信息网络安全 ›› 2021, Vol. 21 ›› Issue (9): 59-66.doi: 10.3969/j.issn.1671-1122.2021.09.009
遗传算法优化CNN的网站指纹攻击方法
- 中国人民公安大学信息网络安全学院,北京 100038
-
收稿日期:2021-05-16出版日期:2021-09-10发布日期:2021-09-22 -
通讯作者:蔡满春 E-mail:caimanchun@ppsuc.edu.cn -
作者简介:李彦霖(1997—),男,广西,硕士研究生,主要研究方向为信息网络安全|蔡满春(1972—),男,河北,副教授,博士,主要研究方向为密码学与通信保密|芦天亮(1985—),男,河北,副教授,博士,主要研究方向为恶意代码与人工智能安全|席荣康(1997—),男,河南,硕士研究生,主要研究方向为匿名通信 -
基金资助:“十三五”国家密码发展基金密码理论研究重点课题(MMJJ20180108);中国人民公安大学2019年基本科研业务费重大项目(2019JKF108)
A Website Fingerprinting Attack Method via Convolutional Neural Network Optimized by Genetic Algorithm
LI Yanlin, CAI Manchun( ), LU Tianliang, XI Rongkang
), LU Tianliang, XI Rongkang
- College of Information Network Security, People’s Public Security University of China, Beijing 100038, China
-
Received:2021-05-16Online:2021-09-10Published:2021-09-22 -
Contact:CAI Manchun E-mail:caimanchun@ppsuc.edu.cn
