信息网络安全 ›› 2025, Vol. 25 ›› Issue (7): 1032-1043.doi: 10.3969/j.issn.1671-1122.2025.07.003
简洁低交互的物联网设备认证协议研究
- 1.泉城实验室,济南 250103
2.山东大学网络空间安全学院,青岛 266237
-
收稿日期:2024-12-13出版日期:2025-07-10发布日期:2025-08-07 -
通讯作者:王梅 E-mail:wangmeiz@sdu.edu.cn -
作者简介:王梅(1990—),女,山东,助理研究员,博士,CCF会员,主要研究方向为隐私增强计算与安全认证|杨潇然(2001—),女,山东,硕士研究生,主要研究方向为安全认证及其应用|李增鹏(1989—),男,山东,副研究员,博士,CCF会员,主要研究方向为同态加密与安全多方计算 -
基金资助:国家自然科学基金(62472255);国家自然科学基金(62302271);山东省高等学校青创科技支持计划(2024KJH79);山东省自然科学基金(ZR2023MF045);山东省自然科学基金(ZR2023QF088);青岛市自然科学基金(23-2-1-152-zyyd-jch)
Research on Simple and Low Interaction Authentication Protocols for IoT Devices
WANG Mei1,2( ), YANG Xiaoran2, LI Zengpeng1,2
), YANG Xiaoran2, LI Zengpeng1,2
- 1. Quan Cheng Laboratory, Jinan 250103, China
2. School of Cyber Science and Technology, Shandong University, Qingdao 266237, China
-
Received:2024-12-13Online:2025-07-10Published:2025-08-07 -
Contact:WANG Mei E-mail:wangmeiz@sdu.edu.cn
摘要:
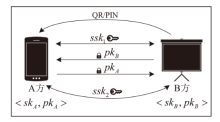
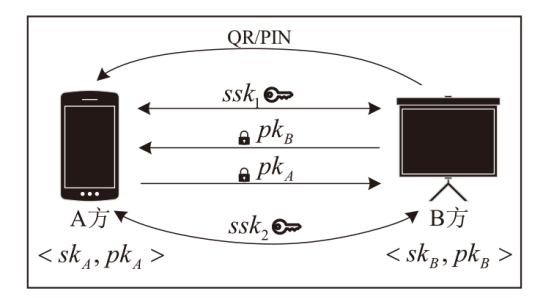
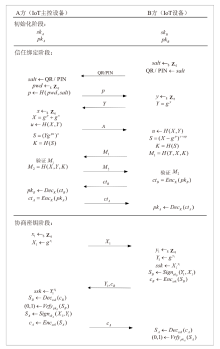
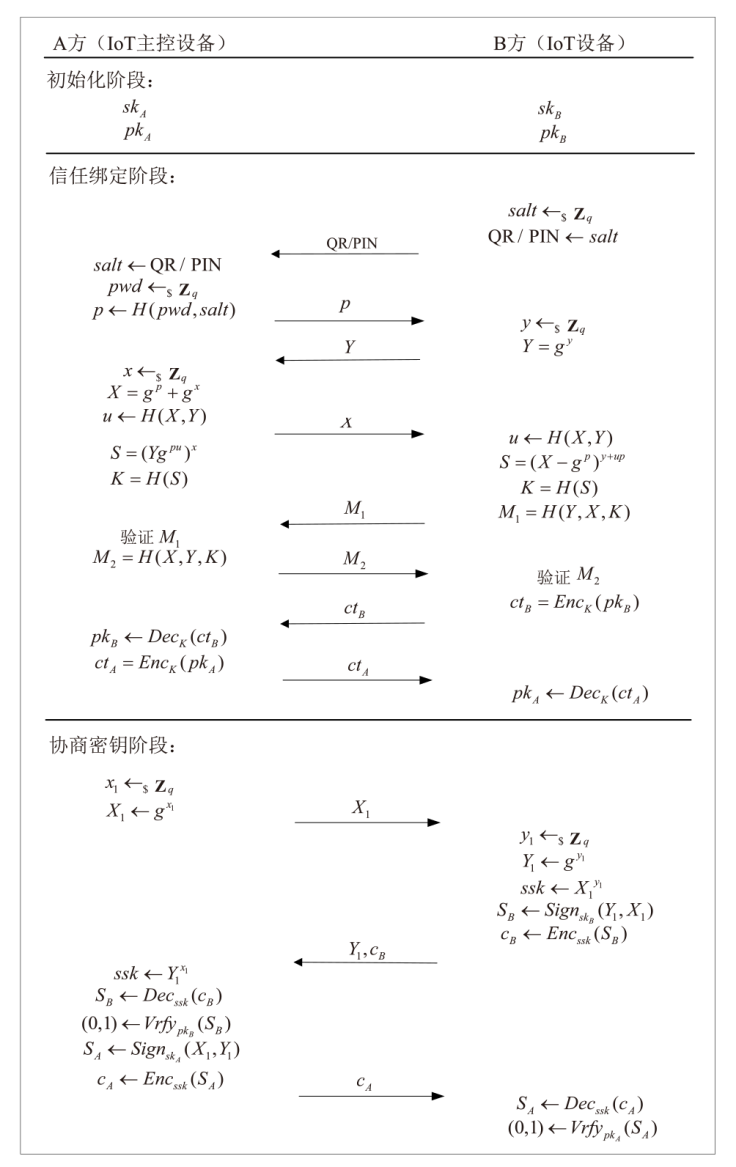
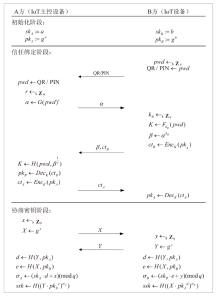
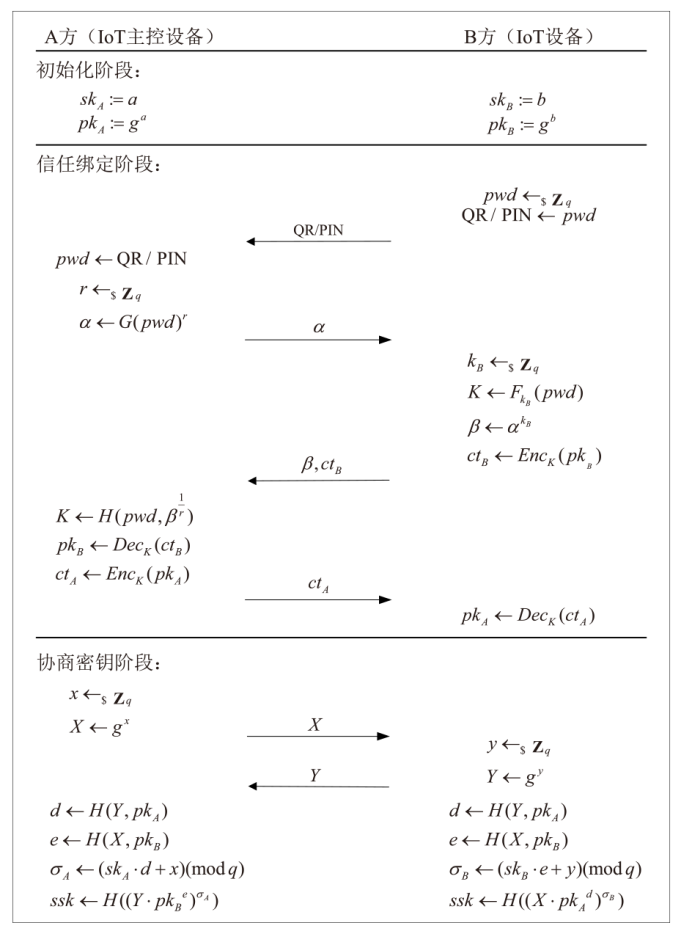
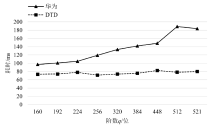
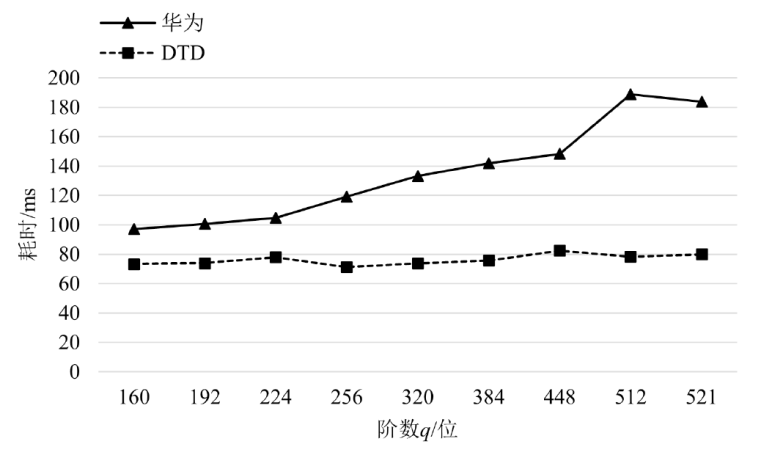
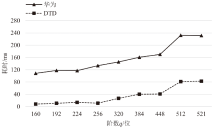
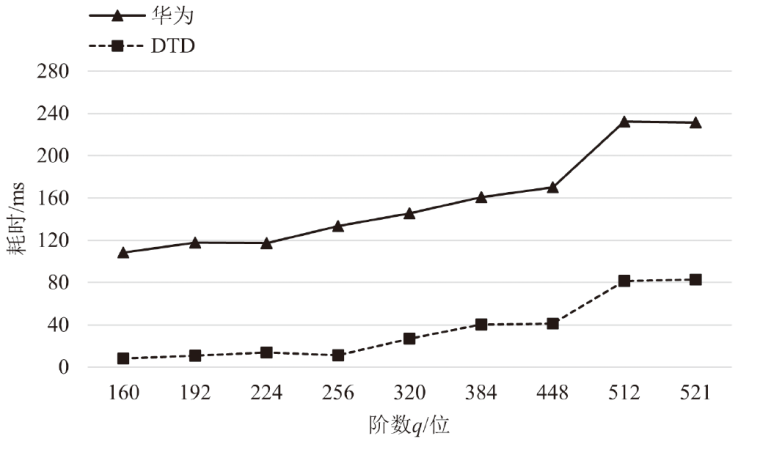
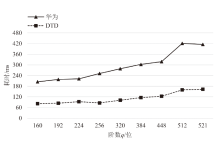
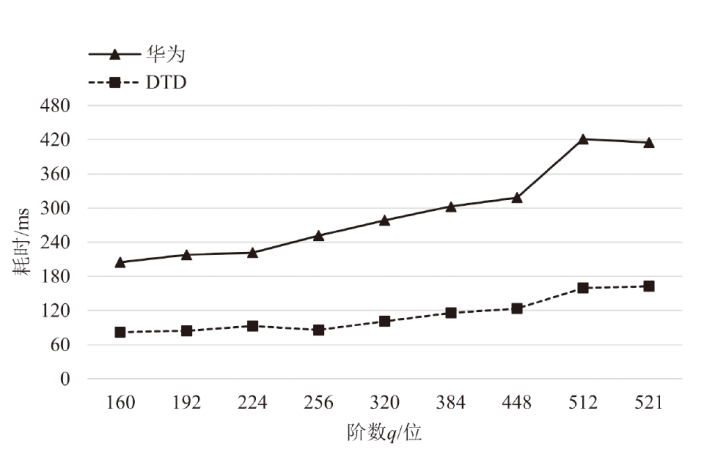
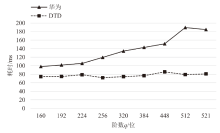
