信息网络安全 ›› 2021, Vol. 21 ›› Issue (4): 81-88.doi: 10.3969/j.issn.1671-1122.2021.04.009
基于议价贝叶斯博弈模型的防欺诈策略
- 1.青岛大学计算机科学技术学院,青岛 266071
2.中国海洋大学信息科学与工程学院,青岛 266100
-
收稿日期:2021-01-16出版日期:2021-04-10发布日期:2021-05-14 -
通讯作者:程相国 E-mail:15964252399@163.com -
作者简介:任航(1997—),女,山东,硕士研究生,主要研究方向为众包计算、网络安全|程相国(1969—),男,山东,教授,博士,主要研究方向为密码学、信息安全|张睿(1995—),女,山东,硕士研究生,主要研究方向为对抗攻击、网络安全|夏辉(1986—),男,山东,教授,博士,主要研究方向为众包计算、对抗攻击、物联网安全。 -
基金资助:国家自然科学基金(61872205);山东省自然科学基金(ZR2019MF018);青岛市应用基础研究计划(18-2-2-56-jch)
A Novel Fraud Prevention Strategy Based on Bargaining Bayesian Game Model
REN Hang1, CHENG Xiangguo1( ), ZHANG Rui2, XIA Hui2
), ZHANG Rui2, XIA Hui2
- 1. College of Computer Science and Technology, Qingdao University, Qingdao 266071, China
2. College of Information Science and Engineering, Ocean University of China, Qingdao 266100, China
-
Received:2021-01-16Online:2021-04-10Published:2021-05-14 -
Contact:CHENG Xiangguo E-mail:15964252399@163.com
摘要:
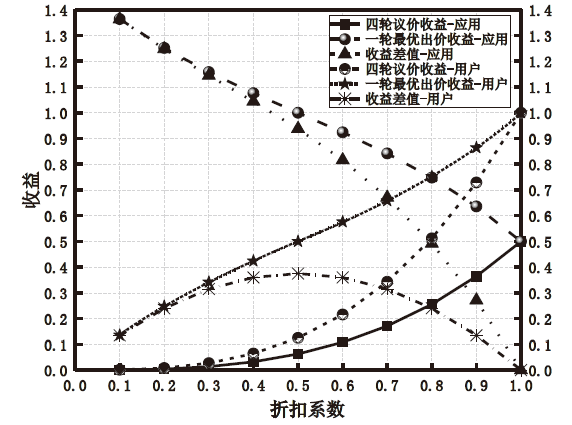
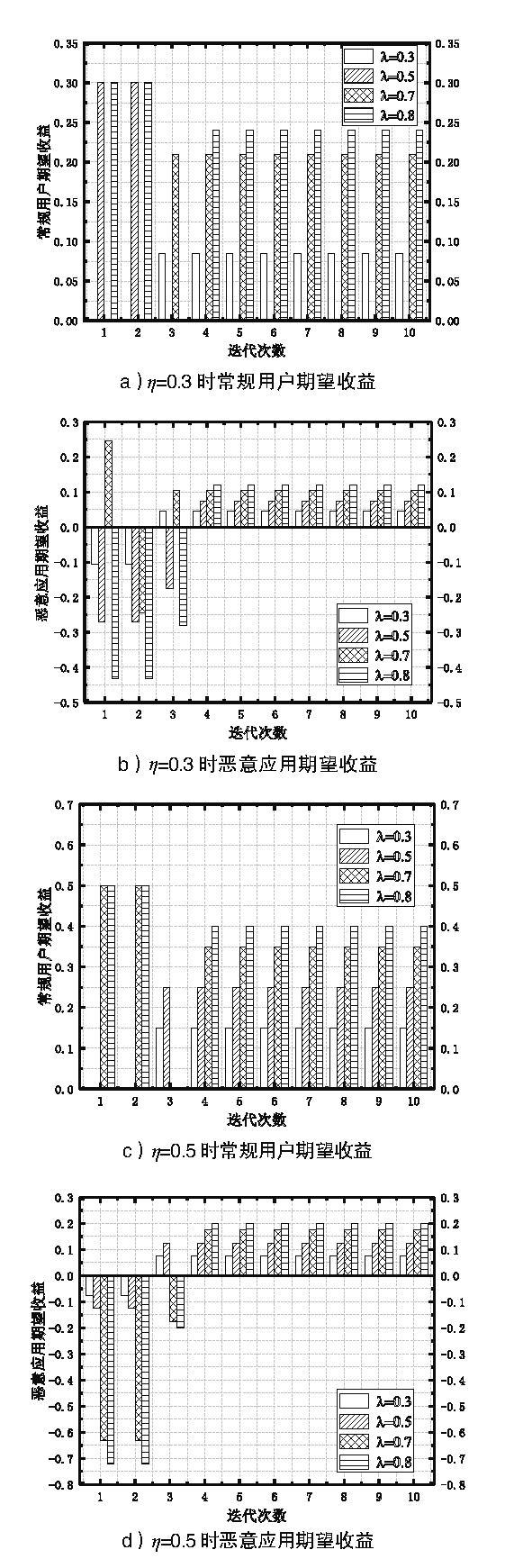
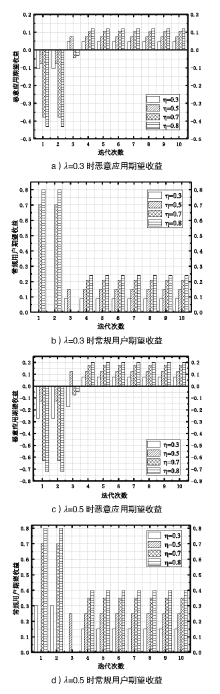
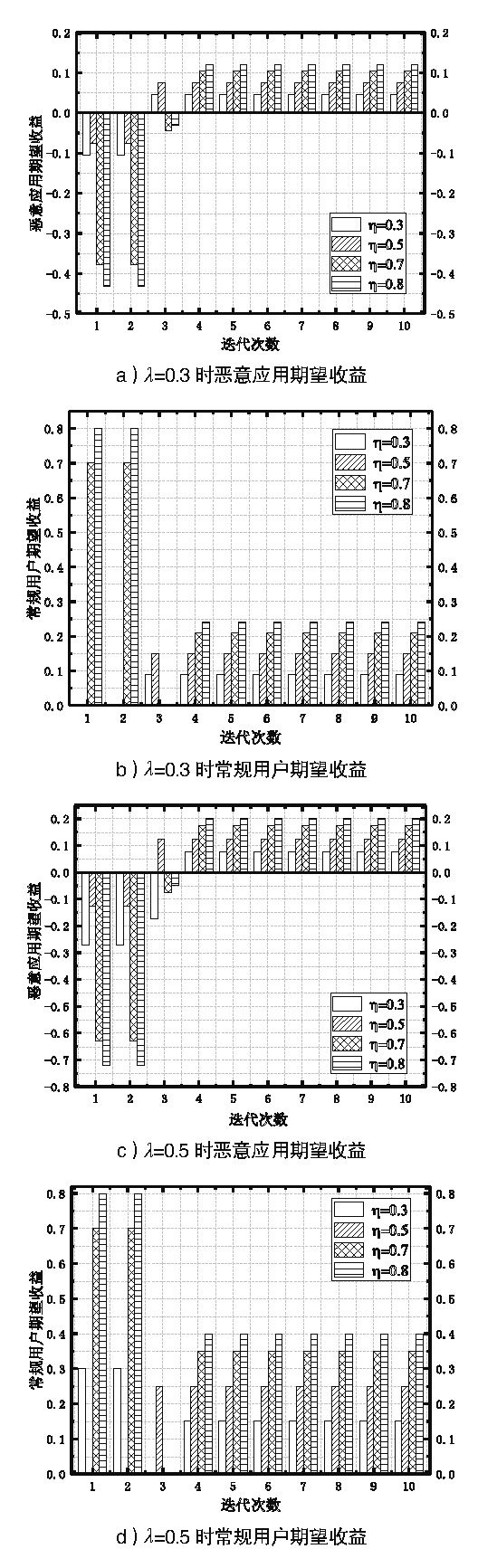
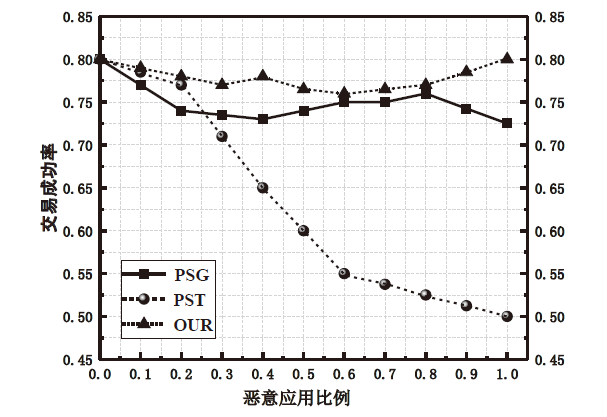