摘要:
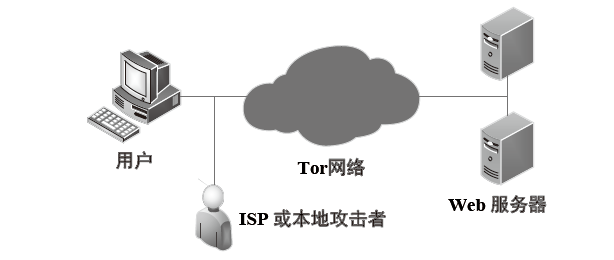
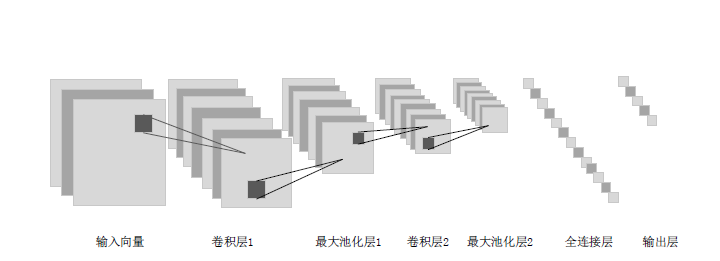
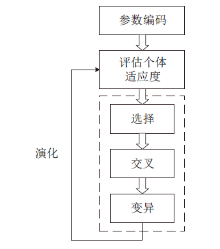
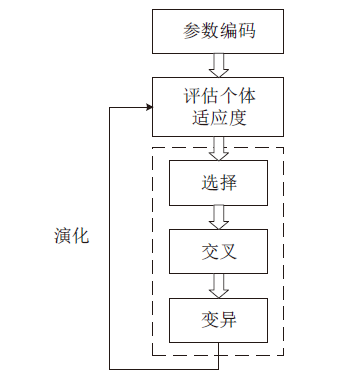
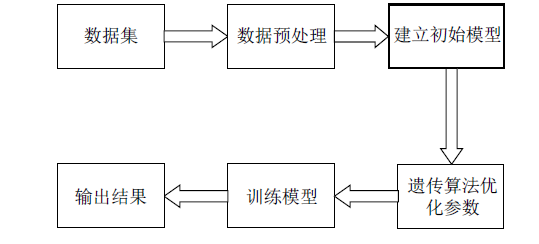
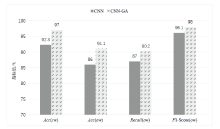
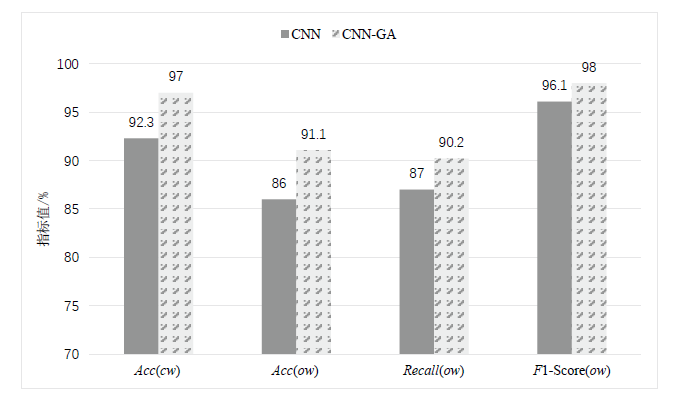
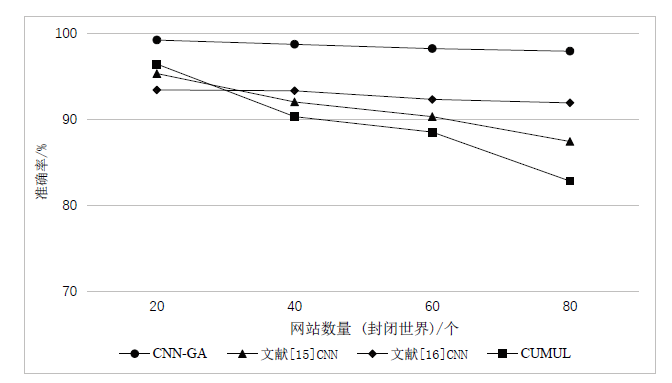
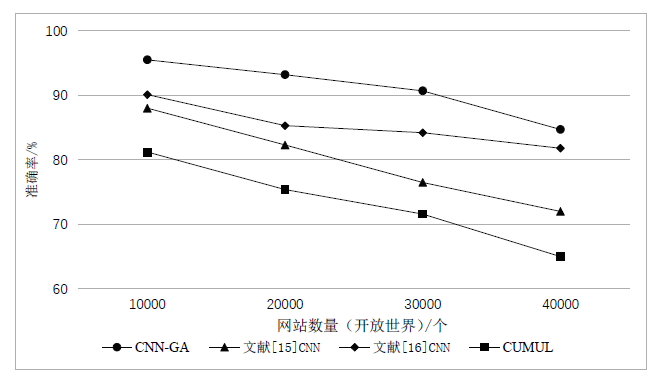
网站指纹攻击常用来分析Tor网络的用户访问行为,分析效果受限于构造指纹的流量特征集。经过手动特征工程和特征选择,可以得到一组代表该攻击方式的指纹特征。随着Tor网络协议的更新,手工提取的流量特征可能失效。文章提出一种遗传算法优化卷积神经网络的网站指纹攻击方法,实现流量特征的自动提取,并与已有的指纹攻击研究比较,在封闭世界数据集和开放世界数据集中,文章所提方法的识别准确率有一定提升。
中图分类号:
引用本文
李彦霖, 蔡满春, 芦天亮, 席荣康. 遗传算法优化CNN的网站指纹攻击方法[J]. 信息网络安全, 2021, 21(9): 59-66.
LI Yanlin, CAI Manchun, LU Tianliang, XI Rongkang. A Website Fingerprinting Attack Method via Convolutional Neural Network Optimized by Genetic Algorithm[J]. Netinfo Security, 2021, 21(9): 59-66.
