信息网络安全 ›› 2021, Vol. 21 ›› Issue (7): 43-53.doi: 10.3969/j.issn.1671-1122.2021.07.006
基于关键载荷截取的SQL注入攻击检测方法
郭春1,2, 蔡文艳1,2, 申国伟1,2( ), 周雪梅1,2
), 周雪梅1,2
- 1.贵州大学计算机科学与技术学院,贵阳 550025
2.贵州省软件工程与信息安全特色重点实验室,贵阳 550025
-
收稿日期:2021-03-31出版日期:2021-07-10发布日期:2021-07-23 -
通讯作者:申国伟 E-mail:gwshen@gzu.edu.cn -
作者简介:郭春(1986—),男,湖南,副教授,博士,主要研究方向为入侵检测、恶意代码检测和数据挖掘|蔡文艳(1995—),女,贵州,硕士研究生,主要研究方向为网络与信息安全|申国伟(1986—),男,湖南,副教授,博士,主要研究方向为知识图谱、恶意代码检测和数据挖掘|周雪梅(1977—),女,贵州,讲师,硕士,主要研究方向为网络安全和入侵检测技术 -
基金资助:国家自然科学基金(62062022);贵州省科学技术基金(黔科合基础[2017]1051)
Research on SQL Injection Attacks Detection Method Based on the Truncated Key Payload
GUO Chun1,2, CAI Wenyan1,2, SHEN Guowei1,2( ), ZHOU Xuemei1,2
), ZHOU Xuemei1,2
- 1. College of Computer Science and Technology, Guizhou University, Guiyang 550025, China
2. Guizhou Provincial Key Laboratory of Software Engineering and Information Security, Guiyang 550025, China
-
Received:2021-03-31Online:2021-07-10Published:2021-07-23 -
Contact:SHEN Guowei E-mail:gwshen@gzu.edu.cn
摘要:
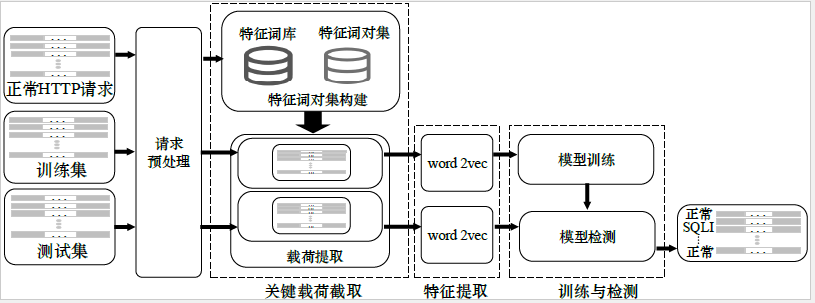
SQL注入攻击是黑客对数据库进行攻击的常用手段之一,对当前Web应用程序安全构成了重大威胁。针对由于SQL注入攻击语句与正常HTTP请求语句之间存在较多相同字符串而影响分类准确性的问题,文章在分析SQL注入攻击全过程中各阶段攻击语句和正常HTTP请求语句区别的基础上,提出了一种基于特征词对的关键载荷截取方法。该方法能够从SQL注入攻击语句中截取出区别于正常HTTP请求语句的关键载荷。结合自然语言处理技术、所截取的关键载荷、word2vec和分类算法,文章构建了一种基于关键载荷截取的SQL注入攻击检测方法并搭建Web系统对其进行了实验测试。实验结果表明,该方法在检测准确性和检测效率上均优于基于完整请求和word2vec的SQL注入攻击检测方法。
中图分类号:
引用本文
郭春, 蔡文艳, 申国伟, 周雪梅. 基于关键载荷截取的SQL注入攻击检测方法[J]. 信息网络安全, 2021, 21(7): 43-53.
GUO Chun, CAI Wenyan, SHEN Guowei, ZHOU Xuemei. Research on SQL Injection Attacks Detection Method Based on the Truncated Key Payload[J]. Netinfo Security, 2021, 21(7): 43-53.