多媒体信息易遭受敌手攻击,如恶意应用通过虚假报价来欺诈未采取防护措施的用户,导致用户财产或隐私面临极大的威胁。为解决上述问题,文章提出一种基于议价贝叶斯博弈模型的防欺诈策略来保护用户隐私。首先利用四轮讨价还价确定应用和用户交互时的收益矩阵,引入常规用户的检测率对收益矩阵进行调整,抑制恶意应用虚假报价;然后通过贝叶斯纳什均衡分析确定用户的最优防御策略以防止用户遭受恶意应用的欺骗,避免个人隐私泄露。仿真结果表明,文章方案提高了应用和用户在交易达成时各自的收益,降低了恶意应用采取欺骗策略的概率,增强了用户隐私的安全性。
中图分类号:
引用本文
任航, 程相国, 张睿, 夏辉. 基于议价贝叶斯博弈模型的防欺诈策略[J]. 信息网络安全, 2021, 21(4): 81-88.
REN Hang, CHENG Xiangguo, ZHANG Rui, XIA Hui. A Novel Fraud Prevention Strategy Based on Bargaining Bayesian Game Model[J]. Netinfo Security, 2021, 21(4): 81-88.
| [1] |
CALLSNAN C, JERMAN B, BLAZIC A J. User Awareness and Tolerance of Privacy Abuse on Mobile Internet: An Exploratory Study[J]. Telematics and Informatics, 2016,33(1):109-128.
doi: 10.1016/j.tele.2015.04.009 URL |
| [2] | KIRNER-LUDWIG M C. Creation, Dissemination and Uptake of Fake-quotes in Lay Political Discourse on Facebook and Twitter[EB/OL]. http://apps.webofknowledge.com/full_record.do?product=UA&search_mode=GeneralSearch&qid=2&SID=8DrGRLng7MjX1mVH2x4&page=1&doc=1, 2021-01-05. |
| [3] | TIWARI N, SARDAR A S. Advancements in Reversible Data Hiding Techniques: A Review[J]. International Journal of Computer Science and Network Security, 2017,17(3):195-205. |