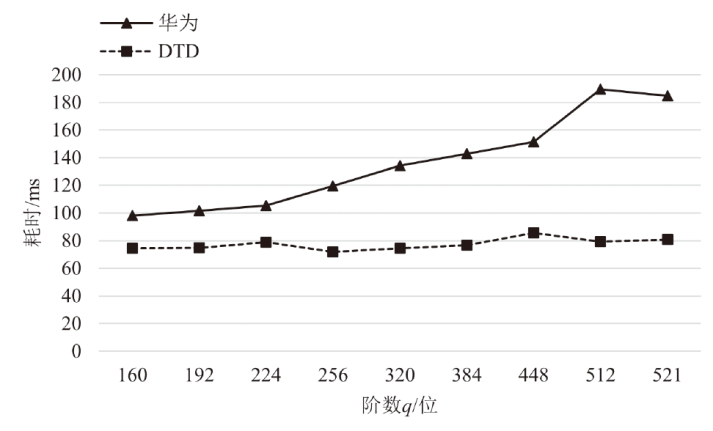
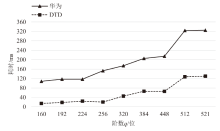
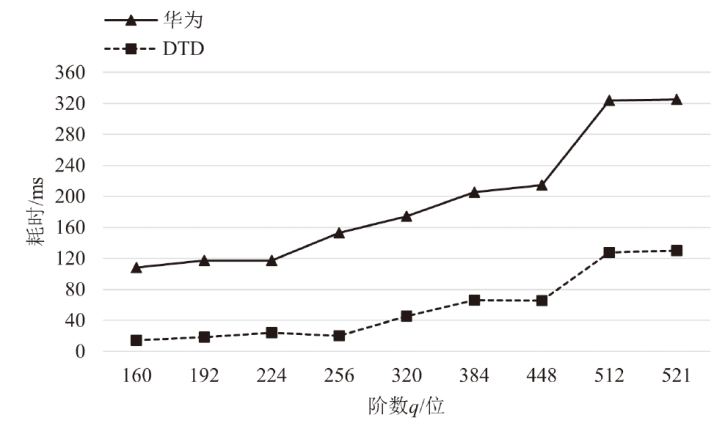
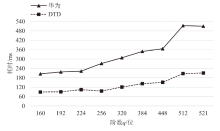
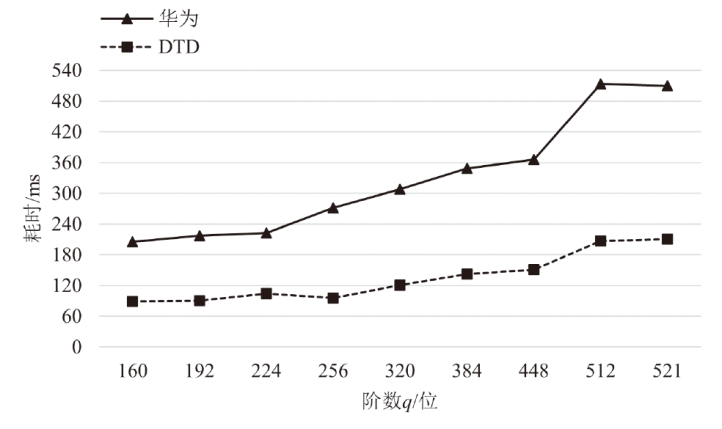
针对物联网设备间认证和加密通信效率及安全性的问题,在物联网技术成熟和应用普及的背景下,文章设计并实现了一种简洁低交互的物联网设备认证协议。该协议的设计包括设备信任绑定过程和设备密钥协商过程。信任绑定过程通过交换云服务器认证的身份标识公钥来验证通信对方的身份,确保身份标识公钥的安全存储。为保障安全性,认证过程中采用对称加密传输双方的身份标识公钥,其密钥通过不经意伪随机函数计算确定。密钥协商过程则基于HMQV协议协商,后续用于安全通信的会话密钥。与华为设备互联认证协议相比,该协议的交互次数减少。实验结果表明,其计算和通信开销更低,效率更高。
中图分类号:
引用本文
王梅, 杨潇然, 李增鹏. 简洁低交互的物联网设备认证协议研究[J]. 信息网络安全, 2025, 25(7): 1032-1043.
WANG Mei, YANG Xiaoran, LI Zengpeng. Research on Simple and Low Interaction Authentication Protocols for IoT Devices[J]. Netinfo Security, 2025, 25(7): 1032-1043.
表1
符号及含义
| 符号 | 含义 |
|---|---|
| 大素数 | |
| 群的阶 | |
| 群的生成元 | |
| 有限群 | |
| 实例生成器 | |
| 安全参数 | |
| 多项式时间内敌手 | |
| 阶为 | |
| 模 | |
| 从一个集合中均匀随机采样 | |
| 口令 | |
| 哈希函数 | |
| 在 | |
| 密钥为 | |
| PPT | 多项式时间 |
| [1] | GARBA A, KHOURY D, BALIAN P, et al. LightCert4IoTs: Blockchain-Based Lightweight Certificates Authentication for IoT Applications[J]. IEEE Access, 2023, 11: 28370-28383. |
| [2] | AMANLOU S, HASAN M K, ABU B K A. Lightweight and Secure Authentication Scheme for IoT Network Based on Publish-Subscribe Fog Computing Model[EB/OL]. (2021-09-13) [2024-10-15]. https://doi.org/10.1016/j.comnet.2021.108465. |
| [3] | SIDDIQUI Z, GAO Jiechao, KHAN M K. An Improved Lightweight PUF-PKI Digital Certificate Authentication Scheme for the Internet of Things[J]. IEEE Internet of Things Journal, 2022, 9(20): 19744-19756. |