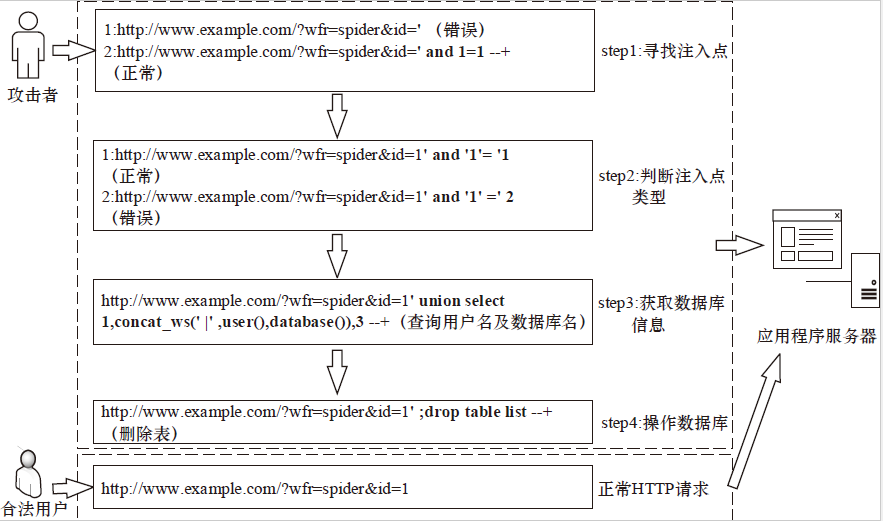
表1
正常请求与各阶段攻击语句及特点对比
| 阶段 | 请求及特点 | 与正常HTTP请求相同的 字符数 | 与正常HTTP请求不同的 字符数 |
|---|---|---|---|
| 正常HTTP请求 | | - | - |
| 寻找注入点 | 1: | 38 | 1 |
| 2: | 38 | 13 | |
| 则判断参数id为注入点 | |||
| 判断注入点类型 | 1: | 39 | 12 |
| 2: | 39 | 12 | |
| 根据错误提示syntax to use near ''1'') LIMIT 0,1' at line 1,则判断为单引号字符型注入点。 | |||
| 获取数据库信息 | | 39 | 55 |
| 成功返回的当前用户和数据库名称 | |||
| 操作 数据库 | | 39 | 21 |
| 删除整个list表 | |||
| [1] | OWASP Top10-open Web Application Security Project. Top Ten Web Application Security Risks[EB/OL]. http://www.owasp.org.cn/owasp-project/OWASPTop102017RC1V1.0.pdf, 2021-03-08. |
| [2] | JACOB I, PIRNAU M. SQL Injection Attacks and Vulnerabilities[J]. Journal of Information Systems & Operations Management, 2020, 14(1):68-81. |
| [3] |
ABIKOYE O C, ABUBAKAR A, DOKORO A H, et al. A Novel Technique to Prevent SQL Injection and Cross-site Scripting Attacks Using Knuth-morris-pratt String Match Algorithm[J]. Eurasip Journal on Information Security, 2020, 2020(1):1-14.
doi: 10.1186/s13635-020-0101-7 URL |
| [4] | JAHANSHAHI R, DOUPÉ A, EGELE M. You Shall Not Pass: Mitigating SQL Injection Attacks on Legacy Web Applications[C]// SIGSAC. The 15th ACM Asia Conference on Computer and Communications Security, October 5, 2020, Taibei, China. New York: Association for Computing Machinery, 2020: 445-457. |
| [5] |
DAS D, SHARMA U, BHATTACHARYYA D K. Defeating SQL Injection Attack in Authentication Security: An Experimental Study[J]. International Journal of Information Security, 2019, 18(1):1-22.