| [4] | LONG Min, ZHAO Yu, ZHANG Xiang, et al. A Separable Reversible Data Hiding Scheme for Encrypted Images Based on TrominoScrambling and Adaptive Pixel Value Ordering[EB/OL]. http://apps.webofknowledge.com/full_record.do?product=UA&search_mode=GeneralSearch&qid=18&SID=8DrGRLng7MjX1mVH2x4&page=1&doc=1, 2021-01-03. |
| [5] | KAUR G, SINGH S, RANI R, et al. A Comprehensive Study of Reversible Data Hiding (RDH) Schemes Based on Pixel Value Ordering (PVO)[EB/OL]. http://apps.webofknowledge.com/full_record.do?product=UA&search_mode=GeneralSearch&qid=22&SID=8DrGRLng7MjX1mVH2x4&page=1&doc=1, 2021-01-03. |
| [6] | YUAN Ziqian, GUAN Zijie, FENG Hao. An Improved Information Hiding Algorithm Based on Image[C]// IEEE. 2017 IEEE 15th International Conference on Software Engineering Research, Management and Applications, June 7-9, 2017, London, UK. NJ: IEEE, 2017: 169-172. |
| [7] | OU Bo, SHI Xianglian. Reversible Data Hiding for Three-dimensional Image Based on Depth No-synjournal-error Model[J]. Netinfo Security, 2018,18(5):24-31. |
| 欧博, 石向莲. 基于深度无合成误差模型的三维图像可逆信息隐藏方法研究[J]. 信息网络安全, 2018,18(5):24-31. | |
| [8] |
MOHANARATHINAM A, KAMALRAJ S, VENKATESAN G, et al. Digital Watermarking Techniques for Image Security: A Review[J]. Journal of Ambient Intelligence and Humanized Computing, 2020,11(8):3221-3229.