| [4] | TSAI J L, LO N W. Secure Anonymous Key Distribution Scheme for Smart Grid[J]. IEEE Transactions on Smart Grid, 2016, 7(2): 906-914. |
| [5] | BELLOVIN S M, MERRITT M. Encrypted Key Exchange: Password-Based Protocols Secure against Dictionary Attacks[C]// IEEE. Proceedings 1992 IEEE Computer Society Symposium on Research in Security and Privacy. New York: IEEE, 1992: 72-84. |
| [6] | HAO Feng, RYAN P Y A. Password Authenticated Key Exchange by Juggling[C]// Springer. Security Protocols XVI. Heidelberg: Springer, 2011: 159-171. |
| [7] | LEE H, WON D. Prevention of Exponential Equivalence in Simple Password Exponential Key Exchange (SPEKE)[J]. Symmetry, 2015, 7(3): 1587-1594. |
| [8] | POINTCHEVAL D, WANG Guilin. VTBPEKE: Verifier-Based Two-Basis Password Exponential Key Exchange[C]// ACM. Proceedings of the 2017 ACM on Asia Conference on Computer and Communications Security. New York: ACM, 2017: 301-312. |
| [9] | SHAMIR A. Identity-Based Cryptosystems and Signature Schemes[C]// Springer. Advances in Cryptology. Heidelberg: Springer, 2007: 47-53. |
| [10] | LI Xiong, XIONG Yongping, MA Jian, et al. An Efficient and Security Dynamic Identity Based Authentication Protocol for Multi-Server Architecture Using Smart Cards[J]. Journal of Network and Computer Applications, 2012, 35(2): 763-769. |