doi: 10.1007/s10207-017-0393-x URL |
| [6] | DAN G. Rookie Coding Mistake Prior to Gab Hack Came from Site’S CTO[EB/OL]. https://arstechnica.com/gadgets/2021/03/rookie-coding-mistake-prior-to-gab-hack-came-from-sites-cto/?comments=1, 2021-03-03. |
| [7] | GUO Qiquan, ZHANG Haixia. Technology System for Security Protection of Critical Information Infrastructures[J]. Netinfo Security, 2020, 20(11):1-9. |
| 郭启全, 张海霞. 关键信息基础设施安全保护技术体系[J]. 信息网络安全, 2020, 20(11):1-9. | |
| [8] | NADEEM R M, SALEEM R M, BASHIR R, et al. Detection and Prevention of SQL Injection Attack by Dynamic Analyzer and Testing Model[J]. International Journal of Advanced Computer Science and Applications, 2017, 8(8):209-214. |
| MCWHIRTER P R, KIFAYAT K, SHI Q, et al. SQL Injection Attack Classification Through The Feature Extraction of SQL Query Strings Using a Gap-weighted String Subsequence Kernel[J]. Journal of Information Security and Applications, 2018, 18(40):199-216. | |
| [9] | JANA A, MAITY D. Code-based Analysis Approach to Detect and Prevent SQL Injection Attacks[C]// IEEE. 2020 11th International Conference on Computing, Communication and Networking Technologies (ICCCNT), July 1-3, 2020, Kharagpur, India. Piscataway, New Jersey: IEEE, 2020: 1-6. |
| [10] | ZHANG Yajun, LI Zhoujun, LIAO Xiangke, et al. Research on Automated White Box Fuzzy Testing Technology[J]. Computer Science, 2014, 41(2):7-10. |
| 张亚军, 李舟军, 廖湘科, 等. 自动化白盒模糊测试技术研究[J]. 计算机科学, 2014, 41(2):7-10. | |
| [11] |
ALIERO M S, GHANI I, QURESHI K N, et al. An Algorithm For Detecting SQL Injection Vulnerability Using Black-box Testing[J]. Journal of Ambient Intelligence and Humanized Computing, 2020, 11(1):249-266.
doi: 10.1007/s12652-019-01235-z URL |
| [12] | HLAING Z CS S, KHAING M. A Detection and Prevention Technique on SQL Injection Attacks[C]// IEEE. 2020 IEEE Conference on Computer Applications (ICCA), February 27-28, 2020, Yangon, Myanmar. Piscataway, New Jersey: IEEE, 2020: 1-6. |
| [13] | WANG Jie. Research on SQL Injection Defense Based on Abstract Syntax Tree[D]. Wu Han: Wuhan Research Institute of Posts and Telecommunications, 2018. |
| 王杰. 基于抽象语法树的SQL注入防御研究[D]. 武汉:武汉邮电科学研究院, 2018. | |
| [14] | TANG Peng, QIU Weidong, HUANG Zheng, et al. Detection of SQL Injection Based on Artificial Neural Network[J]. Knowledge-based Systems, 2020,20, (190):105528. |
| [15] | MCWHIRTER P R, KIFAYAT K, SHI Q, et al. SQL Injection Attack Classification Through the Feature Extraction of SQL Query Strings Using A Gap-weighted String Subsequence Kernel[J]. Journal of Information Security and Applications, 2018, 18(40):199-216. |
| [16] | CHEN Ding, YAN Qiseng, WU Chunwang, et al. SQL Injection Attack Detection and Prevention Techniques Using Deep Learning[C]// Kehua Guo.International Conference on Computer Big Data and Artificial Intelligence (ICCBDAI 2020), October 24-25, 2020, Changsha, China. Britain: IOP Publishing, 2021: 12-55. |
| [17] | SHARMA S, ZAVARSKY P, BUTAKOV S. Machine Learning Based Intrusion Detection System for Web-based Attacks[C]// IEEE. 2020 IEEE 6th Intl Conference on Big Data Security on Cloud (Big Data Security), May 25-27, 2020, Baltimore, MD, USA. New York: IEEE, 2020: 227-230. |
| [18] | HASAN M, BALBAHAITH Z, TARIQUE M. Detection of SQL Injection Attacks: A Machine Learning Approach[C]// IEEE. 2019 International Conference on Electrical and Computing Technologies and Applications (ICECTA), November 19-21, 2019, Ras Al Khaimah, United Arab Emirates. New York: IEEE, 2019: 1-6. |