doi: 10.1007/s12652-019-01500-1 URL |
| [9] | LIU Yang, TANG Shanyu, LIU Ran, et al. Secure and Robust Digital Image Watermarking Scheme Using Logistic and RSA Encryption[EB/OL]. http://apps.webofknowledge.com/full_record.do?product=UA&search_mode=GeneralSearch&qid=35&SID=8DrGRLng7MjX1mVH2x4&page=1&doc=1, 2018-05-01. |
| [10] | MAMIDI R, DADHICH G, DSOUZA E, et al. Novel Algorithm for Embedding Audio Watermark in Images[C]// IEEE. 3rd International Conference on Computing for Sustainable Global Development, March 16-18, 2016, New Delhi, India. New York: IEEE, 2016: 2654-2659. |
| [11] | NAGTODE S A, KORDE S A. Splicing Detection Technique for Images[C]// Springer. Vaigai College of Engineering. International Conference on Computer Networks, Big Data and IoT, December 19-20, 2018, Madurai, India. Switzerland: Springer International Publishing Ag, 2020: 654-660. |
| [12] | LI Ce, MA Qiang, XIAO Limei, et al. Image Splicing Detection Based on Markov Features in QDCTDomain[EB/OL]. http://apps.webofknowledge.com/full_record.do?product=UA&search_mode=GeneralSearch&qid=46&SID=8DrGRLng7MjX1mVH2x4&page=1&doc=2, 2017-03-08. |
| [13] | VAMSI K, CHADHA R, RAMKUMAR B, et al. Image Splicing Detection Using HMRF Superpixel Segmentation[C]// IEEE. 2017 7th International Conference on Communication Systems and Network Technologies, November 11-13, 2017, Nagpur, India. New York: IEEE, 2018: 177-182. |
| [14] | WANG Shunfei, YAN Junhua, WANG Zhigang. Improved Moving Object Detection Algorithm Based on Local United Feature[J]. Chinese Journal of Scientific Instrument, 2015,36(10):2241-2248. |
| 王顺飞, 闫钧华, 王志刚. 改进的基于局部联合特征的运动目标检测方法[J]. 仪器仪表学报, 2015,36(10):2241-2248. | |
| [15] | ZHANG Yang, LIU Tingwen, SHA Hongzhou, et al. Malicious Domain Detection Based on Multiple-dimensional Features[J]. Journal of Computer Applications, 2016,36(004):941-944. |
| 张洋, 柳厅文, 沙泓州, 等. 基于多元属性特征的恶意域名检测[J]. 计算机应用, 2016,36(004):941-944. | |
| [16] | YUILL J J, JAMES J. Defensive Computer-security Deception Operations: Processes, Principles and Techniques[D]. North Carolina: North Carolina State University, 2006. |
| [17] | HAN Xiao, KHEIR N, BALZAOTTI D. Deception Techniques in Computer Security: A Research Perspective[J]. ACM Computing Surveys, 2018,51(4):36. |
| [18] | ALMESHEKAH M H, SPAFFORD E H. Cyber Security Deception[M]. West-berlin: Springer International Publishing, 2016. |