| [1] | HERRMANN D, WENDOLSKY R, FEDERRATH H. Website Fingerprinting: Attacking Popular Privacy Enhancing Technologies with the Multinomial Naïve-Bayes Classifier [C]//ACM. CCS ’09: 16th ACM Conference on Computer and Communications Security 2009, November 13, 2009, Chicago, Illinois, USA. New York: ACM, 2009: 31-42. |
| [2] | CAI Xiang, NITHYANAND R, WANG Tao, et al. A Systematic Approach to Developing and Evaluating Website Fingerprinting Defenses [C]//ACM. CCS’14: 2014 ACM SIGSAC Conference on Computer and Communications Security, November 3-7, 2014, Scottsdale, Arizona, USA. New York: ACM, 2014: 227-238. |
| [3] | JUAREZ M, AFROZ S, ACAR G, et al. A Critical Evaluation of Website Fingerprinting Attacks [C]// ACM. CCS’14: 2014 ACM SIGSAC Conference on Computer and Communications Security, November 3-7, 2014, Scottsdale, Arizona, USA. New York: ACM, 2014: 263-274. |
| [4] | CHENG H, AVNUR R. Traffic Analysis of SSL Encrypted Web Browsing[EB/OL]. https://citeseerx.ist.psu.edu/viewdoc/download?doi=10.1.1.3.1201&rep=rep1&type=pdf, 2021-01-19. |
| [5] | SUN Qixiang, SIMON D R, WANG Yimin, et al. Statistical Identification of Encrypted Web Browsing Traffic [C]//IEEE. 2002 IEEE Symposium on Security and Privacy, May 12-15, 2002, Berkeley, CA, USA. Washington, D. C: IEEE, 2002: 19-30. |
| [6] | LIBERATORE M, LEVINE B N. Inferring the Source of Encrypted Http Connections [C]//ACM. CCS’06: 13th ACM Conference on Computer and Communications Security 2006, October 30-November 3, 2006, Alexandria, Virginia, USA. New York: ACM, 2006: 255-263. |
| [7] | PANCHENKO A, NIESSEN L, ZINNEN A, et al. Website Fingerprinting in Onion Routing Based Anonymization Networks [C]//ACM. CCS’11: the ACM Conference on Computer and Communications Security Proceedings of the 10th annual ACM workshop on Privacy in the Electronic Society, October 17, 2011, Chicago, Illinois, USA. New York: ACM, 2011: 103-114. |
| [8] | CAI Xiang, ZHANG Xincheng, JOSHI B, et al. Touching from a Distance: Website Fingerprinting Attacks and Defenses [C]//ACM. CCS’12: the ACM Conference on Computer and Communications Security, October 16-18, 2012, Raleigh, North Carolina, USA. New York: ACM, 2012: 605-616. |
| [9] | WANG Tao, GOLDBERG I. Improved Website Fingerprinting on Tor [C]//ACM. CCS'13: 2013 ACM SIGSAC Conference on Computer and Communications Security, November 4, 2013, Berlin, Germany. New York: ACM, 2013: 201-212. |
| [10] | WANG Tao, CAI Xiang, NITHYANAND R, et al. Effective Attacks and Provable Defenses for Website Fingerprinting [C]//USENIX. 23rd USENIX Security Symposium, August 20-22, 2014, San Diego, CA, USA. CA: USENIX, 2014: 143-157. |
| [11] | PANCHENKO A, LANZE F, PENNEKAMP J, et al. Website Fingerprinting at Internet Scale[EB/OL]. https://orbilu.uni.lu/handle/10993/24117, 2021-01-22. |