| [11] | WU T D. The Secure Remote Password Protocol[EB/OL]. [2024-10-15]. https://www.ndss-symposium.org/wp-content/uploads/2017/09/The-Secure-Remote-Password-Protocol.pdf. |
| [12] | JARECKI S, KRAWCZYK H, XU Jiayu. OPAQUE: An Asymmetric PAKE Protocol Secure against Pre-Computation Attacks[C]// Springer. 37th Annual International Conference on the Theory and Applications of Cryptographic Techniques. Heidelberg: Springer, 2018: 456-486. |
| [13] | DIFFIE W, VAN O P C, WIENER M J. Authentication and Authenticated Key Exchanges[J]. Designs, Codes and Cryptography, 1992, 2(2): 107-125. |
| [14] | BLAKE W S, MENEZES A. Unknown Key-Share Attacks on the Station-to-Station (STS) Protocol[C]// Springer. International Workshop on Public Key Cryptography. Heidelberg: Springer, 1999: 154-170. |
| [15] | LAW L, MENEZES A, QU Minghua, et al. An Efficient Protocol for Authenticated Key Agreement[J]. Designs, Codes and Cryptography, 2003, 28(2): 119-134. |
| [16] | KRAWCZYK H. HMQV: A High-Performance Secure Diffie-Hellman Protocol: (Extended Abstract)[C]// Springer. Advances in Cryptology- CRYPTO 2005. Heidelberg: Springer, 2005: 546-566. |
| [17] | KUMARI S, KARUPPIAH M, DAS A K, et al. A Secure Authentication Scheme Based on Elliptic Curve Cryptography for IoT and Cloud Servers[J]. The Journal of Supercomputing, 2018, 74(12): 6428-6453. |
| [18] | BABU E S, DADI A K, SINGH K K, et al. A Distributed Identity-Based Authentication Scheme for Internet of Things Devices Using Permissioned Blockchain System[EB/OL]. (2022-02-04) [2024-10-15]. https://doi.org/10.1111/exsy.12941. |