| [19] | LI Yuan, WANG Guoyin, LI Zhixing, et al. Convolutional Neural Network Anomaly Detection Based on Sequence Attention Mechanism[J]. Journal of Zhengzhou University (Natural Science Edition), 2019, 51(2):20-25. |
| 李苑, 王国胤, 李智星, 等. 基于序列注意力机制的卷积神经网络异常检测[J]. 郑州大学学报(理学版), 2019, 51(2):20-25. | |
| [20] | LI Qi, WANG Fang, WANG Junfeng, et al. LSTM-based SQL Injection Detection Method for Intelligent Transportation System[J]. IEEE Transactions on Vehicular Technology, 2019, 68(5):4182-4191. |
| [21] | LI Ming, XING Guangsheng, WANG Zhihui, et al. Research on real-time online intelligent detection technology of SQL injection behavior[J]. Journal of Hunan University(Natural Sciences), 2020, 47(8):31-41. |
| 李铭, 邢光升, 王芝辉, 等. SQL注入行为实时在线智能检测技术研究[J]. 湖南大学学报(自然科学版), 2020, 47(8):31-41. | |
| [22] | ZHANG Huafeng, ZHAO Bo, YUAN Hui, et al. SQL Injection Detection Based on Deep Belief Network[C]// Ali Emrouznejad. The 3rd International Conference on Computer Science and Application Engineering, October 22, 2019, Sanya, China. New York: Association for Computing Machinery, 2019: 1-6. |
| [23] | GUPTA S, KHARE V. BlazingText: Scaling and Accelerating Word2vec using Multiple GPUs[C]// IEEE. The International Conference for High Performance Computing, Networking, Storage and Analysis, November 12, 2017, Denver, CO, USA. New York: Association for Computing Machinery, 2017: 1-5. |
| [24] | CASELLESD H, LESAINT F, ROYOL J. Word2vec Applied to Recommendation: Hyperparameters Matter[C]// RecSys. The 12th ACM Conference on Recommender Systems, October 2, 2018, Vancouver British Columbia, Canada. New York: Association for Computing Machinery, 2018: 352-356. |
| [25] | ASGHARI M, SIERRAS D, ELMAGHR A. Trends on Health in Social Media: Analysis Using Twitter Topic Modeling[C]// IEEE. 2018 IEEE International Symposium on Signal Processing and Information Technology (ISSPIT), December 6-8, 2018, Louisville, KY, USA. New York: IEEE, 2018: 558-563. |
| [1] | 徐瑜, 周游, 林璐, 张聪. 无监督机器学习在游戏反欺诈领域的应用研究[J]. 信息网络安全, 2020, 20(9): 32-36. |
| [2] | 郭春, 陈长青, 申国伟, 蒋朝惠. 一种基于可视化的勒索软件分类方法[J]. 信息网络安全, 2020, 20(4): 31-39. |
| [3] | 杜义峰, 郭渊博. 一种基于信任值的雾计算动态访问控制方法[J]. 信息网络安全, 2020, 20(4): 65-72. |
| [4] | 马泽文, 刘洋, 徐洪平, 易航. 基于集成学习的DoS攻击流量检测技术[J]. 信息网络安全, 2019, 19(9): 115-119. |
| [5] | 陈冠衡, 苏金树. 基于深度神经网络的异常流量检测算法[J]. 信息网络安全, 2019, 19(6): 68-75. |
| [6] | 田春岐, 李静, 王伟, 张礼庆. 一种基于机器学习的Spark容器集群性能提升方法[J]. 信息网络安全, 2019, 19(4): 11-19. |
| [7] | 胡建伟, 赵伟, 闫峥, 章芮. 基于机器学习的SQL注入漏洞挖掘技术的分析与实现[J]. 信息网络安全, 2019, 19(11): 36-42. |
| [8] | 张健, 陈博翰, 宫良一, 顾兆军. 基于图像分析的恶意软件检测技术研究[J]. 信息网络安全, 2019, 19(10): 24-31. |
| [9] | 文伟平, 李经纬, 焦英楠, 李海林. 一种基于随机探测算法和信息聚合的漏洞检测方法[J]. 信息网络安全, 2019, 19(1): 1-7. |
| [10] | 于颖超, 丁琳, 陈左宁. 机器学习系统面临的安全攻击及其防御技术研究[J]. 信息网络安全, 2018, 18(9): 10-18. |
| [11] | 张阳, 姚原岗. 基于Xgboost算法的网络入侵检测研究[J]. 信息网络安全, 2018, 18(9): 102-105. |
| [12] | 文伟平, 吴勃志, 焦英楠, 何永强. 基于机器学习的恶意文档识别工具设计与实现[J]. 信息网络安全, 2018, 18(8): 1-7. |
| [13] | 和湘, 刘晟, 姜吉国. 基于机器学习的入侵检测方法对比研究[J]. 信息网络安全, 2018, 18(5): 1-11. |
| [14] | 陈红松, 王钢, 宋建林. 基于云计算入侵检测数据集的内网用户异常行为分类算法研究[J]. 信息网络安全, 2018, 18(3): 1-7. |
| [15] | 段桂华, 申卓祥, 申东杰, 李智. 一种基于特征提取的有效下载链接识别方案研究[J]. 信息网络安全, 2018, 18(10): 31-36. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||