVIĆ M, AMBROLADZE N, et al. Learning to Fuzz from Symbolic Execution with Application to Smart Contracts[C]// ACM. 2019 ACM SIGSAC Conference on Computer and Communications Security. New York: ACM, 2019: 531-548. |
| [14] | NGUYEN T D, PHAM L H, SUN Jun, et al. sFuzz: An Efficient Adaptive Fuzzer for Solidity Smart Contracts[C]// ACM. ACM/IEEE 42nd International Conference on Software Engineering. New York: ACM, 2020: 778-788. |
| [15] | LIANAN. VaaS: Automated Formal Verification Platform for Smart Contract[EB/OL]. (2019-07-03)[2022-05-11]. https://www.lianantech.com/. |
| [16] | AMANI S, BÉGEL M, BORTIN M, et al. Towards Verifying Ethereum Smart Contract Bytecode in Isabelle/HOL[C]// ACM. 7th ACM SIGPLAN International Conference on Certified Programs and Proofs. New York: ACM, 2018: 66-77. |
| [17] | FEIST J, GRIECO G, GROCE A. Slither: A Static Analysis Framework for Smart Contracts[C]// IEEE. 2019 IEEE/ACM 2nd International Workshop on Emerging Trends in Software Engineering for Blockchain(WETSEB). New York: IEEE, 2019: 8-15. |
| [18] | TIKHOMIROV S, VOSKRESENSKAYA E, IVANITSKIY I, et al. Smartcheck: Static Analysis of Ethereum Smart Contracts[C]// ACM. 1st International Workshop on Emerging Trends in Software Engineering for Blockchain. New York: ACM, 2018: 9-16. |
| [19] | QIAN Peng, LIU Zhenguang, HE Qinming, et al. Towards Automated Reentrancy Detection for Smart Contracts Based on Sequential Models[J]. IEEE Access, 2020(8): 19685-19695. |
| [20] | TANN W J W, HAN Xingjie, GUPTA S S, et al. Towards Safer Smart Contracts: A Sequence Learning Approach to Detecting Security Threats[EB/OL]. (2018-11-16)[2022-05-25]. https://arxiv.org/abs/1811.06632v3. |
| [21] | SUN Yuhang, GU Lize. Attention-Based Machine Learning Model for Smart Contract Vulnerability Detection[EB/OL]. (2021-01-15)[2022-05-25]. https://iopscience.iop.org/article/10.1088/1742-6596/1820/1/012004. |
| [22] | WANG Wei, SONG Jingjing, XU Guangquan, et al. Contractward: Automated Vulnerability Detection Models for Ethereum Smart Contracts[J]. IEEE Transactions on Network Science and Engineering, 2020, 8(2): 1133-1144. |
| [23] | YU Xingxin, ZHAO Haoyue, HOU Botao, et al. DeeSCVHunter: A Deep Learning-Based Framework for Smart Contract Vulnerability Detection[C]// IEEE. 2021 International Joint Conference on Neural Networks (IJCNN). New York: IEEE, 2021: 1-8. |
| [24] | MIKOLOV T, CHEN Kai, CORRADO G, et al. Efficient Estimation of Word Representations in Vector Space[EB/OL]. (2013-01-16)[2022-05-25]. https://arxiv.org/abs/1301.3781. |
| [25] | HOCHREITER S, SCHMIDHUBER J. Long Short-Term Memory[J]. Neural Computation, 1997, 9(8): 1735-1780. |
| [26] | BAHDANAU D, CHO K, BENGIO Y. Neural Machine Translation by Jointly Learning to Align and Translate[EB/OL]. (2014-09-01)[2022-05-25]. https://arxiv.org/abs/1409.0473v7. |
| [27] | ALBERT E, GORDILLO P, LIVSHITS B, et al. Ethir: A Framework for High-Level analysis of Ethereum Bytecode[C]// Springer. International Symposium on Automated Technology for Verification and Analysis. Heidelberg: Springer, 2018: 513-520. |
| [28] | ZAREMBA W, SUTSKEVER I, VINYALS O. Recurrent Neural Network Regularization[EB/OL]. (2014-09-08)[2022-05-25]. https://arxiv.org/abs/1409.2329. |
| [29] | KIM Y. Convolutional Neural Networks for Sentence Classification[EB/OL]. (2014-08-25)[2022-05-25]. https://arxiv.org/abs/1408.5882v2. |
| [1] | 张玉健, 刘代富, 童飞. 基于局部图匹配的智能合约重入漏洞检测方法[J]. 信息网络安全, 2022, 22(8): 1-7. |
| [2] | 胡艺, 佘堃. 基于区块链和智能合约的双链车联网系统[J]. 信息网络安全, 2022, 22(8): 26-35. |
| [3] | 黄保华, 赵伟宏, 彭丽, 谢统义. 基于MPT索引的高效链上PKI模型[J]. 信息网络安全, 2022, 22(8): 72-80. |
| [4] | 王健, 黄俊. 基于智能合约的日志安全存储与公平访问方法[J]. 信息网络安全, 2022, 22(7): 27-36. |
| [5] | KELEKET GOMA Christy Junior Yannick, 易文哲, 王鹃. 一种基于SGX的轻量Fabric链码可信执行环境构建方法[J]. 信息网络安全, 2022, 22(7): 73-83. |
| [6] | 王姝爽, 马兆丰, 刘嘉微, 罗守山. 区块链跨链安全接入与身份认证方案研究与实现[J]. 信息网络安全, 2022, 22(6): 61-72. |
| [7] | 于克辰, 郭莉, 阴宏伟, 燕雪松. 面向数据中心场景的基于区块链与博弈论的高价值数据共享模型[J]. 信息网络安全, 2022, 22(6): 73-85. |
| [8] | 华景煜, 黄达明. 以太坊智能合约定理证明中的形式化规约研究综述[J]. 信息网络安全, 2022, 22(5): 11-20. |
| [9] | 冯景瑜, 张琪, 黄文华, 韩刚. 基于跨链交互的网络安全威胁情报共享方案[J]. 信息网络安全, 2022, 22(5): 21-29. |
| [10] | 刘嘉微, 马兆丰, 王姝爽, 罗守山. 基于区块链的隐私信用数据受限共享技术研究[J]. 信息网络安全, 2022, 22(5): 54-63. |
| [11] | 崔皓宇, 马利民, 王佳慧, 张伟. 基于区块链的属性加密多授权机构安全模型研究[J]. 信息网络安全, 2022, 22(5): 84-93. |
| [12] | 石润华, 王树豪, 李坤昌. V2G中一种轻量级的跨域双向认证方案[J]. 信息网络安全, 2022, 23(3): 20-28. |
| [13] | 陈彬杰, 魏福山, 顾纯祥. 基于KNN的具有隐私保护功能的区块链异常交易检测[J]. 信息网络安全, 2022, 23(3): 78-84. |
| [14] | 张光华, 闫风如, 张冬雯, 刘雪峰. 基于LSTM-Attention的内部威胁检测模型[J]. 信息网络安全, 2022, 22(2): 1-10. |
| [15] | 王健, 张蕴嘉, 刘吉强, 陈志浩. 基于区块链的司法数据管理及电子证据存储机制[J]. 信息网络安全, 2022, 22(2): 21-31. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||