| [12] | HAYES J, DANEZIS G. K-Fingerprinting: A Robust Scalable Website Fingerprinting Technique [C]//USENIX. 25th USENIX Security Symposium, August 10-12, 2016, Austin, Texas, USA. CA: USENIX, 2016: 1187-1203. |
| [13] | WANG Zhanyi. The Applications of Deep Learning on Traffic Identification[J]. BlackHat USA, 2015, 24(11): 1-10. |
| [14] | ABE K, GOTO S. Fingerprinting Attack on Tor Anonymity Using Deep Learning[J]. Proceedings of the Asia-Pacific Advanced Network, 2016, 42(4): 15-20. |
| [15] | RIMMER V, PREUVENEERS D, JUAREZ M, et al. Automated Website Fingerprinting Through Deep Learning[EB/OL]. https://arxiv.org/abs/1708.06376, 2021-01-25. |
| [16] | SIRINAM P, IMANI M, JUAREZ M, et al. Deep Fingerprinting: Undermining Website Fingerprinting Defenses with Deep Learning [C]//ACM. CCS’18: 2018 ACM SIGSAC Conference on Computer and Communications Security, October 15-19, 2018, Toronto, Canada. New York: ACM, 2018: 1928-1943. |
| [17] | BHAT S, LU D, KWON A, et al. Var-cnn: A Data-efficient Website Fingerprinting Attack Based on Deep Learning[EB/OL]. https://dspace.mit.edu/handle/1721.1/129817, 2021-02-25. |
| [18] | RAHMAN M S, SIRINAM P, MATHEWS N, et al. Tik-Tok: The Utility of Packet Timing in Website Fingerprinting Attacks[EB/OL]. https://arxiv.org/abs/1902.06421, 2021-02-27. |
| [19] | MA Chencheng, DU Xuehui, CAO Lifeng, et al. Burst-Analysis Website Fingerprinting Attack Based on Deep Neural Network[J]. Journal of Computer Research and Development, 2020, 57(4): 746. |
| 马陈城, 杜学绘, 曹利峰, 等. 基于深度神经网络 burst 特征分析的网站指纹攻击方法[J]. 计算机研究与发展, 2020, 57(4): 746. |
| [1] | 弋晓洋, 张健. 基于图像的网络钓鱼邮件检测方法研究[J]. 信息网络安全, 2021, 21(9): 52-58. |
| [2] | 李桥, 龙春, 魏金侠, 赵静. 一种基于LMDR和CNN的混合入侵检测模型[J]. 信息网络安全, 2020, 20(9): 117-121. |
| [3] | 王湘懿, 张健. 基于图像和机器学习的虚拟化平台异常检测[J]. 信息网络安全, 2020, 20(9): 92-96. |
| [4] | 刘静, 张学谦, 刘全明. 混合Gabor的轻量级卷积神经网络的验证码识别研究[J]. 信息网络安全, 2020, 20(7): 77-84. |
| [5] | 张蕾华, 黄进, 张涛, 王生玉. 视频侦查中人像智能分析应用及算法优化[J]. 信息网络安全, 2020, 20(5): 88-93. |
| [6] | 王蓉, 马春光, 武朋. 基于联邦学习和卷积神经网络的入侵检测方法[J]. 信息网络安全, 2020, 20(4): 47-54. |
| [7] | 顾兆军, 郝锦涛, 周景贤. 基于改进双线性卷积神经网络的恶意网络流量分类算法[J]. 信息网络安全, 2020, 20(10): 67-74. |
| [8] | 龙敏, 龙啸海, 马莉. 基于深度卷积神经网络的指纹活体检测算法研究[J]. 信息网络安全, 2018, 18(6): 28-35. |
| [9] | 赵旭, 黄光球, 崔艳鹏, 王明明. 基于改进选择算子的NIDS多媒体包多线程择危处理模型[J]. 信息网络安全, 2018, 18(10): 45-50. |
| [10] | 夏玉明, 胡绍勇, 朱少民, 刘丽丽. 基于卷积神经网络的网络攻击检测方法研究[J]. 信息网络安全, 2017, 17(11): 32-36. |
| [11] | 胡青, 刘本永. 基于卷积神经网络分类的说话人识别算法[J]. 信息网络安全, 2016, 16(4): 55-60. |
| [12] | 郝文江;李思其;丁文纯. 遗传算法在社交网站数据分析中的应用[J]. , 2013, 13(2): 0-0. |
| [13] | 薛琴. BP神经网络在入侵检测系统中的应用研究[J]. , 2011, 11(11): 0-0. |
| [14] | 杨晓勇. 混沌遗传算法在优化问题中的应用[J]. , 2011, 11(10): 0-0. |
| [15] | 赵光耀;邹鹏;韩伟红. 基于遗传算法和LSSVM的网络安全事件发生频率预测[J]. , 2010, (10): 0-0. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||