| [19] | URIAS V E, STOUT W M S LUC-WATSON J. et al. Technologies to Enable Cyber Deception[C]// IEEE. 2017 International Carnahan Conference on Security Technology, October 23-26, 2017, Madrid, SPAIN. New York: IEEE, 2017: 1-6. |
| [20] | WANG Changchun, SHI Changhui, WANG Chong, et al. An Analyzing Method for Computer Network Security Based on Markov Game Model[C]// IEEE. 2016 IEEE Advanced Information Management, Communicates, Electronic and Automation Control Conference, October 3-5, 2016, Xi'an, China. New York: IEEE, 2017: 454-458. |
| [21] | ATTIAH A, CHATTERJEE M, ZOU C C. A Game Theoretic Approach to Model Cyber Attack and Defense Strategies[C]// IEEE. 2018 IEEE International Conference on Communications, May 20-24, 2018, Kansas City, MO, USA. New York: IEEE, 2018: 1-7. |
| [22] | LIU Qilie, LIU Maosong, LI Yun, et al. Novel Game-based Incentive Strategy for opportunistic networks[J]. Application Research of Computers, 2015,32(7):2128-2132. |
| 刘期烈, 刘茂松, 李云, 等. 基于博弈论的机会网络激励机制的研究[J]. 计算机应用研究, 2015,32(7):2128-2132. |
| [1] | 王健, 赵曼莉, 陈志浩, 石波. 基于假名的智能交通条件隐私保护认证协议[J]. 信息网络安全, 2021, 21(4): 49-61. |
| [2] | 周由胜, 王明, 刘媛妮. 支持区间查询的基于位置服务外包数据隐私保护方案[J]. 信息网络安全, 2021, 21(3): 26-36. |
| [3] | 路宏琳, 王利明. 面向用户的支持用户掉线的联邦学习数据隐私保护方法[J]. 信息网络安全, 2021, 21(3): 64-71. |
| [4] | 刘峰, 杨杰, 齐佳音. 基于哈希证明系统的区块链两方椭圆曲线数字签名算法研究[J]. 信息网络安全, 2021, 21(1): 19-26. |
| [5] | 汪金苗, 谢永恒, 王国威, 李易庭. 基于属性基加密的区块链隐私保护与访问控制方法[J]. 信息网络安全, 2020, 20(9): 47-51. |
| [6] | 李宁波, 周昊楠, 车小亮, 杨晓元. 云环境下基于多密钥全同态加密的定向解密协议设计[J]. 信息网络安全, 2020, 20(6): 10-16. |
| [7] | 张佳程, 彭佳, 王雷. 大数据环境下的本地差分隐私图信息收集方法[J]. 信息网络安全, 2020, 20(6): 44-56. |
| [8] | 肖彪, 闫宏强, 罗海宁, 李炬成. 基于差分隐私的贝叶斯网络隐私保护算法的改进研究[J]. 信息网络安全, 2020, 20(11): 75-86. |
| [9] | 何泾沙, 杜晋晖, 朱娜斐. 基于k匿名的准标识符属性个性化实现算法研究[J]. 信息网络安全, 2020, 20(10): 19-26. |
| [10] | 黄保华, 程琪, 袁鸿, 黄丕荣. 基于距离与误差平方和的差分隐私K-means聚类算法[J]. 信息网络安全, 2020, 20(10): 34-40. |
| [11] | 唐春明, 林旭慧. 隐私保护集合交集计算协议[J]. 信息网络安全, 2020, 20(1): 9-15. |
| [12] | 汪金苗, 王国威, 王梅, 朱瑞瑾. 面向雾计算的隐私保护与访问控制方法[J]. 信息网络安全, 2019, 19(9): 41-45. |
| [13] | 郝文江, 林云. 互联网企业社会责任现状与启示研究[J]. 信息网络安全, 2019, 19(9): 130-133. |
| [14] | 周权, 许舒美, 杨宁滨. 一种基于ABGS的智能电网隐私保护方案[J]. 信息网络安全, 2019, 19(7): 25-30. |
| [15] | 李怡霖, 闫峥, 谢皓萌. 车载自组织网络的隐私保护综述[J]. 信息网络安全, 2019, 19(4): 63-72. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||