| [19] | DANIEL R M, THOMAS A, RAJSINGH E B, et al. A Strengthened ECK Secure Identity Based Authenticated Key Agreement Protocol Based on the Standard CDH Assumption[EB/OL]. (2023-07-11) [2024-10-15]. https://doi.org/10.1016/j.ic.2023.105067. |
| [20] | CAO Jin, LI Hui, MA Maode, et al. A Simple and Robust Handover Authentication between HeNB and eNB in LTE Networks[J]. Computer Networks, 2012, 56(8): 2119-2131. |
| [21] | GB/T 32907-2016 Information Security Technology—SM4 Block Cipher Algorithm[S]. Beijing: Standards Press of China, 2016. |
| GB/T 32907-2016 信息安全技术 SM4 分组密码算法[S]. 北京: 中国标准出版社, 2016. | |
| [22] | GB/T 32918.2-2016 Information Security Technology—Public Key Cryptographic Algorithm SM2 Based on Elliptic Curves-Part 2: Digital Signature Algorithm[S]. Beijing: Standards Press of China, 2016. |
| GB/T 2918. 2-2016信息安全技术 SM2椭圆曲线公钥密码算法第2部分:数字签名算法[S]. 北京: 中国标准出版社, 2016. | |
| [23] | CASACUBERTA S, HESSE J, LEHMANN A. SoK: Oblivious Pseudorandom Functions[C]// IEEE. 2022 IEEE 7th European Symposium on Security and Privacy (EuroS&P). New York: IEEE, 2022: 625-646. |
| [24] | BELLARE M, POINTCHEVAL D, ROGAWAY P. Authenticated Key Exchange Secure against Dictionary Attacks[C]// Springer. Advances in Cryptology — EUROCRYPT 2000. Heidelberg: Springer, 2000: 139-155. |
| [25] | ABDALLA M, FOUQUE P A, POINTCHEVAL D. Password-Based Authenticated Key Exchange in the Three-Party Setting[C]// Springer. Public Key Cryptography-PKC 2005. Heidelberg: Springer, 2005: 65-84. |
| [1] | 张光华, 常继友, 陈放, 毛伯敏, 王鹤, 张建燕. 基于库函数动态替换的物联网设备固件仿真方案[J]. 信息网络安全, 2025, 25(7): 1053-1062. |
| [2] | 邓东上, 王伟业, 张卫东, 吴宣够. 基于模型特征方向的分层个性化联邦学习框架[J]. 信息网络安全, 2025, 25(6): 889-897. |
| [3] | 李强, 沈援海, 王锦泽, 黄晏瑜, 孙建国. 一种面向工业物联网环境的离线—在线签名方案[J]. 信息网络安全, 2025, 25(3): 392-402. |
| [4] | 袁征, 张跃飞, 冯笑, 乔雅馨. 基于PUF的电力物联网智能终端认证协议[J]. 信息网络安全, 2025, 25(1): 13-26. |
| [5] | 张学旺, 陈思宇, 罗欣悦, 雷志滔, 谢昊飞. 面向云辅助工业物联网的高效可搜索属性基加密方案[J]. 信息网络安全, 2024, 24(9): 1352-1363. |
| [6] | 邢长友, 王梓澎, 张国敏, 丁科. 基于预训练Transformers的物联网设备识别方法[J]. 信息网络安全, 2024, 24(8): 1277-1290. |
| [7] | 张晓均, 张楠, 郝云溥, 王周阳, 薛婧婷. 工业物联网系统基于混沌映射三因素认证与密钥协商协议[J]. 信息网络安全, 2024, 24(7): 1015-1026. |
| [8] | 胡丞聪, 胡红钢. 基于格的最优轮数口令认证秘密共享协议[J]. 信息网络安全, 2024, 24(6): 937-947. |
| [9] | 李志华, 陈亮, 卢徐霖, 方朝晖, 钱军浩. 面向物联网Mirai僵尸网络的轻量级检测方法[J]. 信息网络安全, 2024, 24(5): 667-681. |
| [10] | 杨杰超, 胡汉平, 帅燕, 邓宇昕. 基于时变互耦合双混沌系统的轻量级序列密码[J]. 信息网络安全, 2024, 24(3): 385-397. |
| [11] | 冯光升, 蒋舜鹏, 胡先浪, 马明宇. 面向物联网的入侵检测技术研究新进展[J]. 信息网络安全, 2024, 24(2): 167-178. |
| [12] | 翟鹏, 何泾沙, 张昱. 物联网环境下基于SM9算法和区块链技术的身份认证方法[J]. 信息网络安全, 2024, 24(2): 179-187. |
| [13] | 印杰, 陈浦, 杨桂年, 谢文伟, 梁广俊. 基于人工智能的物联网DDoS攻击检测[J]. 信息网络安全, 2024, 24(11): 1615-1623. |
| [14] | 王君艳, 伊鹏, 贾洪勇, 张建辉. 基于改进CAE的物联网终端风险评估模型[J]. 信息网络安全, 2024, 24(1): 150-159. |
| [15] | 张伟, 李子轩, 徐晓瑀, 黄海平. SDP-CoAP:基于软件定义边界的安全增强CoAP通信框架设计[J]. 信息网络安全, 2023, 23(8): 17-31. |
| 阅读次数 | ||||||
|
全文 |
|
|||||
|
摘要 |
|
|||||